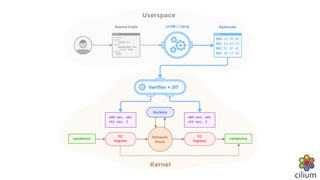
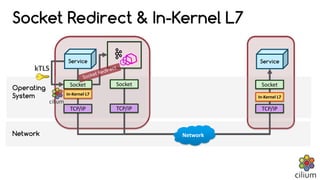
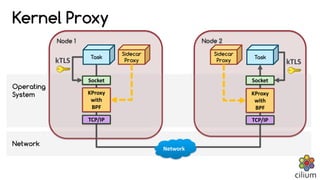
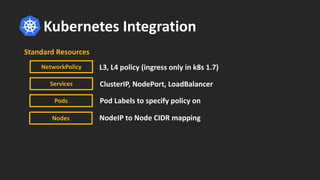
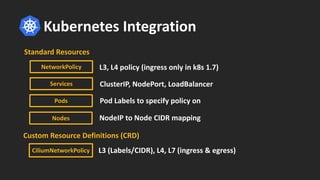
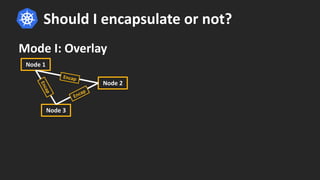
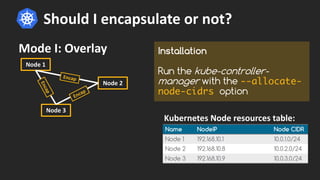
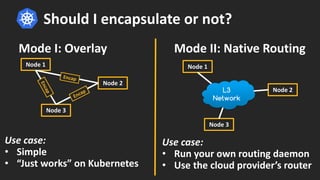
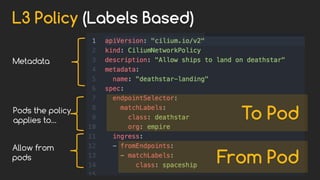
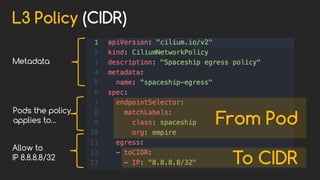
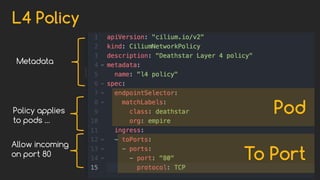
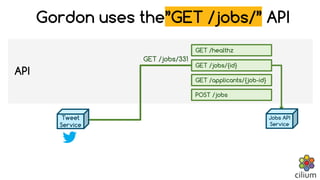
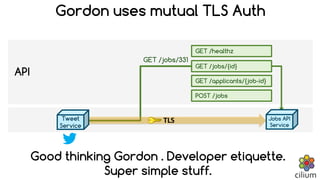
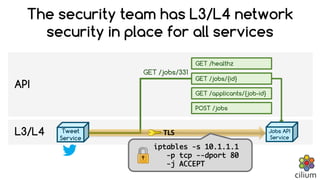
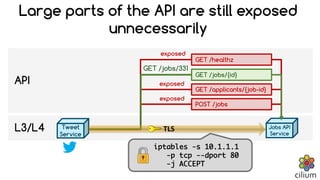
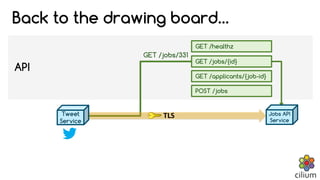
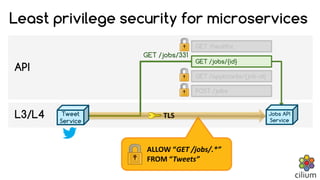
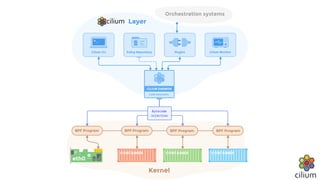
Cilium provides network security and visibility for microservices. It uses eBPF/XDP to provide fast and scalable networking and security controls at layers 3-7. Key features include identity-based firewalling, load balancing, and mutual TLS authentication between services. It integrates with Kubernetes to apply network policies using standard Kubernetes resources and custom CiliumNetworkPolicy resources for finer-grained control.










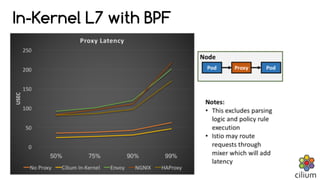
![Powers of BPF: XDP - DDoS mitigation
Metric iptables / ipset XDP
DDoS rate [packets/s] 11.6M 11.6M
Drop rate [packets/s] 7.1M 11.6M
Time to load rules [time] 3 min 20 sec 31 sec
Latency under load [ms] 2.3ms 0.1ms
Throughput under DDoS [Gbit/s] 0.014 6.5
Requests/s under DDoS [kReq/s] 0.28 82.8
Sender: Send 64B packets as fast as possible è Receiver: Drop as fast as possible
Source: Daniel Borkmann’s presentation yesterday:
http://schd.ws/hosted_files/ossna2017/da/BPFandXDP.pdf](https://image.slidesharecdn.com/ciliummeetupslides-180306014238/85/Cilium-API-aware-Networking-and-Security-for-Containers-based-on-BPF-21-320.jpg)