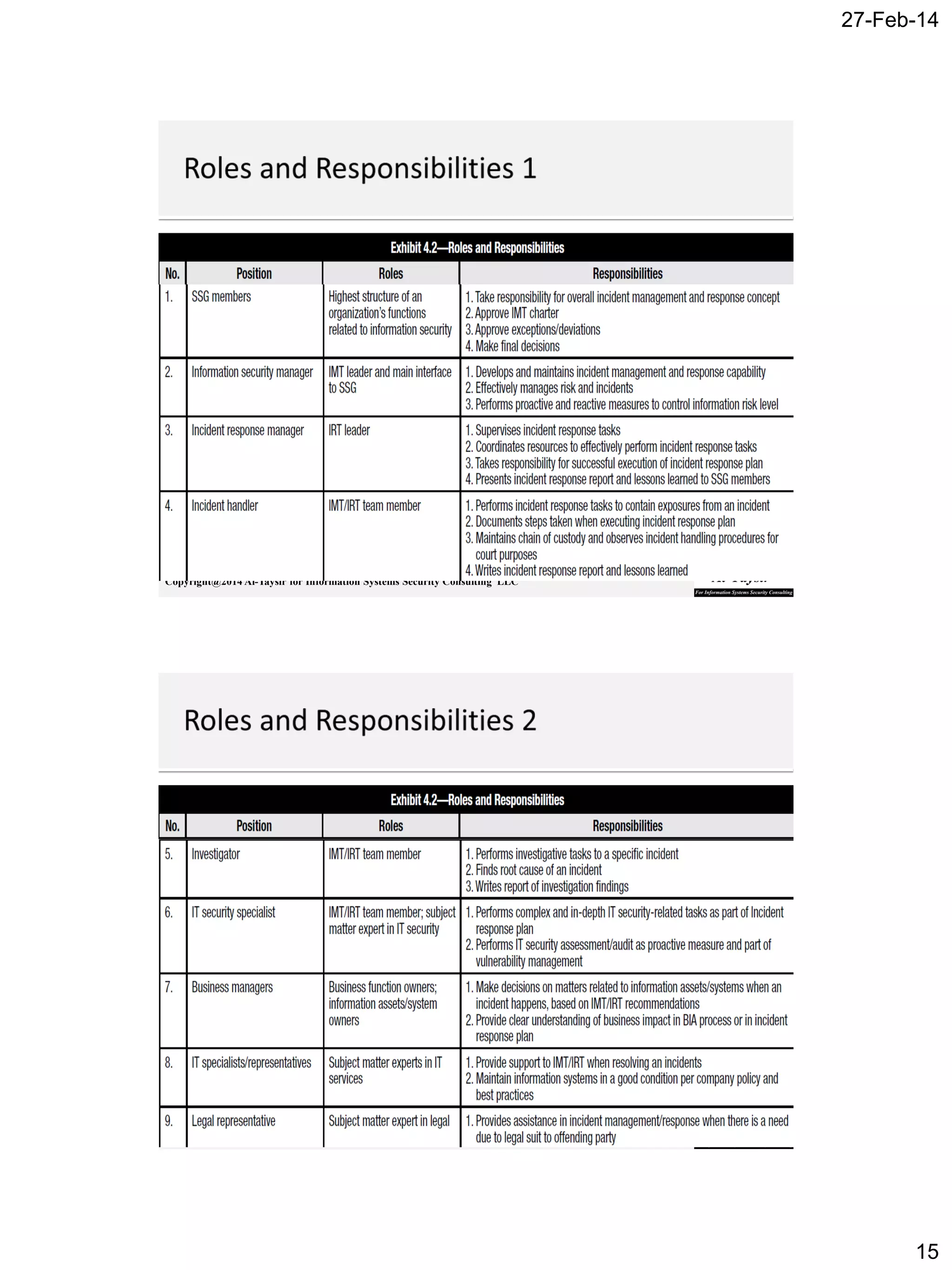
The document discusses incident management and response. It covers topics such as defining incidents and objectives of incident management, roles and responsibilities in incident response, developing incident response plans and procedures, testing and reviewing plans, and ensuring integration with business continuity and disaster recovery plans. The goal is to establish capabilities to effectively detect, investigate, respond to and recover from security incidents to minimize business impact.