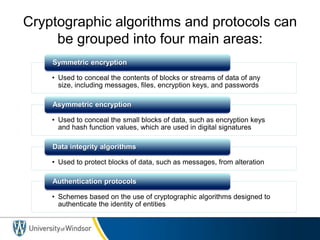
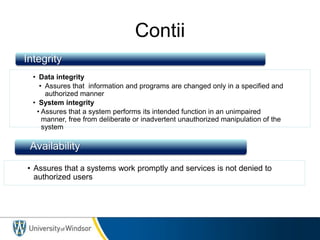
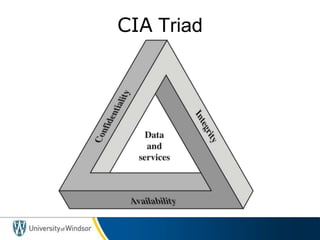
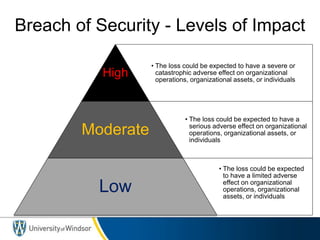
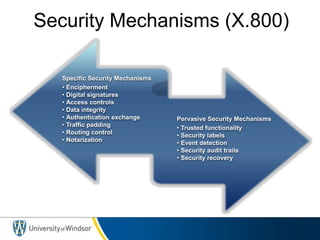
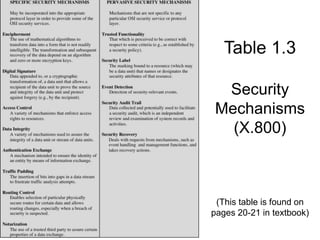
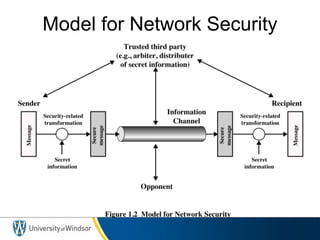
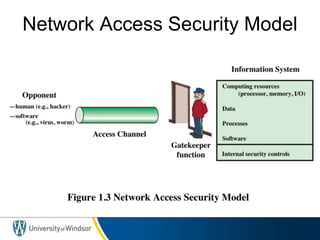
This document provides information about the 60-467 Network Security course taught by Dr. Robert D. Kent at the University of Windsor. The 3-sentence summary is:
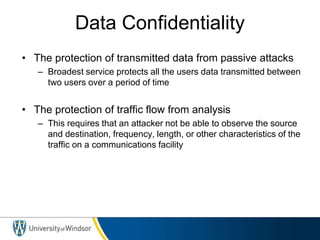
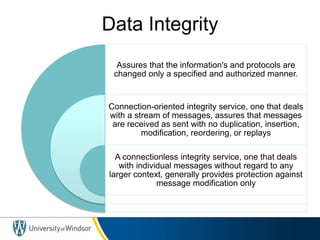
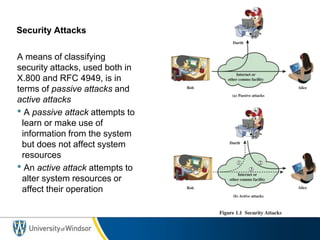
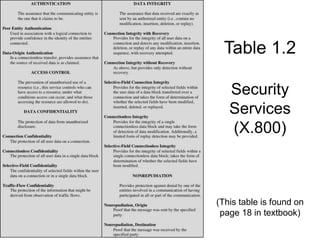
The course introduces advanced topics in network security including encryption, authentication, intrusion detection, and security of email and web access. Students must complete a midterm exam, individual research essay, presentation, and two projects (individual and group). The course website provides basic information, requirements are outlined, and the textbook for the course is Cryptography and Network Security by William Stallings which covers topics such as cryptography algorithms, network security services, and security attacks.