Embed presentation
Downloaded 12 times
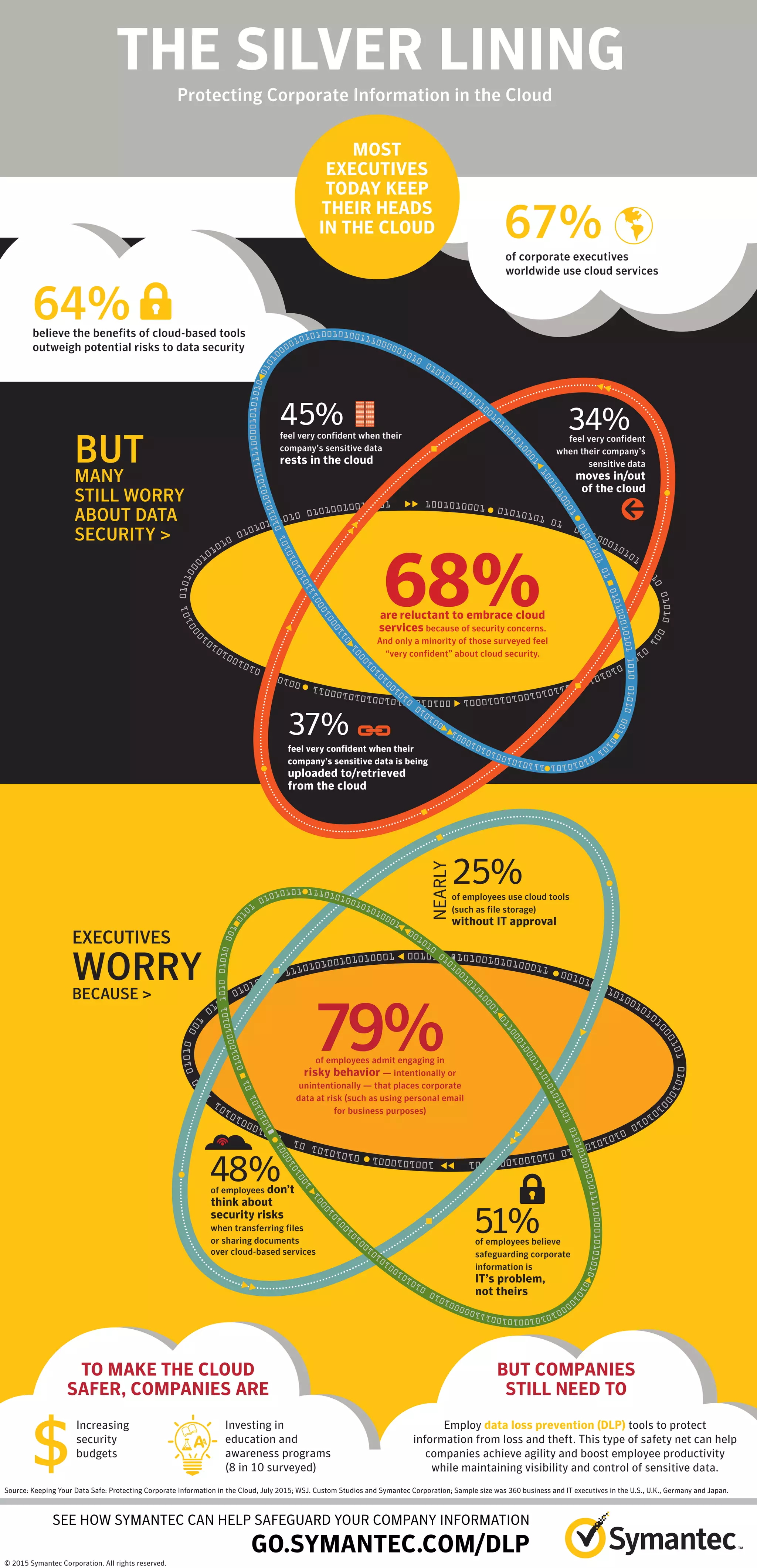

The document discusses corporate executives' use of and concerns about cloud services. While most executives believe the benefits of cloud tools outweigh security risks, many employees do not consider security and share documents without approval. Nearly half of employees admit engaging in risky behavior with corporate data. To address these issues and make the cloud safer, companies are increasing security budgets and investing in education programs. However, only a minority of surveyed executives feel very confident about cloud security.
