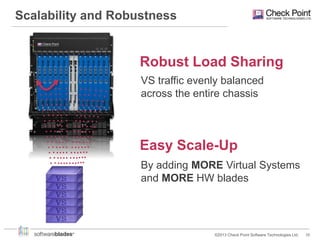
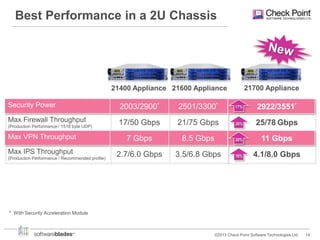
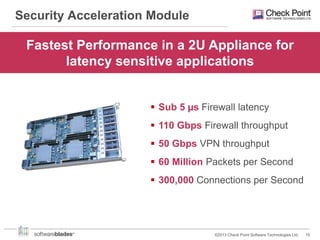
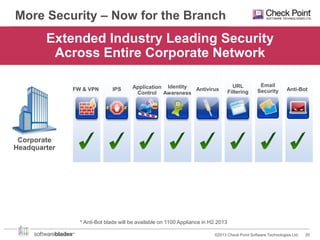
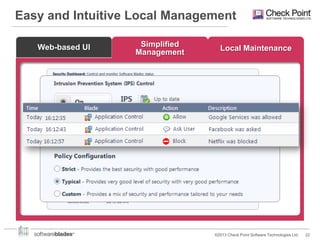
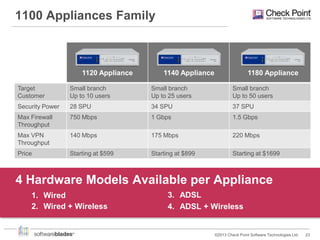
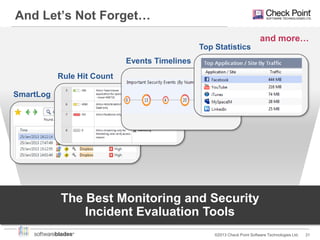
Check Point offers security solutions for enterprises moving from branches to data centers. They provide next generation firewalls, virtual systems, and software blades that deliver high performance security. Their 61000 and 21000 appliances include features like load balancing, customized security policies, and high throughput. For branches, the 1100 appliances extend enterprise-level security with local management. Check Point also provides a compliance blade and security monitoring tools to give organizations full visibility over their security posture and compliance.

![My Enterprise Security
[Restricted] ONLY for designated groups and individuals
©2013 Check Point Software Technologies Ltd.
3](https://image.slidesharecdn.com/securingngenterprise-131204085125-phpapp01/85/Check-Point-From-Branch-to-Data-Center-3-320.jpg)