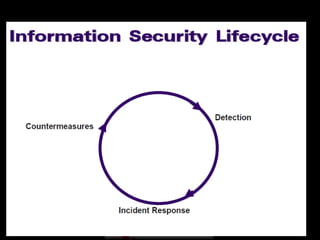
The document discusses cybercrime and building a cybercrime case. It defines different types of cyber crimes including data crimes like data interception and theft, and network crimes like network interference and sabotage. It explains the three bodies of law relevant to cybercrime cases - criminal law which deals with punishments, civil law which deals with disputes between individuals, and administrative law which governs government agencies. It then outlines the key steps in incident handling for cybersecurity incidents - preparation, identification, containment, eradication, recovery, and lessons learned. Finally, it discusses the importance of properly managing digital evidence collected during an investigation.