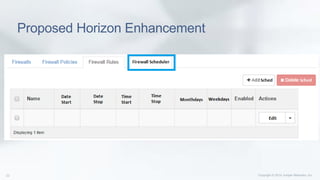
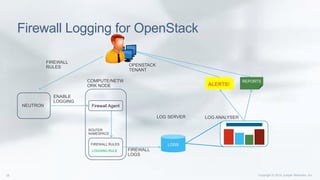
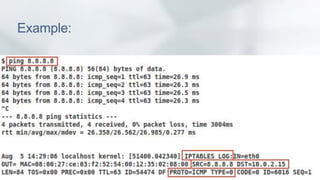
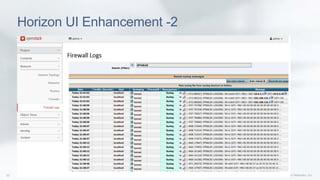
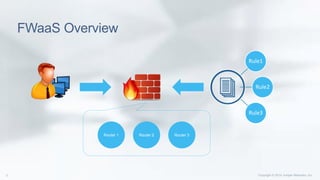
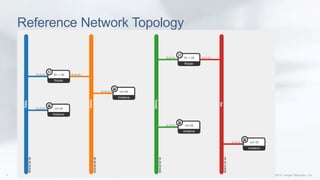
This document discusses enhancing the performance and capabilities of OpenStack's firewall-as-a-service (FWaaS). It proposes improvements to FWaaS performance by validating firewall rules and distributing rules only to relevant routers. It also discusses scheduling firewall rules based on time and enabling logging of firewall packets to help with debugging, threat analysis, and rule tuning. The document outlines integrating firewall logging with OpenStack using IPTables rules and collecting logs in a centralized server for analysis. Finally, it proposes extending the Horizon UI to make firewall logs accessible to tenants.

















![Scheduling – IPTables Spec
• Periodicity:
• datestart YYYY[-MM[-DD[Thh[:mm[:ss]]]]]
• datestop YYYY[-MM[-DD[Thh[:mm[:ss]]]]]
• timestart hh:mm[:ss]
• timestop hh:mm[:ss]
• monthdays day[,day...]
• weekdays day[,day...]
• contiguous
• Kerneltz](https://image.slidesharecdn.com/openstacksummitindia2015juniper-150820164052-lva1-app6891/85/Enhancing-OpenStack-FWaaS-for-real-world-application-20-320.jpg)