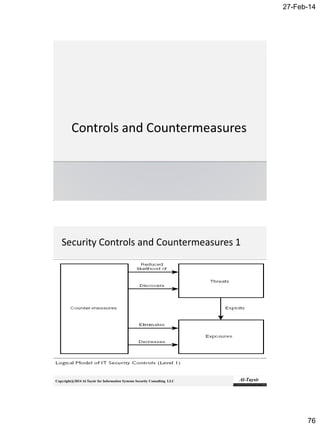
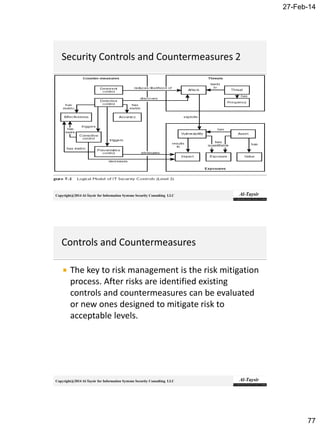
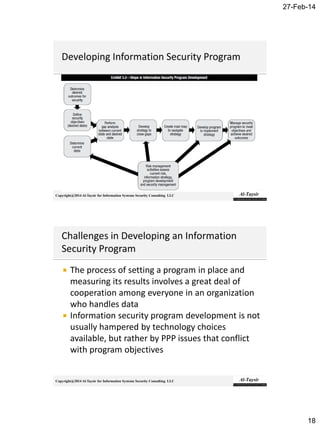
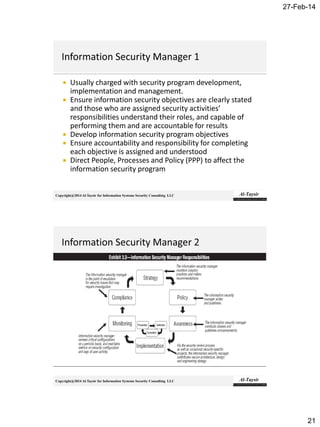
The document discusses the roles and responsibilities of an Information Security Manager (ISM). It explains that an ISM is responsible for developing, implementing, and managing an information security program to align with the organization's information security strategy and business objectives. This involves directing people, processes, and policies to identify controls, create control activities, and monitor control points. It also requires the ISM to ensure commitment from senior management and cooperation across organizational units. Effective information security programs require balancing security, cost, and business needs.


![27-Feb-14
3
Copyright@2014 Al-Taysir for Information Systems Security Consulting LLC
Establish and manage the information security
program in alignment with the information
security strategy.
The content area in this chapter will represent
approximately 25% of the CISM examination.
Copyright@2014 Al-Taysir for Information Systems Security Consulting LLC
Establish and maintain the information security program in
alignment with the information security strategy.
Ensure alignment between the information security
program and other business functions (for example,
human resources [HR], accounting, procurement and IT) to
support integration with business processes.
Identify, acquire, manage and define requirements for
internal and external resources to execute the information
security program.
Establish and maintain information security architectures
(people, process, technology) to execute the information
security program.](https://image.slidesharecdn.com/ch3cism2014-170826193807/85/Ch3-cism-2014-3-320.jpg)











































![27-Feb-14
53
Copyright@2014 Al-Taysir for Information Systems Security Consulting LLC
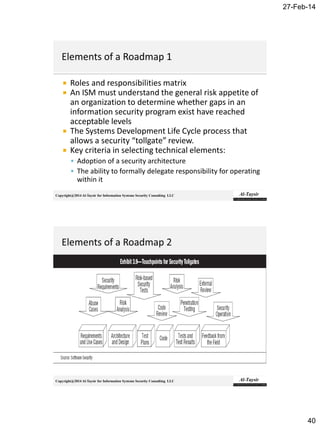
Should include some or all of the following:
Reference
▪ Project name/reference, origins/background/ current state
Context
▪ Business objectives/opportunities, business strategic alignment (priority)
Value Proposition
▪ Desired business outcomes, outcomes road map, business benefits (by
outcome), quantified benefits value, costs/ROI financial scenarios, risk/costs
of not proceeding, project risk (to project, benefits and business)
Focus
▪ Problem/solution scope, assumptions/constraints, options
identified/evaluated, size, scale and complexity assessment
Deliverables
▪ Outcomes, deliverables and benefits planned; organizational areas impacted
(internally and externally); key stakeholders
Copyright@2014 Al-Taysir for Information Systems Security Consulting LLC
Dependencies
▪ CSFs
Project metrics
▪ KGIs, KPIs
Workload
▪ Approach, phase/stage definitions (project change] activities,
technical delivery activities, workload estimate/breakdown, project
plan and schedule, critical path analysis)
Required resources
▪ Project leadership team, project governance team, team resources,
funding
Commitments (required)
▪ Project controls, review schedule, reporting processes, deliverables
schedule, financial budget/schedule](https://image.slidesharecdn.com/ch3cism2014-170826193807/85/Ch3-cism-2014-53-320.jpg)