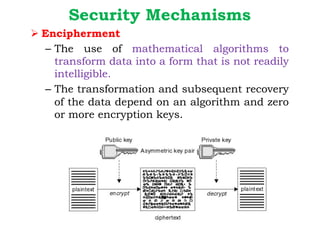
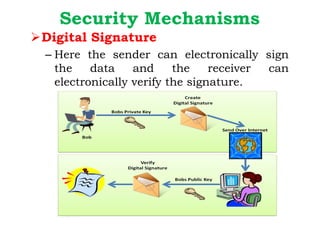
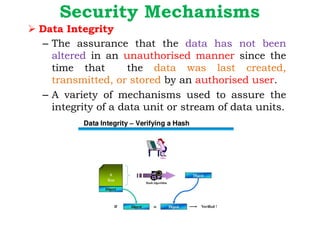
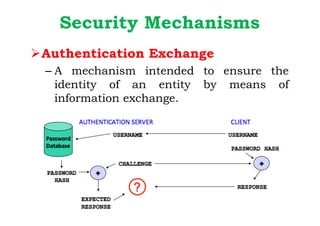
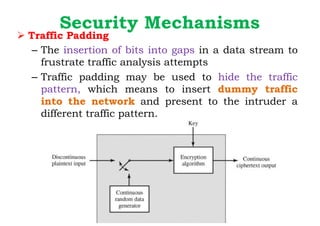
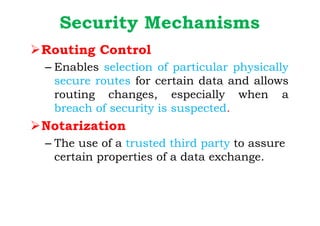
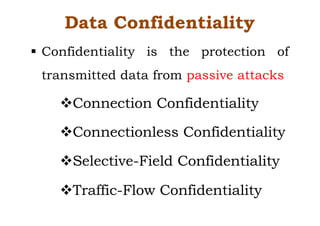
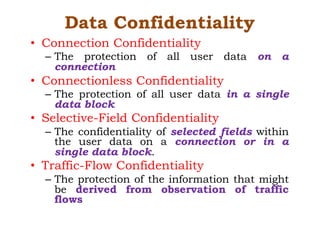
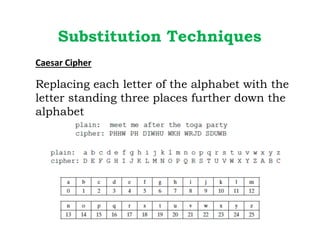
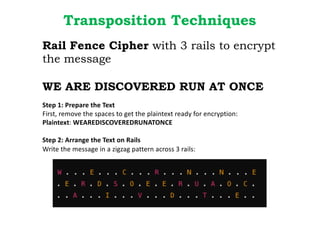
Dr. M.V. Ranjith Kumar is a Senior Audit Program Manager at Infosys with 15 years of experience in cybersecurity and information security audits across various industries. He specializes in areas such as telematics implementation, blockchain architecture, and vendor risk assessments, and has published research in cybersecurity fields. The document outlines his qualifications, course content on cryptography and cyber security, and essential concepts related to computer security, cryptographic techniques, and the legal aspects of cybersecurity.










![The U.S. Department of Justice [DoJ]
categorizes computer crime based on
the role that the computer plays in the
criminal activity, as follows:
ØComputers as targets
ØComputers as storage devices
ØComputers as communications tools](https://image.slidesharecdn.com/cb3491introduction-week2-241003155119-c607f53c/85/CB3491-Introduction-to-cryptography-and-cyber-security-12-320.jpg)