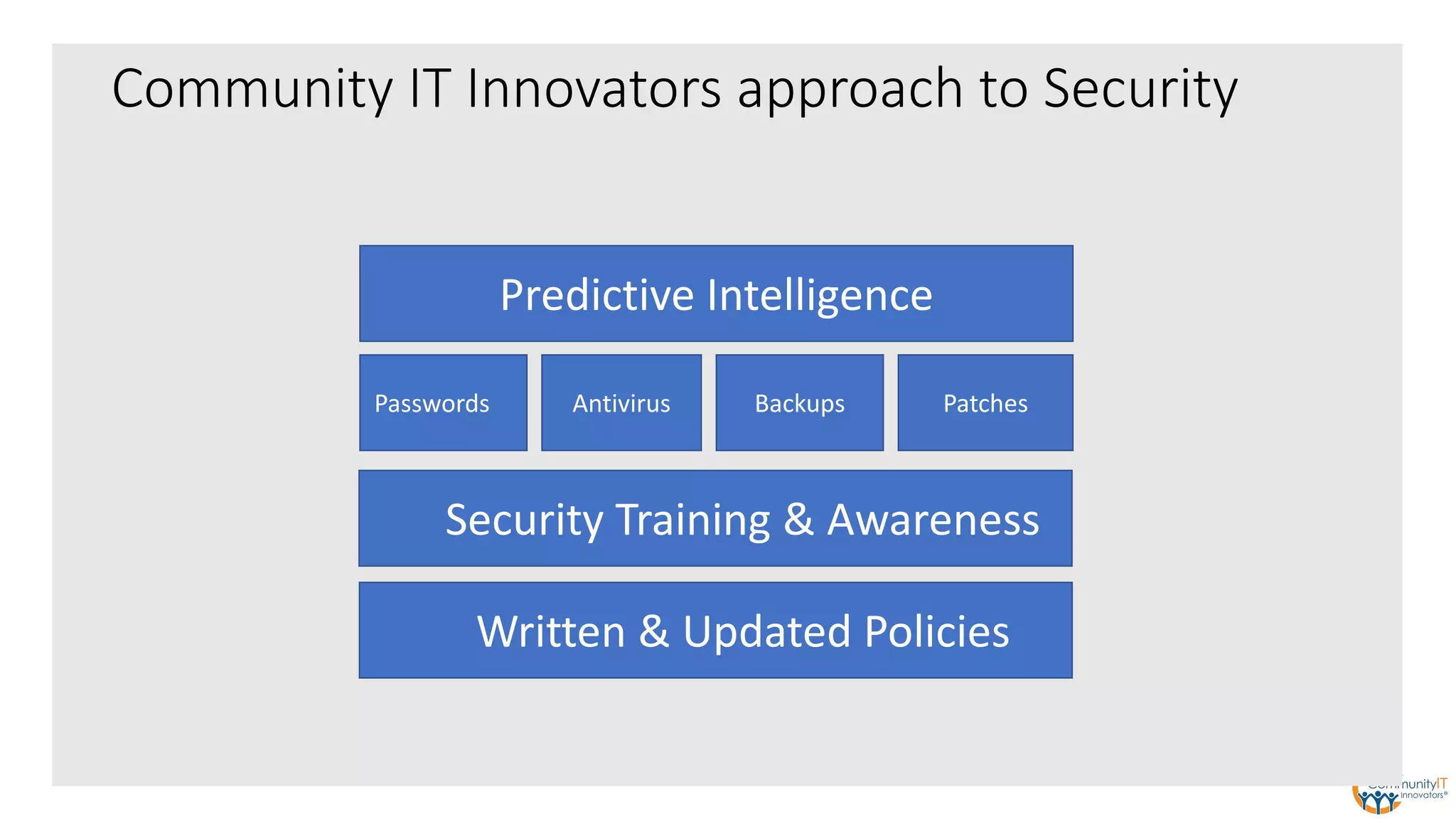
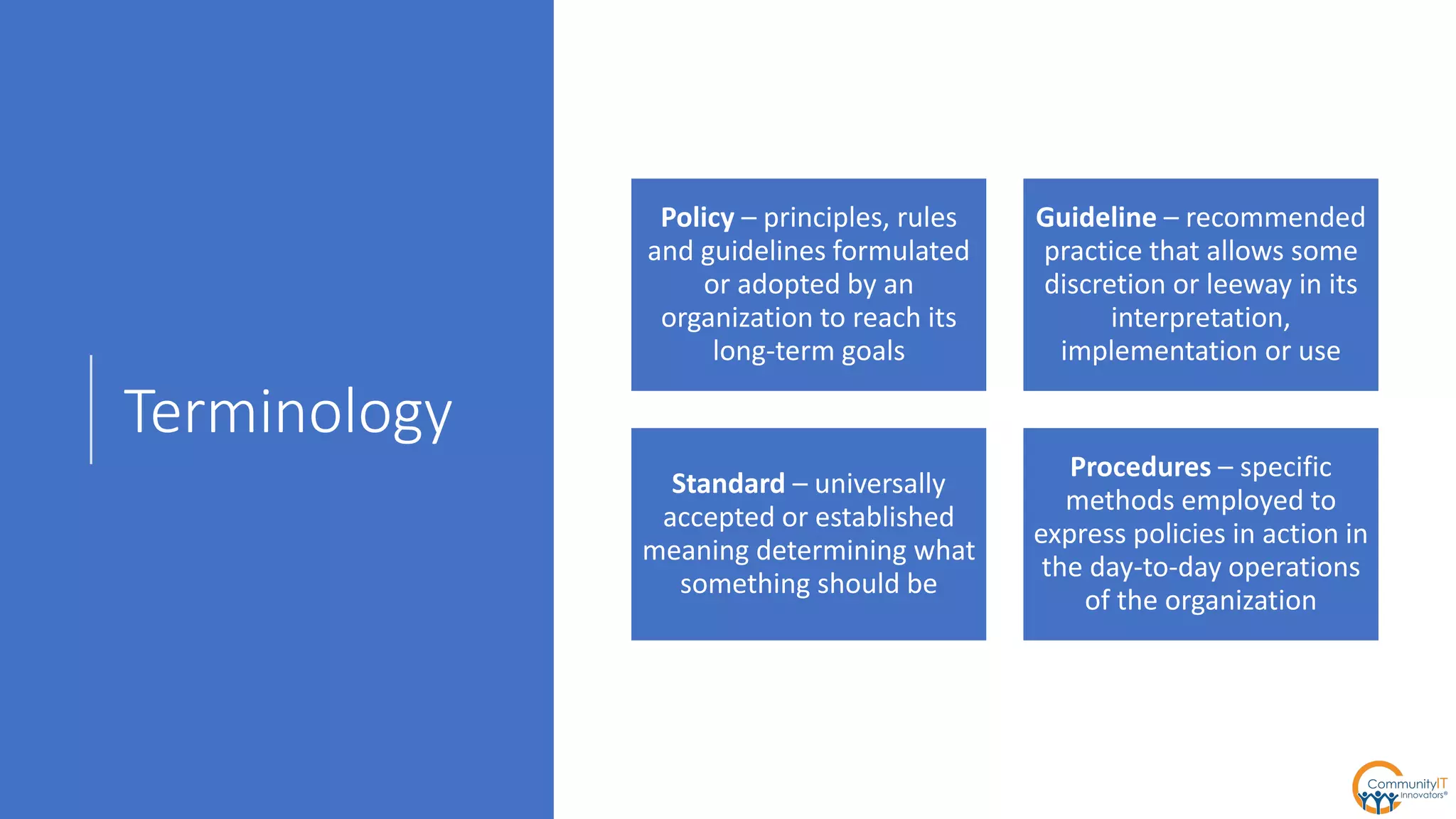
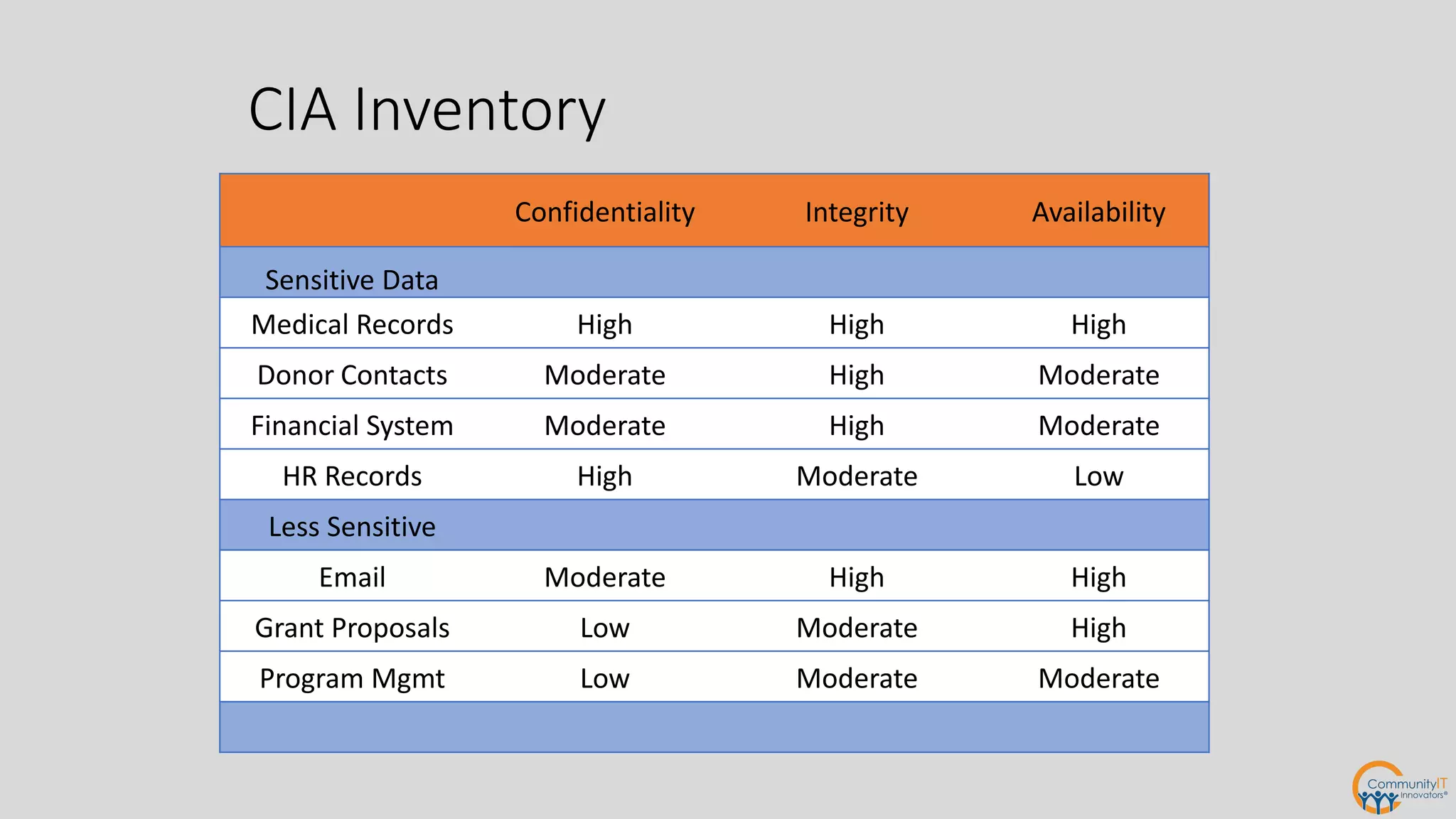
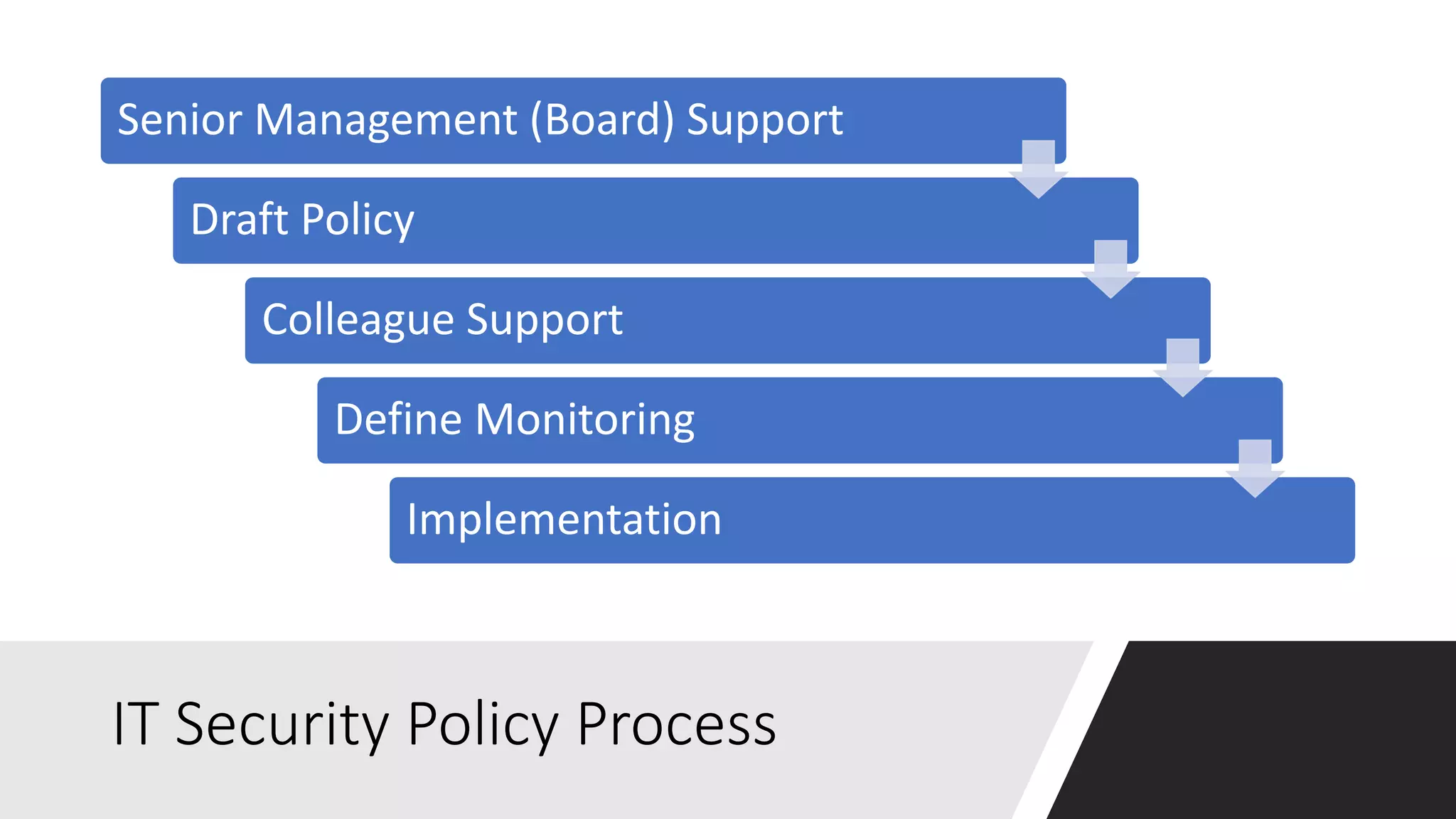
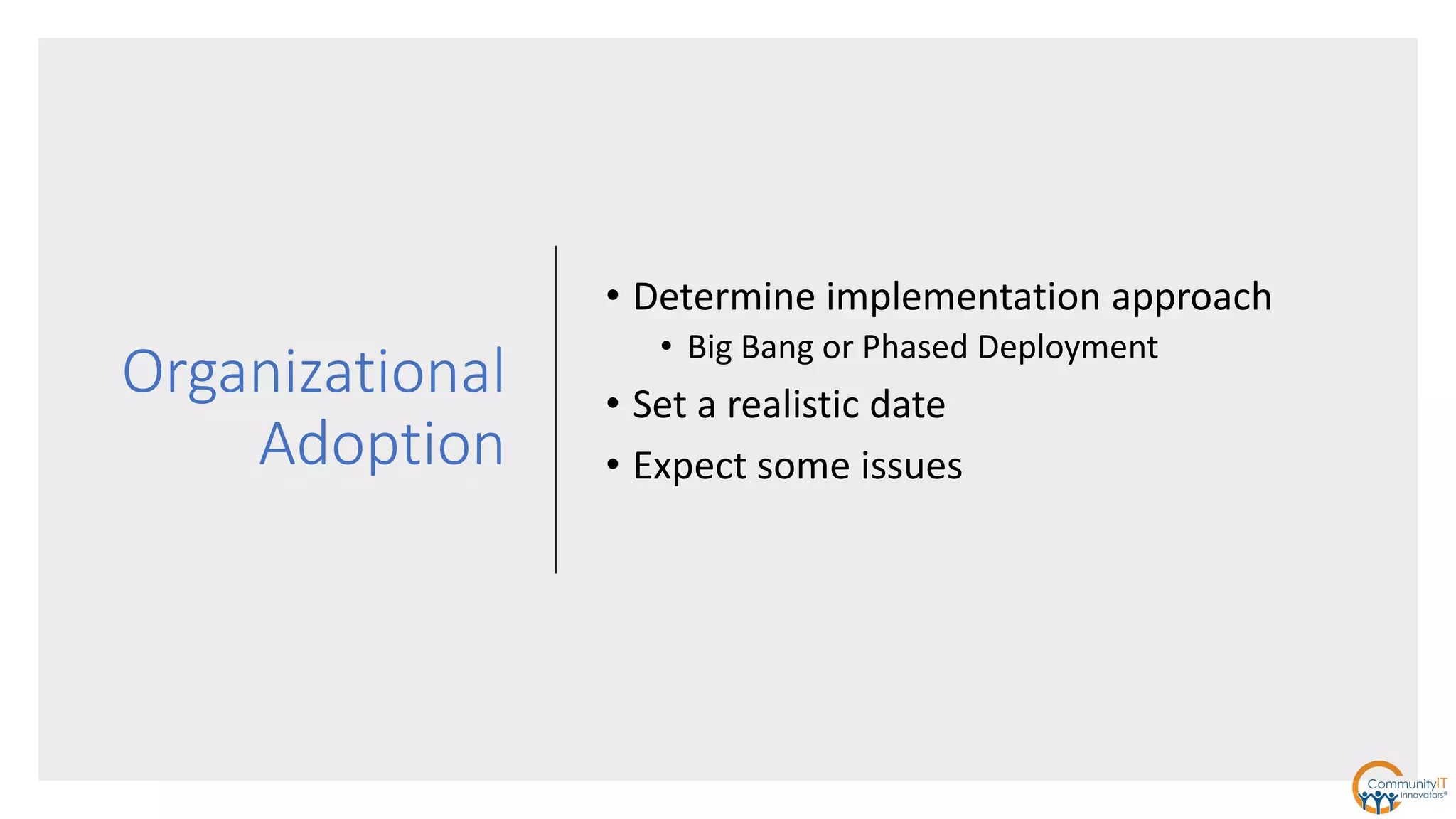
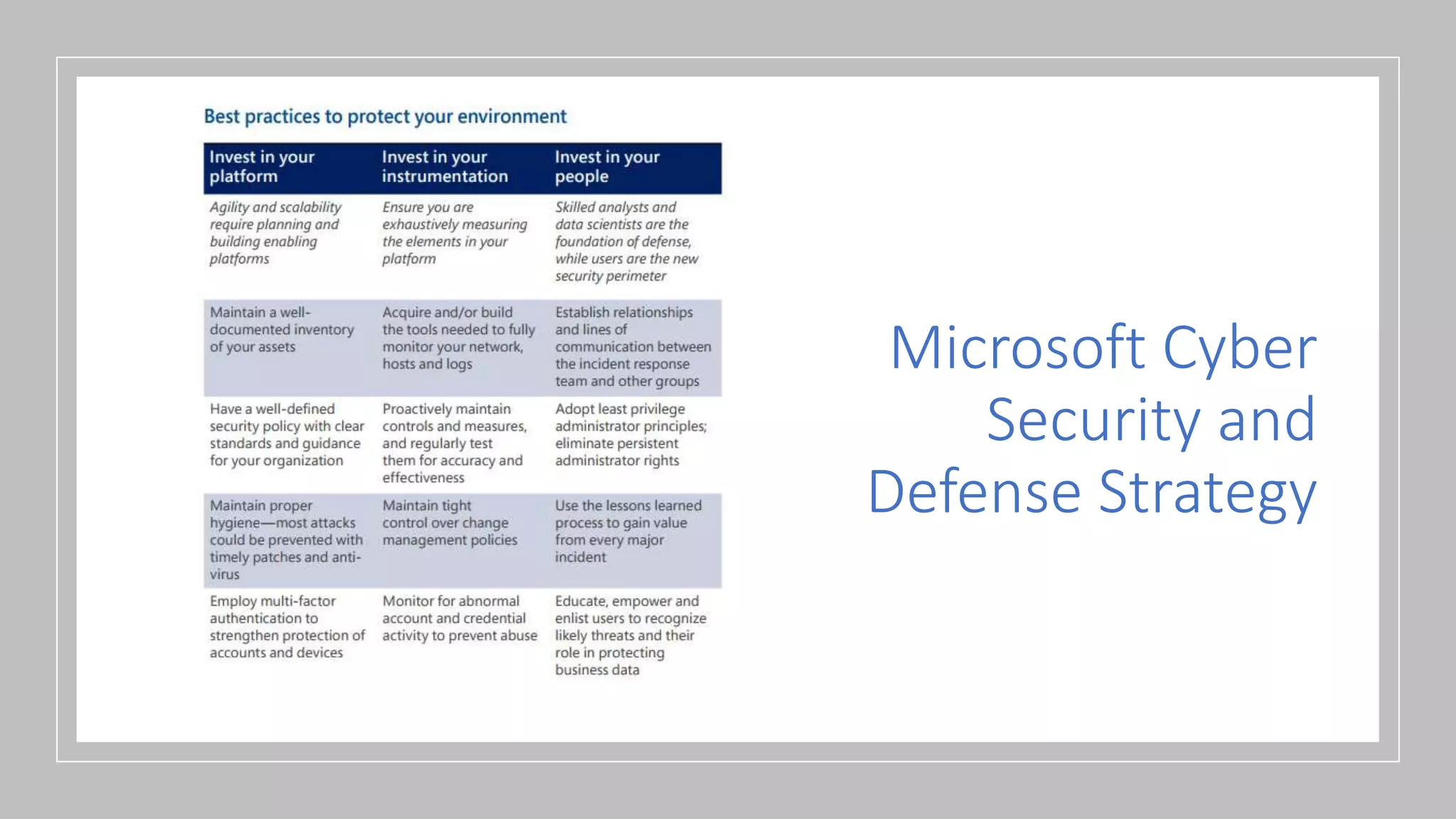
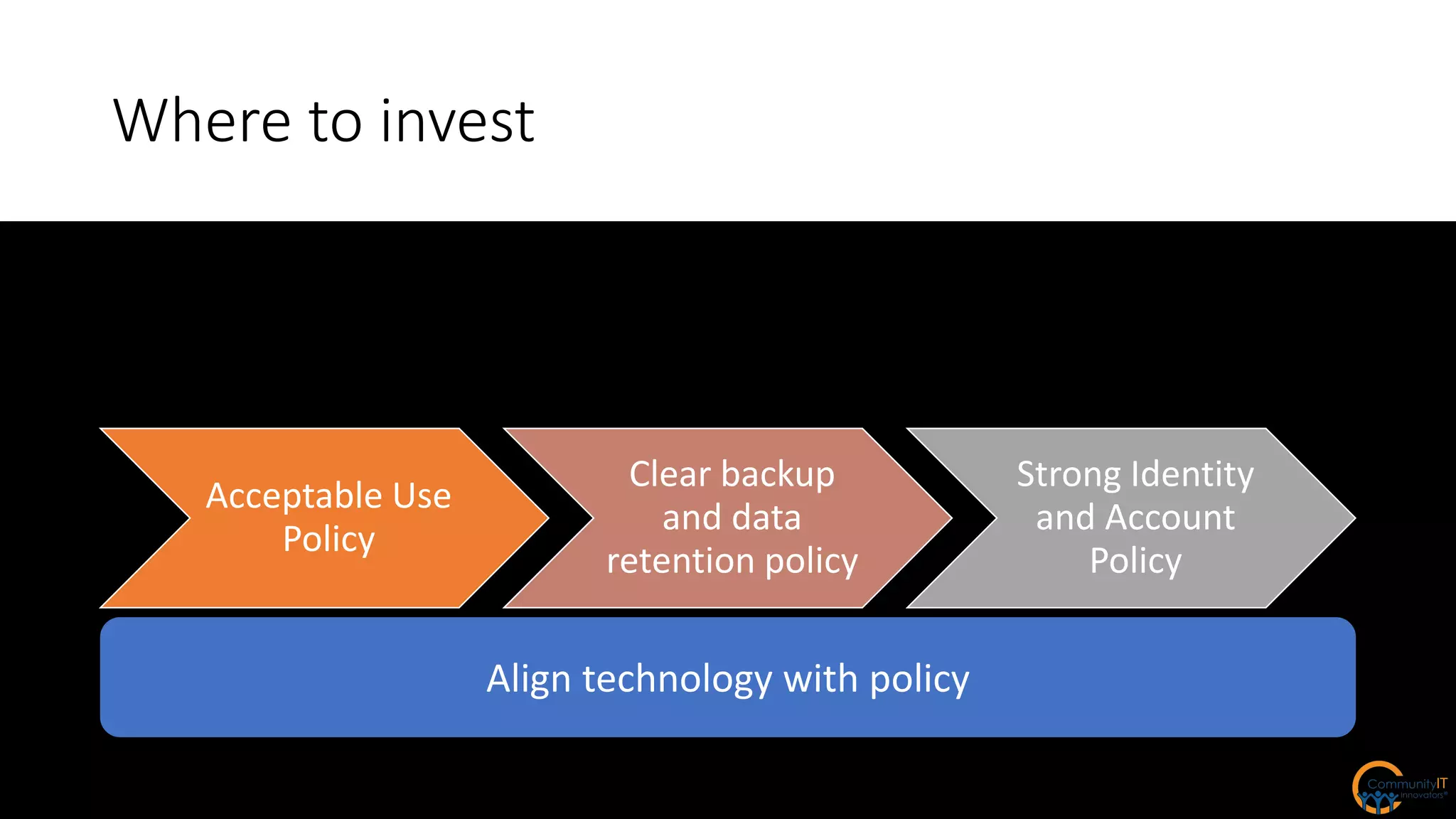
The IT security policy webinar series from July 2017, presented by Matthew Eshleman, highlights the importance of effective technology use for community IT and discusses various security policies that organizations should adopt. Key topics include acceptable use policies, identity management, data classification, and the significance of executive support in policy implementation. Additionally, the webinar emphasizes the need for ongoing training and the establishment of a proactive security culture within organizations.