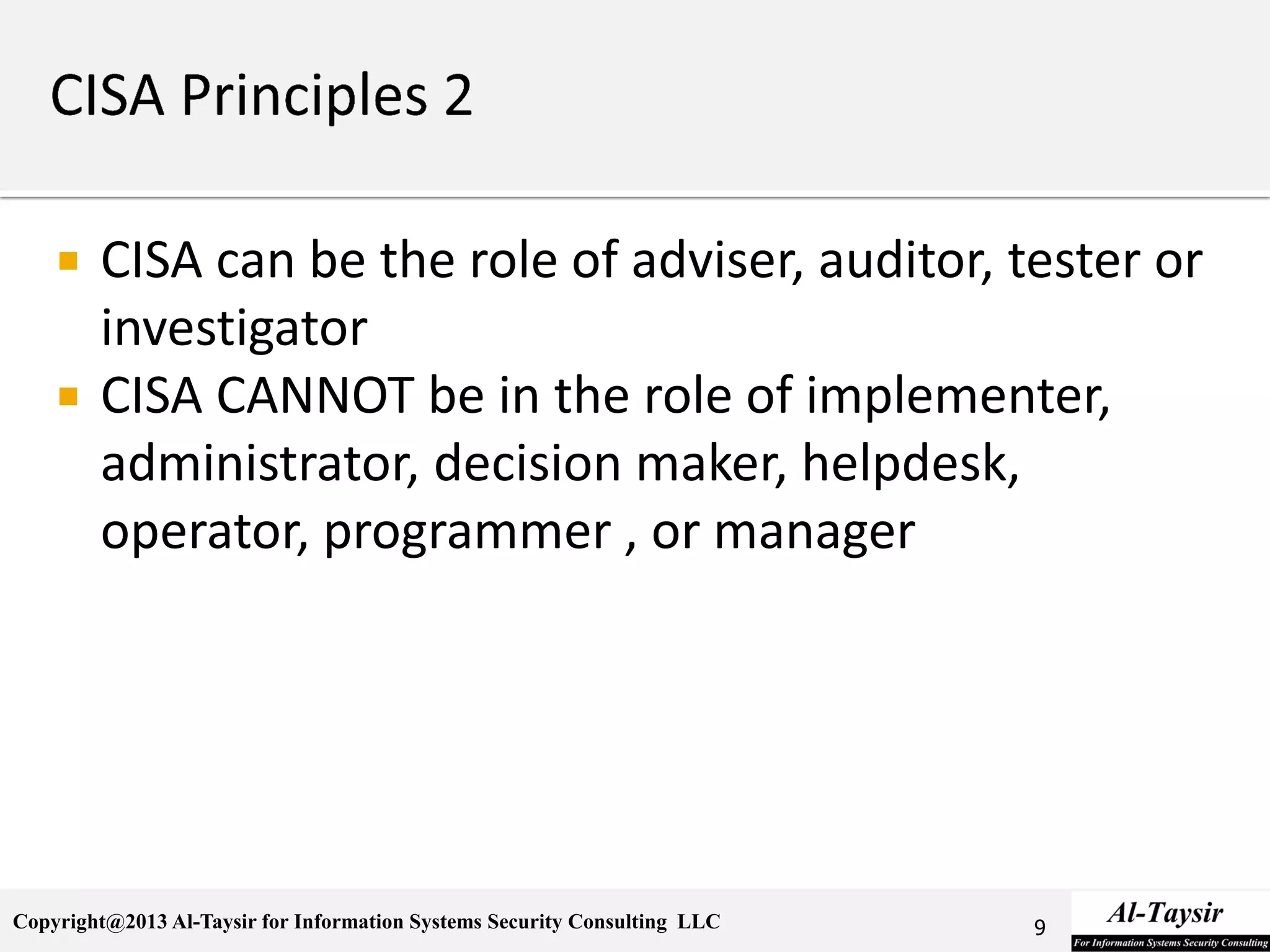
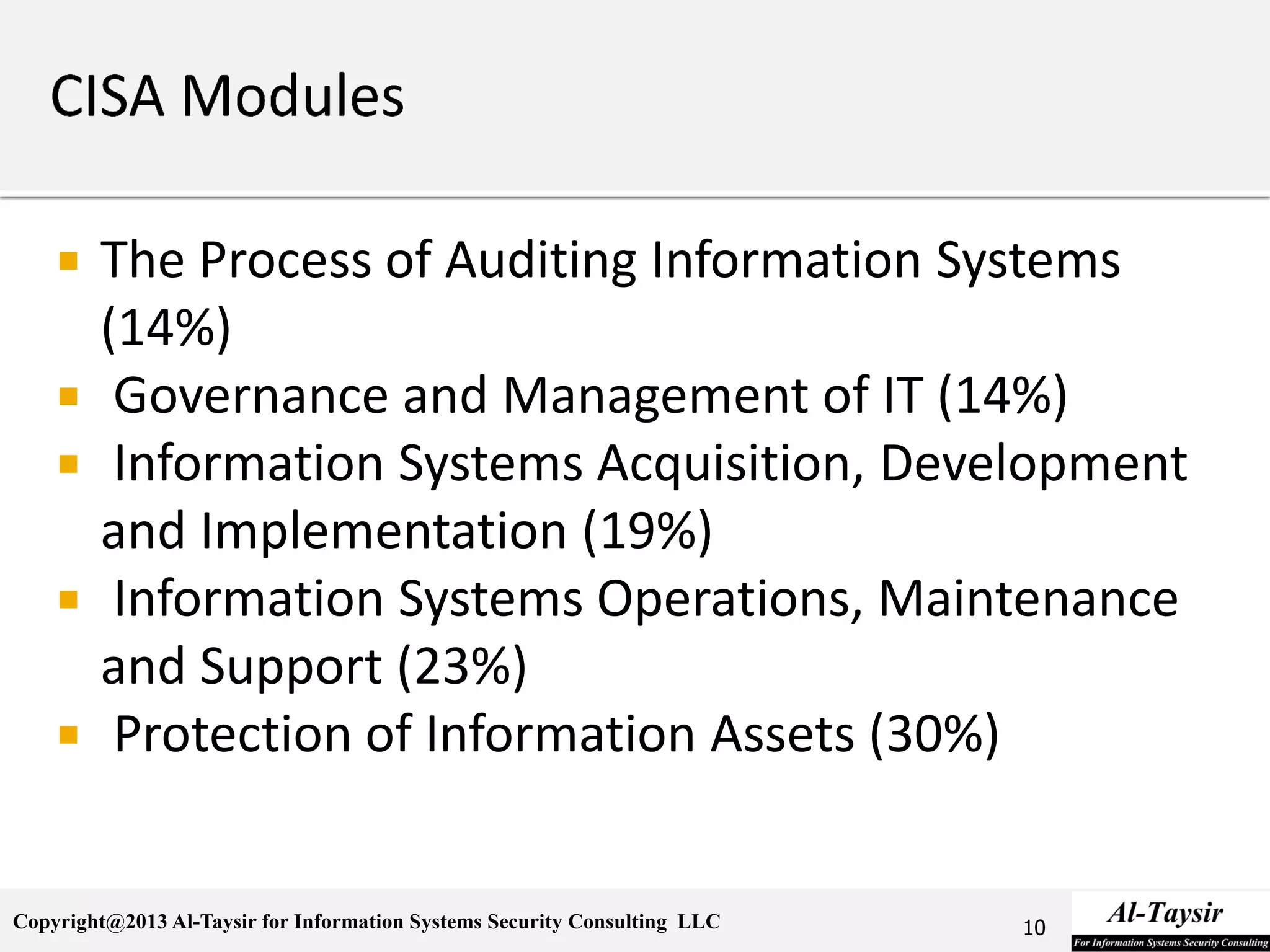
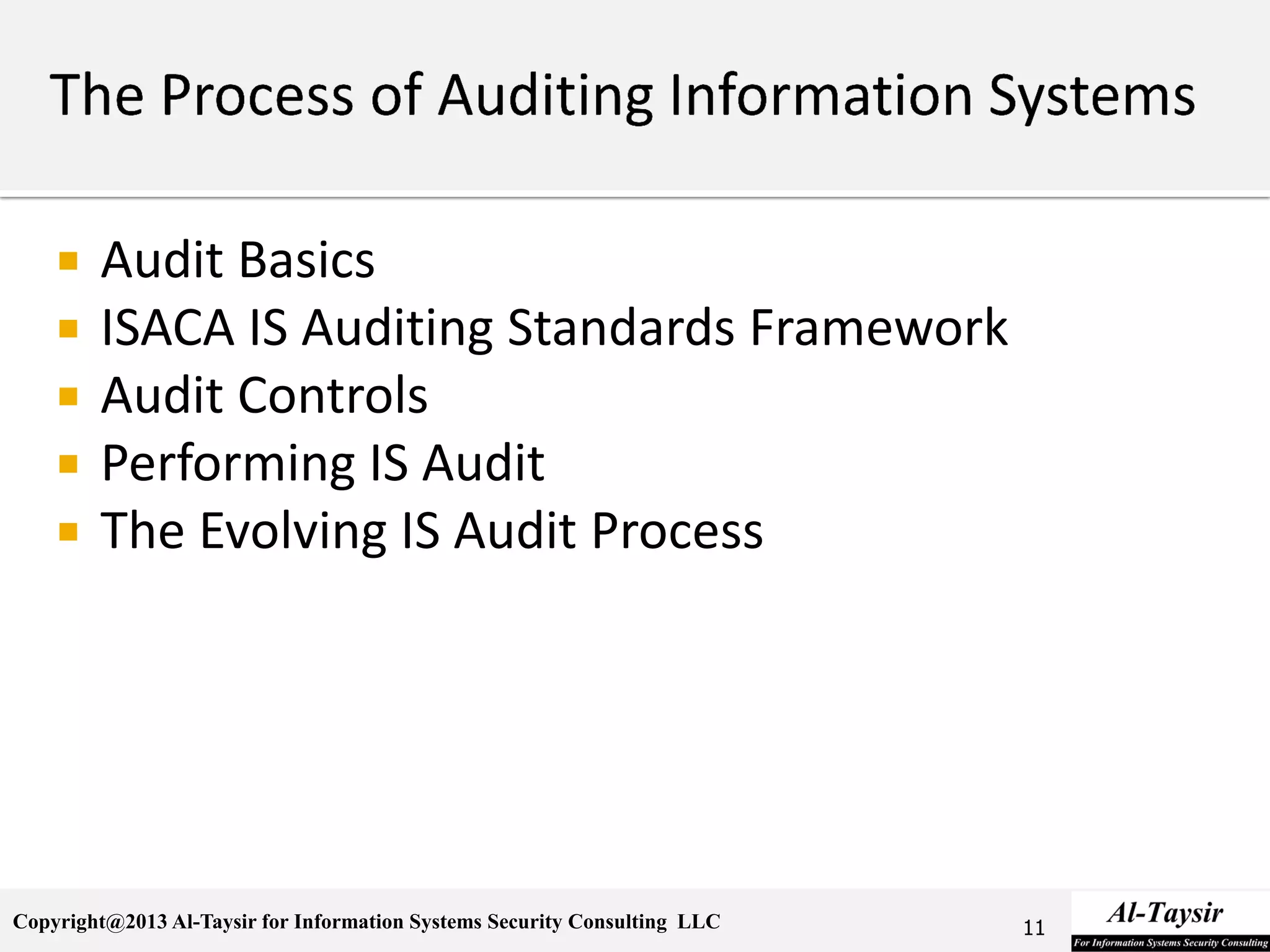
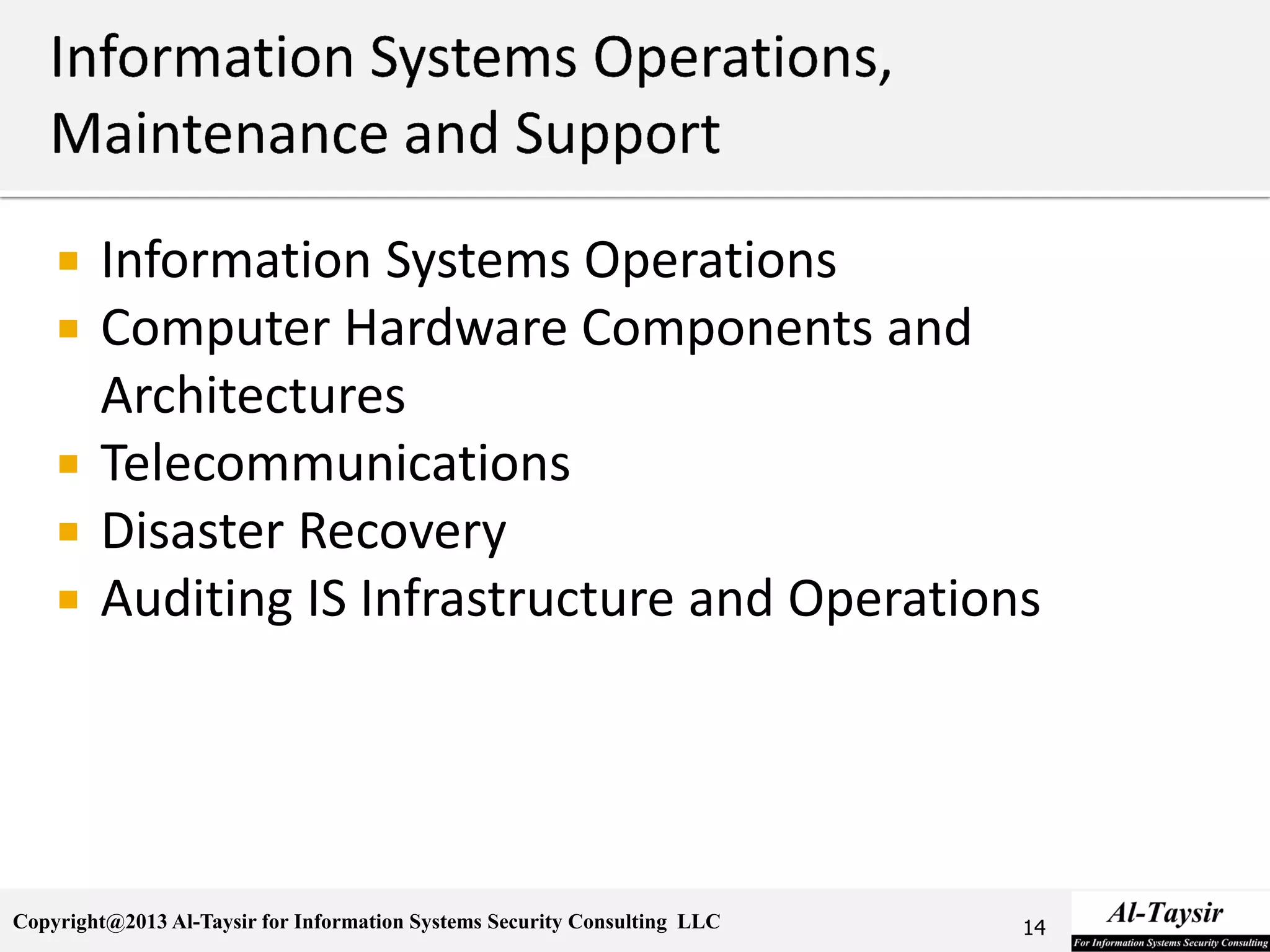
This document provides information about the Certified Information Systems Auditor (CISA) certification. It discusses what CISA is, the benefits of becoming CISA certified, and how to achieve the certification. The CISA certification focuses on controls for managing risks to business information systems. It covers five domains: auditing information systems, governance and management of IT, systems development and implementation, systems operations and support, and protection of information assets. The document outlines the study materials and examination process required to become CISA certified.