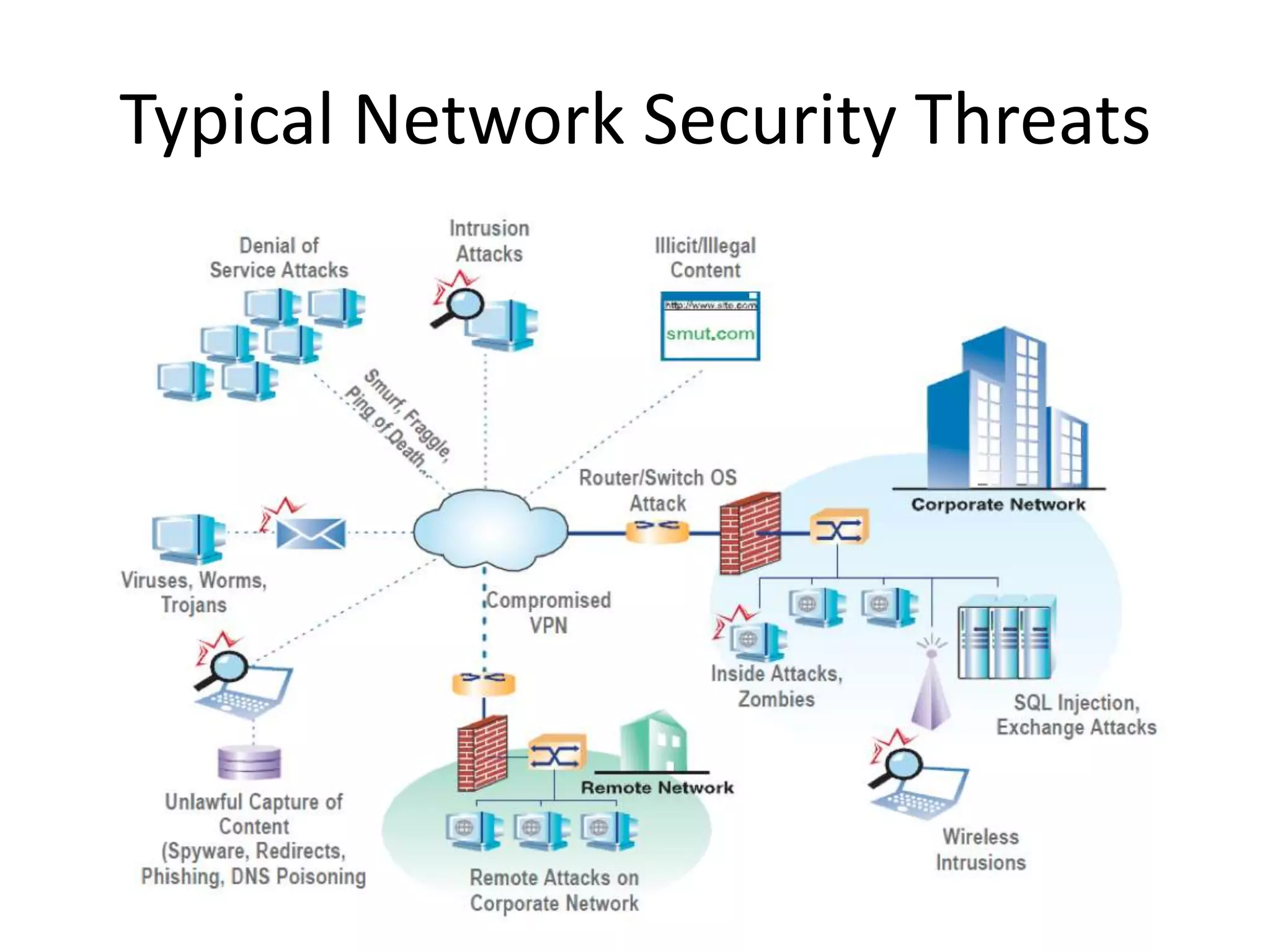
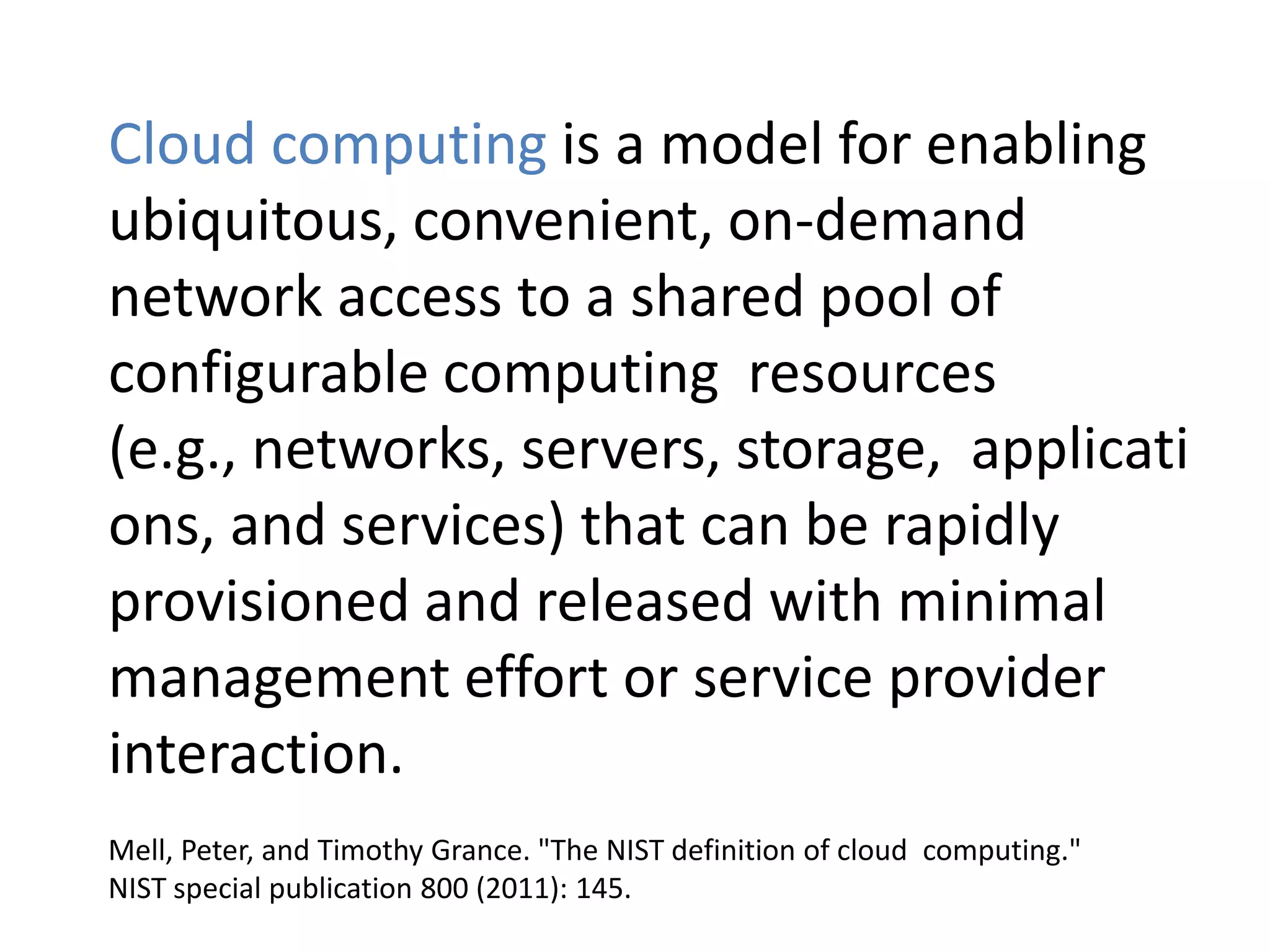
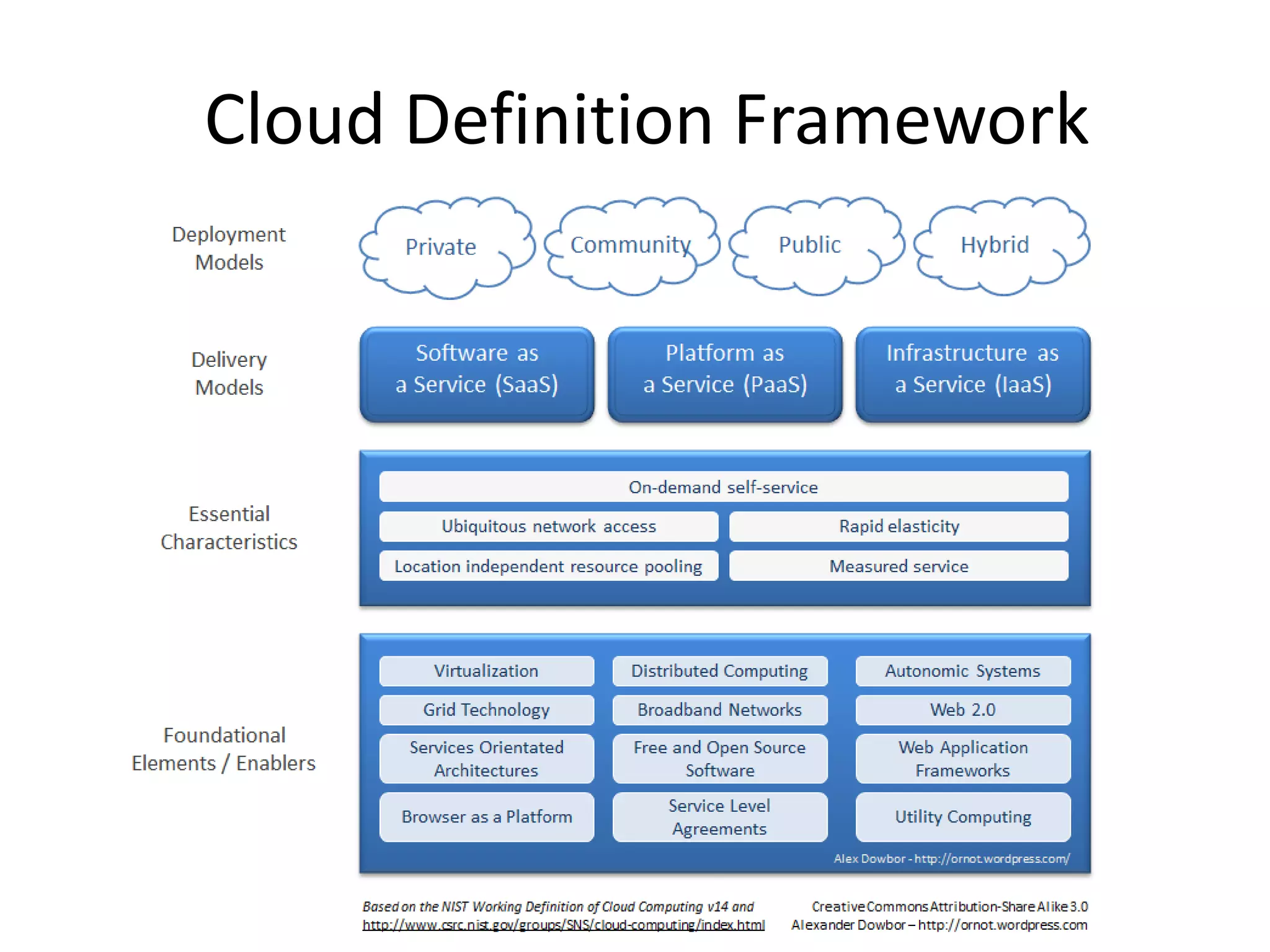
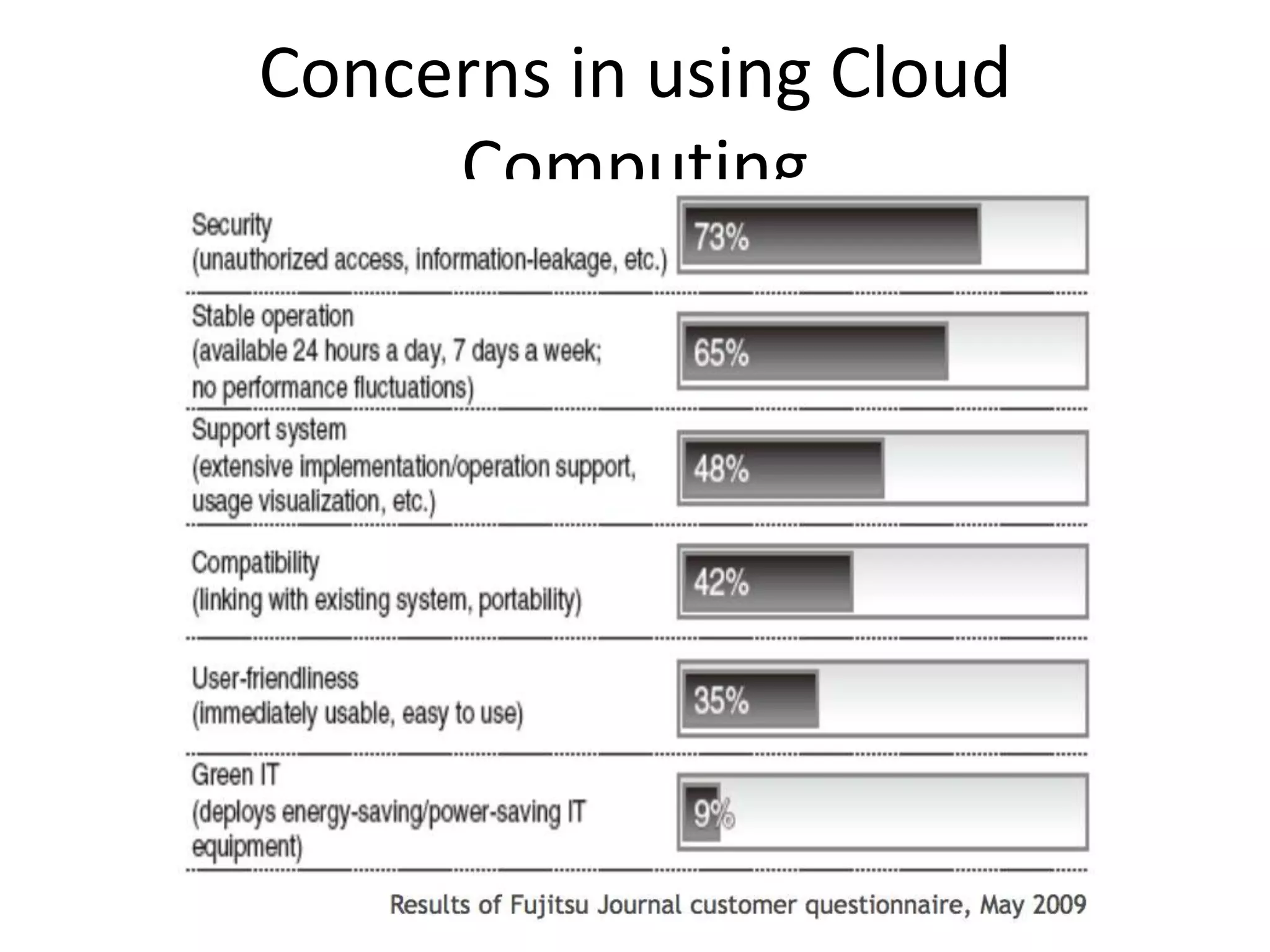
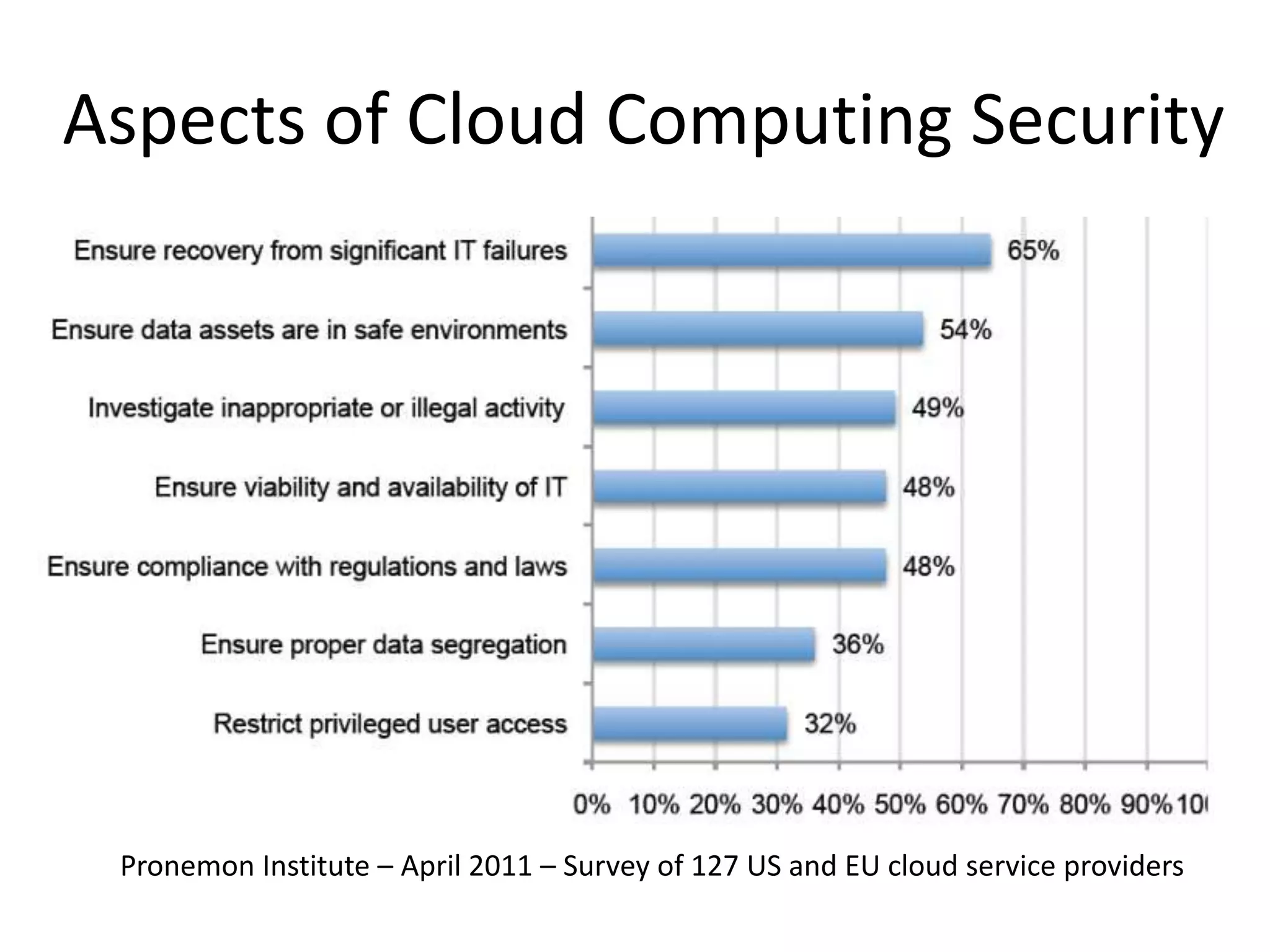
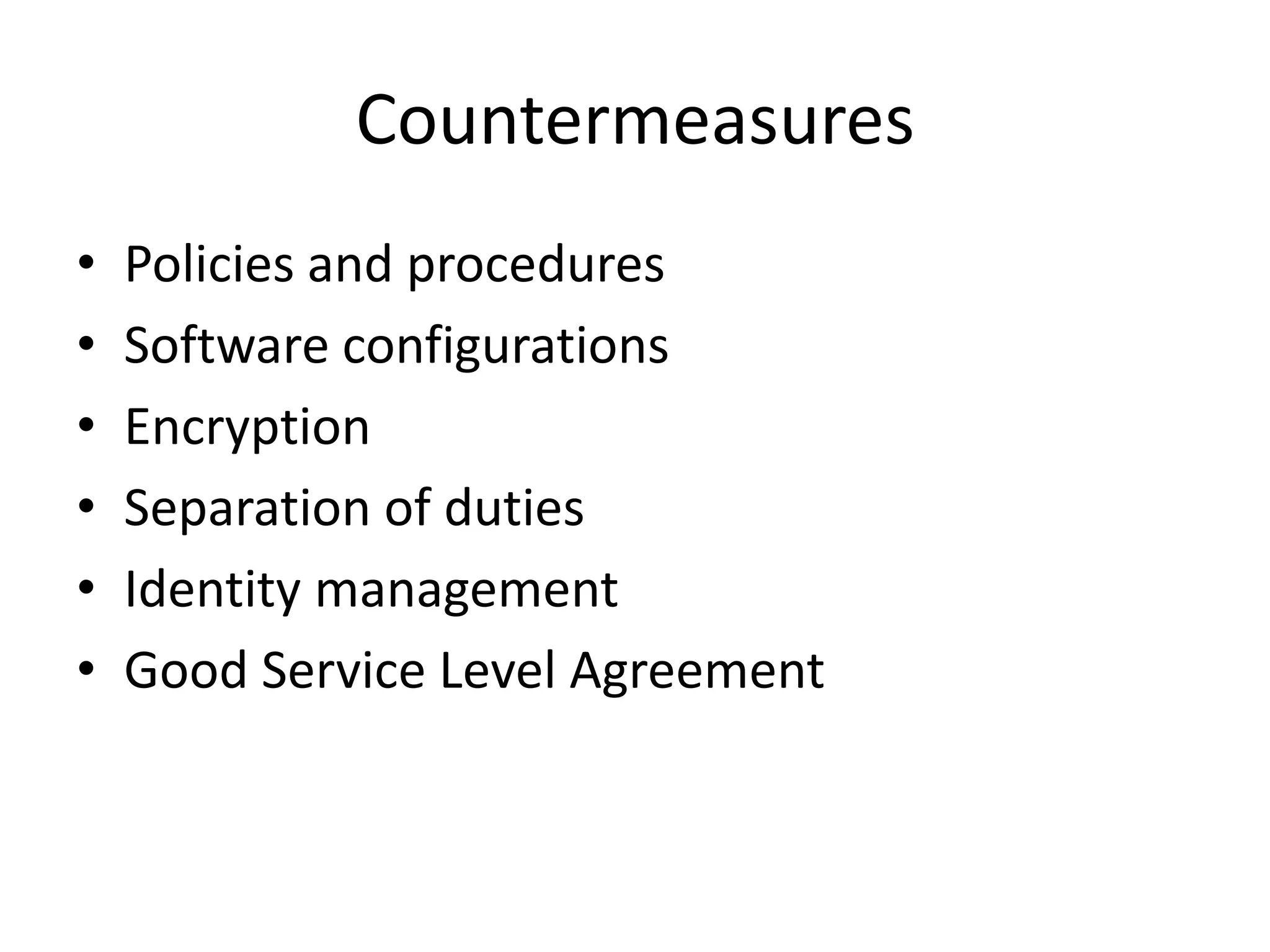
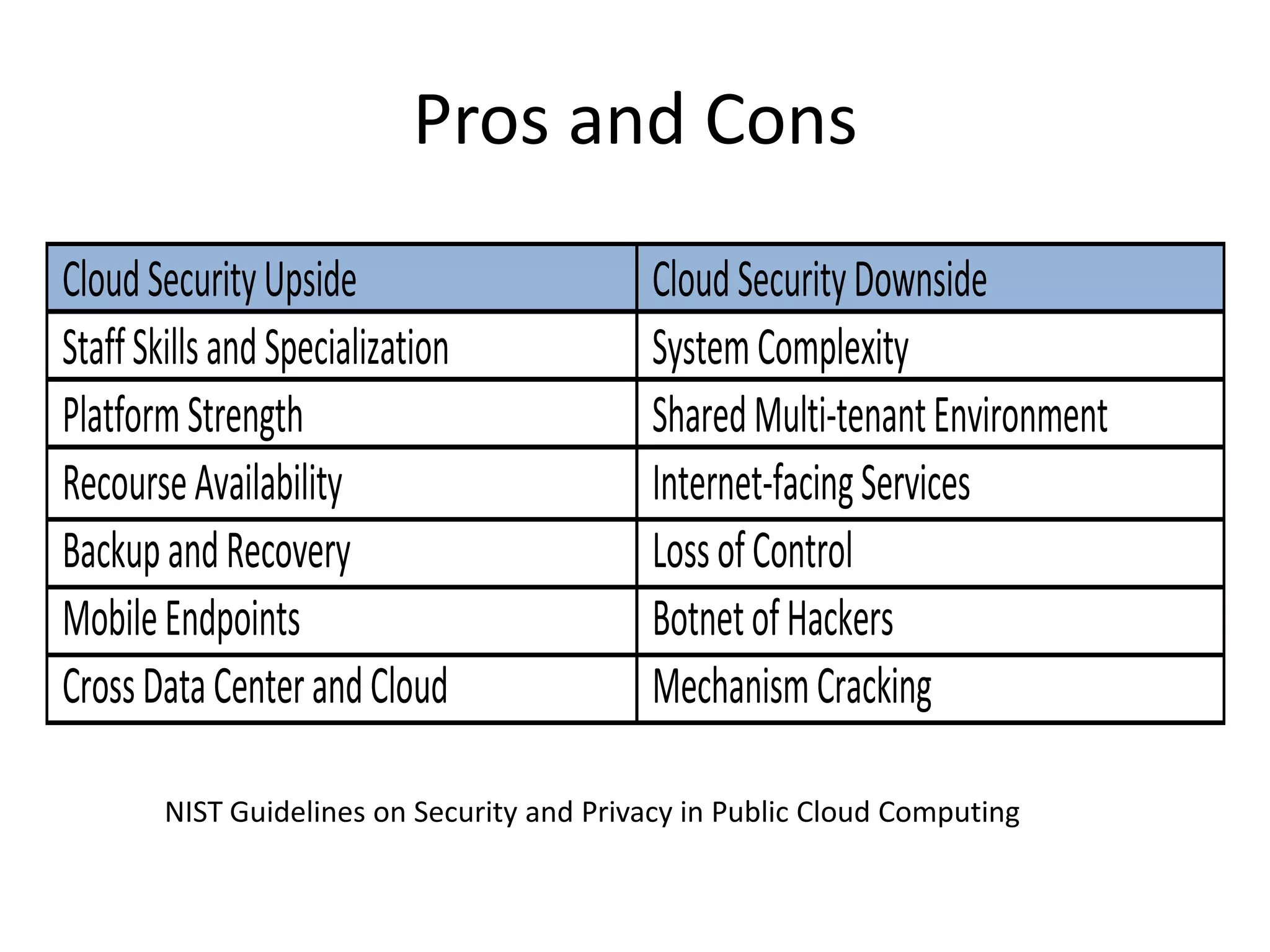
This document discusses cloud computing security. It provides an overview of cloud computing and outlines some of the key benefits it provides including minimized costs, scalability, and efficiency. However, it also notes there are security concerns to consider like data breaches, hijacking, and insider threats. The document examines some common threats and vulnerabilities cloud systems face and recommends various countermeasures that can be implemented, such as encryption, identity management, and service level agreements. It concludes with a summary of the main topics covered regarding cloud computing security.