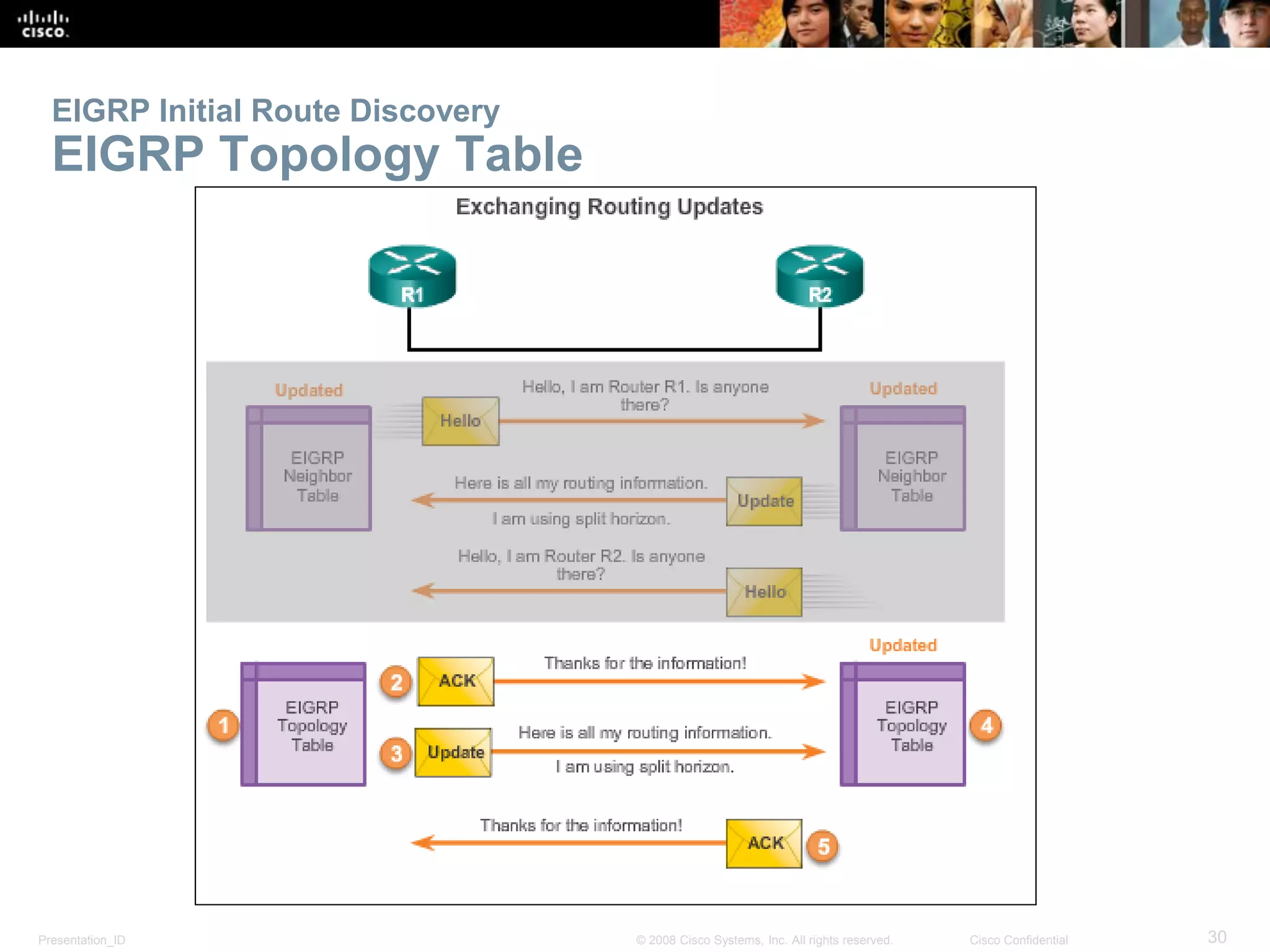
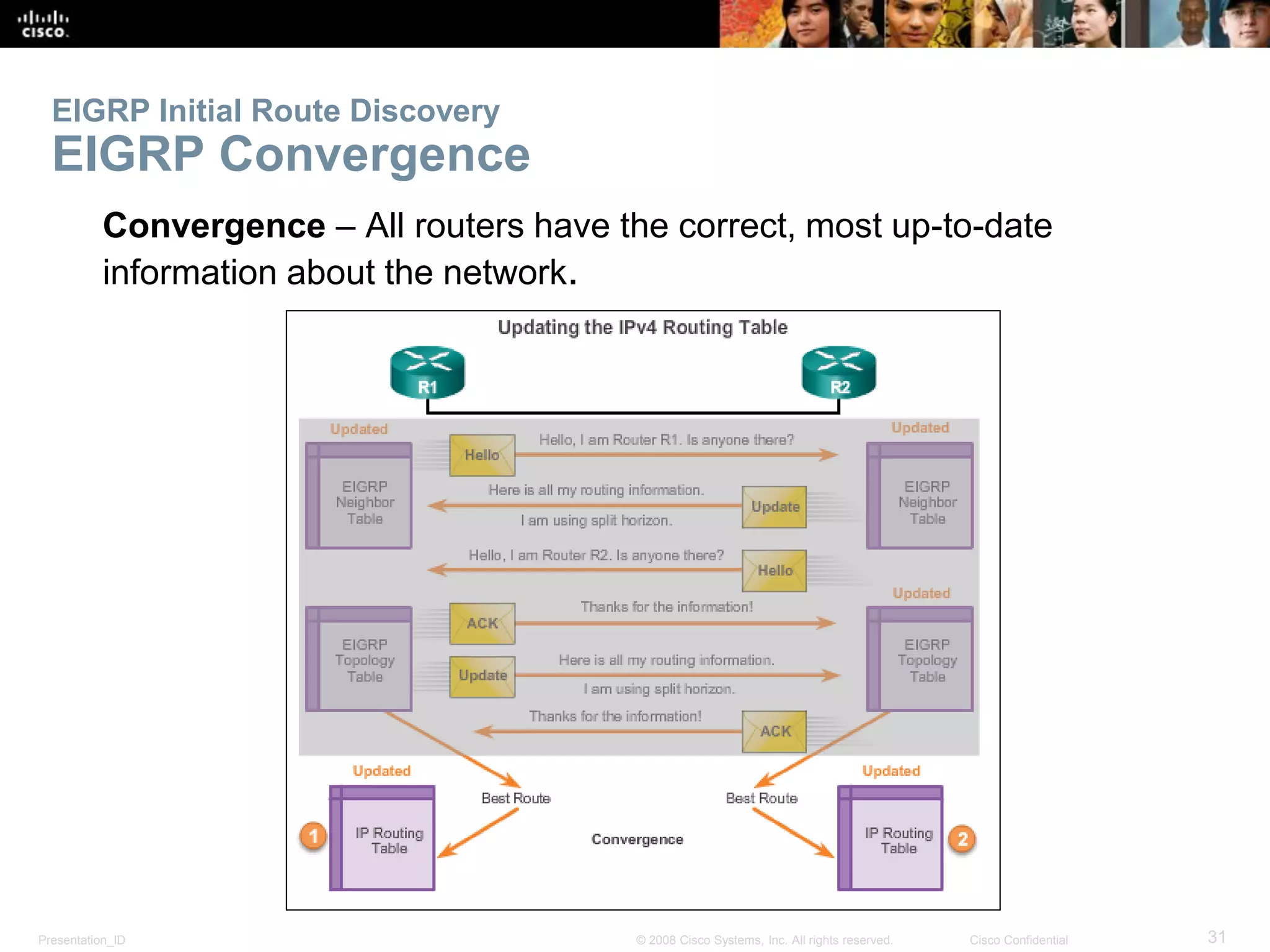
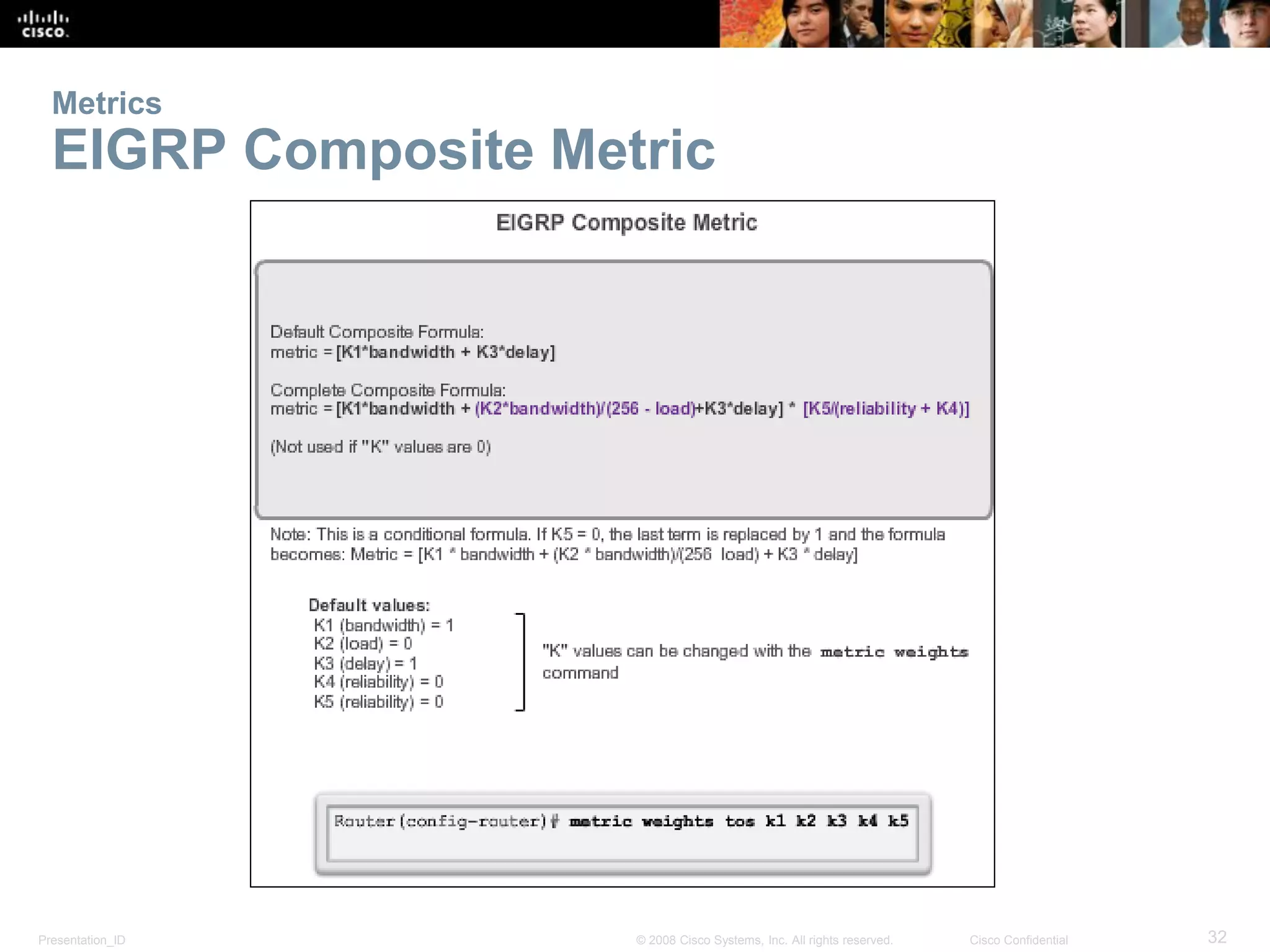
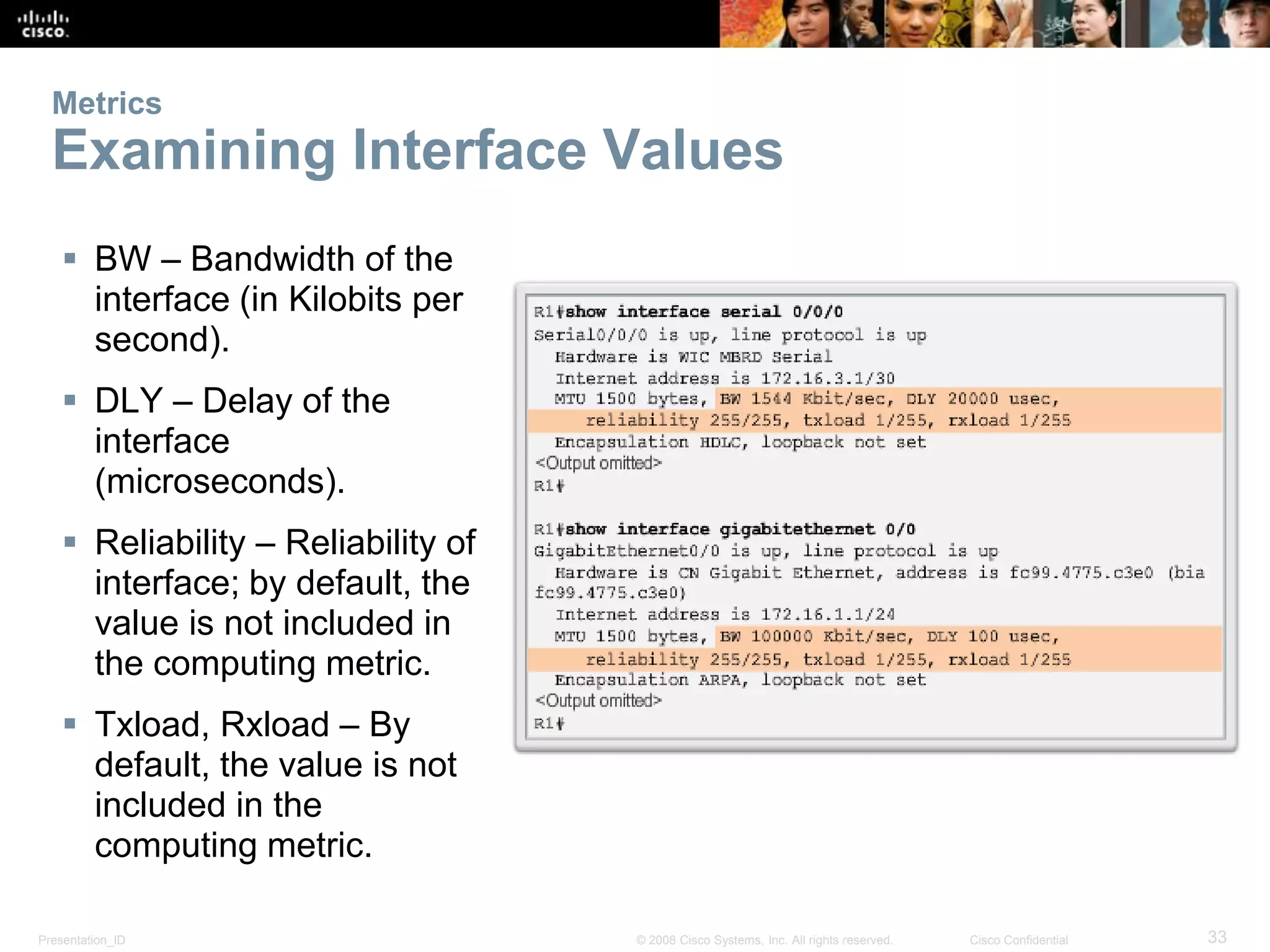
The document provides an overview of the Enhanced Interior Gateway Routing Protocol (EIGRP), detailing its features, packet types, and operational mechanics for both IPv4 and IPv6. It explains the configuration processes, including the use of network commands and passive interfaces, as well as the principles behind the Diffusing Update Algorithm (DUAL) used for route calculation. Key concepts include establishing neighbor adjacencies, calculating composite metrics, and supporting different layer 3 protocols, with a focus on reliability and efficient updates.










![Presentation_ID 23© 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential
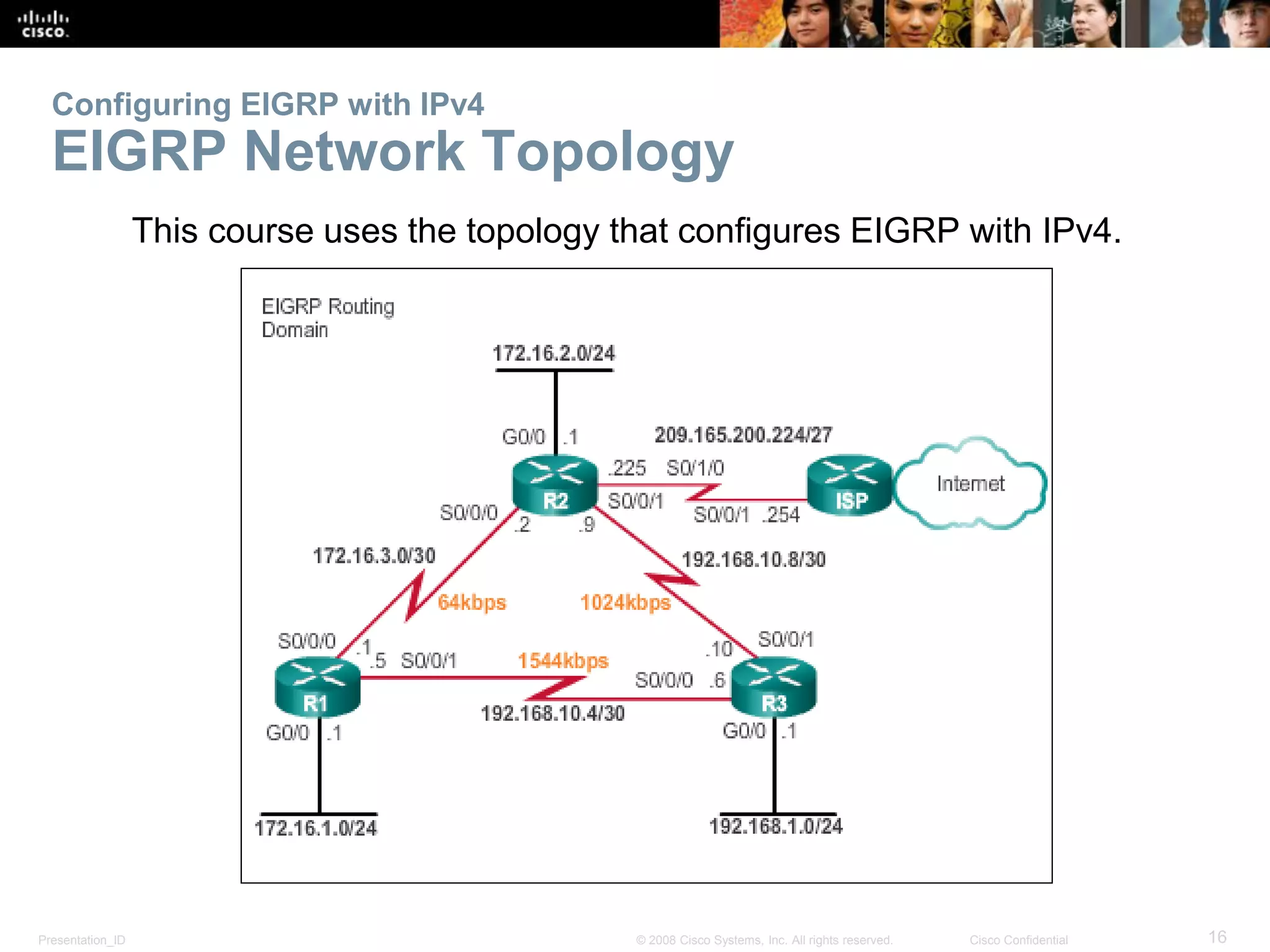
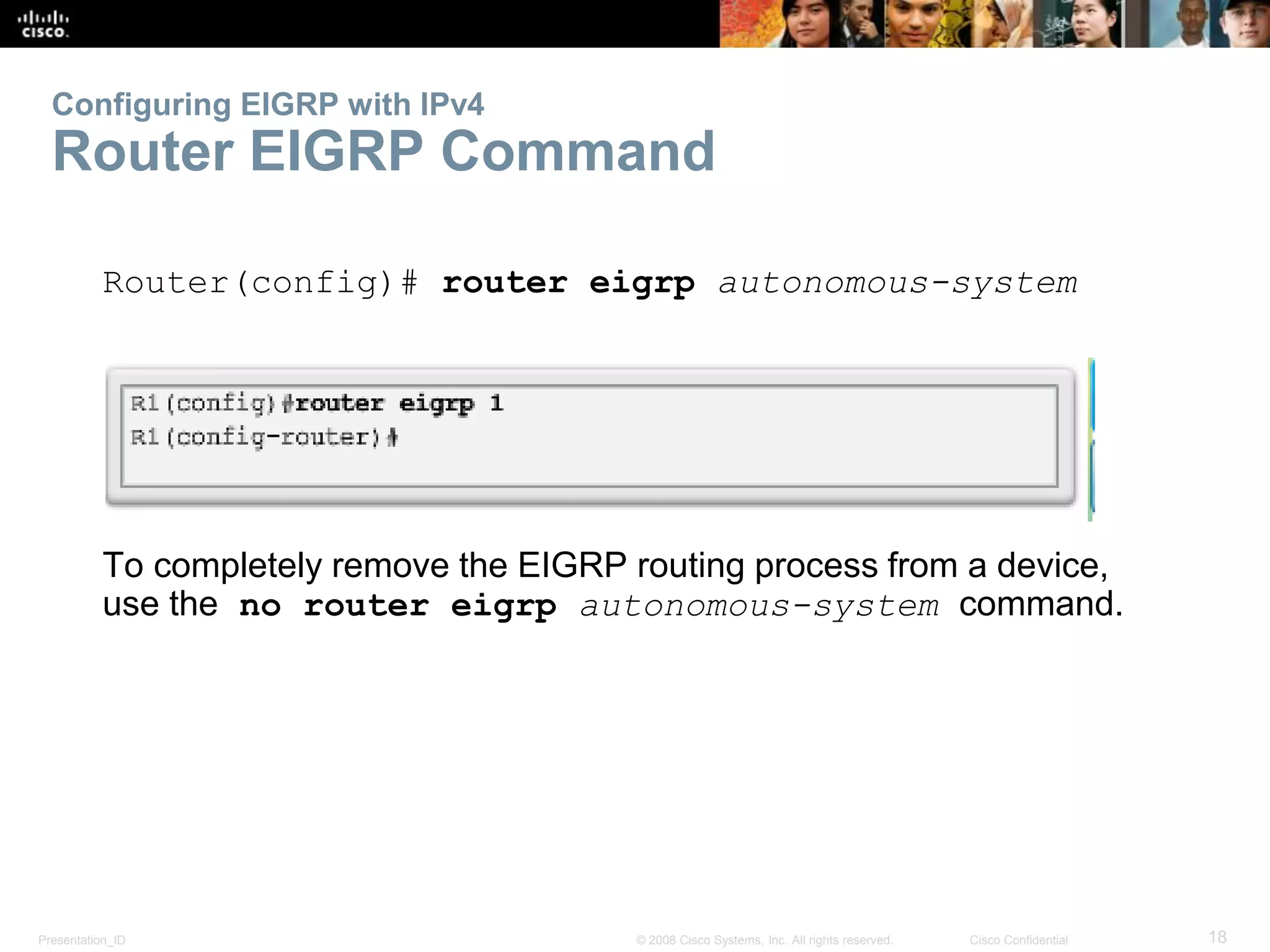
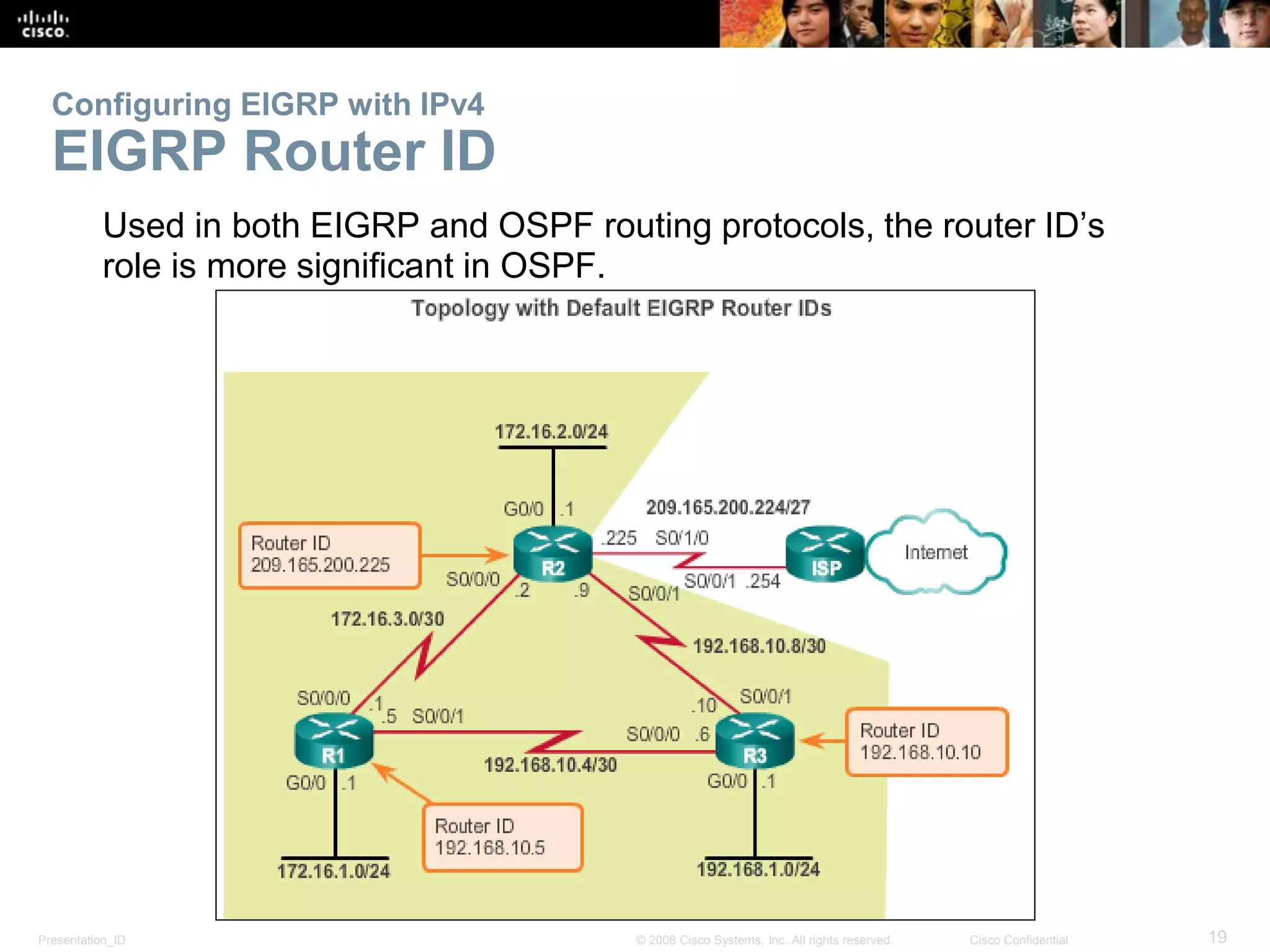
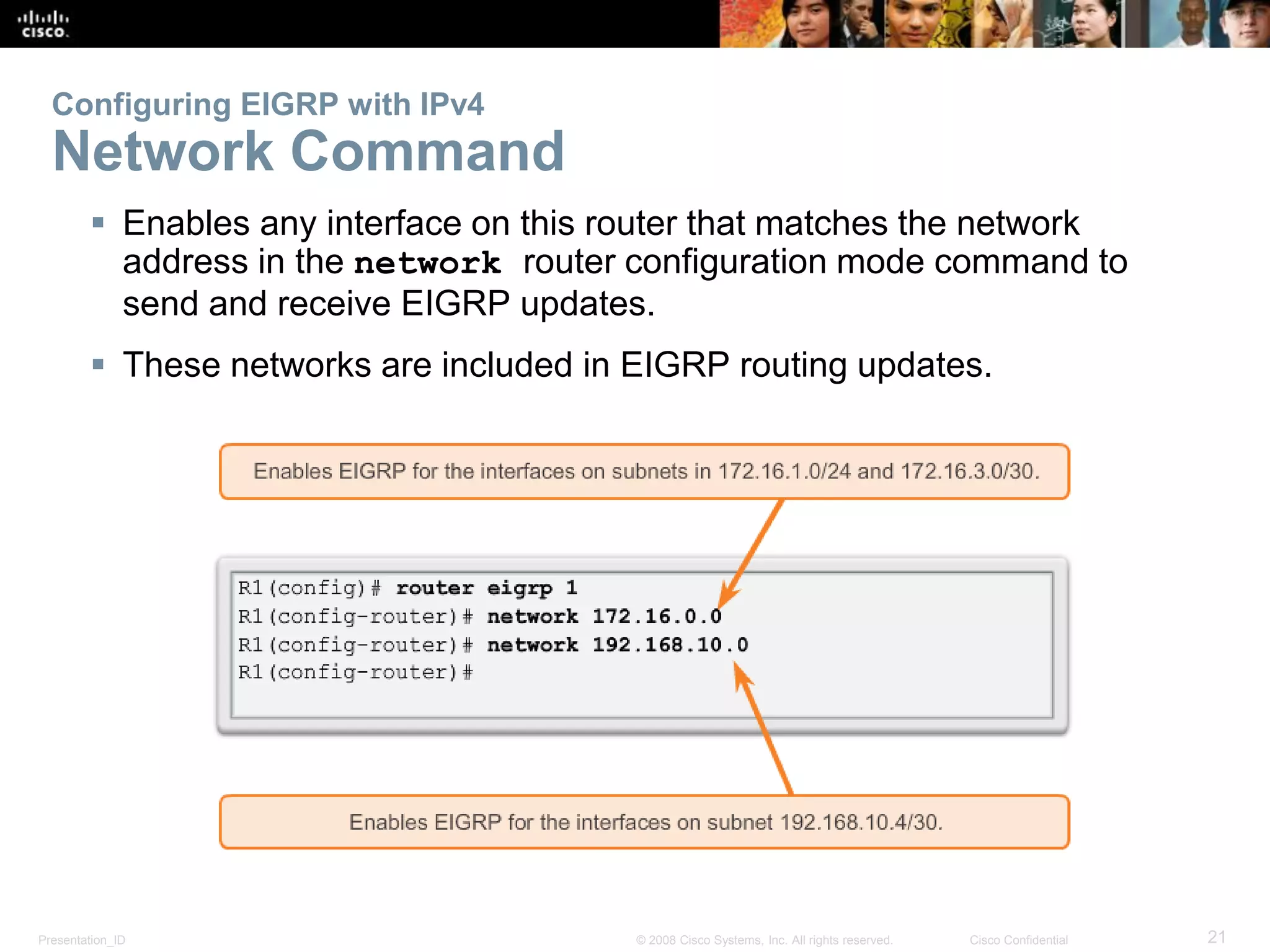
Configuring EIGRP with IPv4
The Network Command and Wildcard Mask
To configure EIGRP to advertise specific subnets only, use the
wildcard-mask option with the network command.
Router(config-router)# network network
address [wildcard-mask]
The wildcard mask is the inverse of the subnet mask.
To calculate the wildcard mask, subtract the subnet mask from
255.255.255.255:
255.255.255.255
-- 255.255.255.252
0. 0. 0. 3 wildcard mask
Note: Some IOS versions also let you enter the subnet mask
instead of a wildcard mask.](https://image.slidesharecdn.com/rb4j95xsqlgyg65itbp8-signature-21cea0c58bcaac2f629a523c81a0be50d3e00f4ef53152280b5357ccda4a6c55-poli-150208054451-conversion-gate02/75/CCNAv5-S3-Chapter-7-EIGRP-23-2048.jpg)