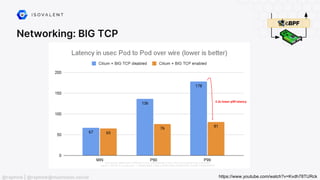
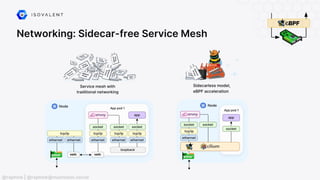
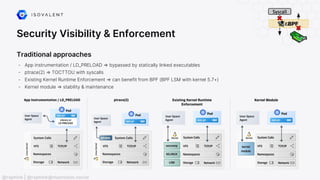
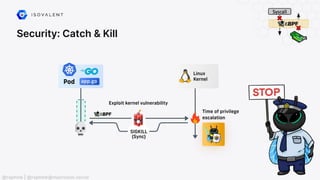
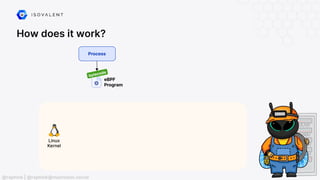
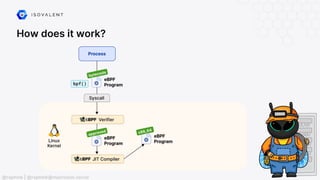
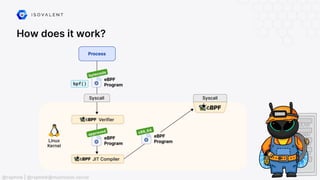
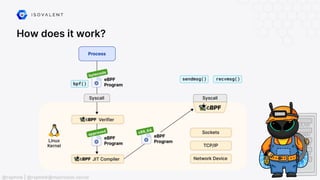
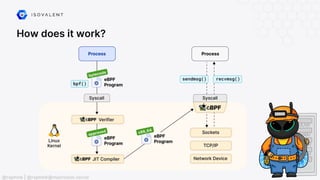
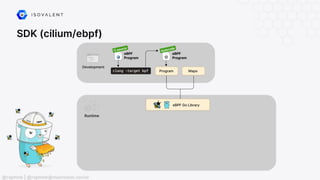
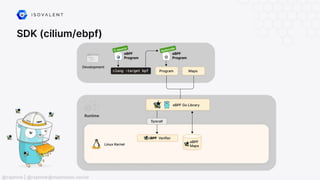
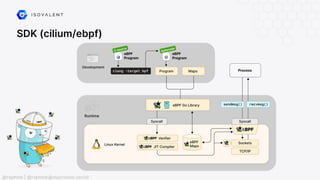
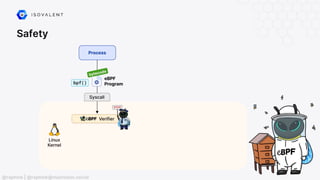
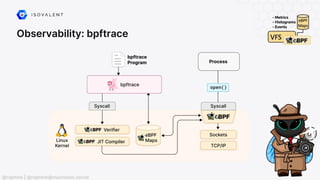
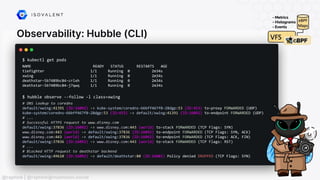
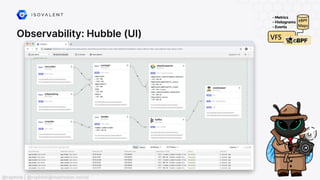
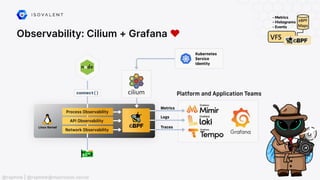
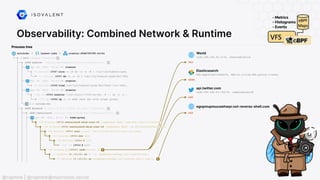
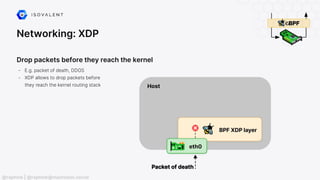
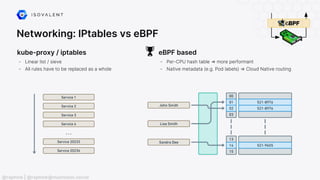
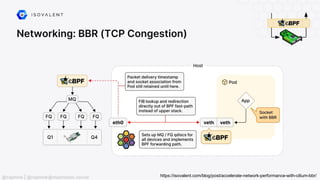
The document discusses eBPF (Extended Berkeley Packet Filter), highlighting its capabilities to enhance the Linux kernel for observability, networking, and security. It emphasizes eBPF's dynamic programmability, making it a powerful tool for performance improvements and real-time event handling. The document also mentions various projects and resources related to eBPF, such as Cilium and Hubble, showcasing practical applications and future developments.
























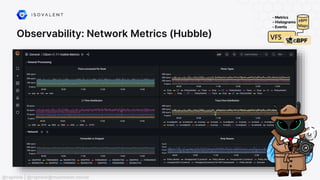
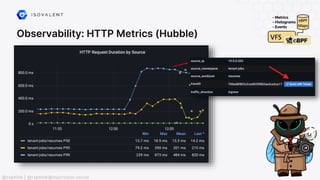
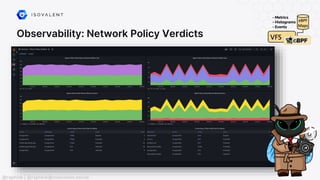
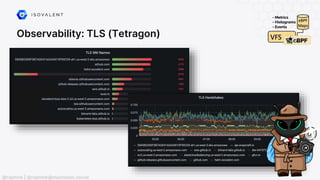



![Networking: NAT46/NAT64
IPv6 / IPv4 bridge
DNS64
NAT64
[64:ff9b::<z>] -> [<z>]
IPv6 Single Stack
K8s cluster
bar.com
A 4.3.2.1
DNS
bar.com
AAAA 64:ff9b::4.3.2.1
SYN 64:ff9b::4.3.2.1
IPv4 / Internet
SYN 4.3.2.1
ext. node
(Dual Stack)
https://www.youtube.com/watch?v=Kvdh78TURck
@raphink | @raphink@mastodon.social](https://image.slidesharecdn.com/cfgmgmtcamp2023ebpf-230207134243-65eb0532/85/Cfgmgmtcamp-2023-eBPF-Superpowers-58-320.jpg)