The document proposes a blockchain-based system to validate digital certificates. Some key points:
- The existing system of certificate issuance has security and forgery issues due to the lack of an effective verification mechanism.
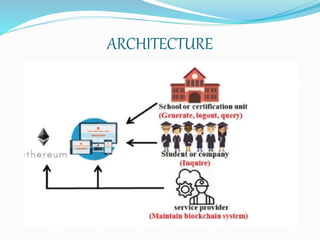
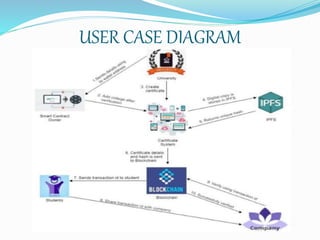
- The proposed system uses blockchain to securely store certificate data and hashes on an immutable ledger. It issues, stores, and allows retrieval and verification of certificates through a common portal.
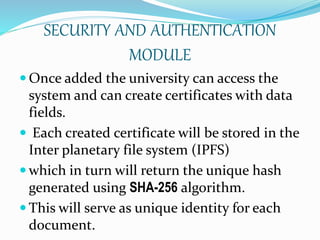
- The system has modules for certificate upload, security/authentication via hashing and digital signatures, and verification of certificates by anyone using the transaction ID and hash stored on the blockchain.
- This new system reduces the possibilities of forgery and ensures security, validity, and confidentiality of graduation certificates.
















![REFERENCE
[1] A. M. Antonopoulos, Mastering Bitcoin: Unlocking
Digital. Sebastopol, CA, USA: O’Reilly Media, 2015.
[2] C. K. Wong and S, S. Lam “Digital signatures for flows
and multicasts”, WEEE/ACM Transactions on
Networking,7(4):504-513,1999.
[3] M. Carvalho and R. Ford, “Moving-target defenses for
computer networks,”IEEE Security & Privacy, vol. 12, no.
2, pp. 73-76, Mar.- Apr.2014.
[4] M. Warasart and P. Kuacharoen,
“Paper-based Document Authentication
using Digital Signature and QR Code,” no. Iccet, 2012.](https://image.slidesharecdn.com/batch6p-230528112641-f9ddbdc3/85/Certificate-Validation-using-block-chain-21-320.jpg)
