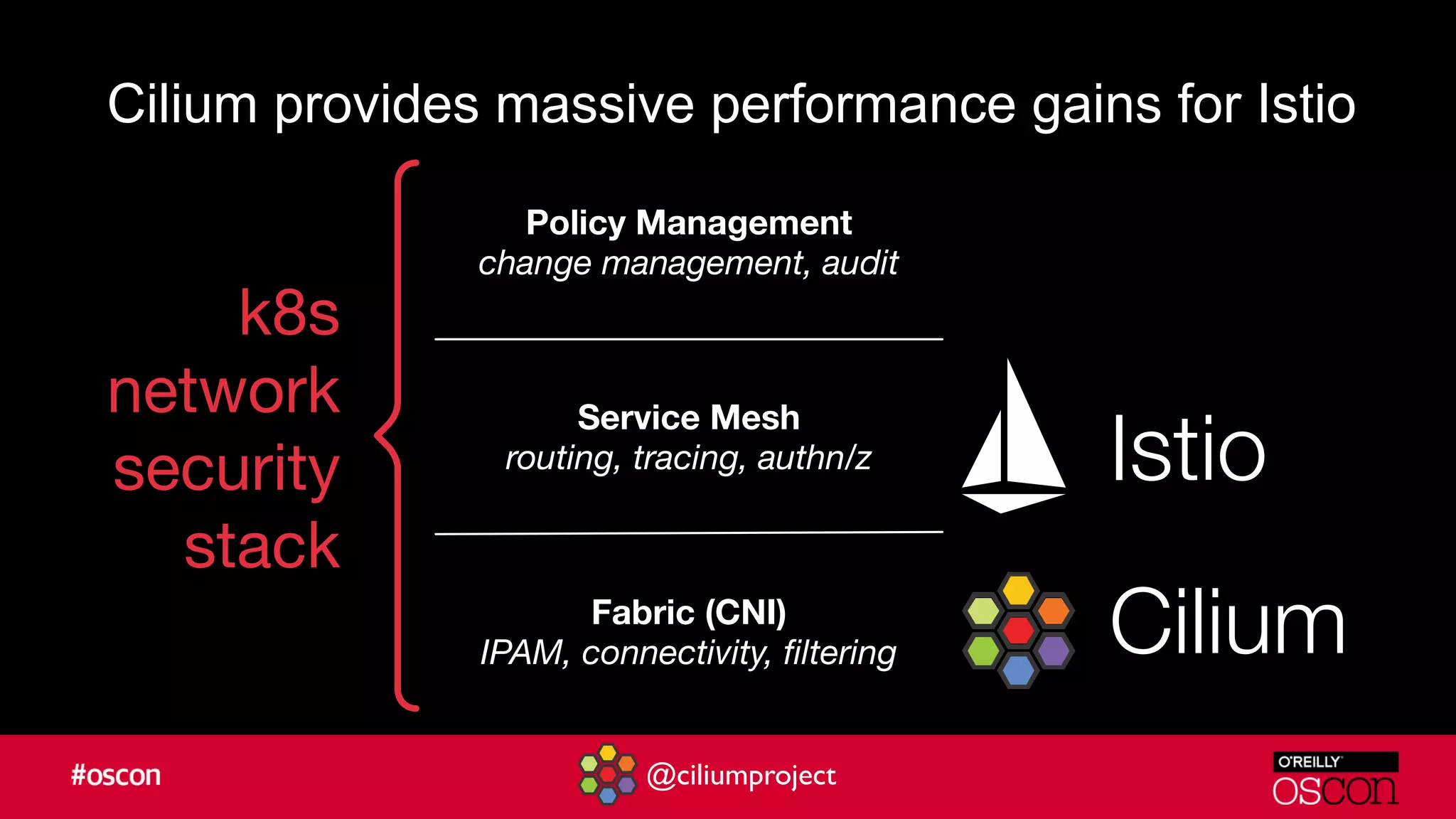
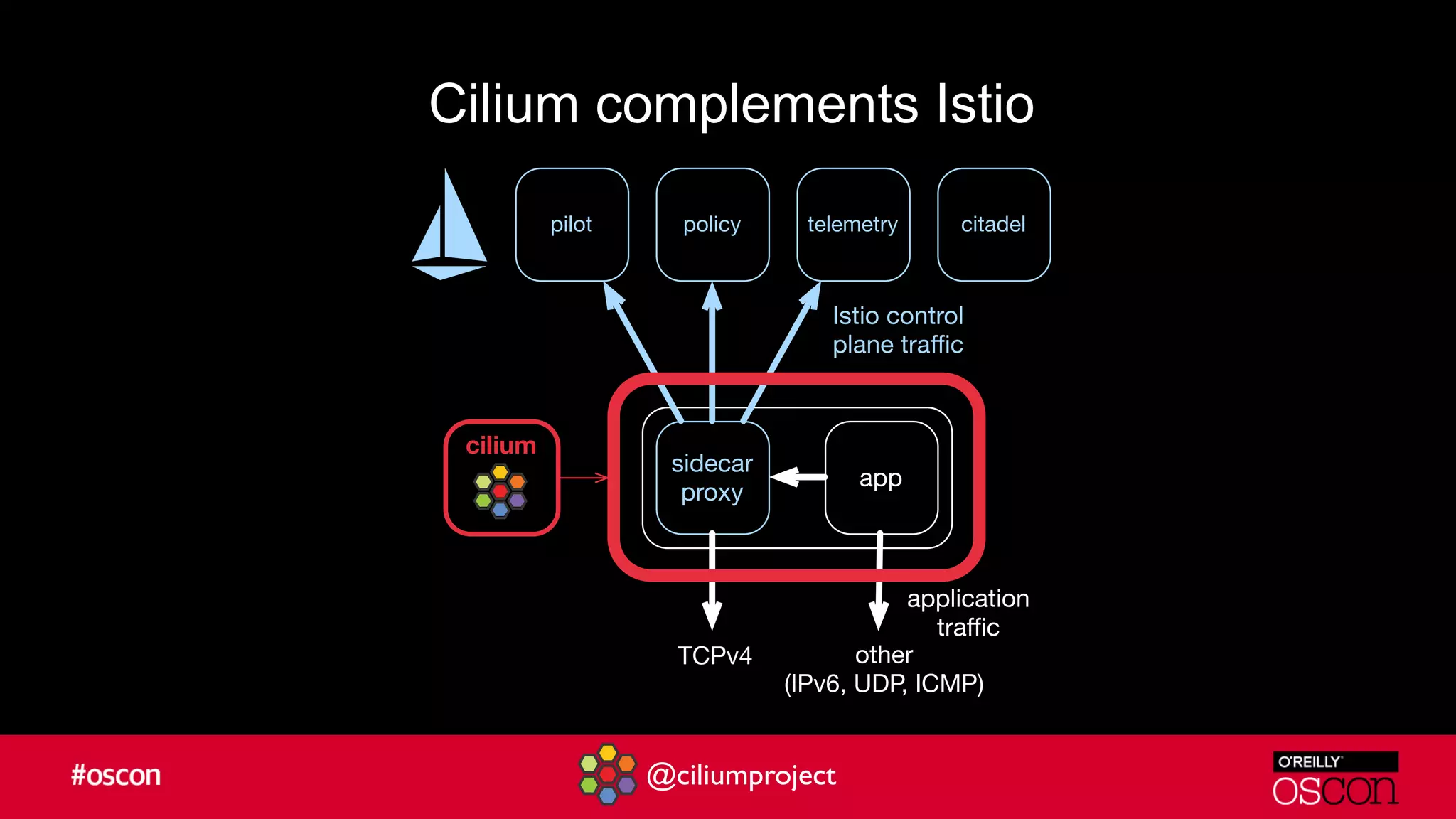
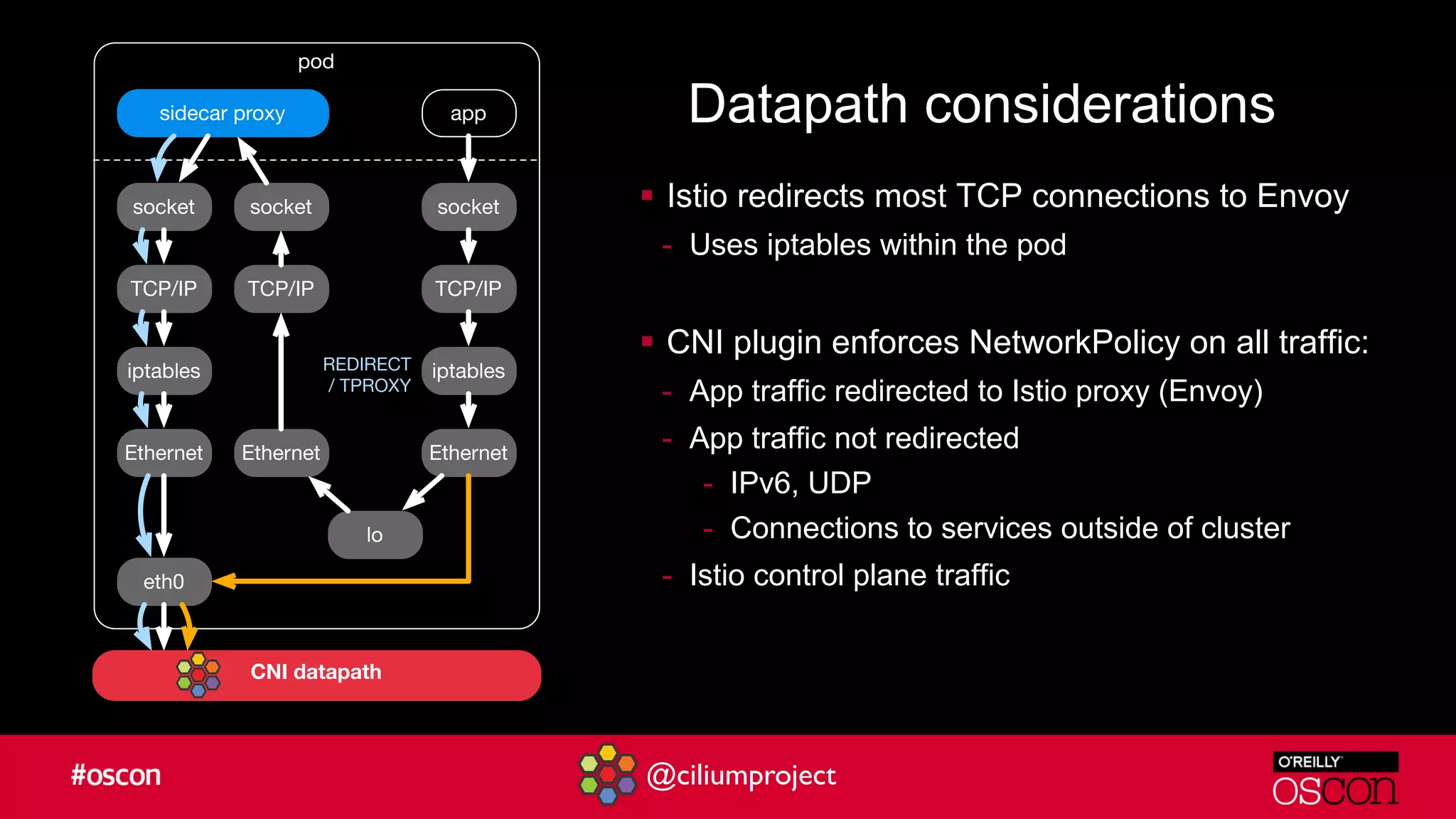
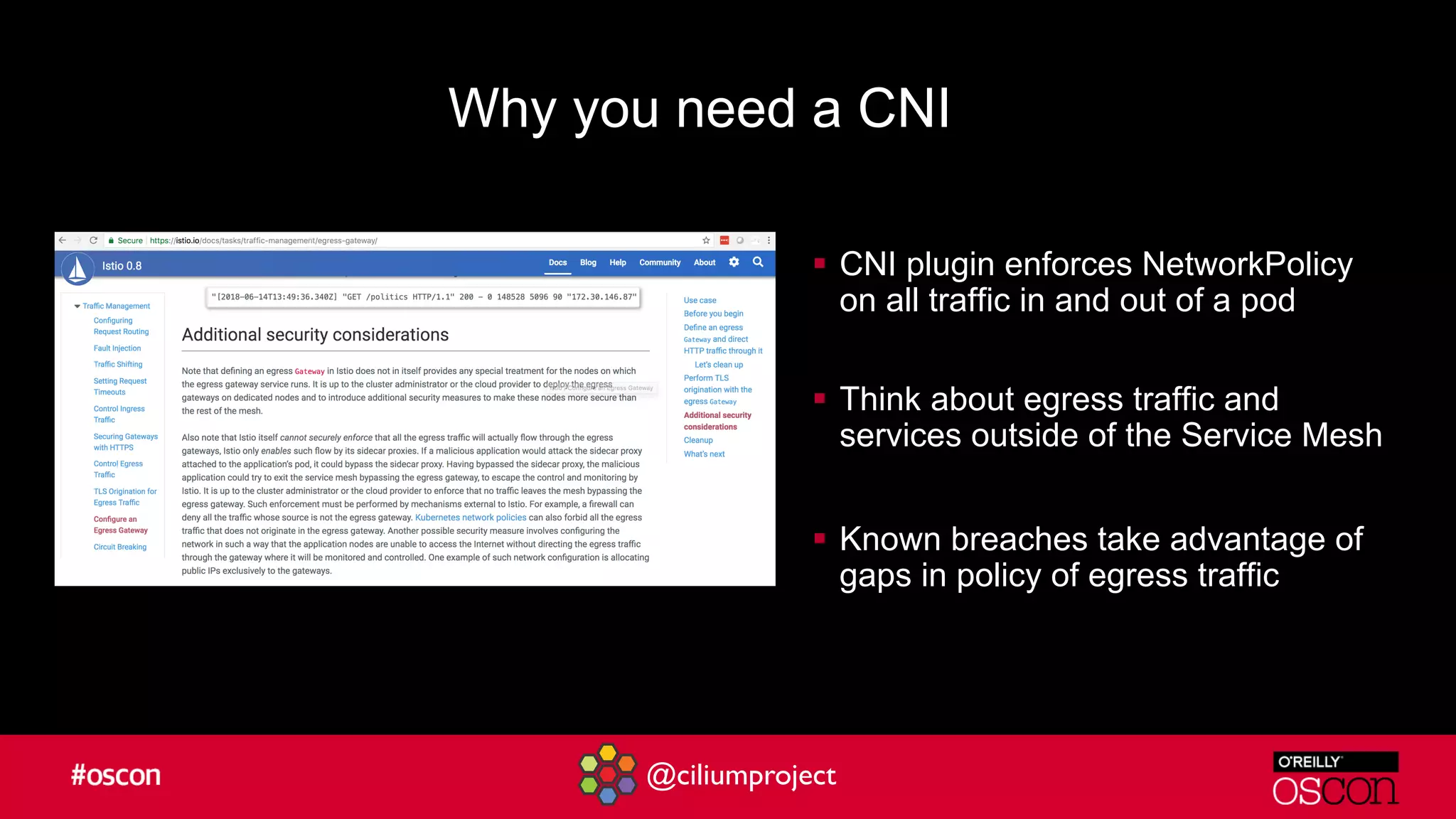
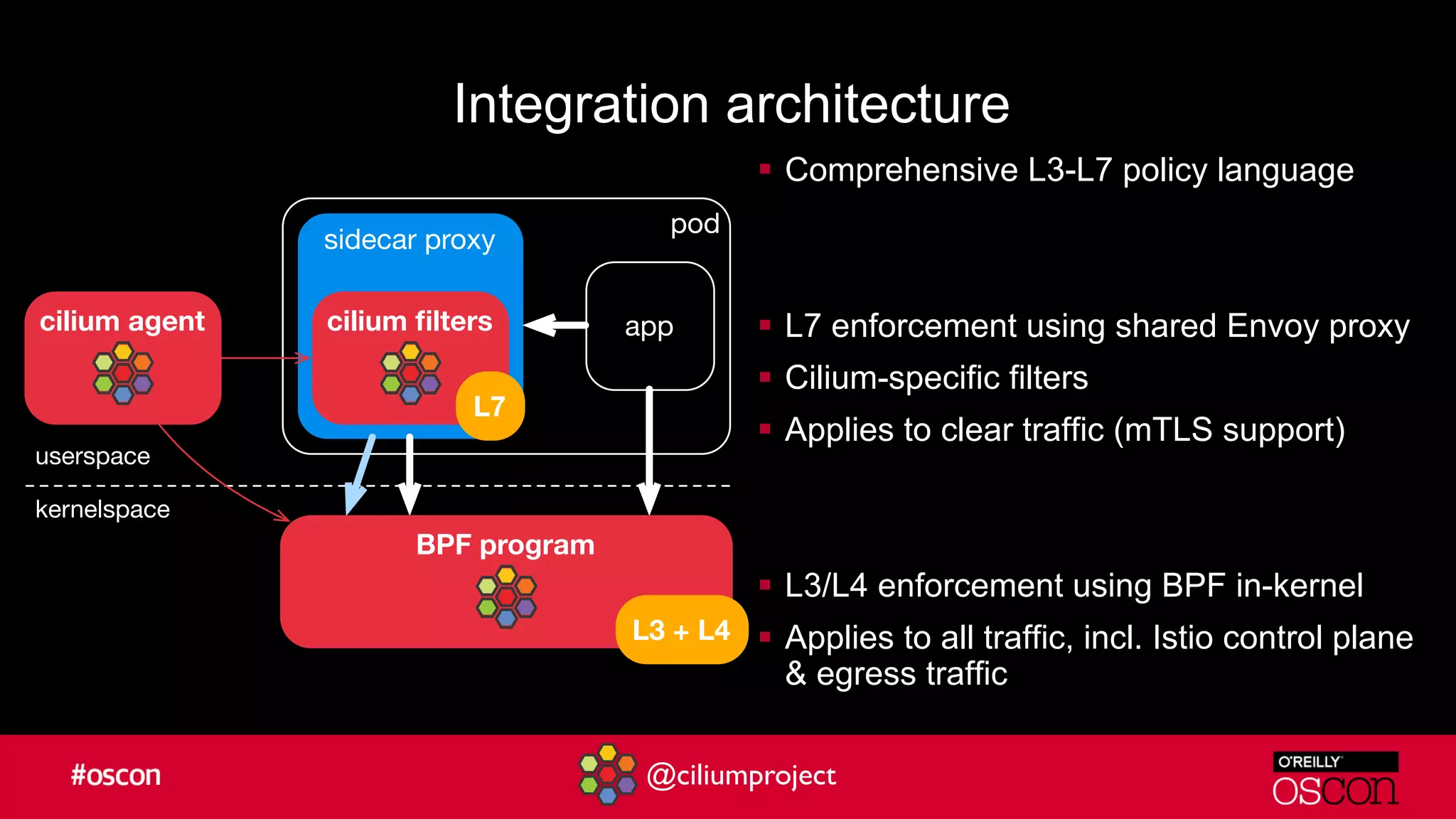
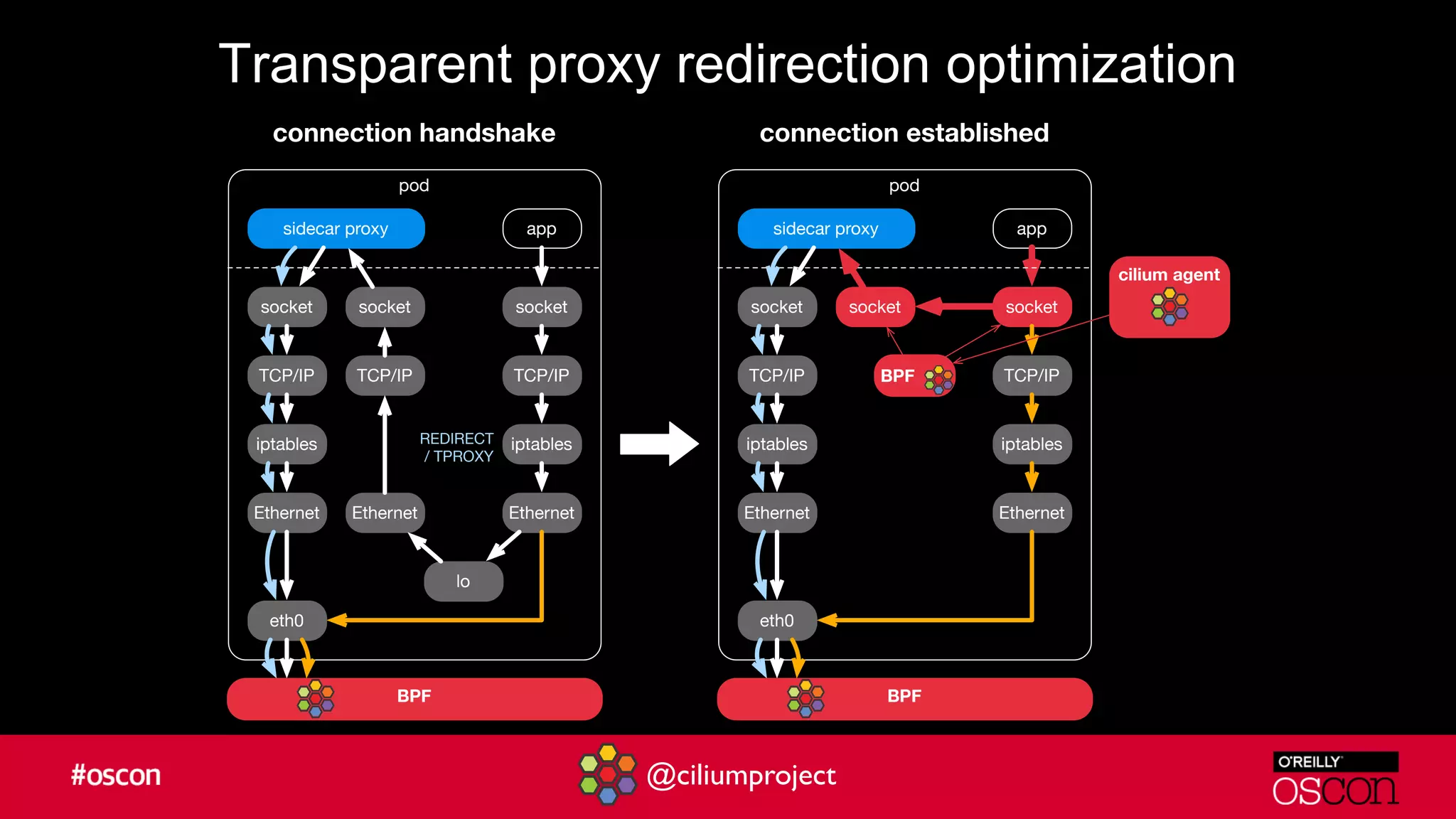
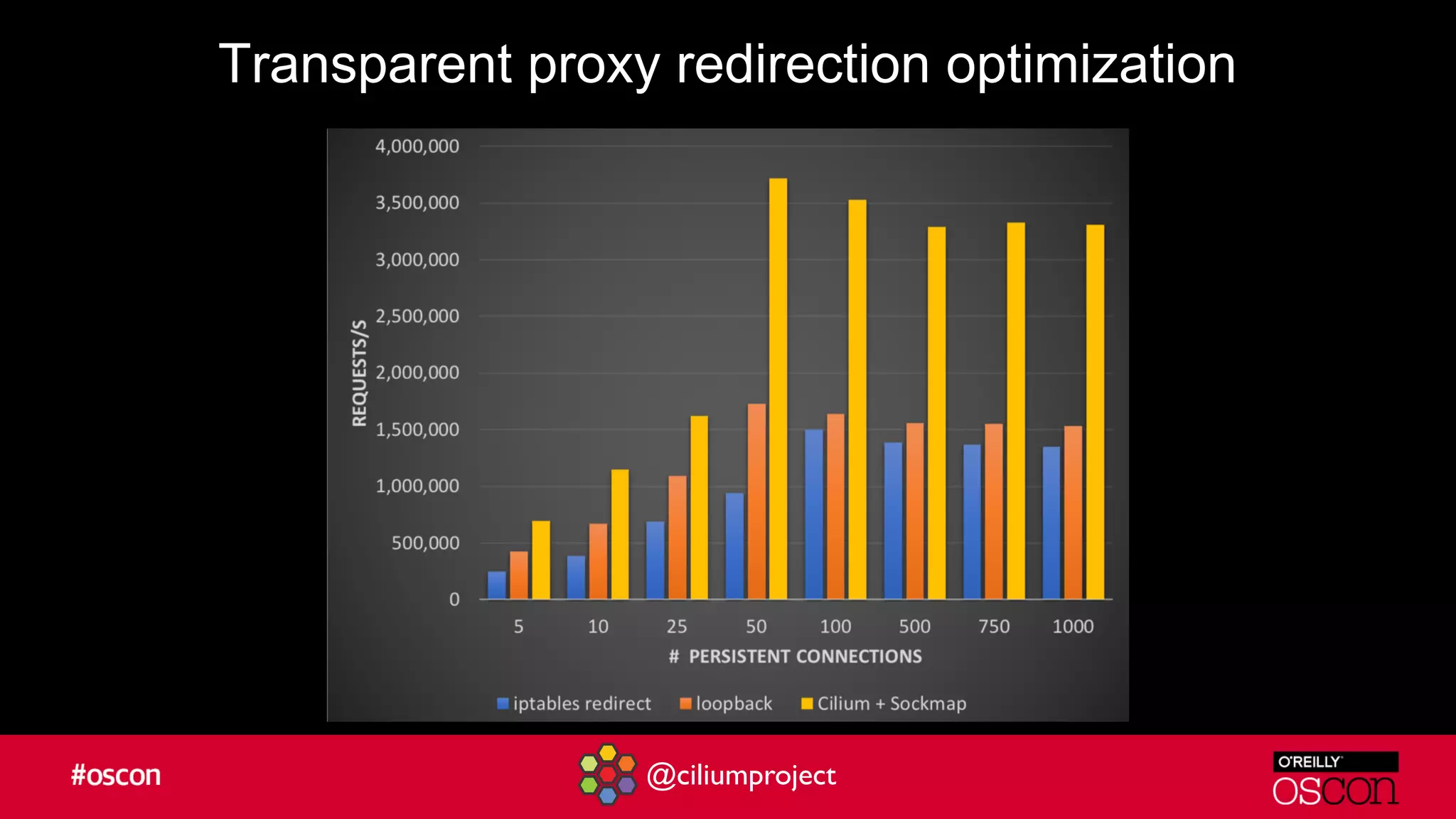
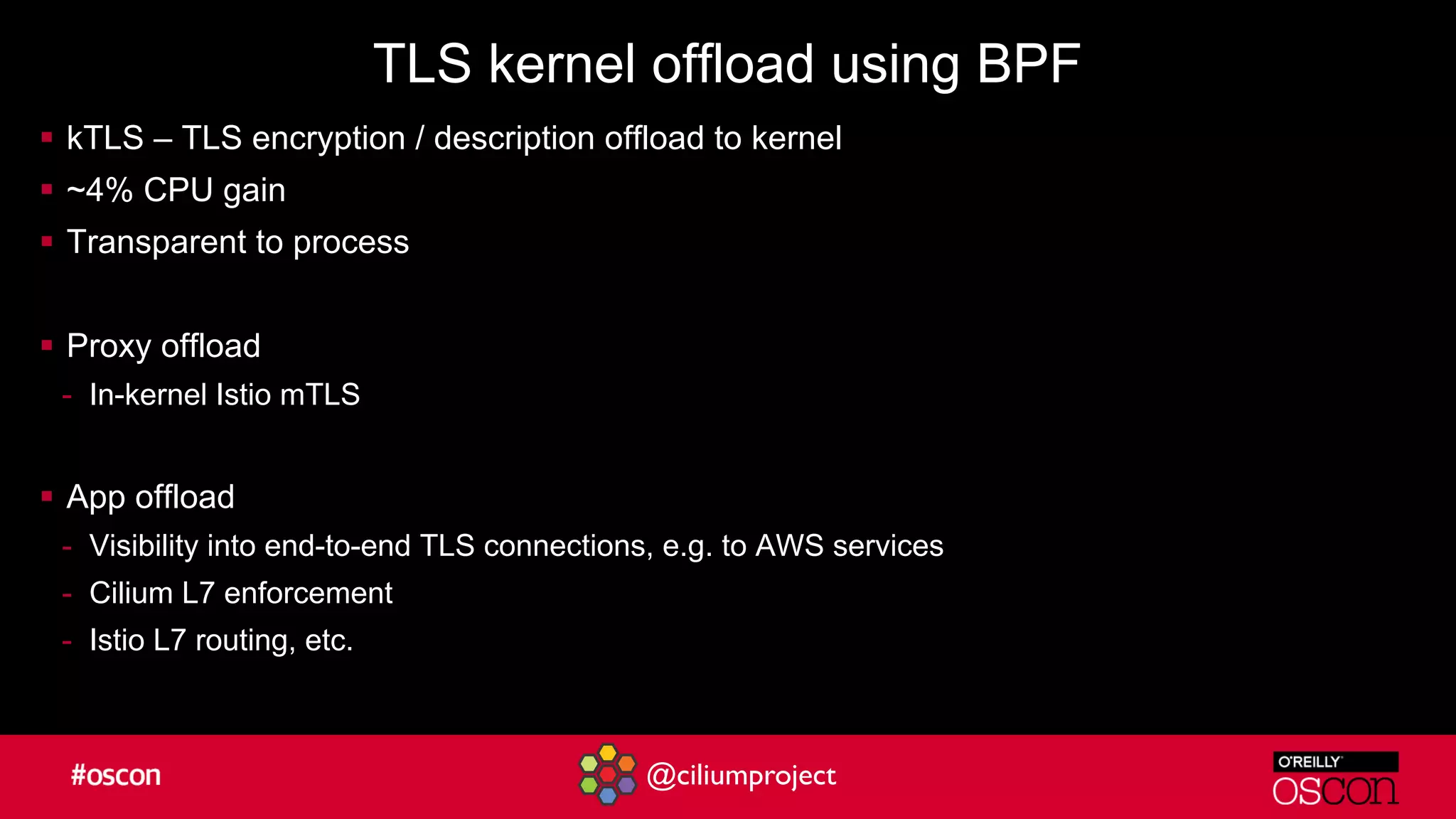
Cilium enhances Istio's performance by integrating with its service mesh to provide robust network security, policy management, and traffic optimization. It leverages BPF for efficient traffic enforcement and enables egress traffic management to prevent breaches. The document encourages users to implement Cilium with Istio for better efficiency and offers resources for getting started.