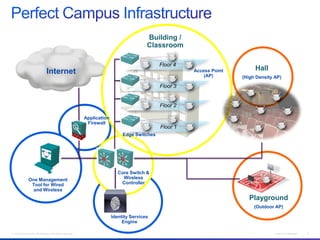
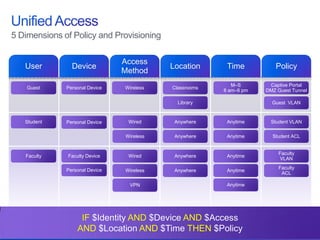
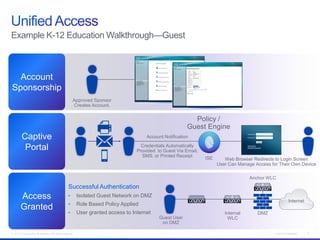
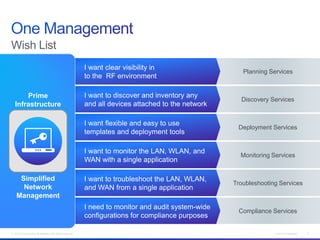
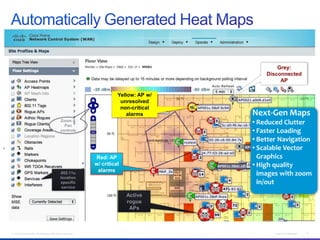
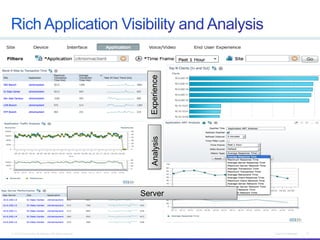
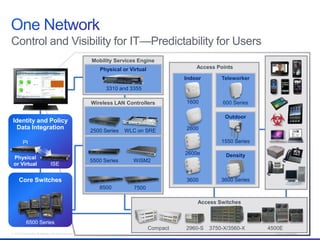
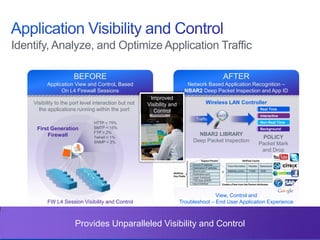
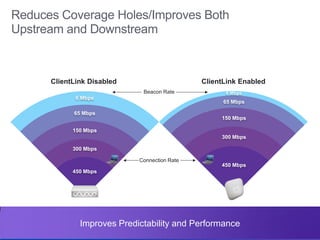
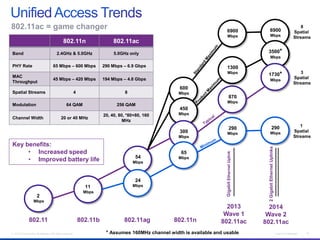
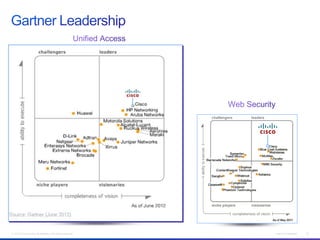
The document discusses building a campus network to support e-learning. It recommends a unified network with one policy, one management system, and one network across wired and wireless. This allows supporting needs like online testing, BYOD, and digital content while improving security, visibility and control through the use of technologies like Identity Services Engine and Prime Infrastructure.