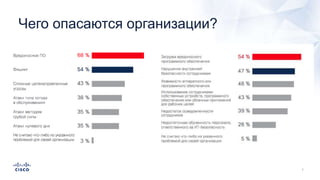
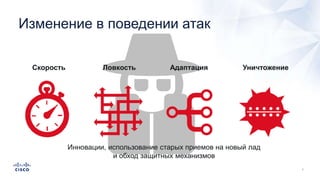
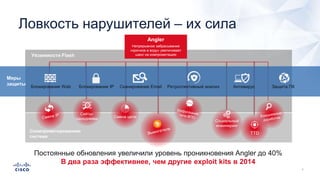
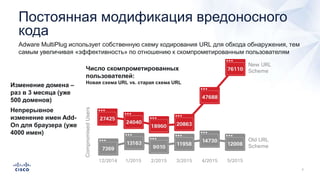
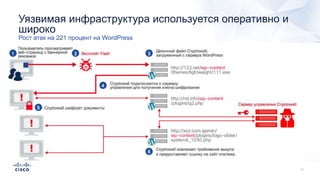
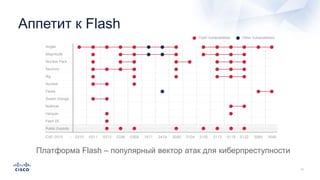
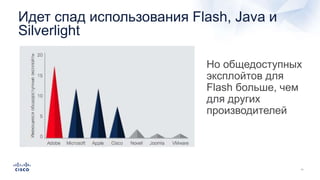
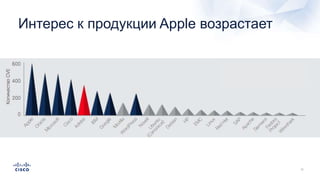
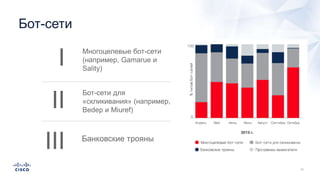
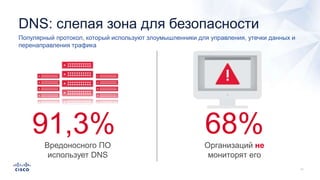
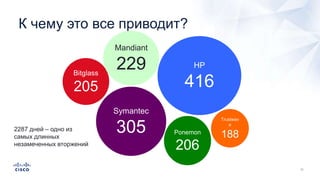
Документ анализирует текущие тенденции внешних угроз в области кибербезопасности, подчеркивая высокую эффективность атак с использованием старых методов и постоянное изменение тактик злоумышленников. Обсуждается рост популярности вымогателей и использование технологий, таких как Tor, для автоматизации атак и сокрытия идентичности. Также акцентируется внимание на проблемах с защитой, включая недостаточный мониторинг DNS и рост атак на веб-ресурсы.