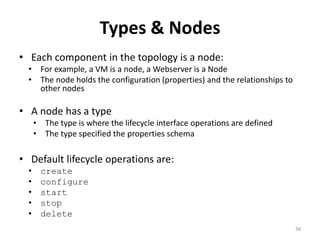
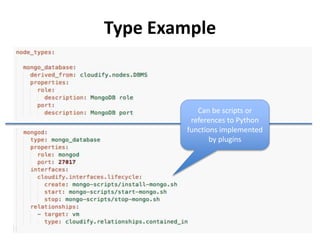
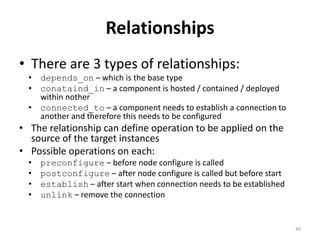
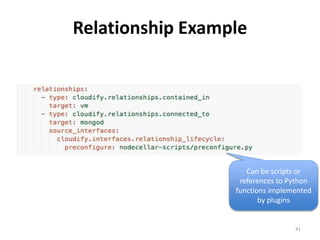
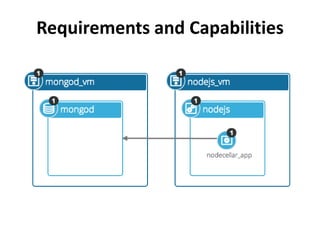
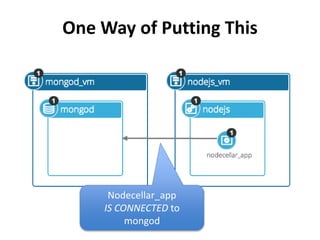
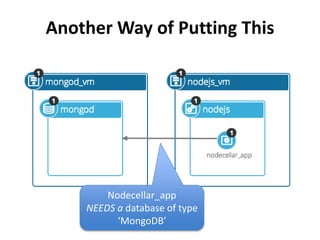
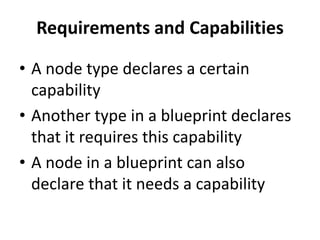
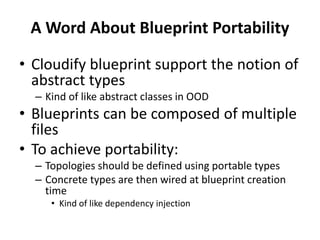
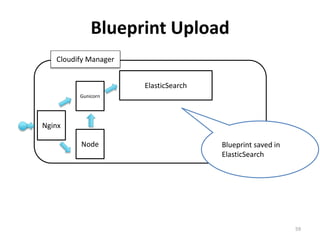
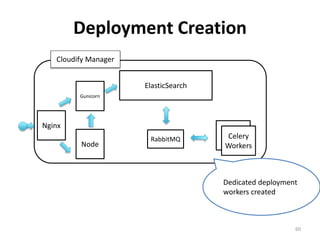
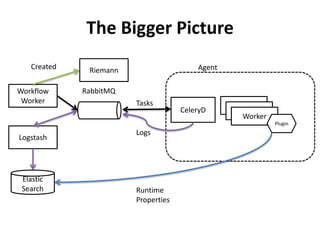
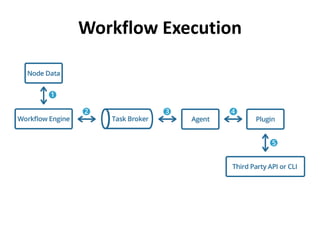
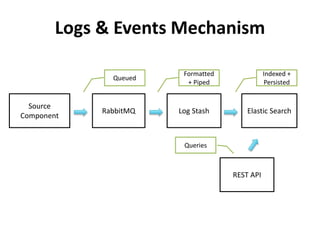
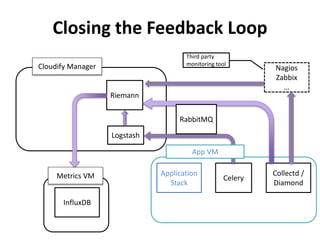
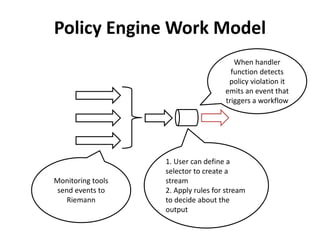
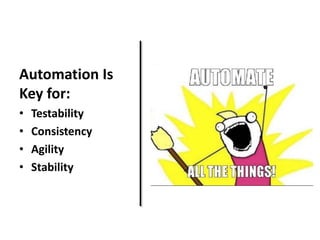
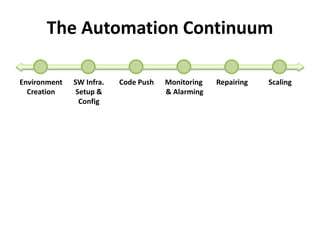
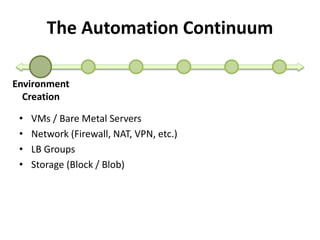
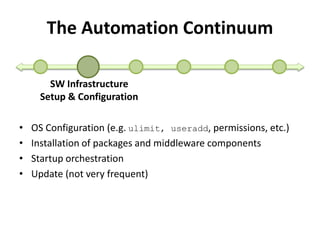
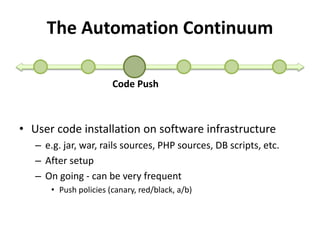
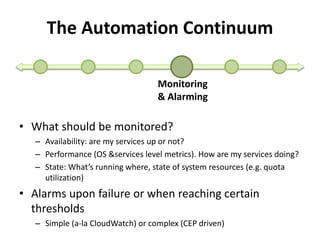
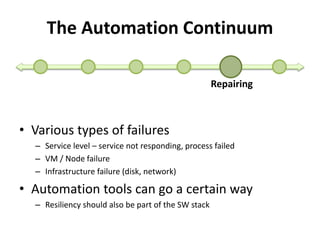
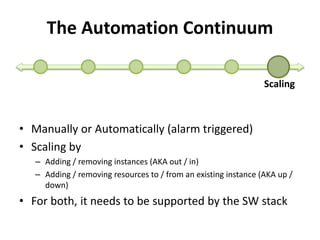
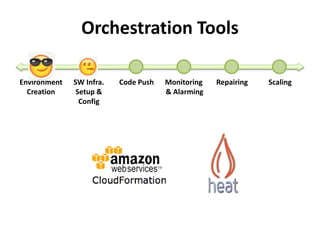
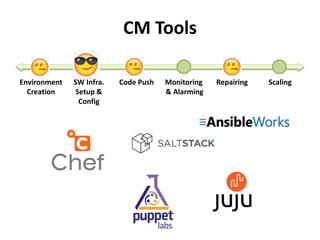
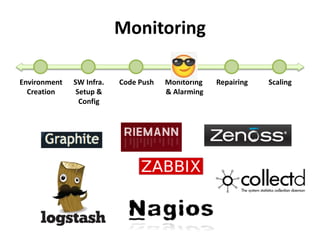
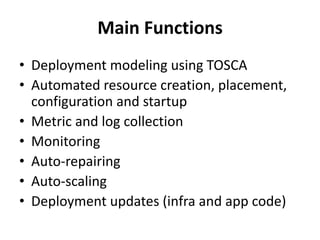
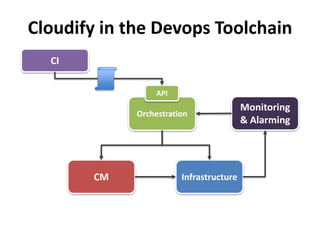
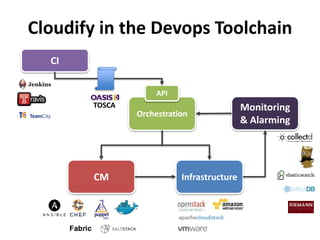
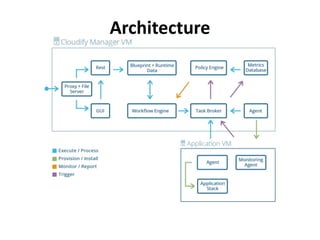
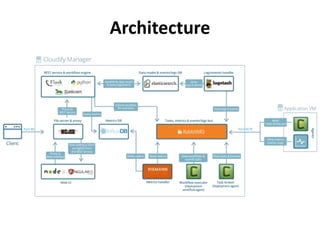
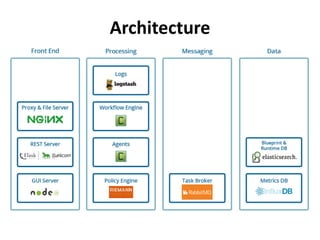
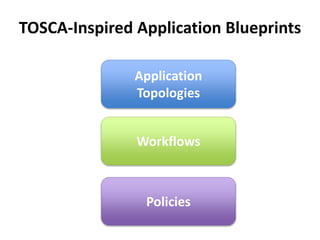
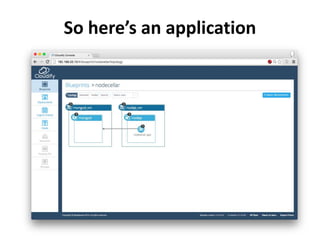
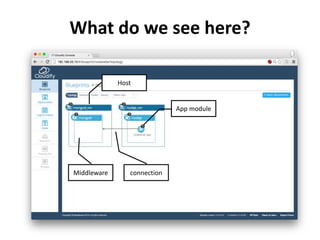
The document discusses Cloudify, an open source platform for deploying, managing, and scaling complex multi-tier applications on cloud infrastructures. It introduces key concepts of Cloudify including topologies defined using TOSCA, workflows written in Python, policies defined in YAML, and how Cloudify ties various automation tools together across the deployment continuum. The document also provides demonstrations of uploading a blueprint to Cloudify and installing an application using workflows, and discusses how Cloudify collects logs, metrics and handles events during workflow execution.













![Inputs and Outputs
inputs:
cloudstack_api_url:
default: ''
type: string
cloudstack_key:
default: ''
type: string
cloudstack_secret:
default: ''
type: string
...
outputs:
endpoint:
description: Web application endpoint
value:
ip_address: { get_attribute: [ nodejs_vm, ip ] }
port: { get_property: [ nodecellar_app, base_port ] }](https://image.slidesharecdn.com/ccceu2014workshop-141119114325-conversion-gate02/85/Cloudify-workshop-at-CCCEU-2014-37-320.jpg)