Check Point Sandblast provides comprehensive protection from modern Internet threats. It uses a combination of techniques including IPS, antivirus, anti-bot, threat extraction, and advanced sandboxing to detect known and unknown threats. The advanced sandboxing analyzes files at the CPU level to provide highly effective detection of evasive malware. Check Point has consistently received recommendations and top ratings from independent testing organizations for its security effectiveness.
![©2016 Check Point Software Technologies Ltd. 1©2015 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals
Olexandr Rapp | orapp@checkpoint.com
Security Engineer - CIS
Комплексная защита от
современных Интернет угроз
с помощью решения
Check Point Sandblast](https://image.slidesharecdn.com/checkpointsandblast-161031085040/75/Check-point-sandblast-1-2048.jpg)


![©2016 Check Point Software Technologies Ltd. 4
Key Technology
[Restricted] ONLY for designated groups and individuals
Unified
Management
Network Security
Next Generation
Threat Prevention
Mobile and
Endpoint
Security
Virtualized Security
/ Cloud Security](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-4-320.jpg)

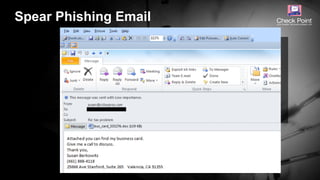
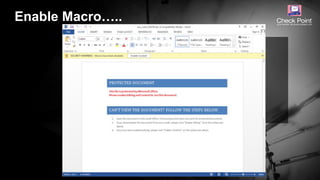
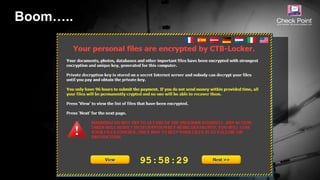
![©2016 Check Point Software Technologies Ltd. 9
• Encrypts local content rendering user files unusable
• In many cases then encrypts network storage
o Impacting many more users
• Once encrypted, almost no chance to decrypt yourself
• Two choices
o Reimage and restore, losing work since last backup
o Pay up
[Protected] Non-confidential content
Damage and Response](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-9-320.jpg)
![©2015 Check Point Software Technologies Ltd. 10
How are these bypassing AV?
Exploit kits turn known
into unknown
So long bankers…hello crypto lockers
[Protected] Non-confidential content
Polymorphic changes
Packing and Obfuscation](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-10-320.jpg)

![©2016 Check Point Software Technologies Ltd. 13[Restricted] ONLY for designated groups and individuals
IPS
Anti Virus
SandBlast
Anti Bot
SandBlast Agent
Комплексный подход
SECURITY GATEWAY](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-12-320.jpg)
![©2016 Check Point Software Technologies Ltd. 14[Restricted] ONLY for designated groups and individuals
Check Point IPS](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-13-320.jpg)
![©2016 Check Point Software Technologies Ltd. 15[Protected] Non-confidential content
Check Point IPS
Prevents Exploits of Known Vulnerabilities
Enforce Protocol
Specifications
Detect Protocol
Anomalies and Attacks
Signature based
Engine](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-14-320.jpg)
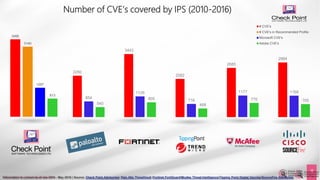

![©2016 Check Point Software Technologies Ltd. 18[Restricted] ONLY for designated groups and individuals
Check Point
Network AV](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-17-320.jpg)
![©2016 Check Point Software Technologies Ltd. 19[Protected] Non-confidential content
Check Point Anti-Virus
Blocks Download of Known Malware
Signatures and MD5 based
Engines
Malware Feeds Blocks Access to Malware
Sites](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-18-320.jpg)
![©2016 Check Point Software Technologies Ltd. 20[Restricted] ONLY for designated groups and individuals
Check Point
Network Anti Bot](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-19-320.jpg)
![©2016 Check Point Software Technologies Ltd. 21
Stop Traffic to
Remote Operators
Multi-tier
Discovery
Check Point Anti-Bot
[Protected] Non-confidential content
Blocks Bot Communication
PREVENT
Bot Damage
IDENTIFY
Bot infected
Devices
Reputation Patterns SPAM](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-20-320.jpg)
![©2016 Check Point Software Technologies Ltd. 22[Protected] Non-confidential content](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-21-320.jpg)


![©2016 Check Point Software Technologies Ltd. 25[Restricted] ONLY for designated groups and individuals
.cleaned.doc.pdf
Less than 1% of users need the original
For those who do, it’s a simple click
Original becomes available after found clean by the sandbox](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-24-320.jpg)
![©2016 Check Point Software Technologies Ltd. 26[Restricted] ONLY for designated groups and individuals
Examine:
• System Registry
• Network Connections
• File System Activity
• System Processes
Open and detonate any files
THE TRADITIONAL SANDBOX
HOW IT WORKS (1st Generation)
Watch for telltale signs of malicious code
at the Operating System level
TH R E AT C O N TAI N E D](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-25-320.jpg)
![©2015 Check Point Software Technologies Ltd. 28
28©2014 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved.
©2010 Check Point Software Technologies Ltd. | [Unrestricted] For everyone |©2010 Check Point Software Technologies Ltd. | [Unrestricted] For everyone |
A
B C
D
E
F
CPU OPERATION
Normal execution](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-27-320.jpg)
![©2015 Check Point Software Technologies Ltd. 29
29©2014 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved.
©2010 Check Point Software Technologies Ltd. | [Unrestricted] For everyone |©2010 Check Point Software Technologies Ltd. | [Unrestricted] For everyone |
ROP EXPLOIT
(Return Oriented
Programming)
A
B C
D
E
F2
1
3
4
5
6 Hijacks small pieces
of legitimate code
from the memory
and manipulates
the CPU to load and
execute the actual
malware.](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-28-320.jpg)
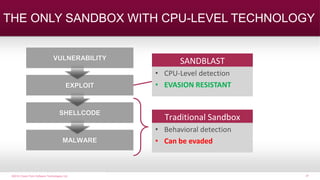
![©2016 Check Point Software Technologies Ltd. 30[Protected] Non-confidential content
• Highest catch rate
• Evasion-resistant
• Efficient and fast
• Unique to Check Point
CPU-LEVEL &
OS-LEVEL
EXPLOIT
DETECTION](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-29-320.jpg)
![©2015 Check Point Software Technologies Ltd. 32
32©2014 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved.
©2010 Check Point Software Technologies Ltd. | [Unrestricted] For everyone | 32©2014 Check Point Software Technologies Ltd.
14,000,000+
FILES INSPECTION / WEEK
February 2016
THREAT EMULATION
CLOUD SERVICE:
55,000+
UNKNOWN MALWARE
DETECTION / WEEK
February 2016
We have the experience!](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-31-320.jpg)
![©2016 Check Point Software Technologies Ltd. 33[Restricted] ONLY for designated groups and individuals
Block UNKNOWN and ZERO-DAY ATTACKS in Microsoft Office 365™
SANDBLAST CLOUD PROTECTS CLOUD-BASED EMAIL
• Advanced Threat Prevention for Office 365
• Fast and Transparent User Experience
• Easy to Deploy and Manage
OFFICE 365 PROTECTION](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-32-320.jpg)

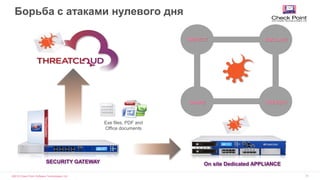
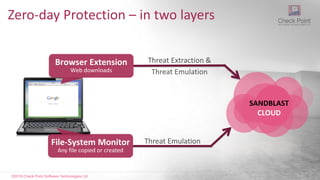
![©2016 Check Point Software Technologies Ltd. 35
SANDBLAST
CLOUD
Eliminate Zero Day Malware at the Endpoint
[Restricted] ONLY for designated groups and individuals
Web downloads sent
to SandBlast cloud1 Sanitized version
delivered promptly2 Original file emulated
in the background3](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-34-320.jpg)
![©2016 Check Point Software Technologies Ltd. 36
CONVERT to PDF for best security,
or SANITIZE keeping the original
format
Instant Protection for Web Downloads
[Restricted] ONLY for designated groups and individuals](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-35-320.jpg)
![©2016 Check Point Software Technologies Ltd. 37
Access to the Original File
[Restricted] ONLY for designated groups and individuals
Only After Threat Emulation
when verdict is benign
Self-Catered
No Helpdesk Overhead](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-36-320.jpg)
![©2016 Check Point Software Technologies Ltd. 40
Collect Forensics Data and Trigger Report
Generation
[Restricted] ONLY for designated groups and individuals
FORENSICS data
continuously collected
from various OS sensors1Report generation
automatically triggered
upon detection of network
events or 3rd party AV
2
Digested incident
report sent to
SmartEvent4Processes
Registry
Files
Network
Advanced
algorithms analyze
raw forensics data3](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-38-320.jpg)

![©2016 Check Point Software Technologies Ltd.
SUMMARY
[Protected] Non-confidential content](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-40-320.jpg)


![©2016 Check Point Software Technologies Ltd. 46©2015 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups and individuals
Olexandr Rapp | orapp@checkpoint.com
Security Engineer – CIS
QUESTIONS](https://image.slidesharecdn.com/checkpointsandblast-161031085040/85/Check-point-sandblast-43-320.jpg)