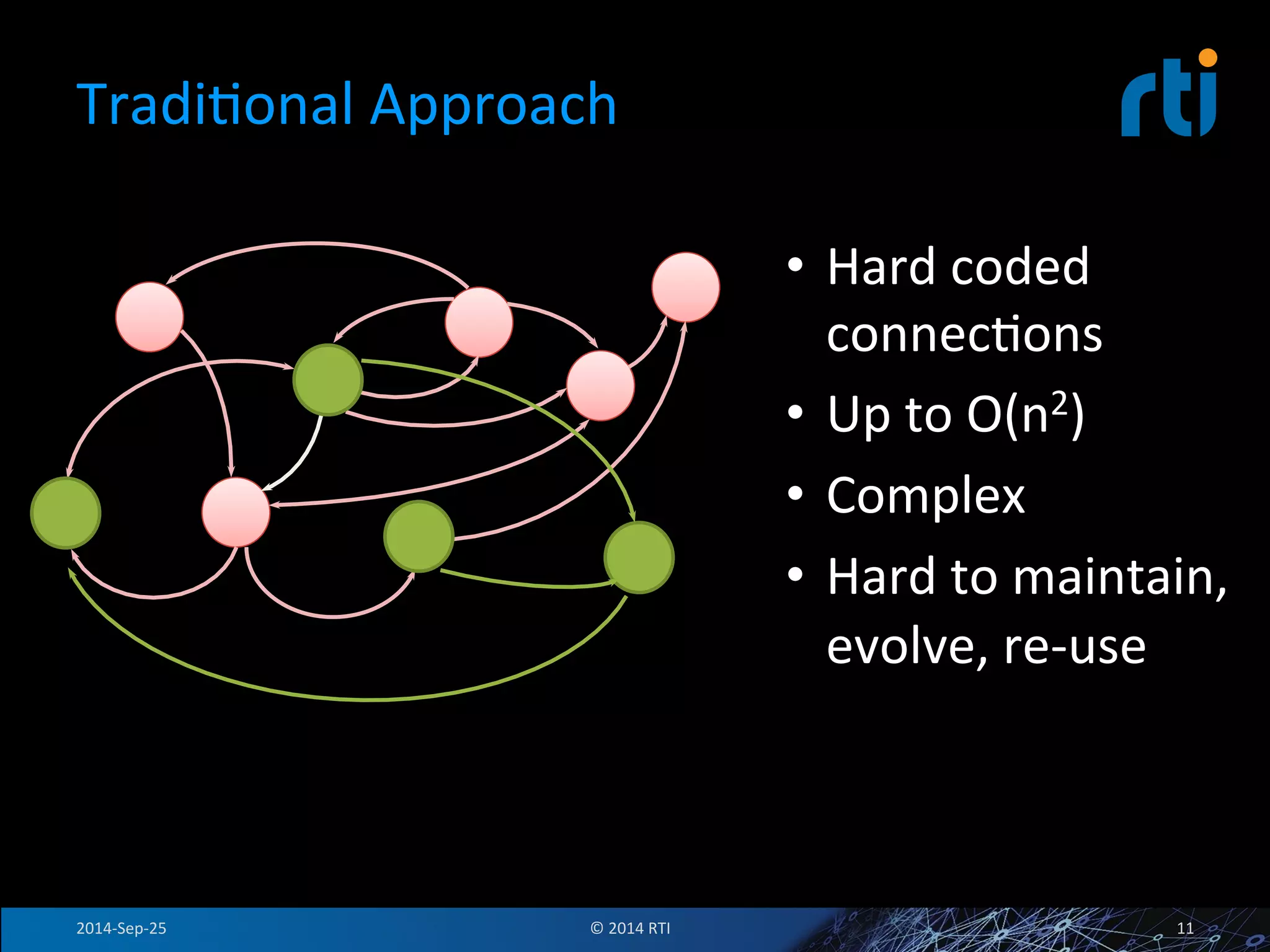
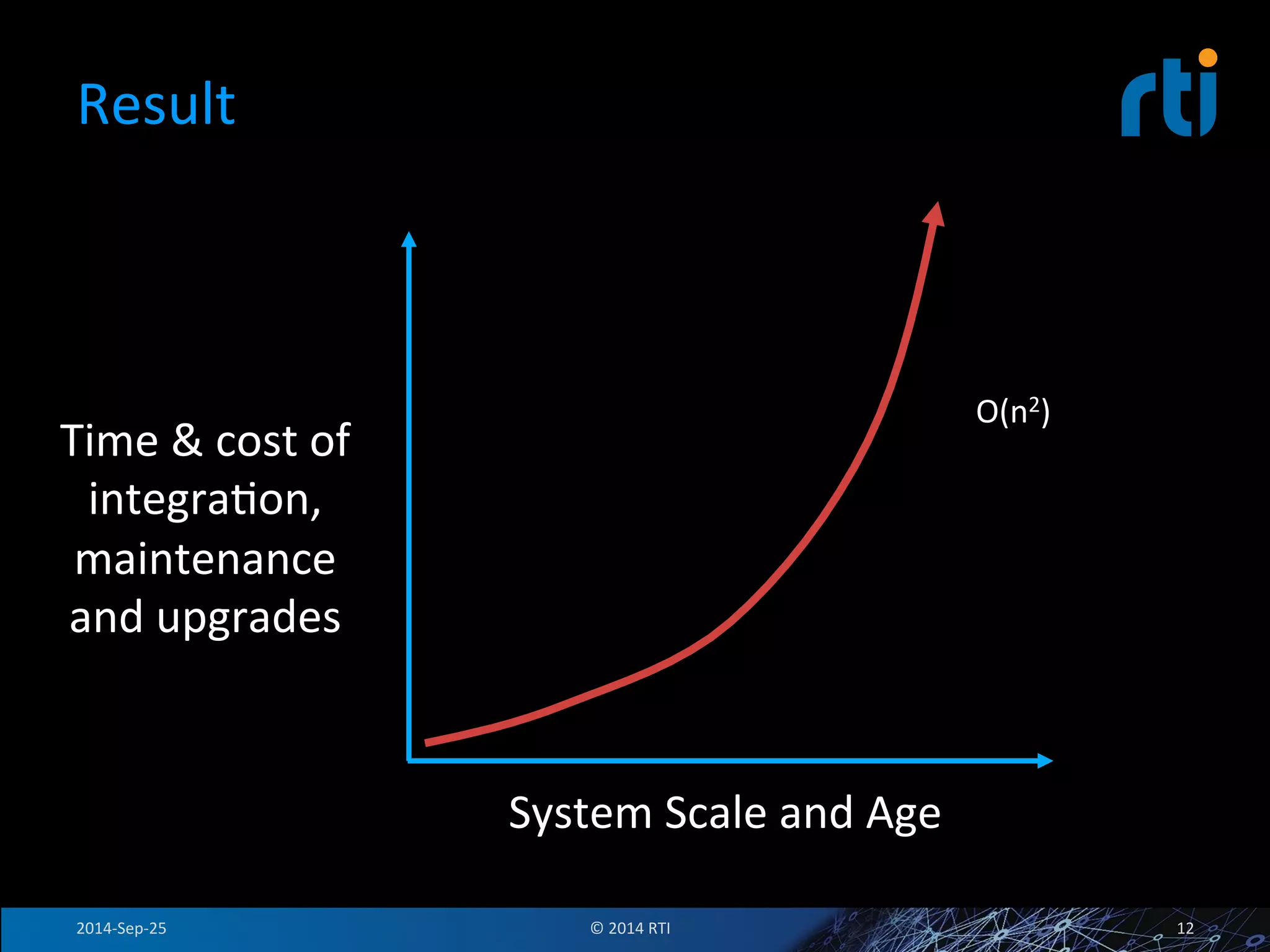
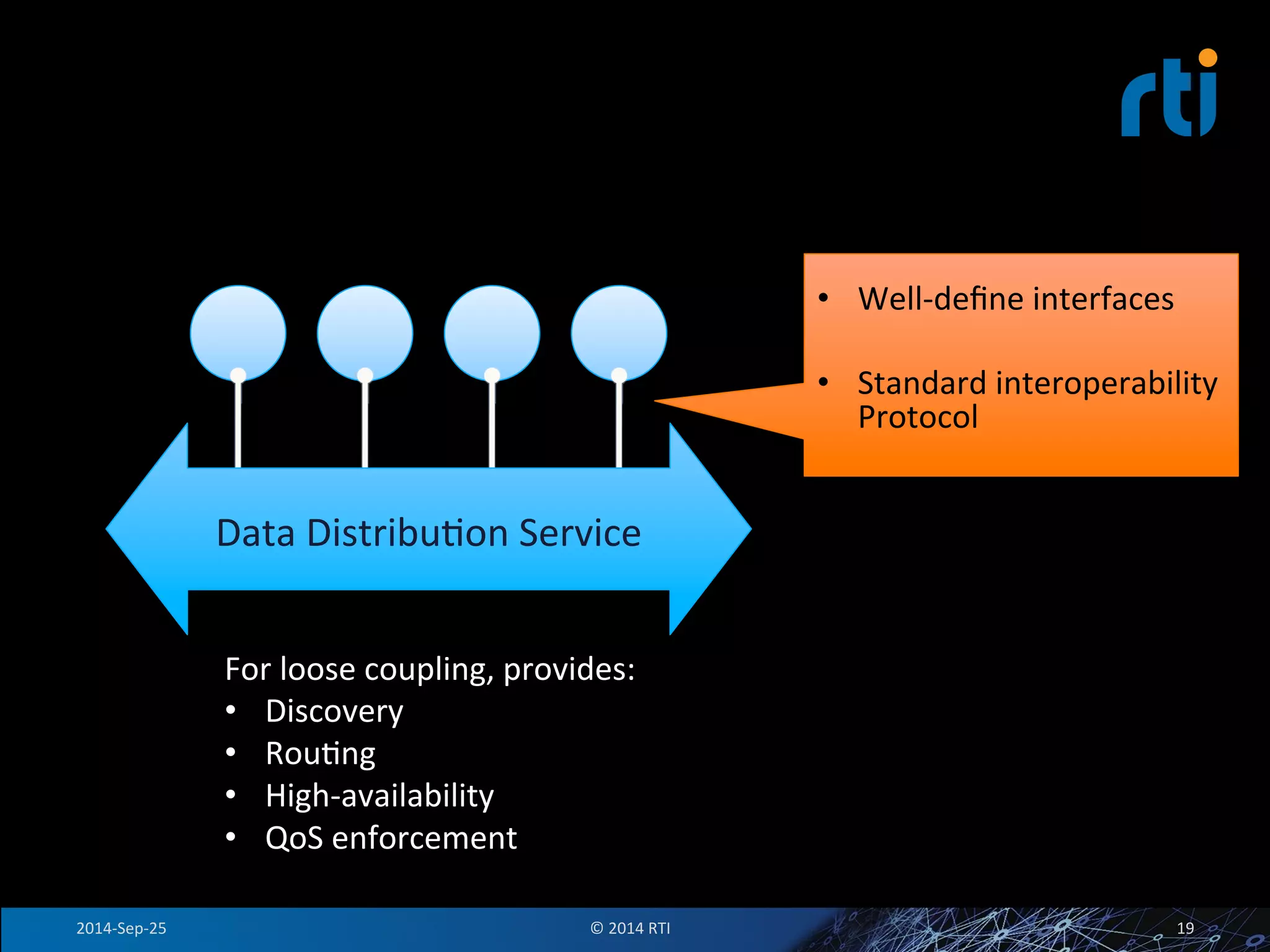
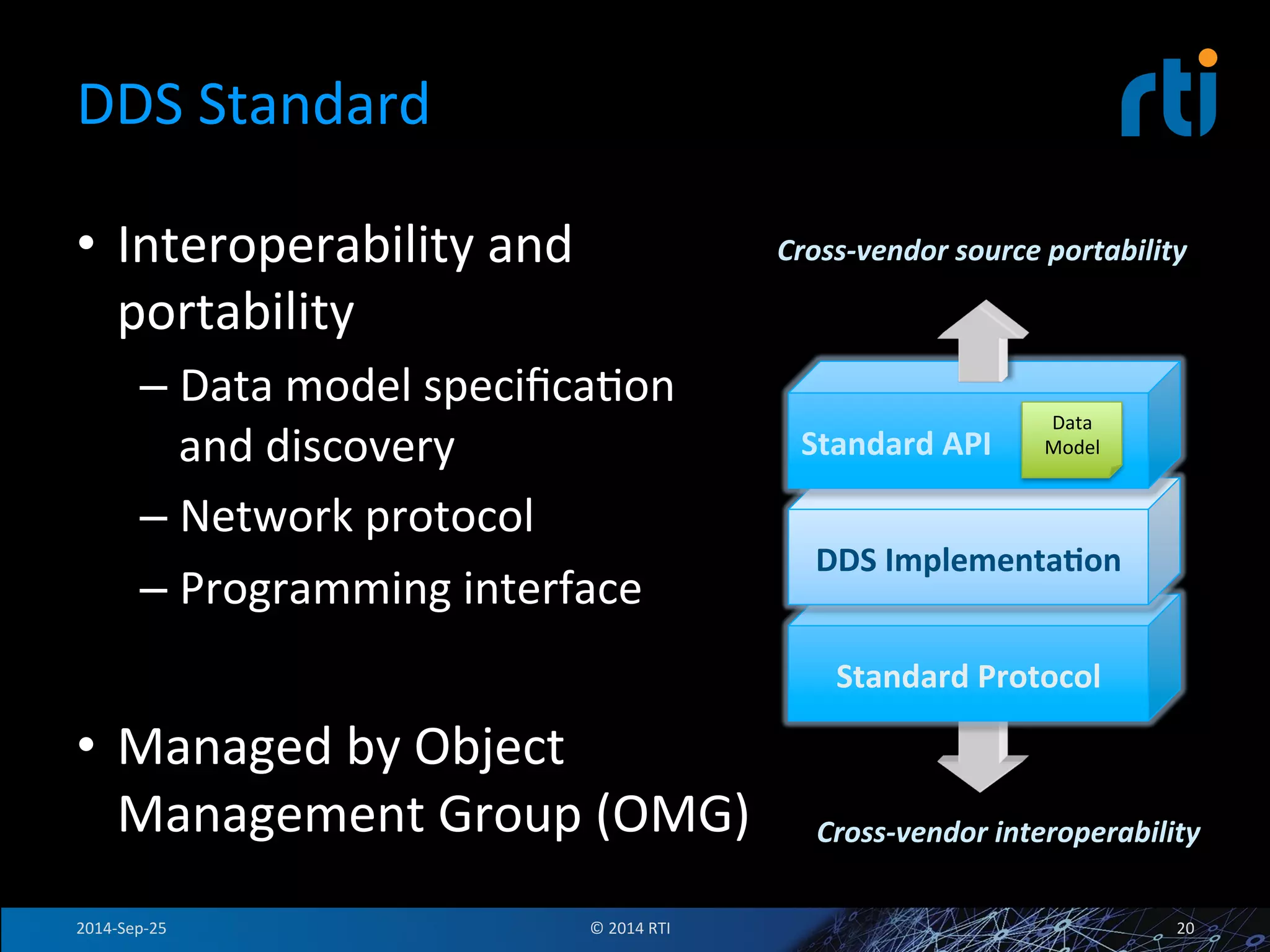
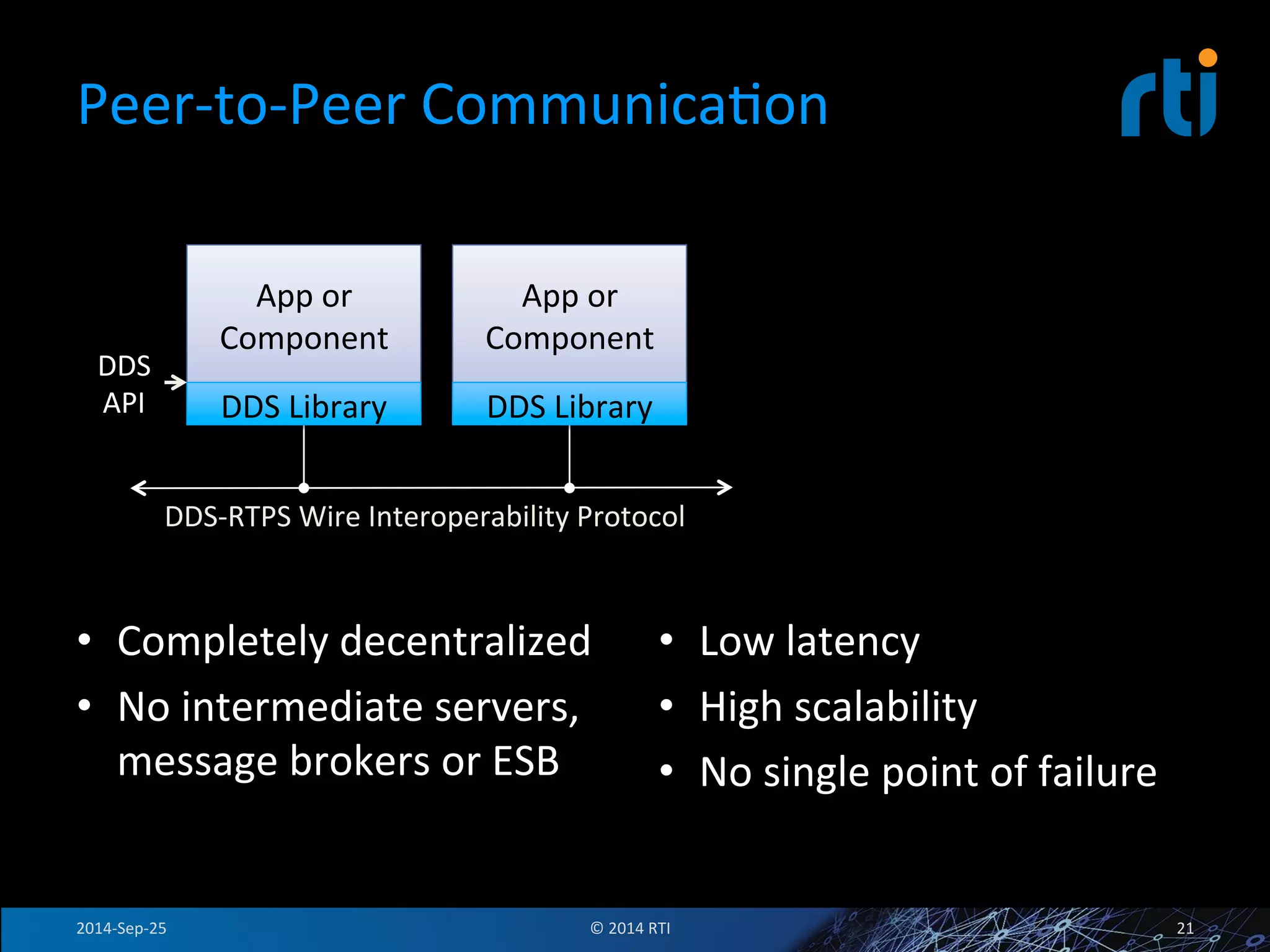
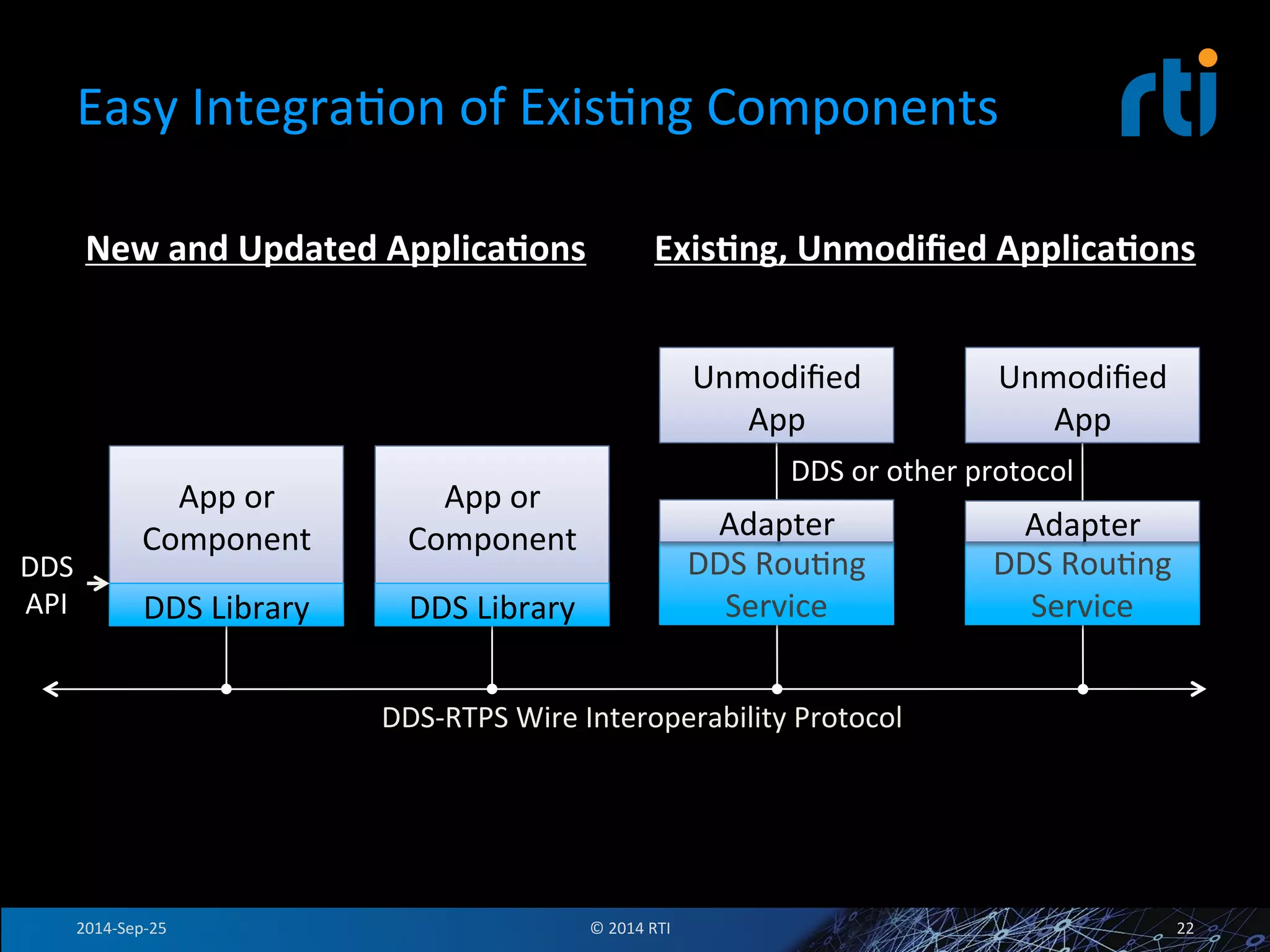
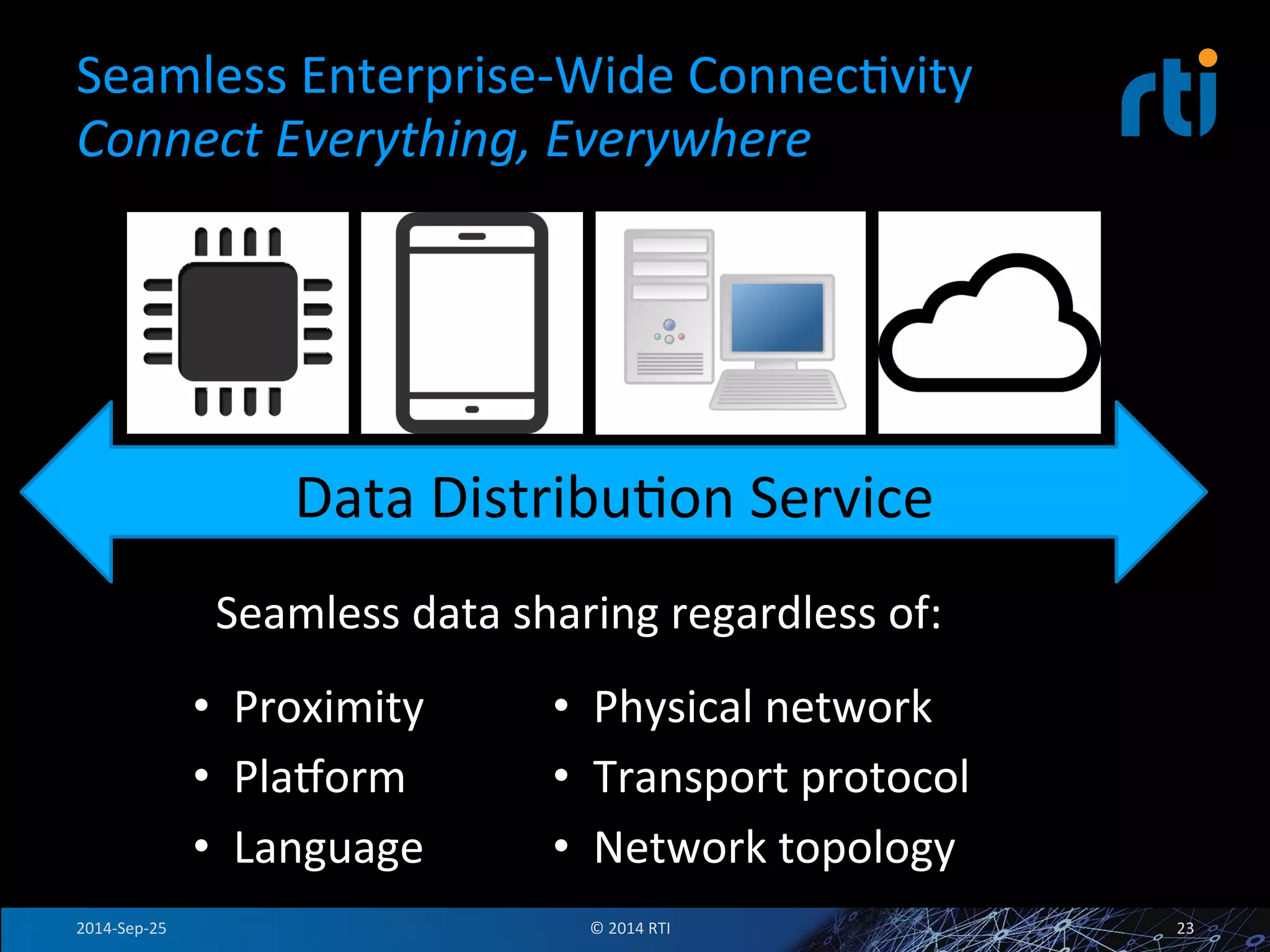
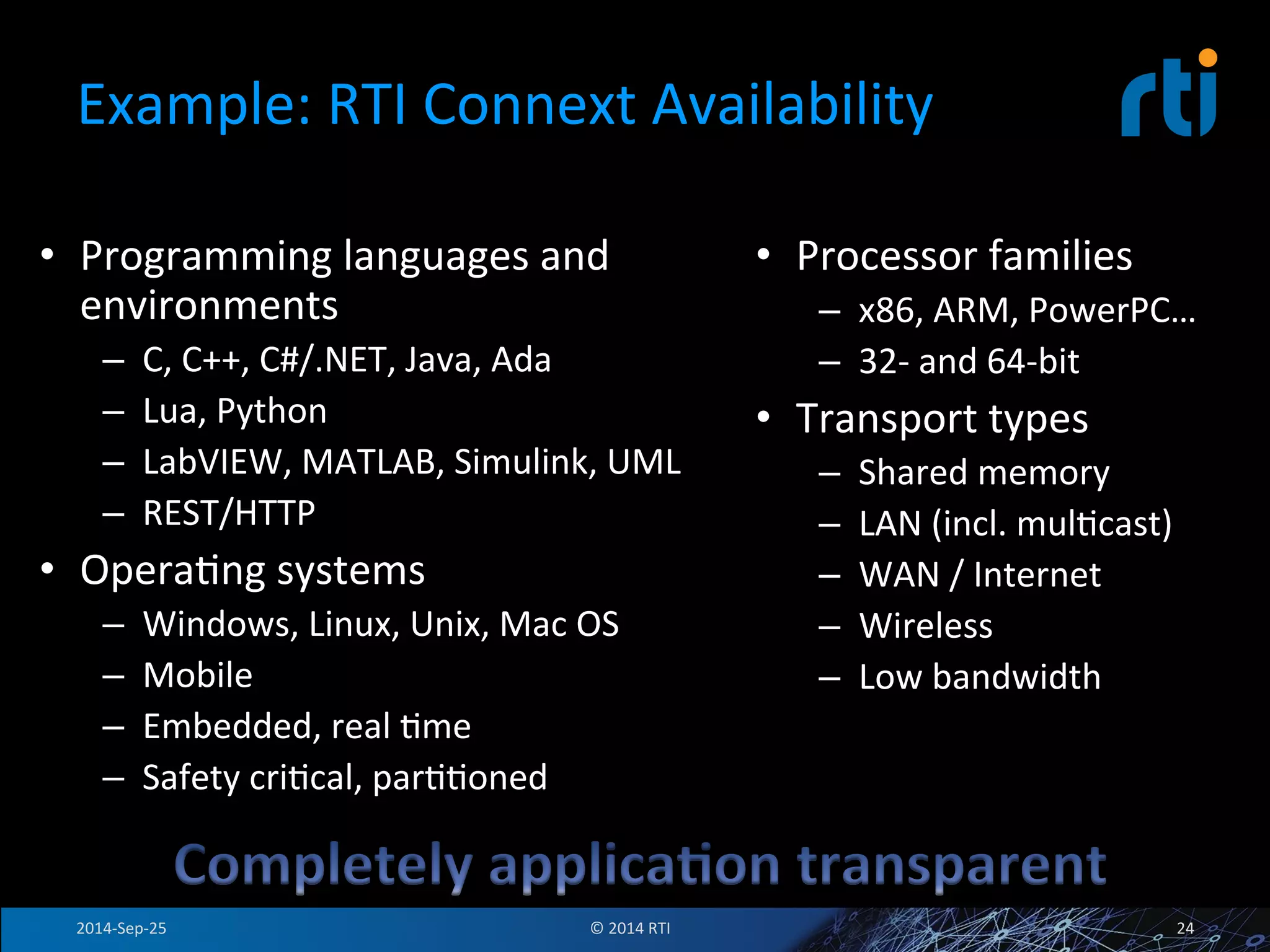
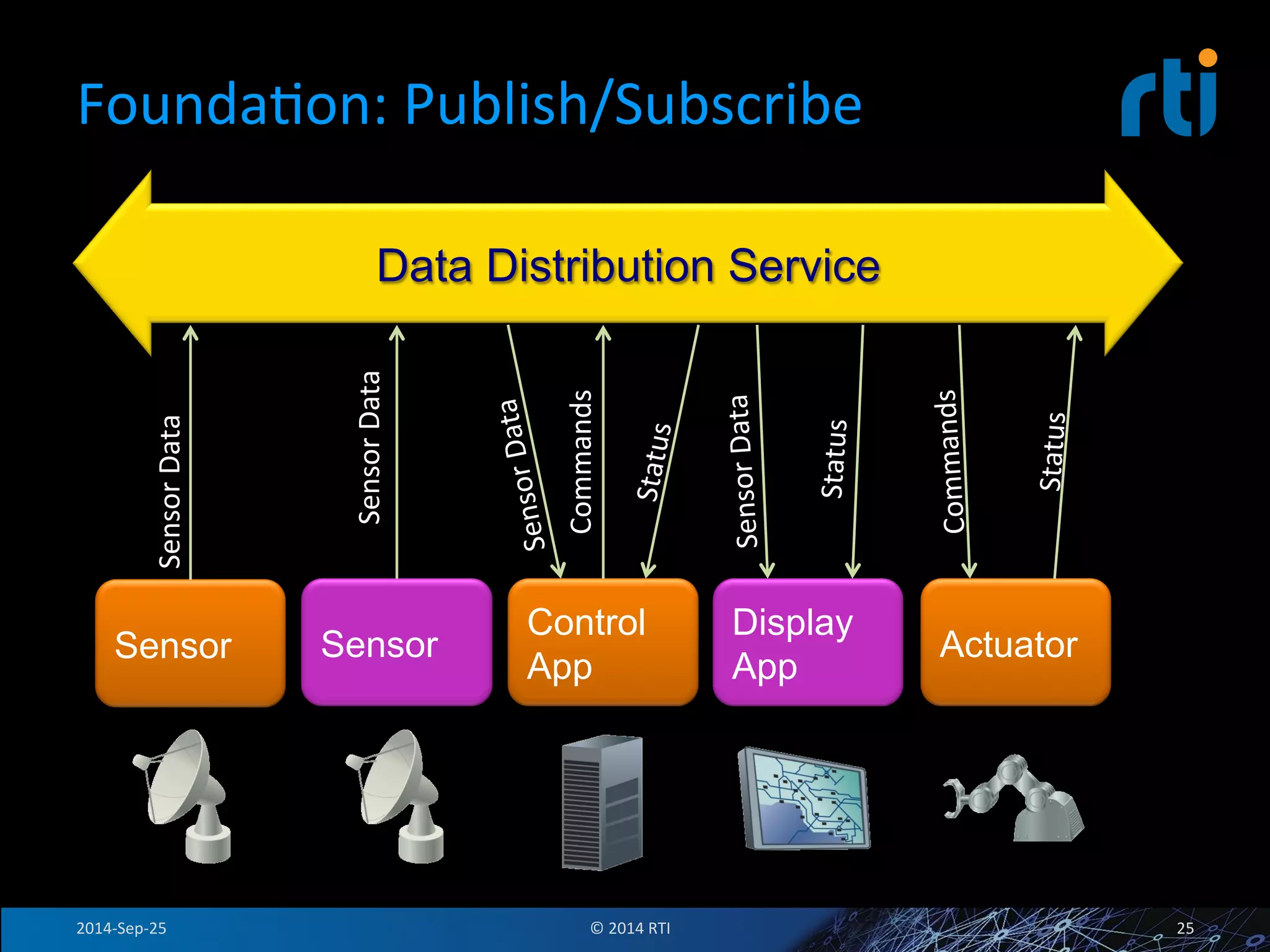
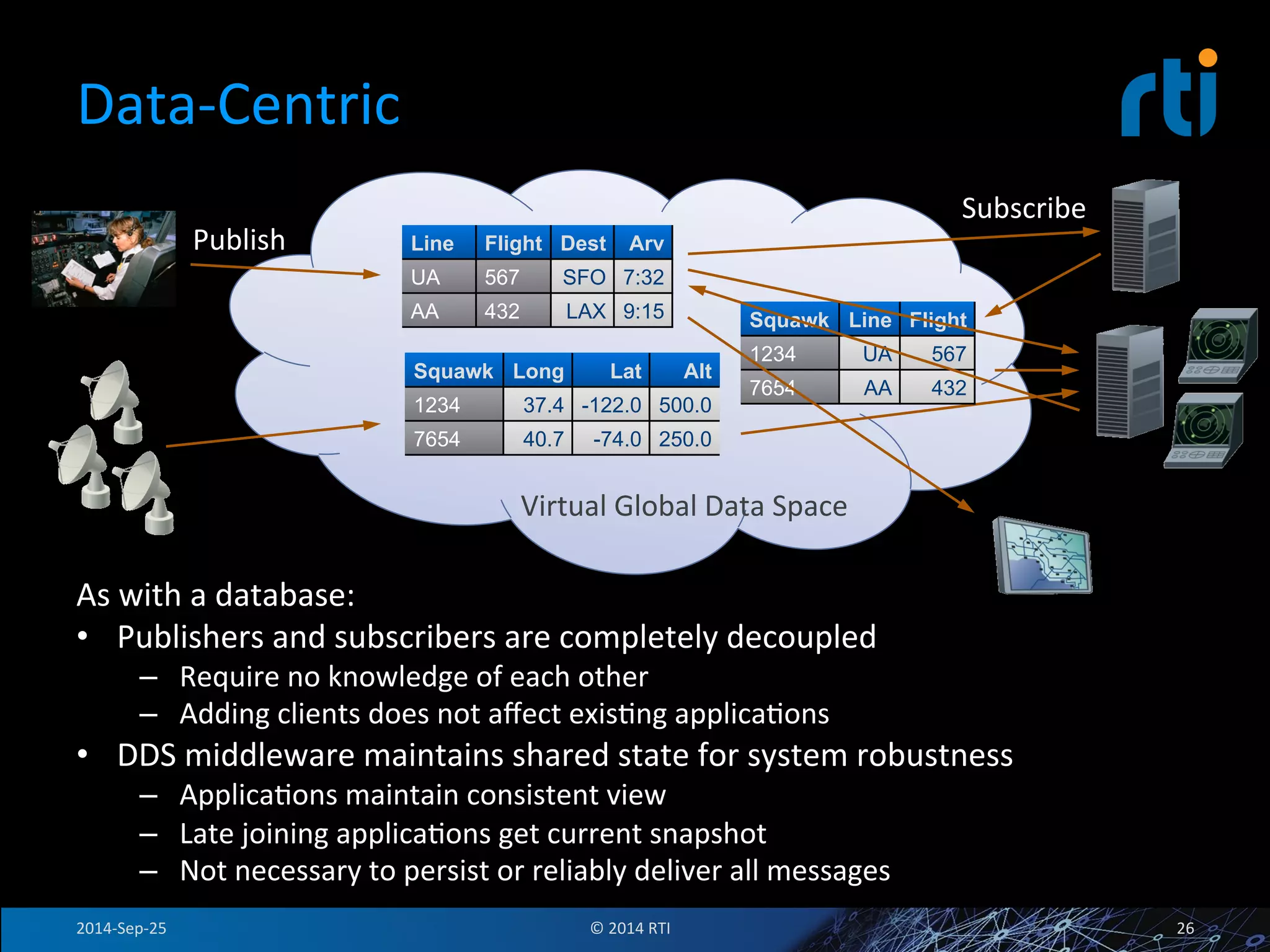
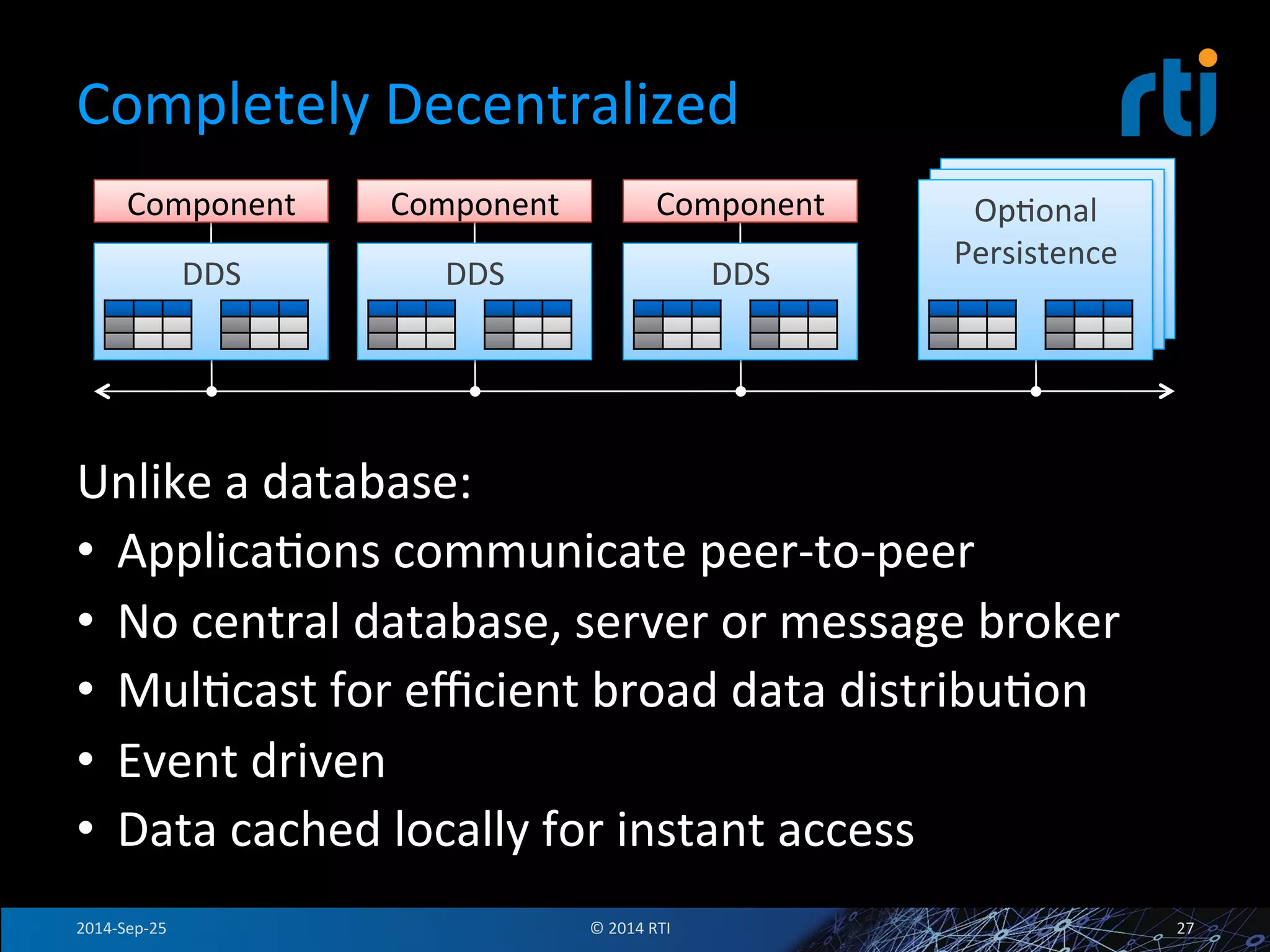
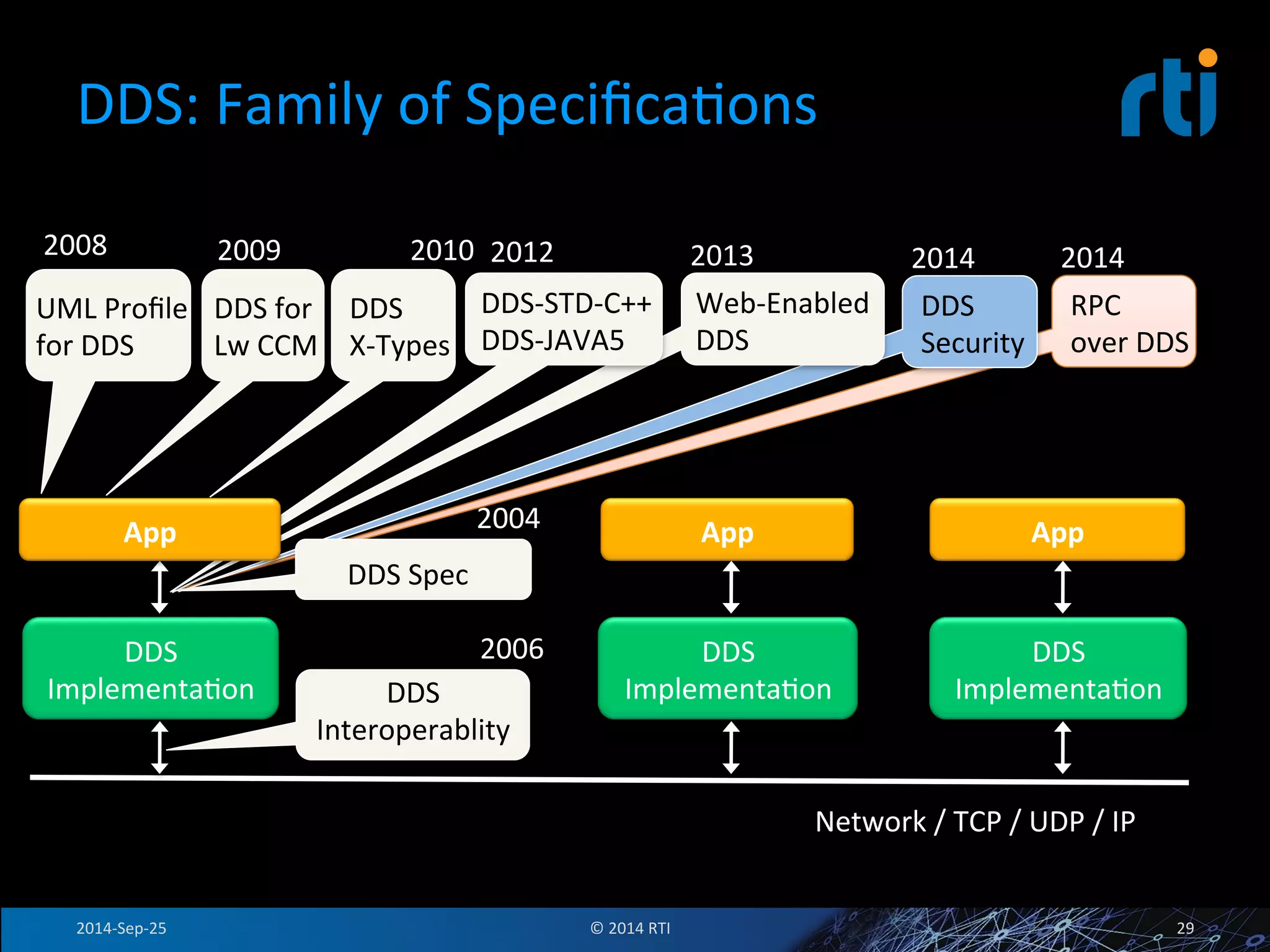
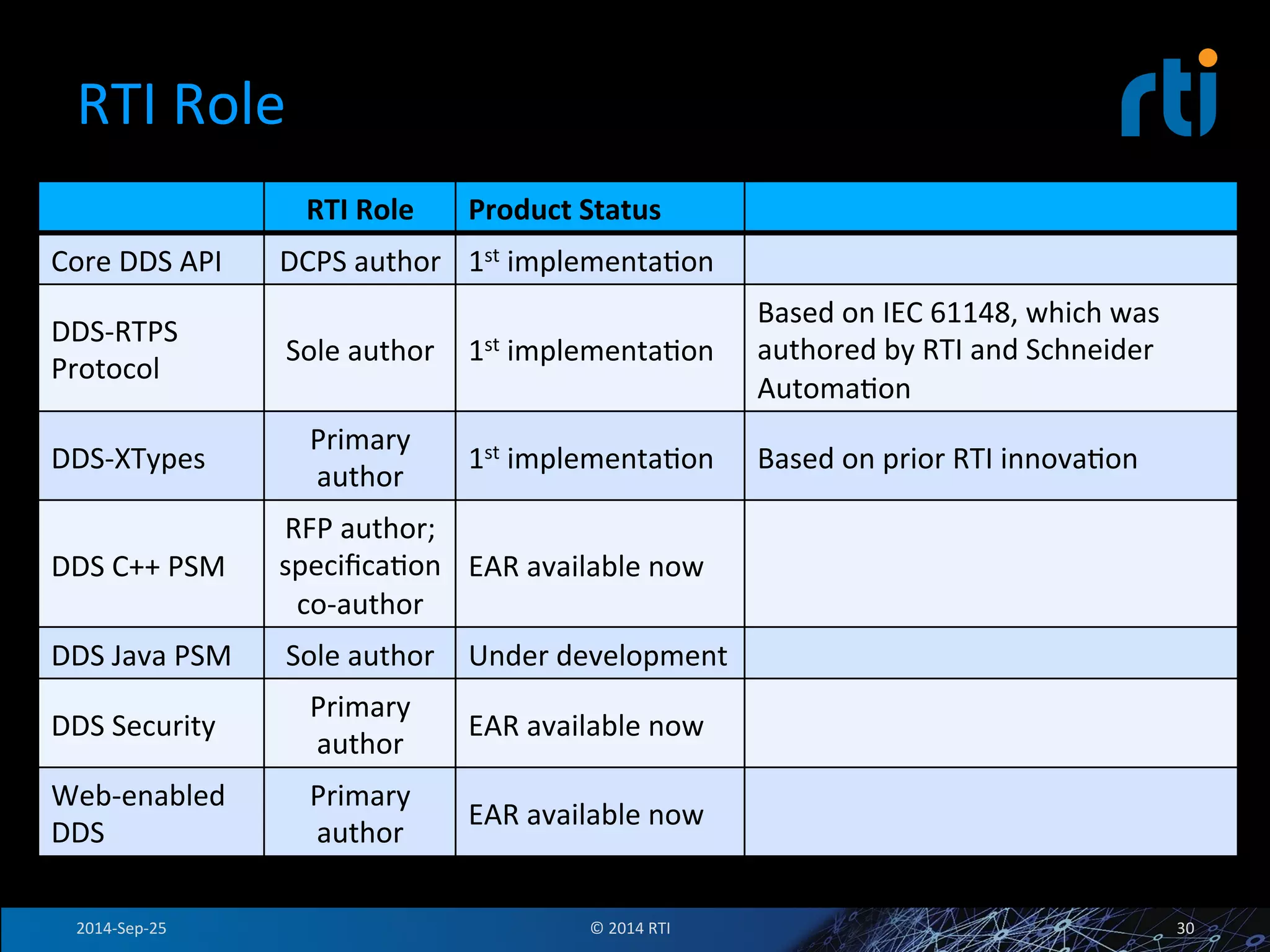
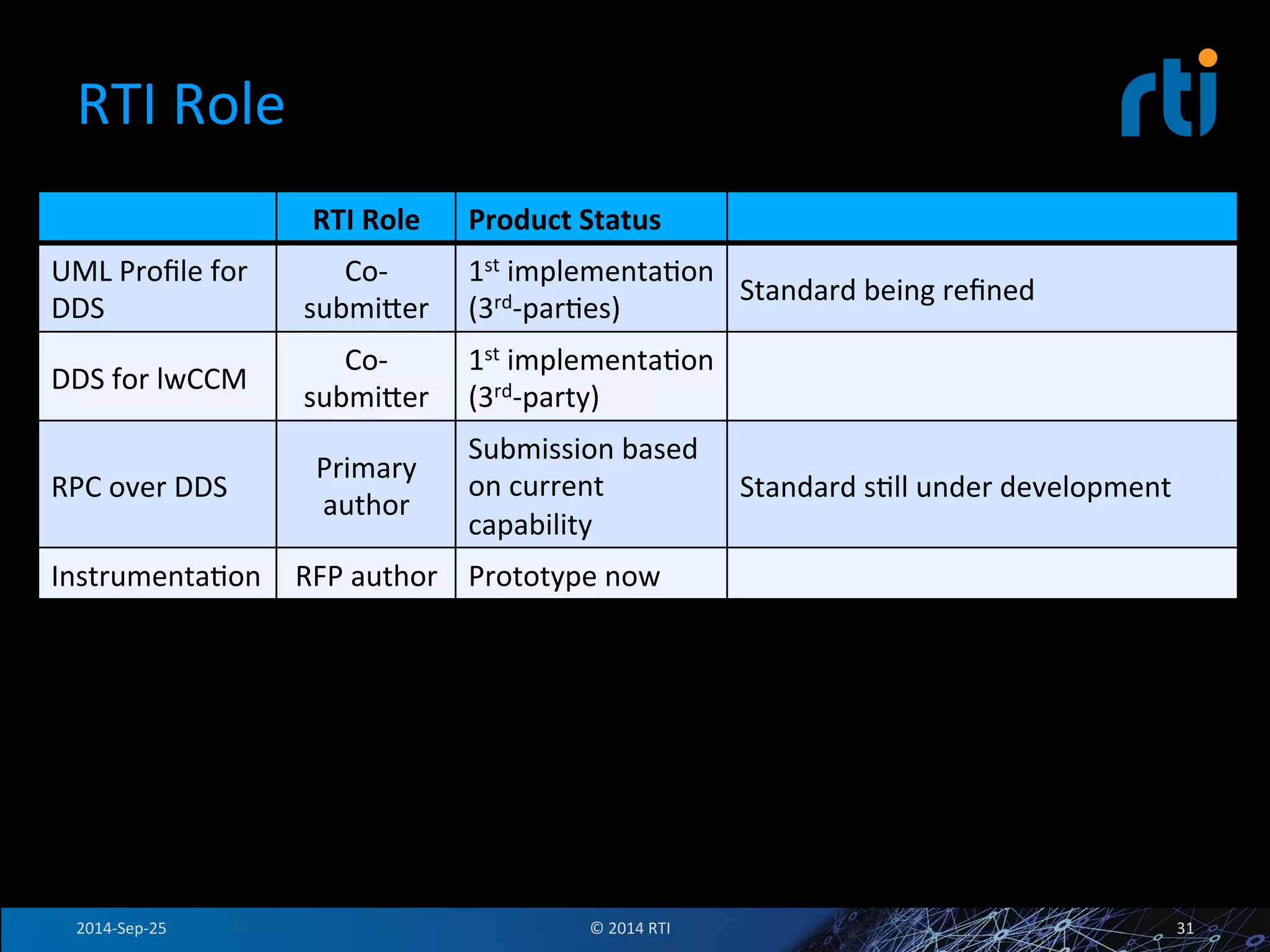
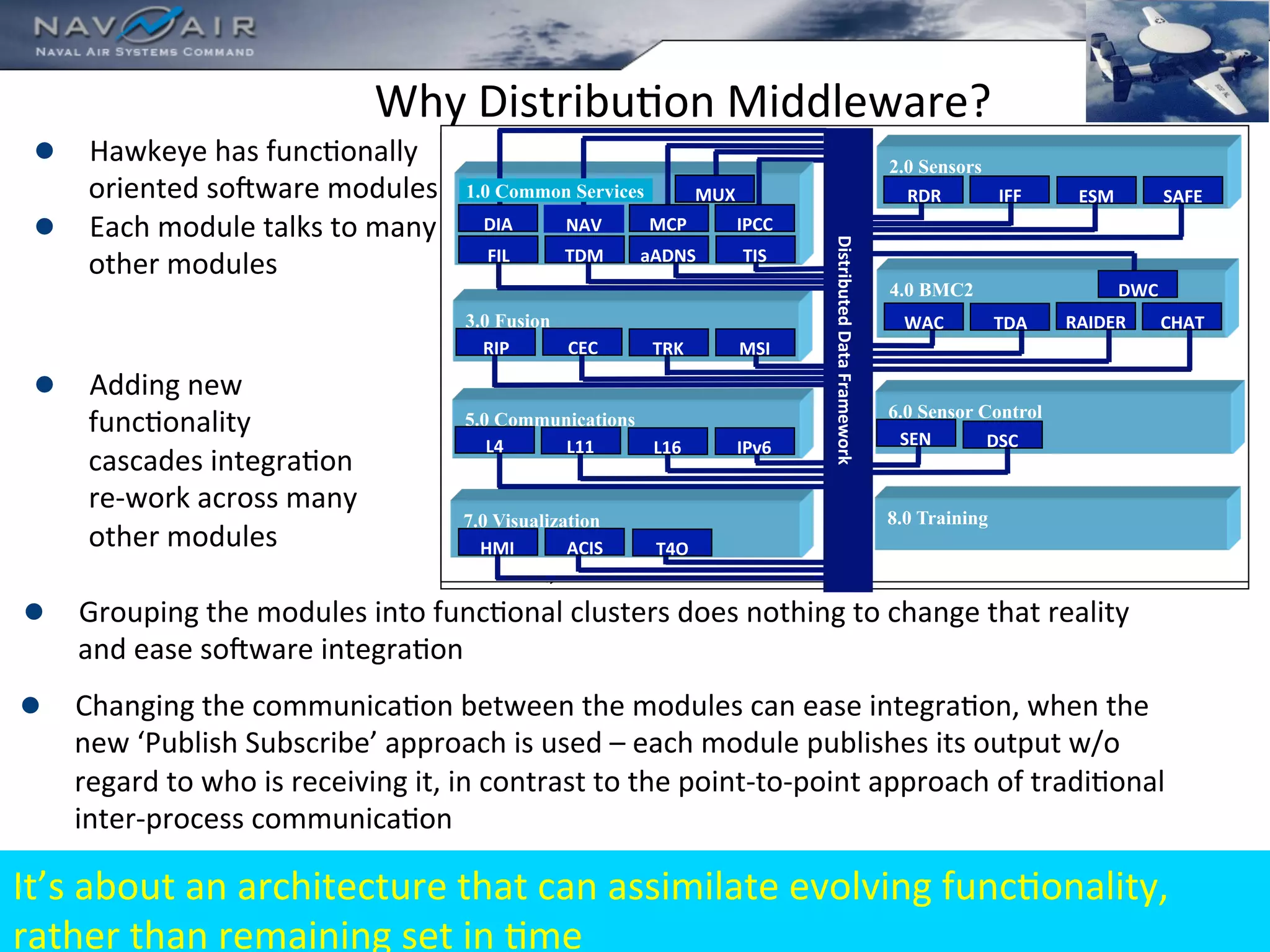
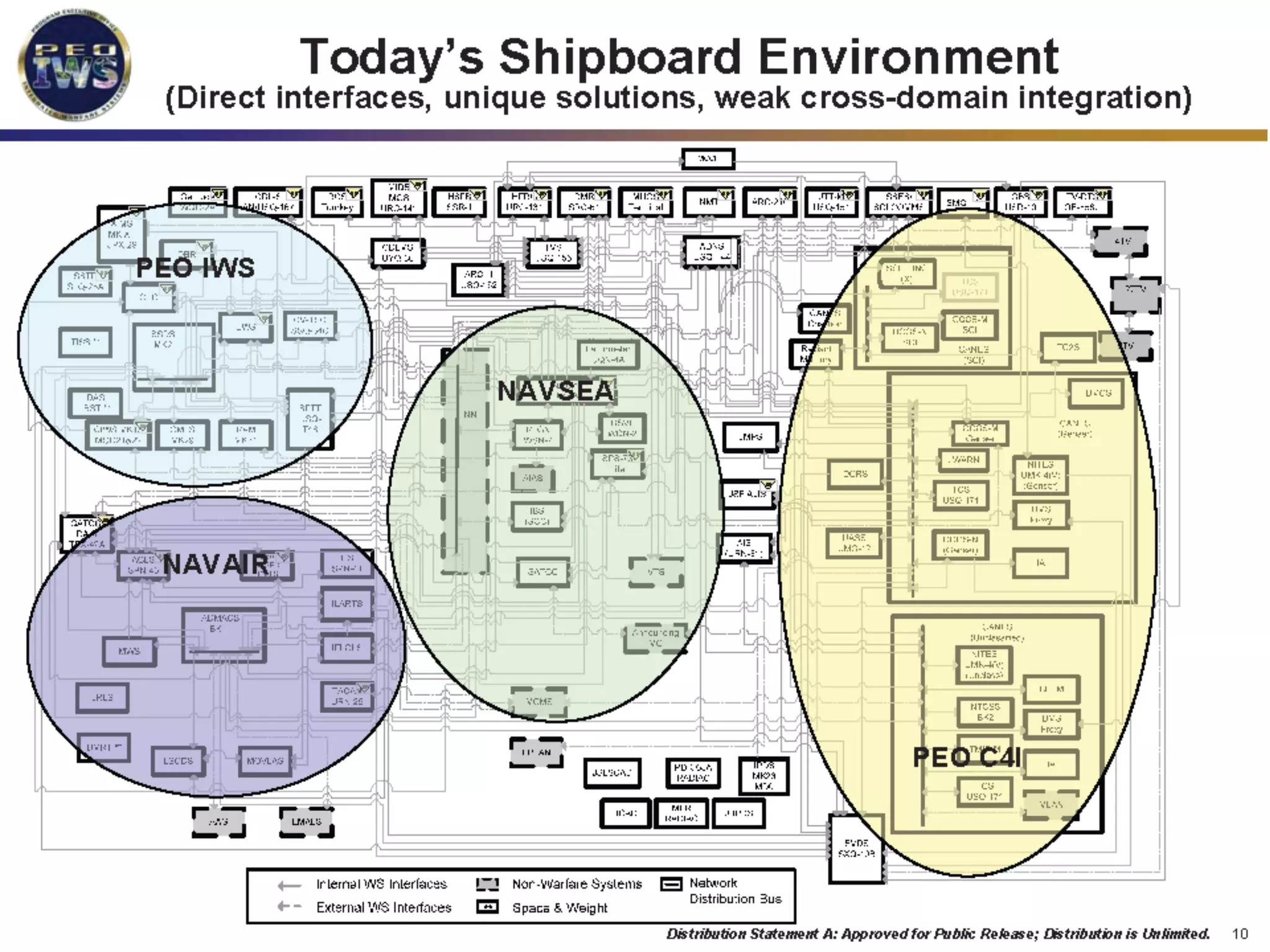
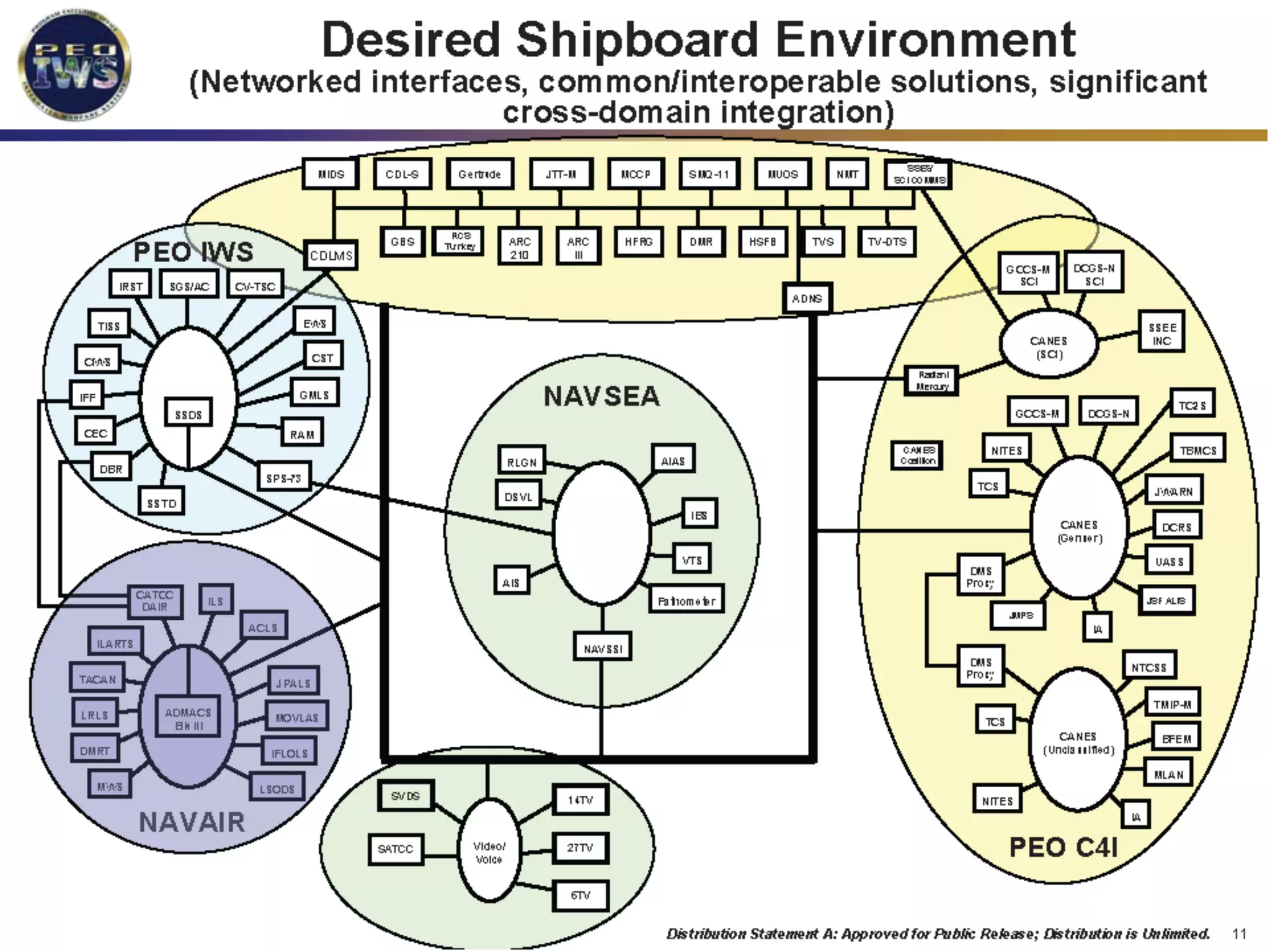
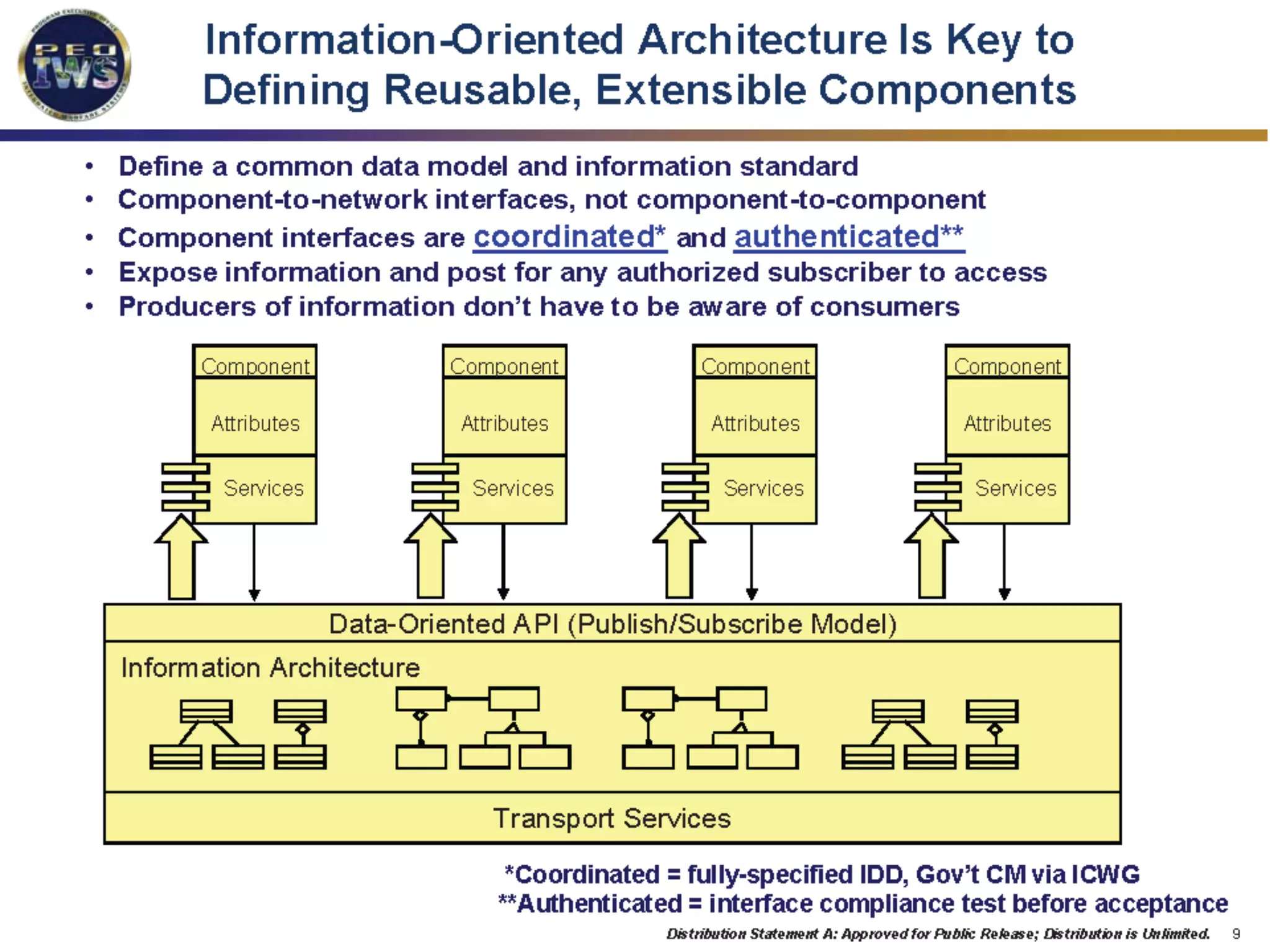
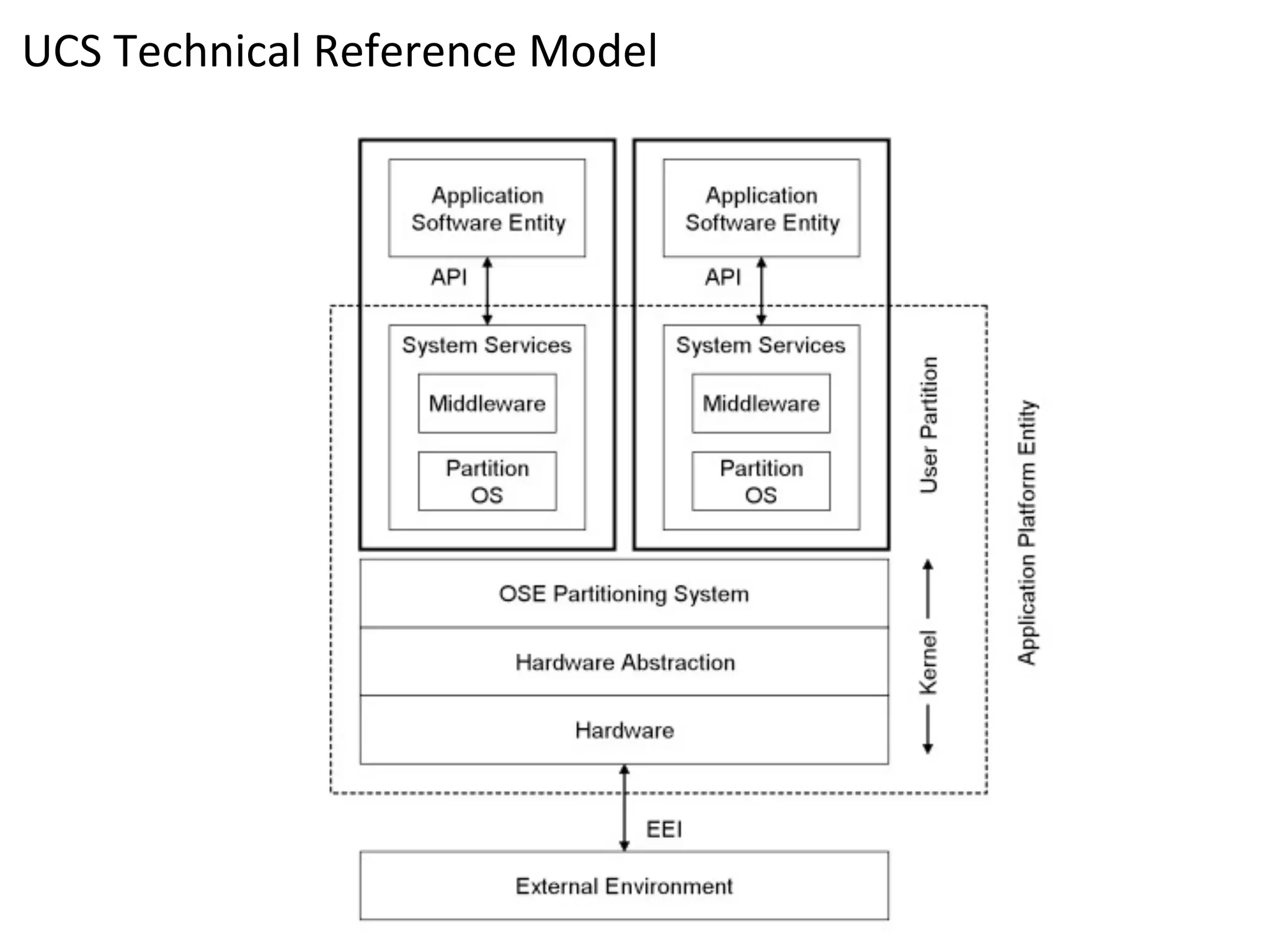
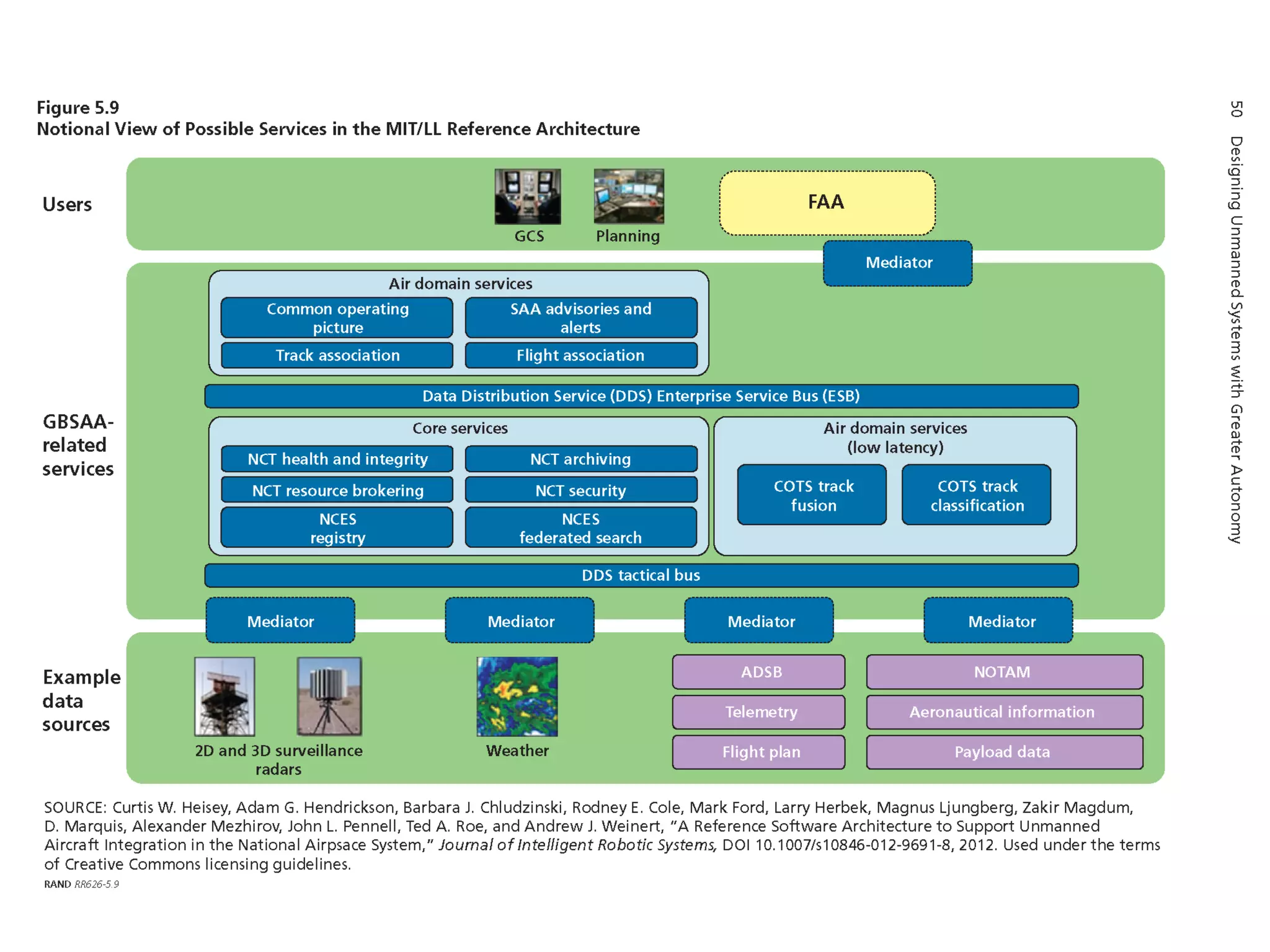
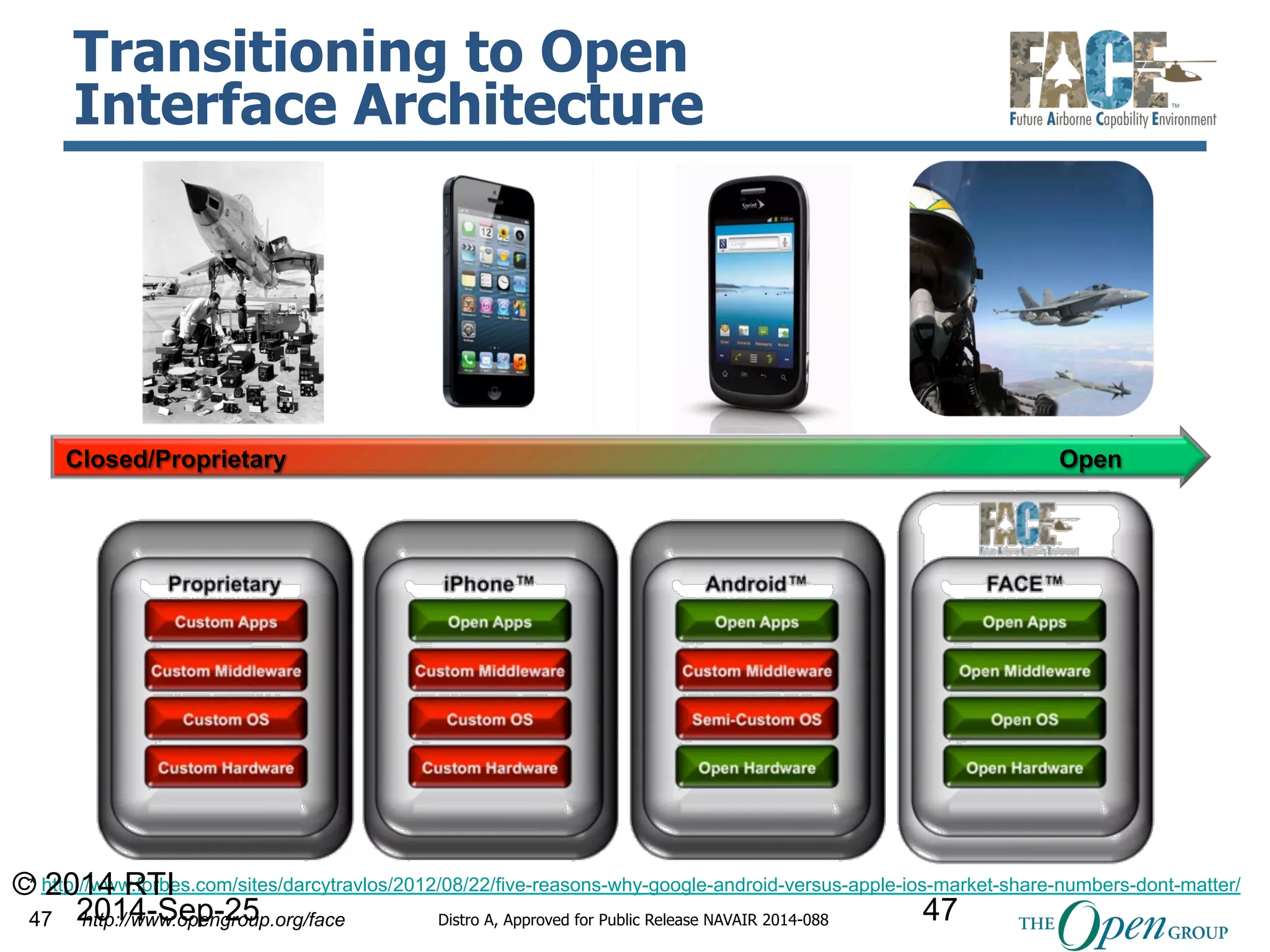
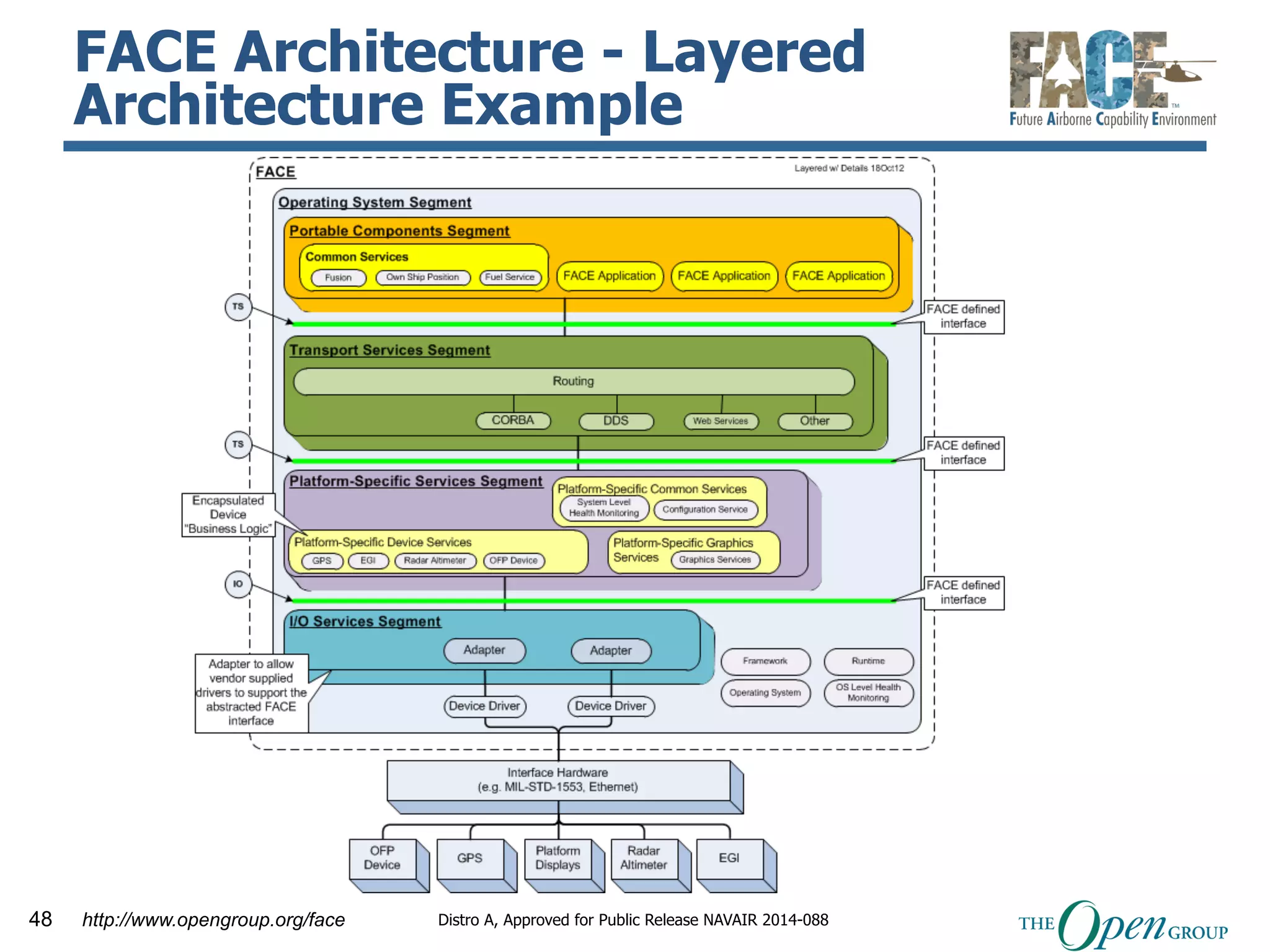
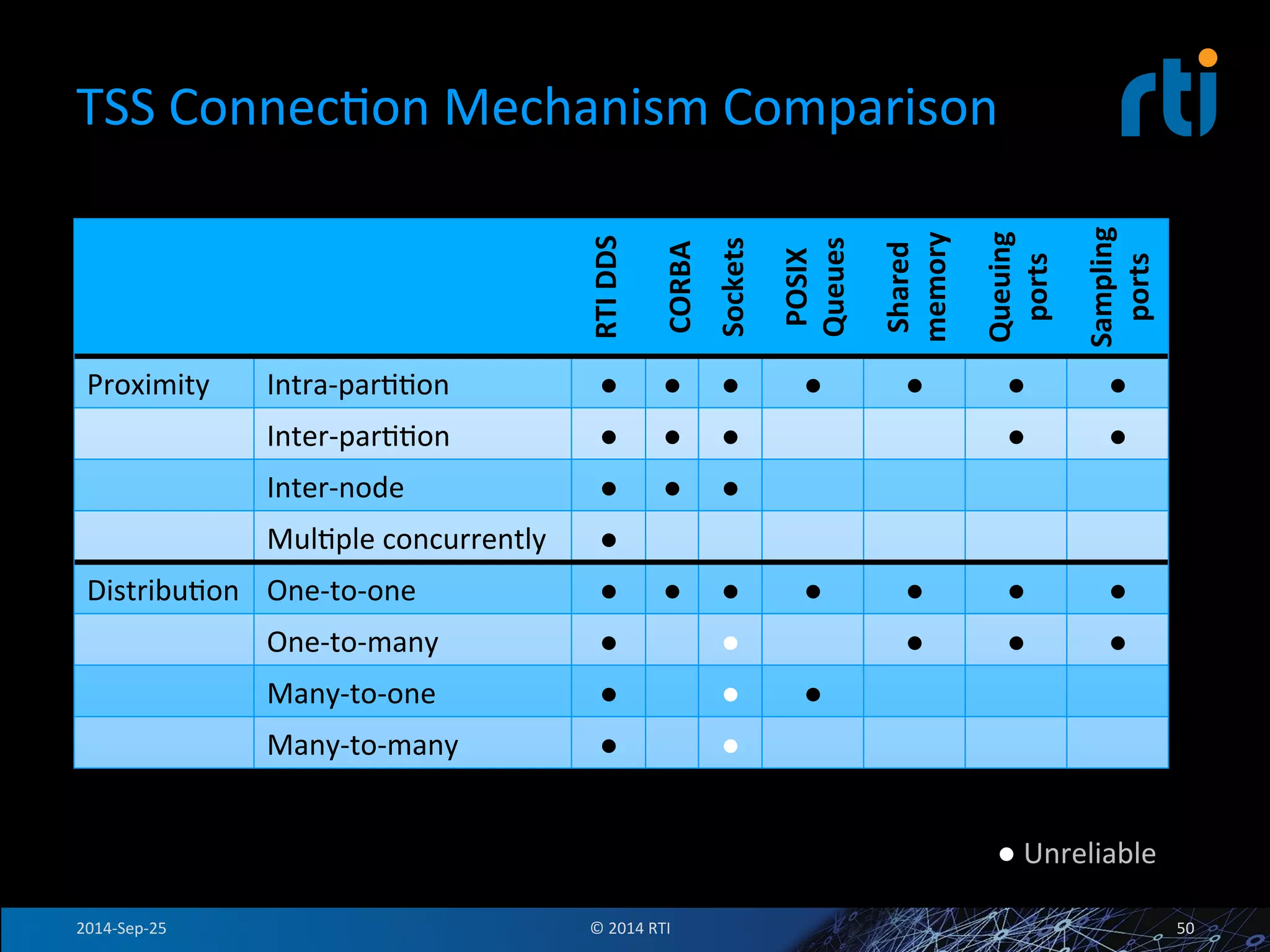
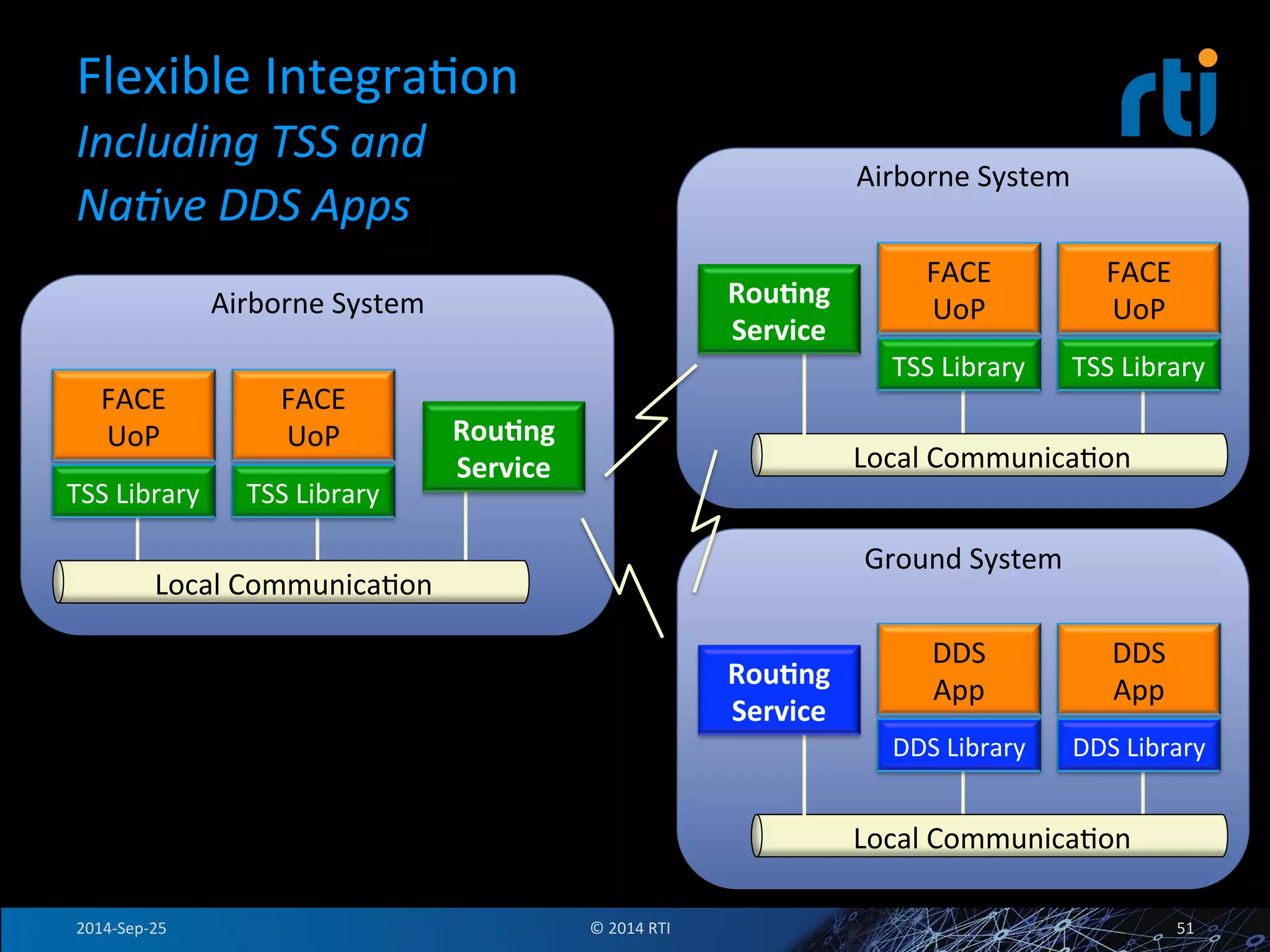
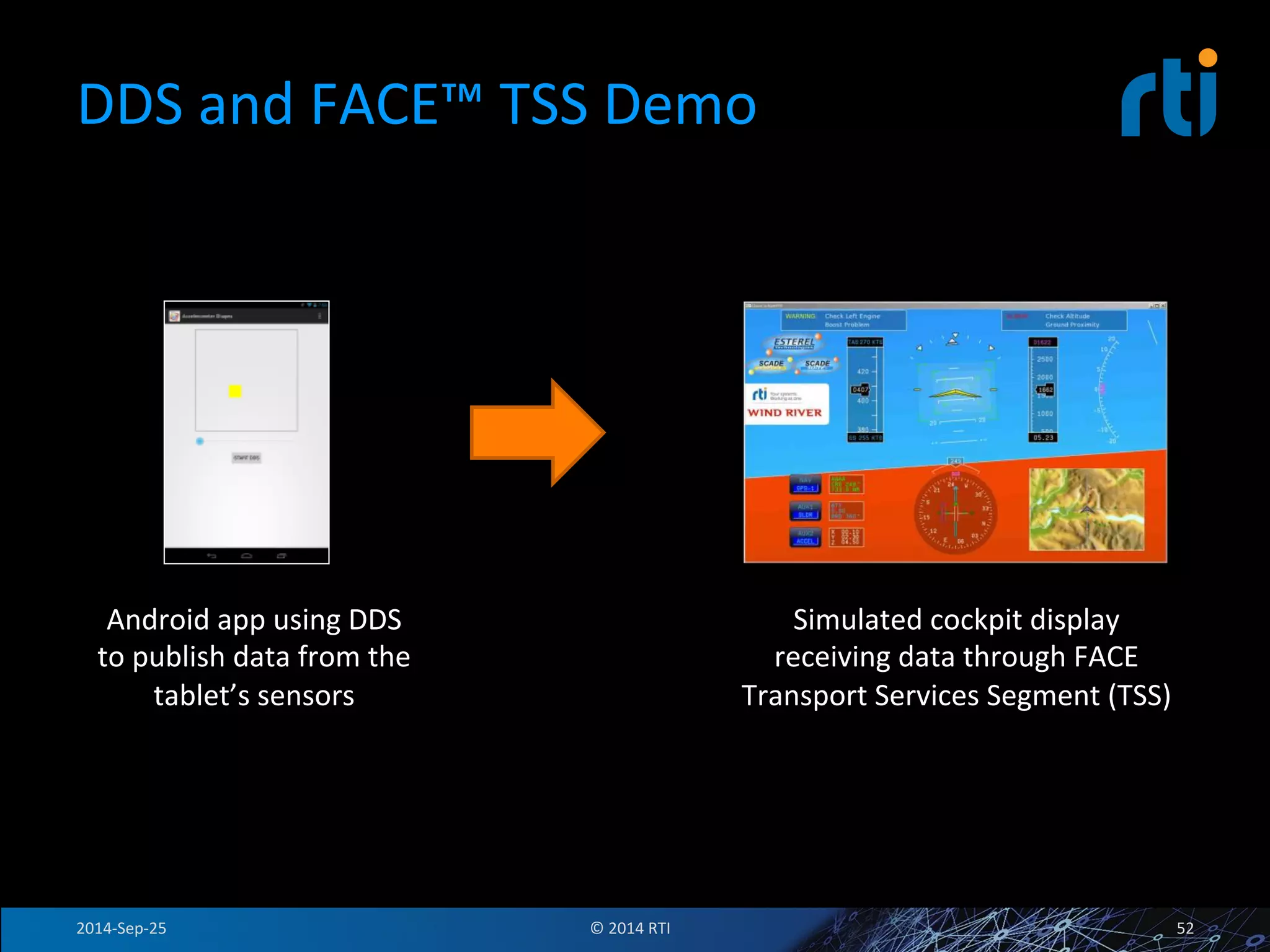
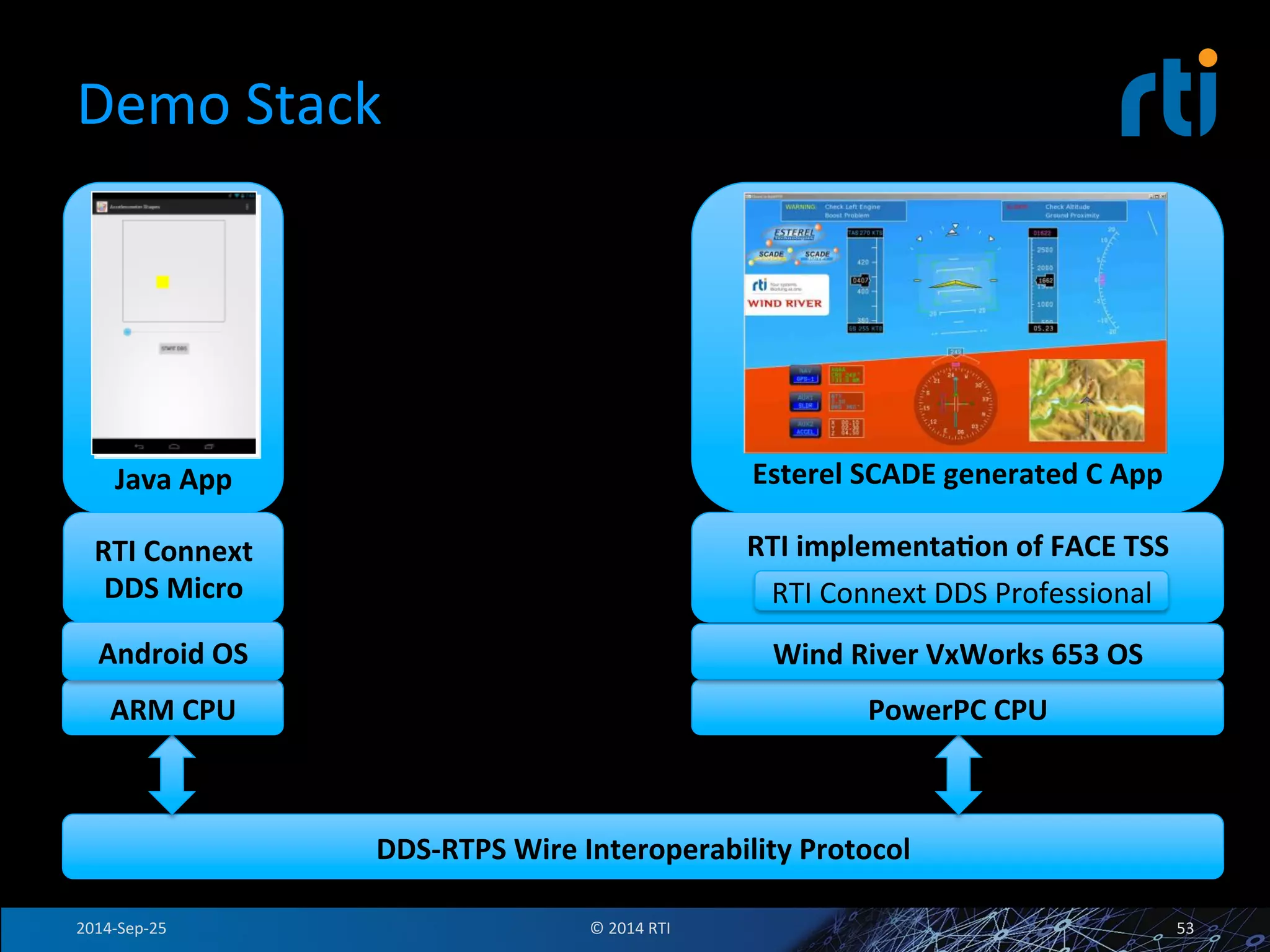
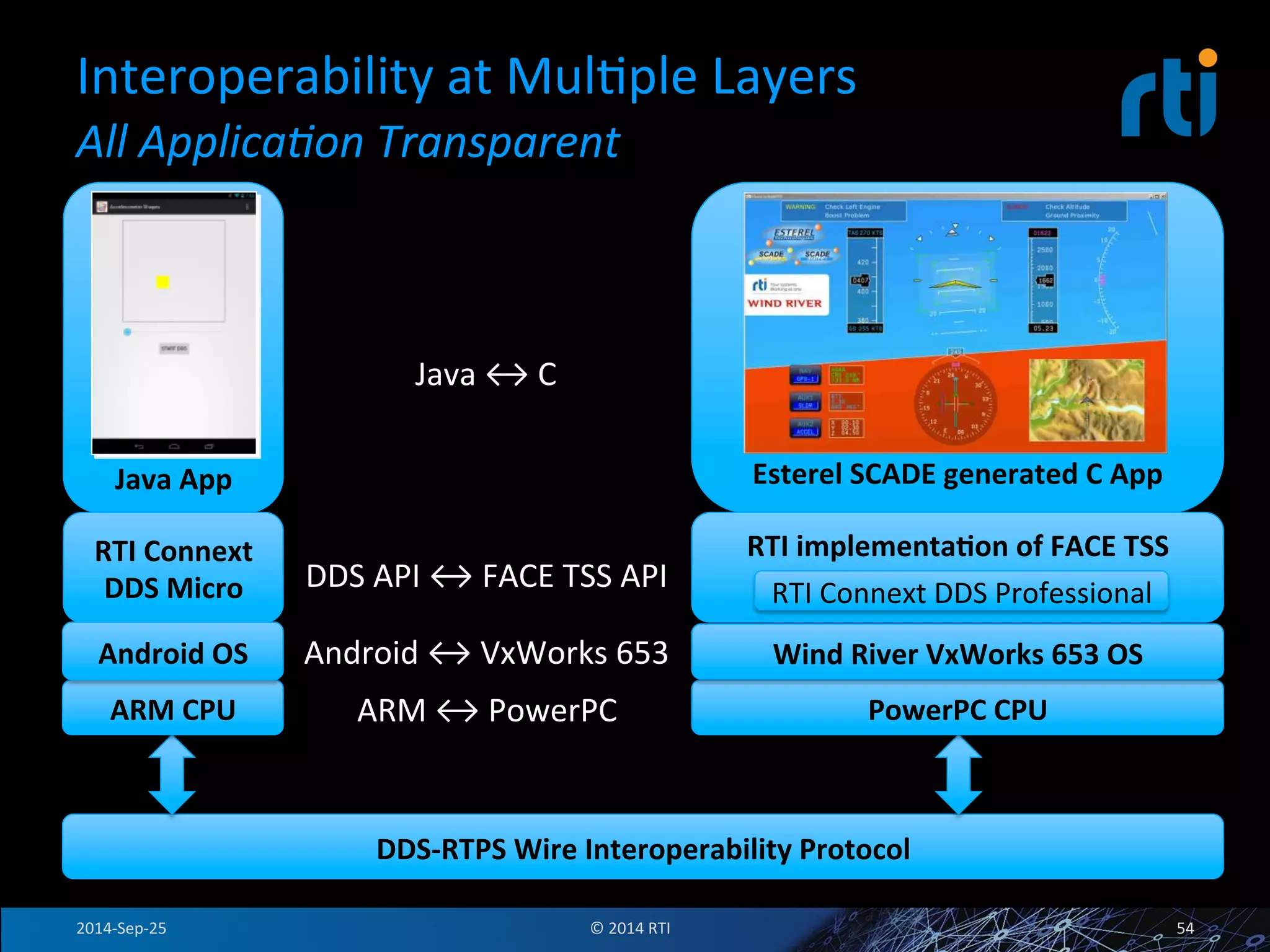
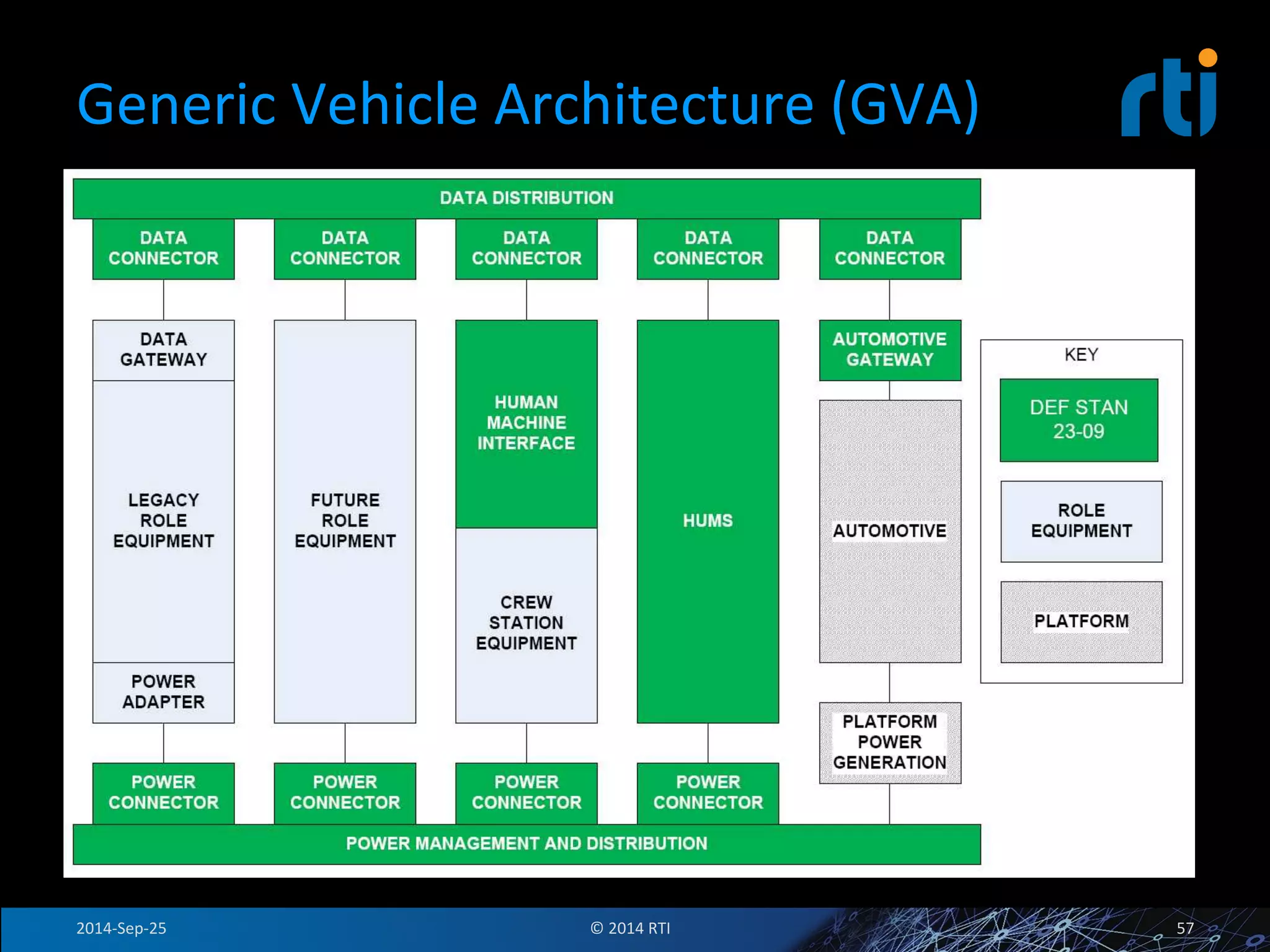
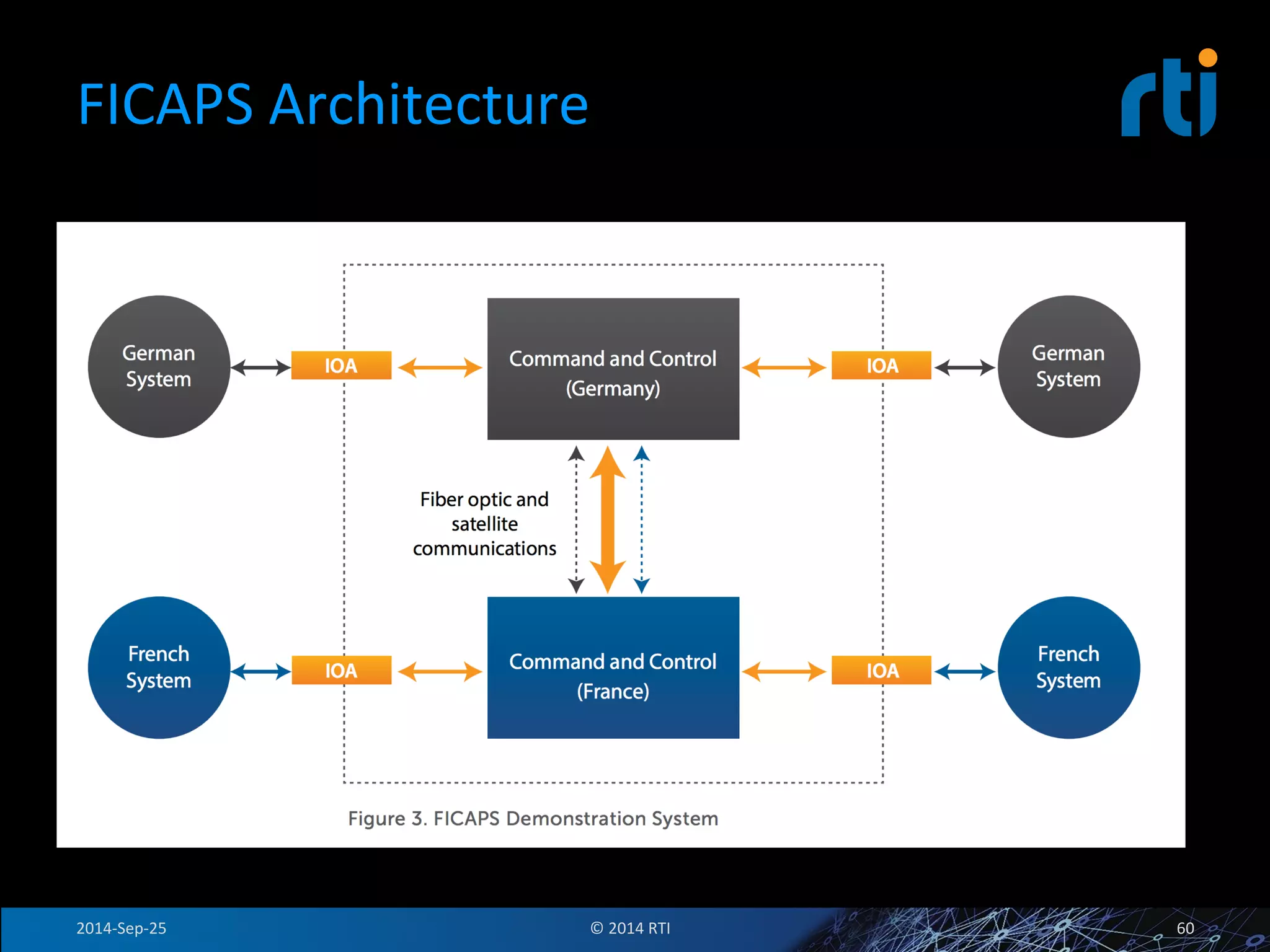
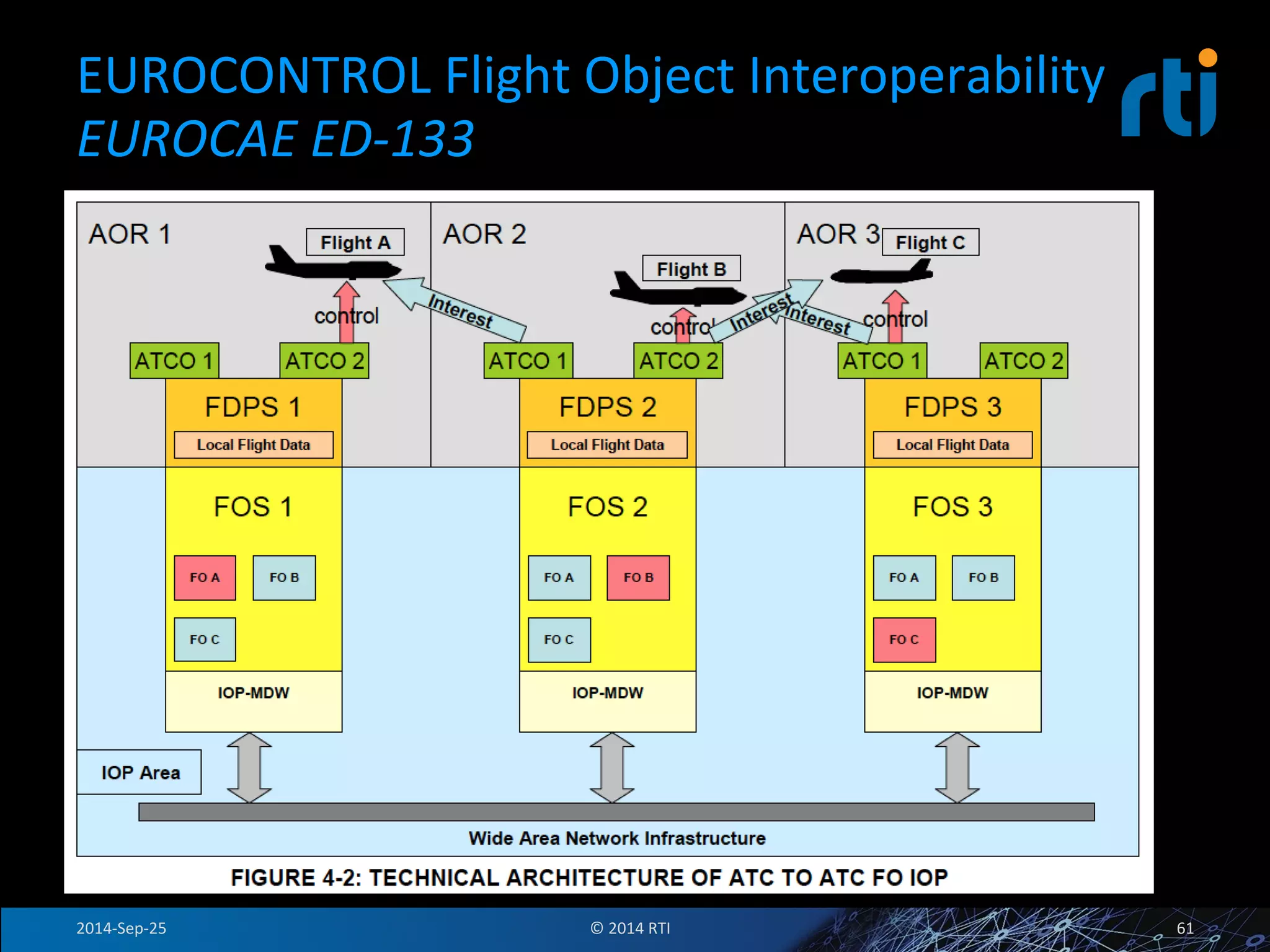
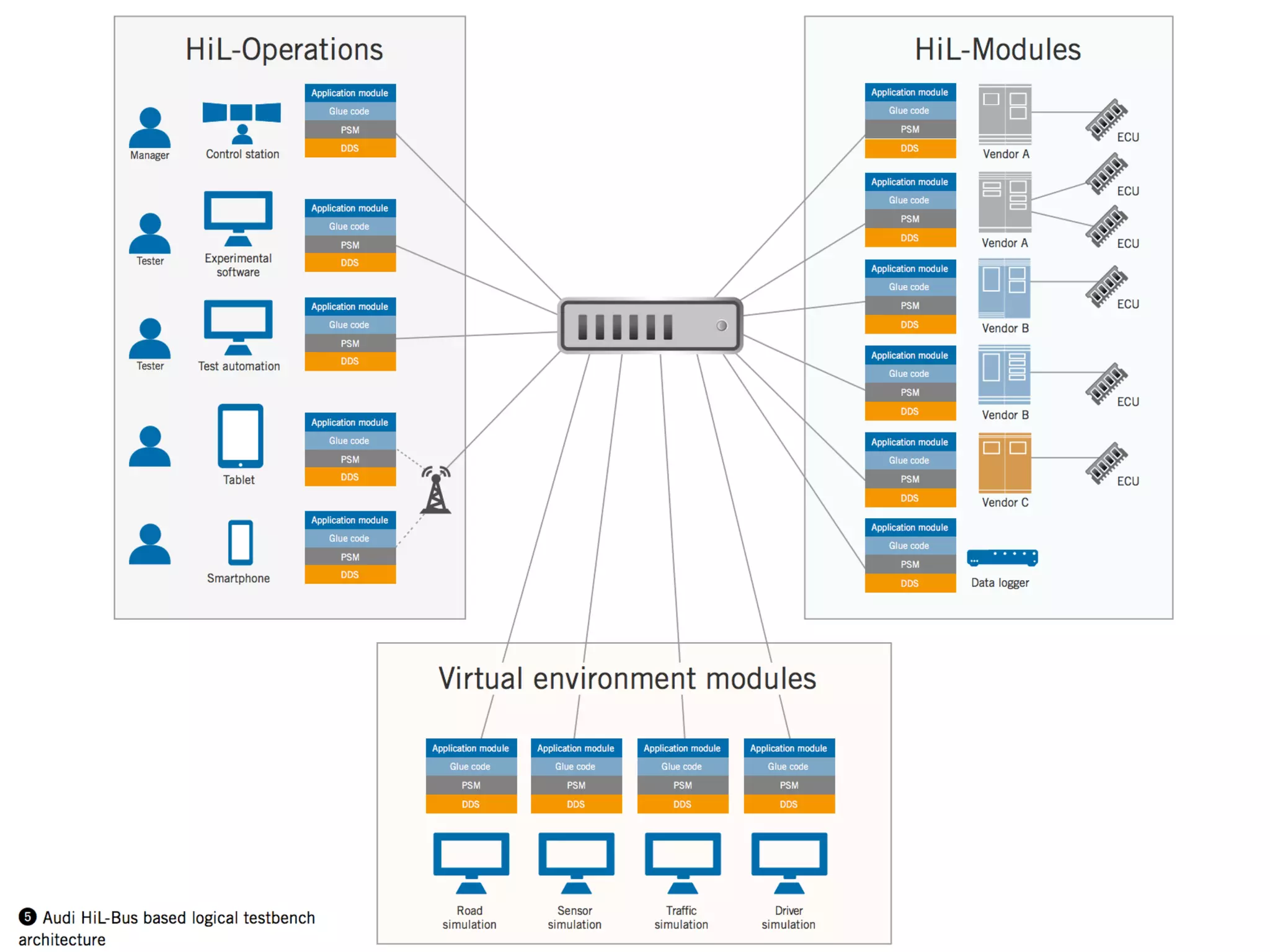
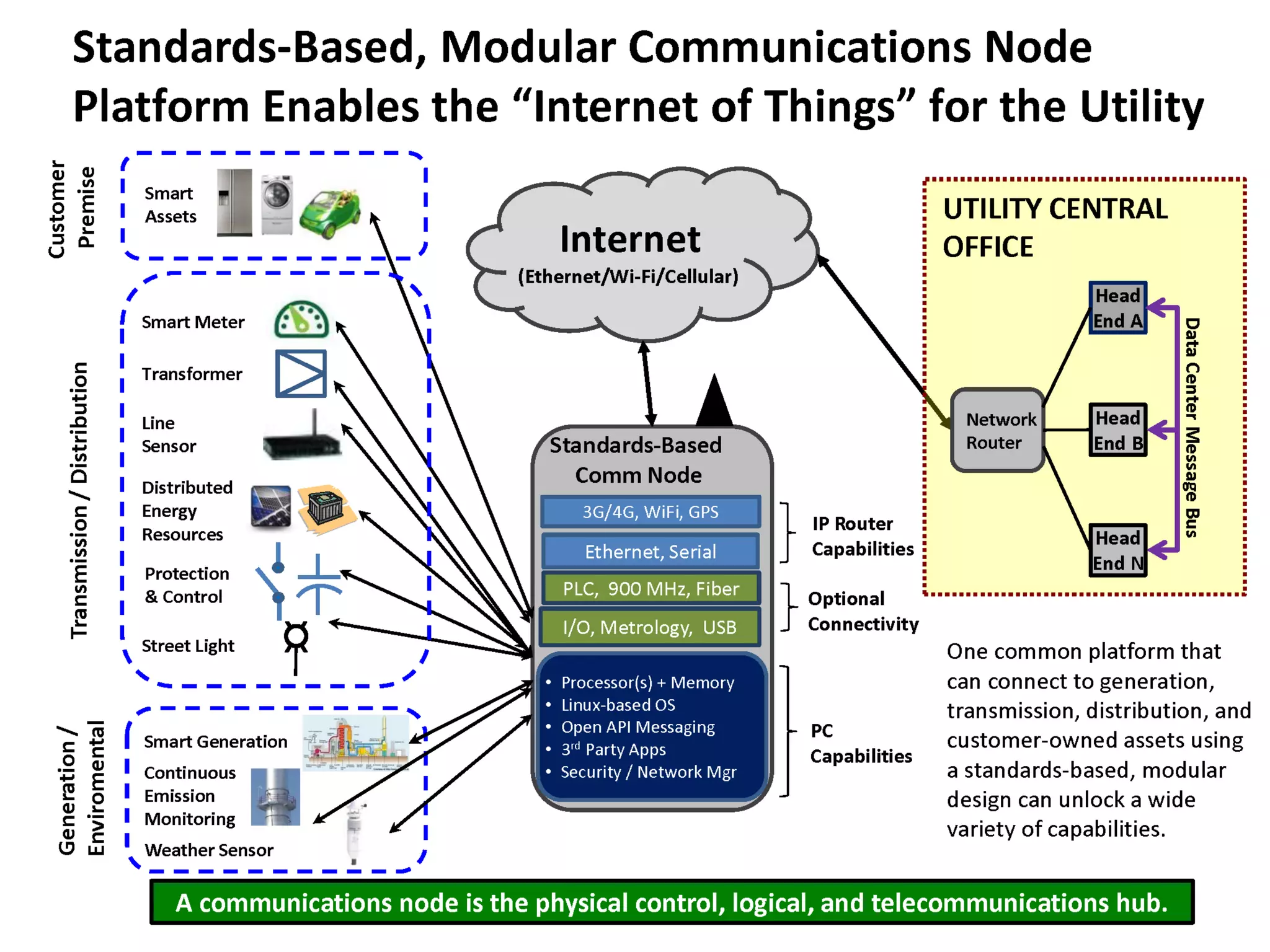
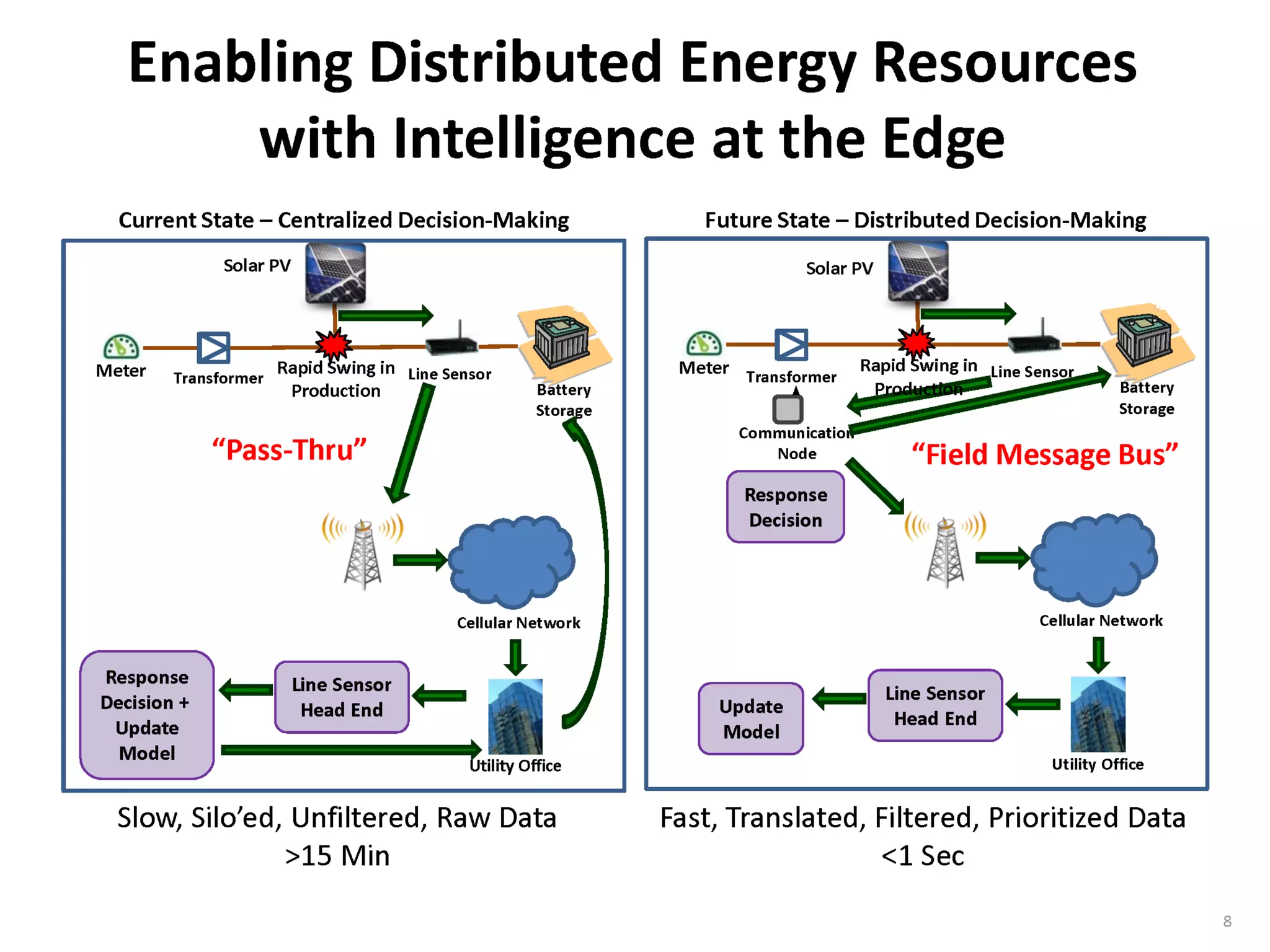
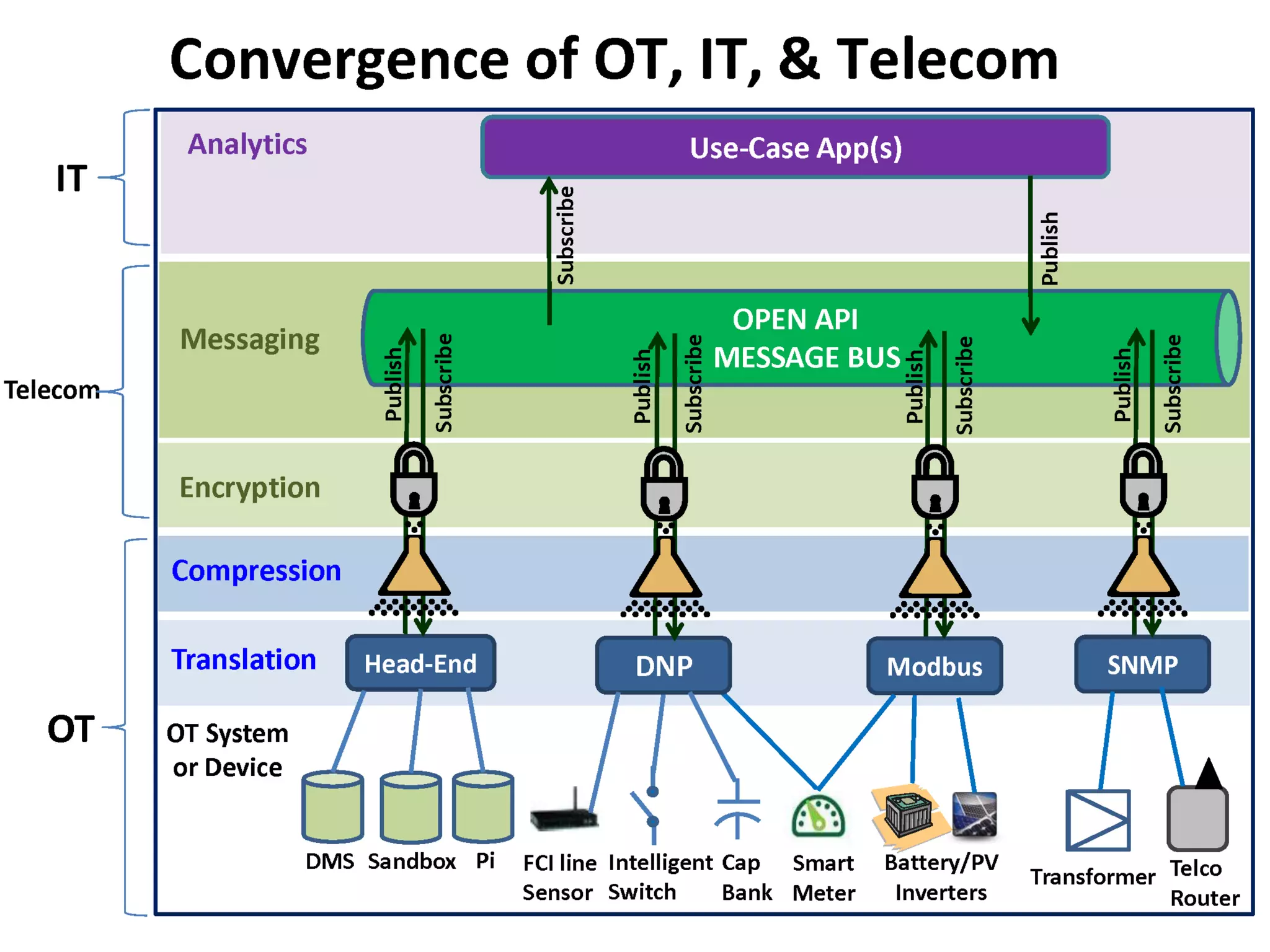
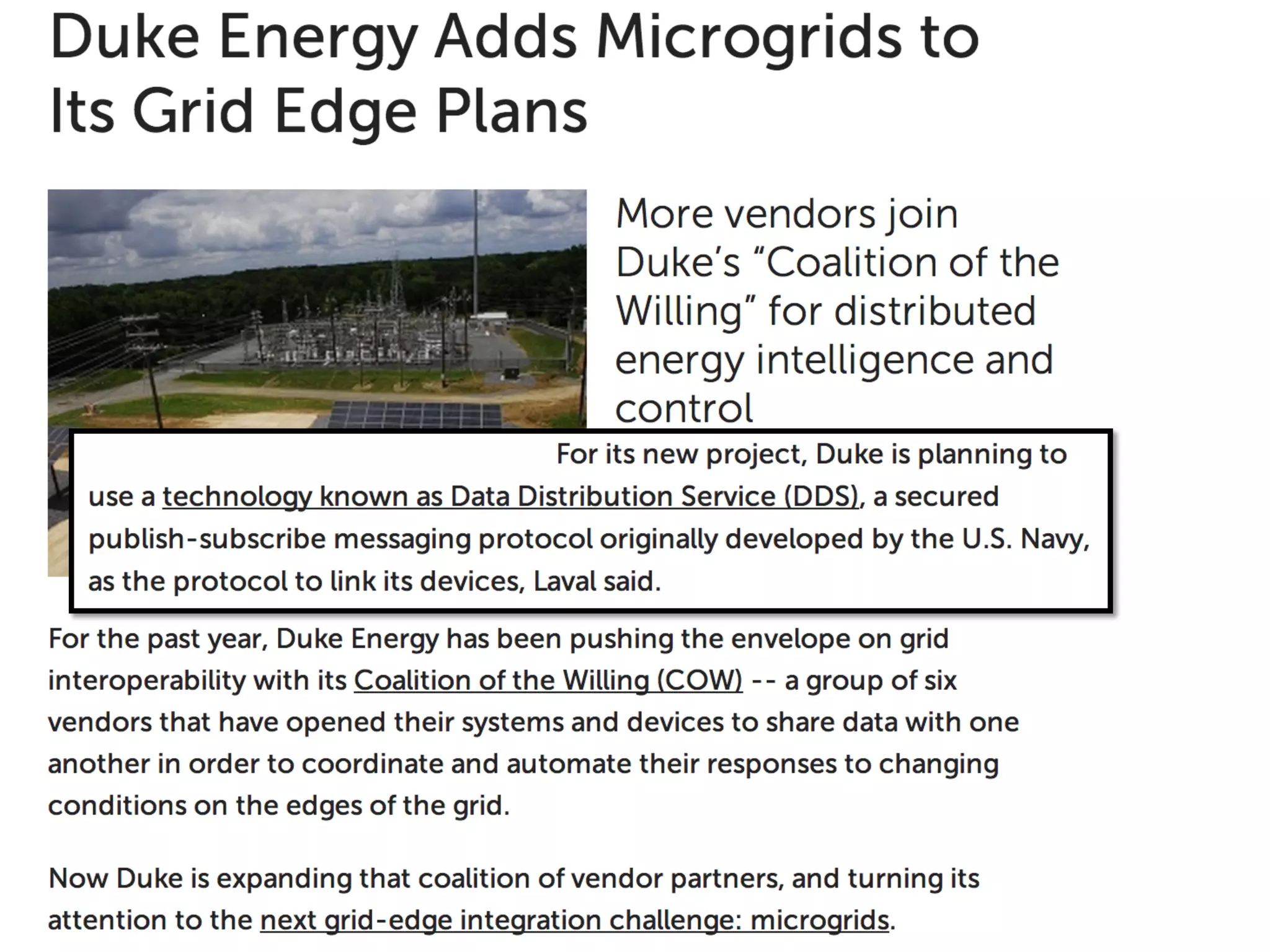
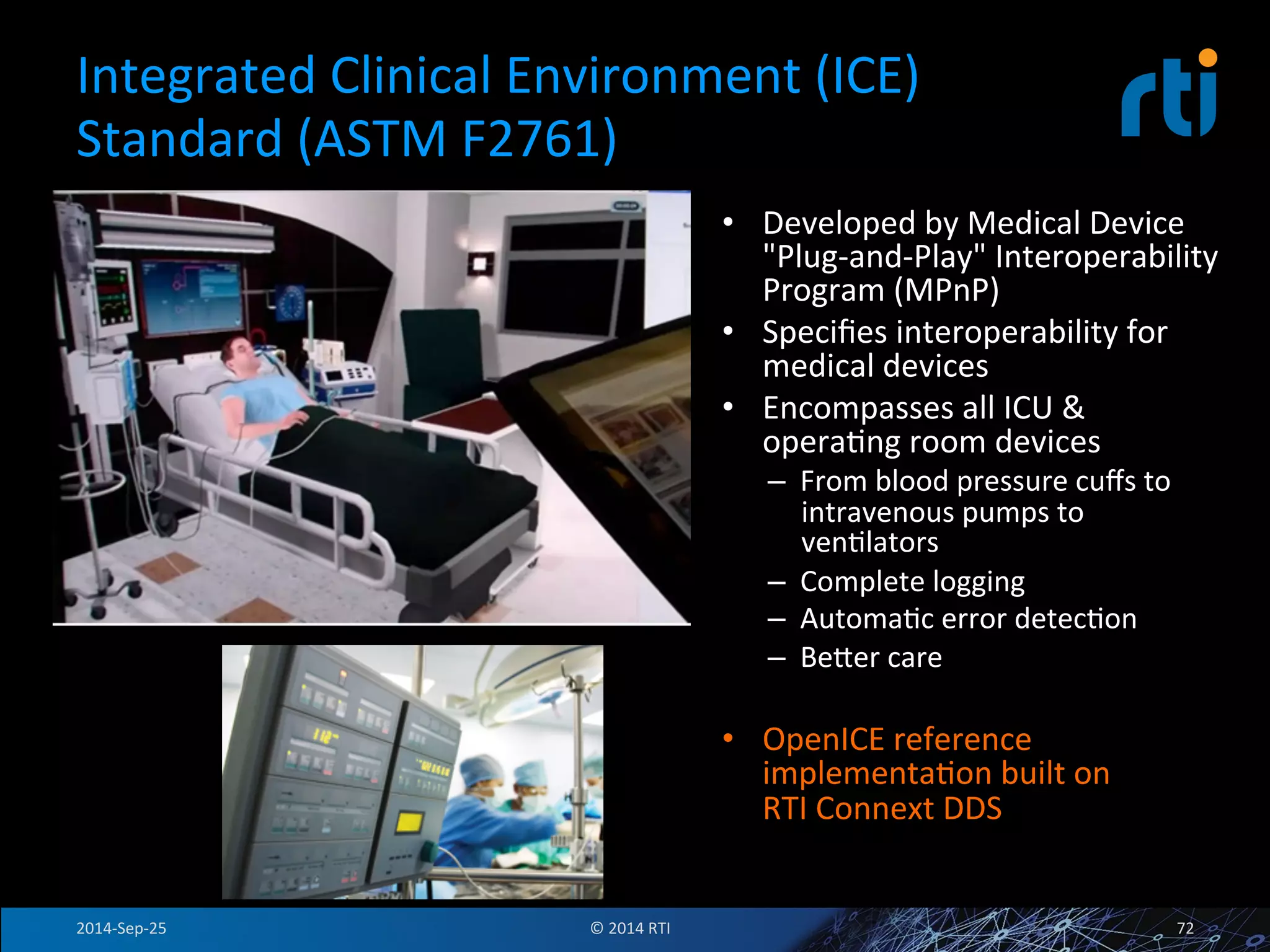
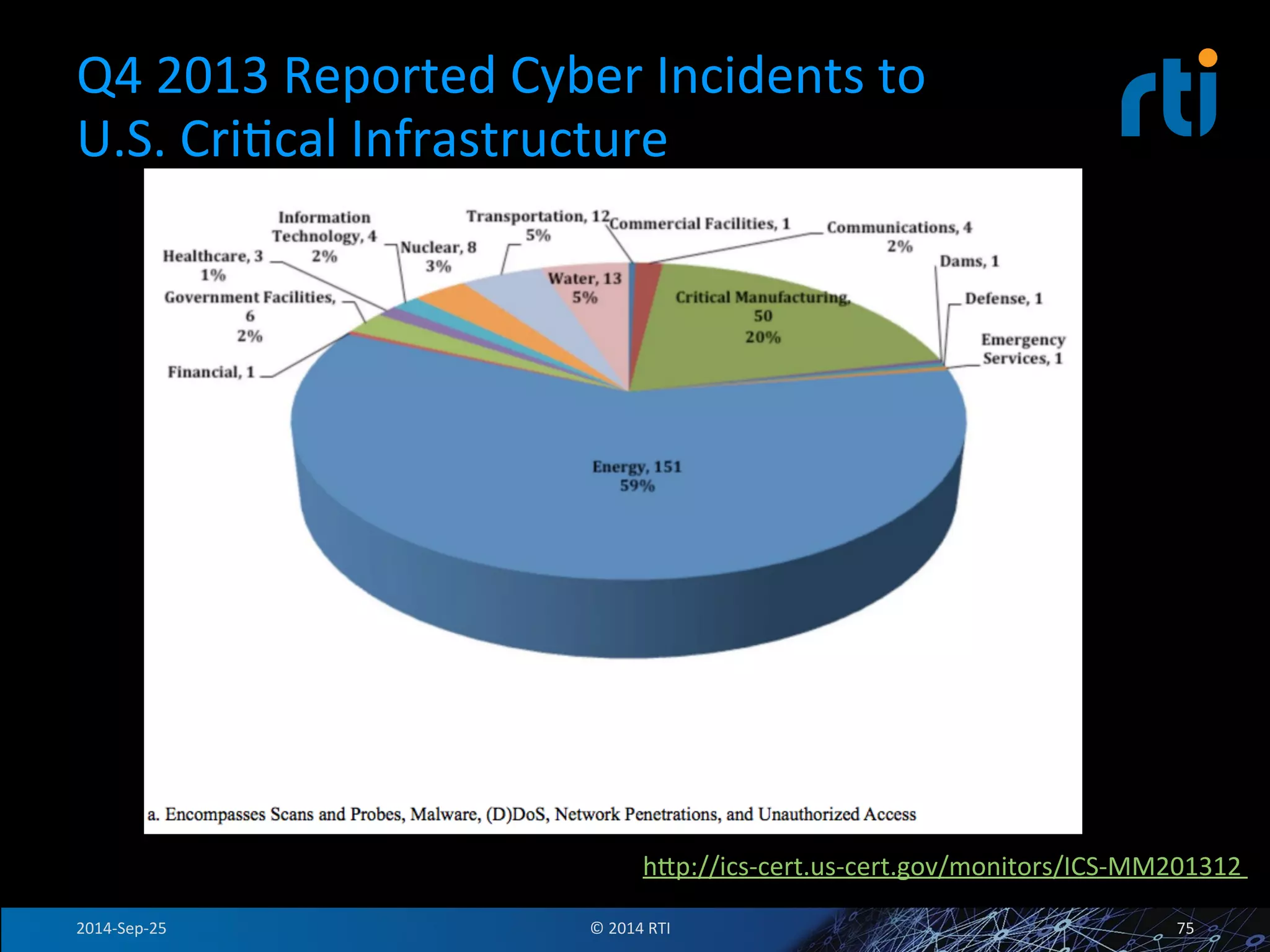
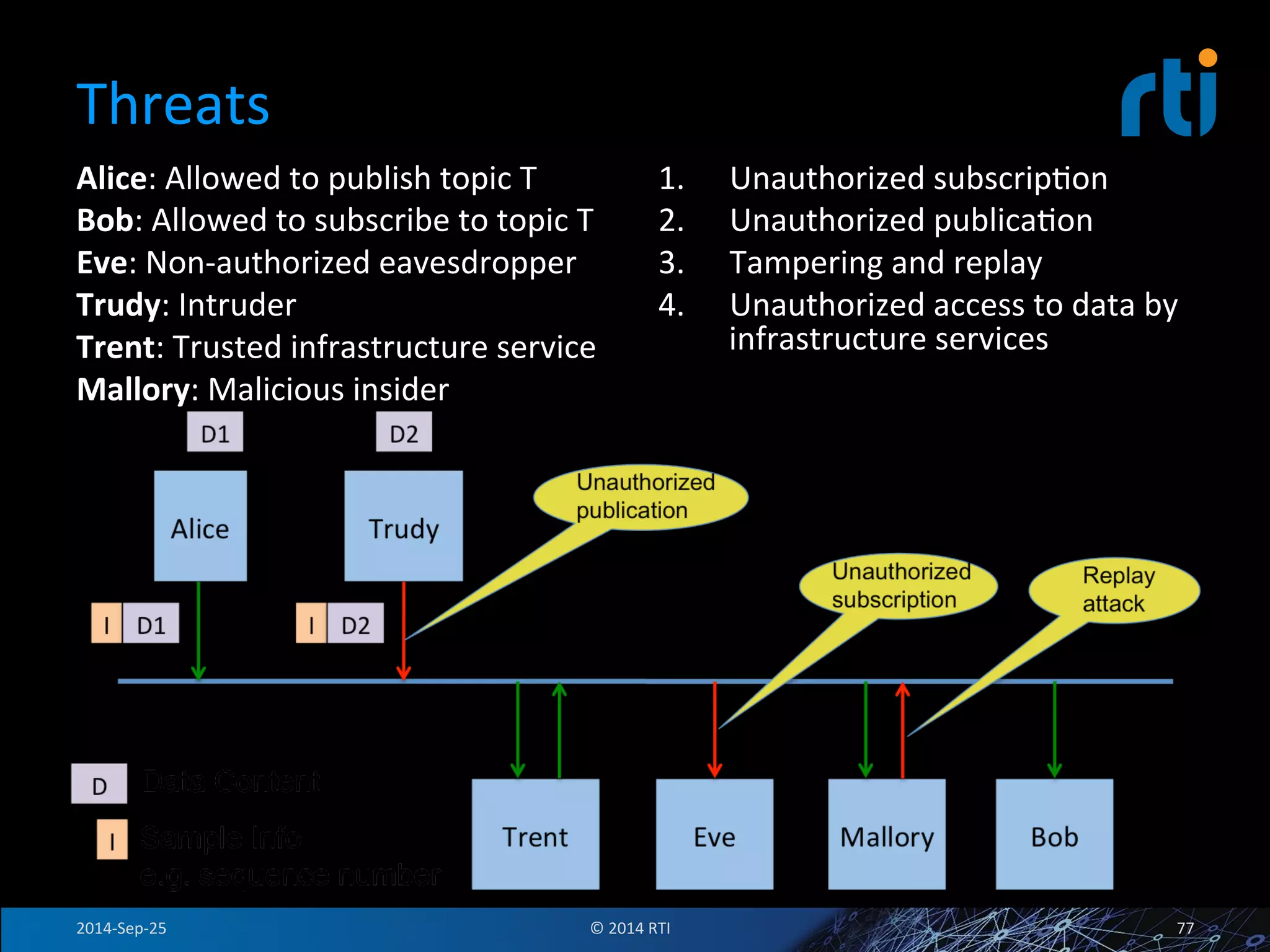
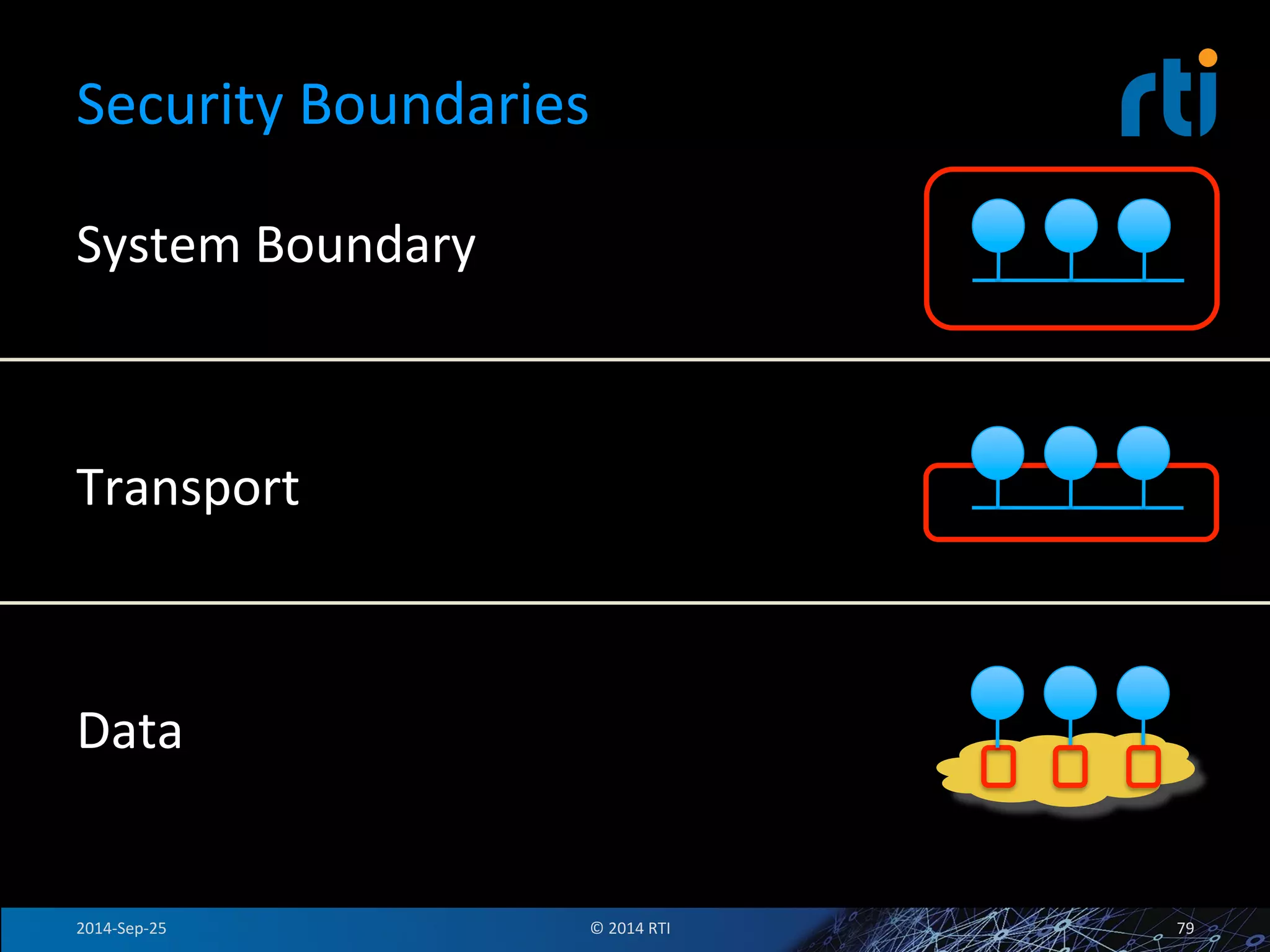
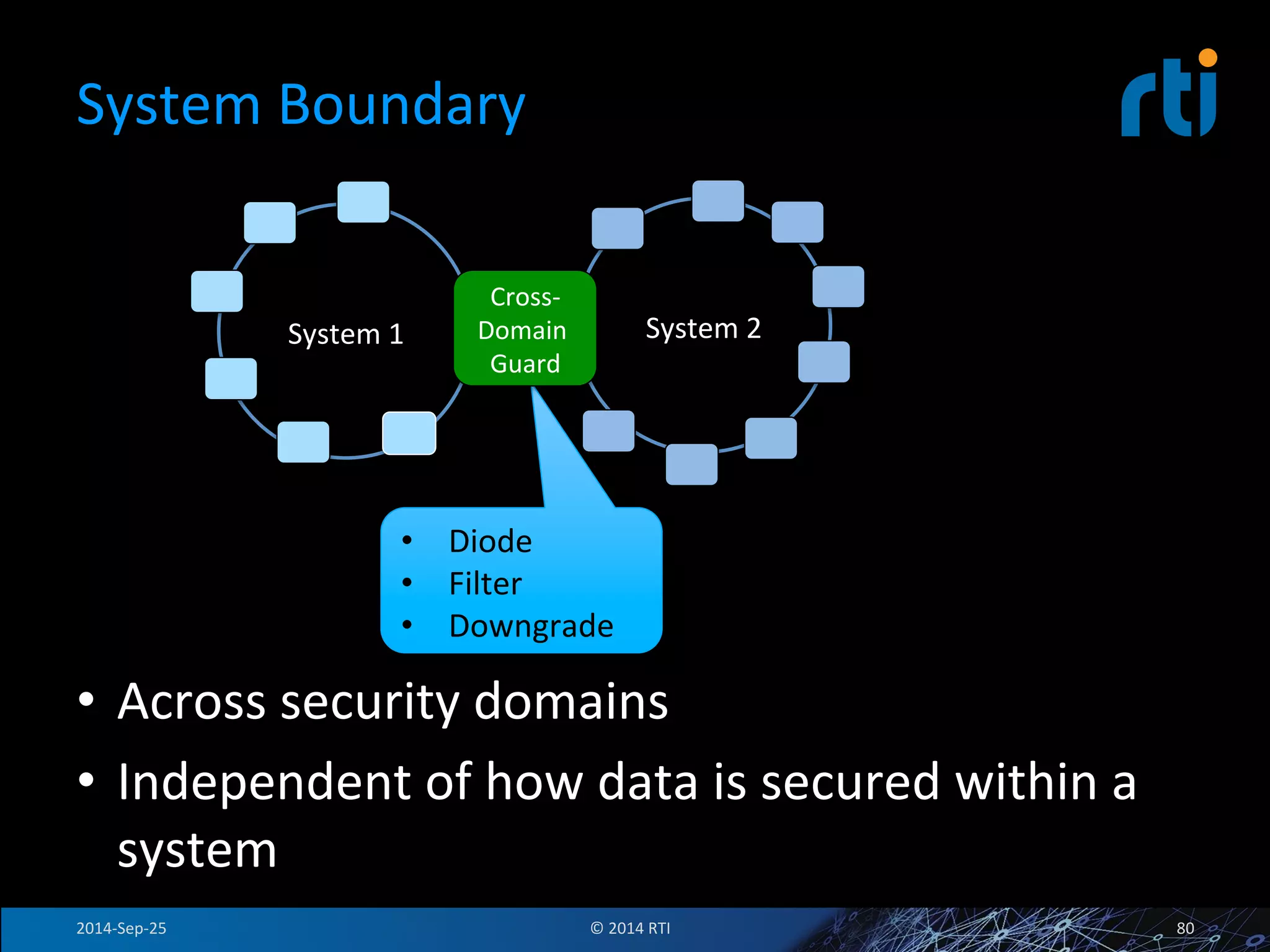
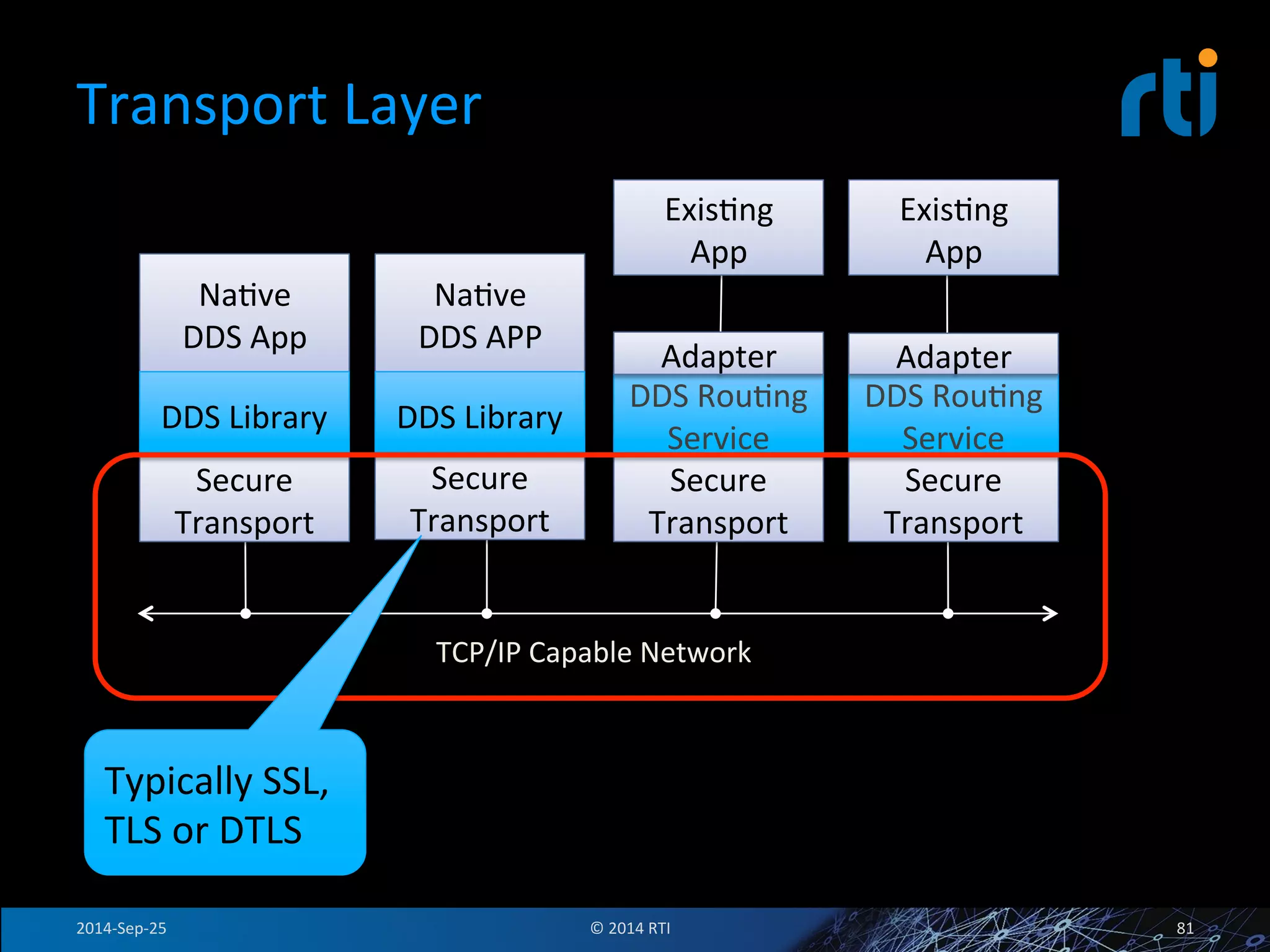
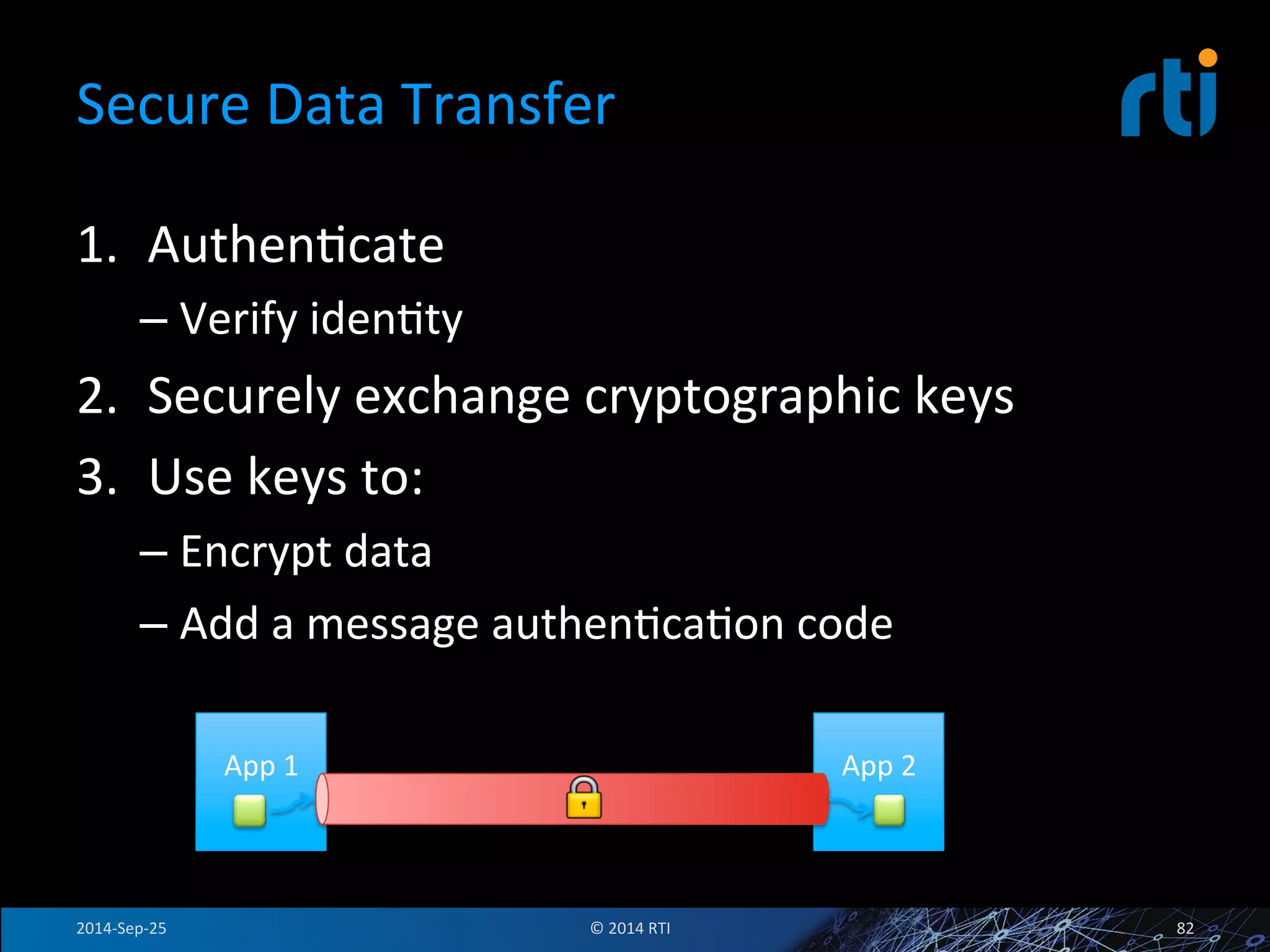
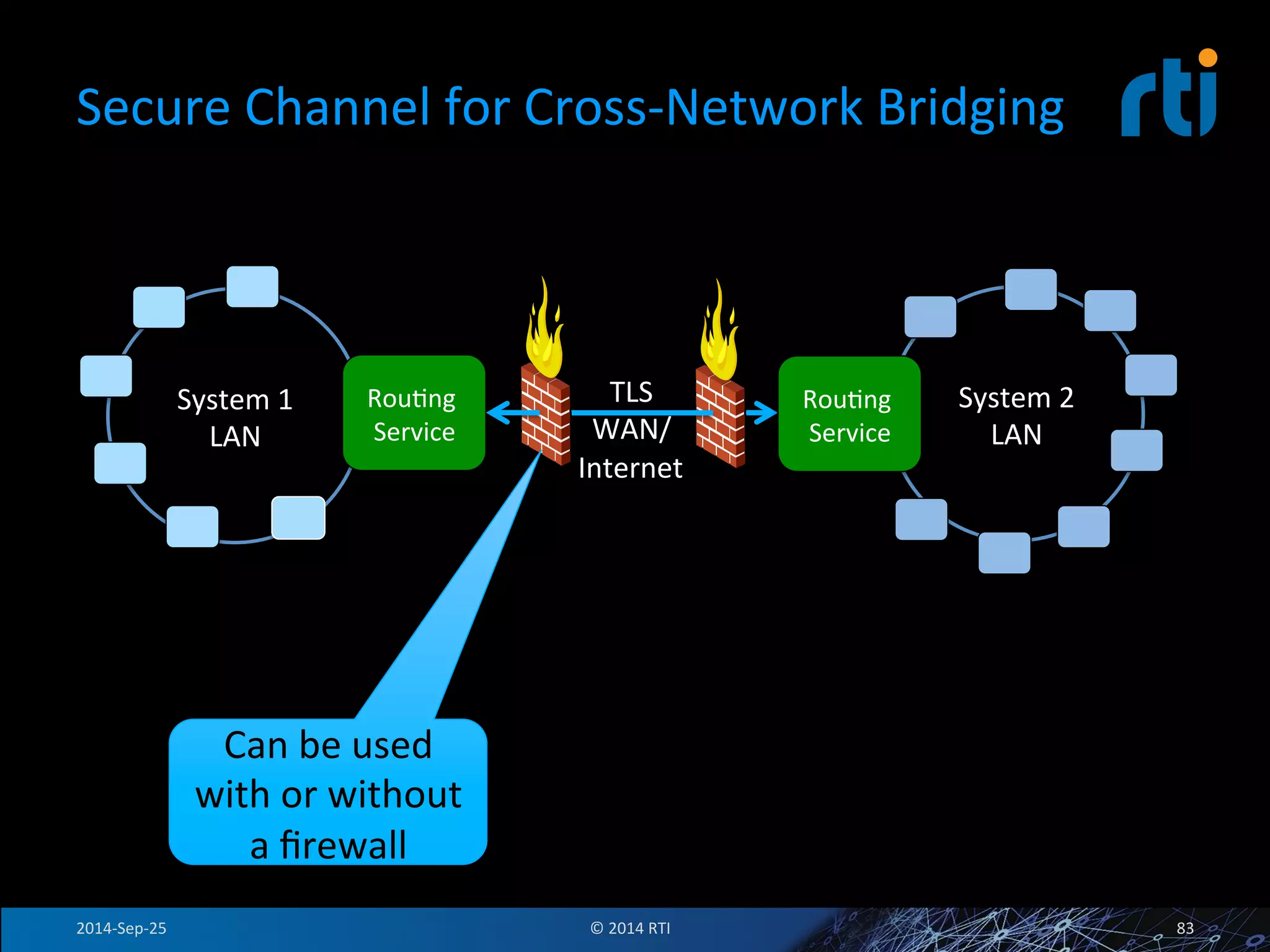
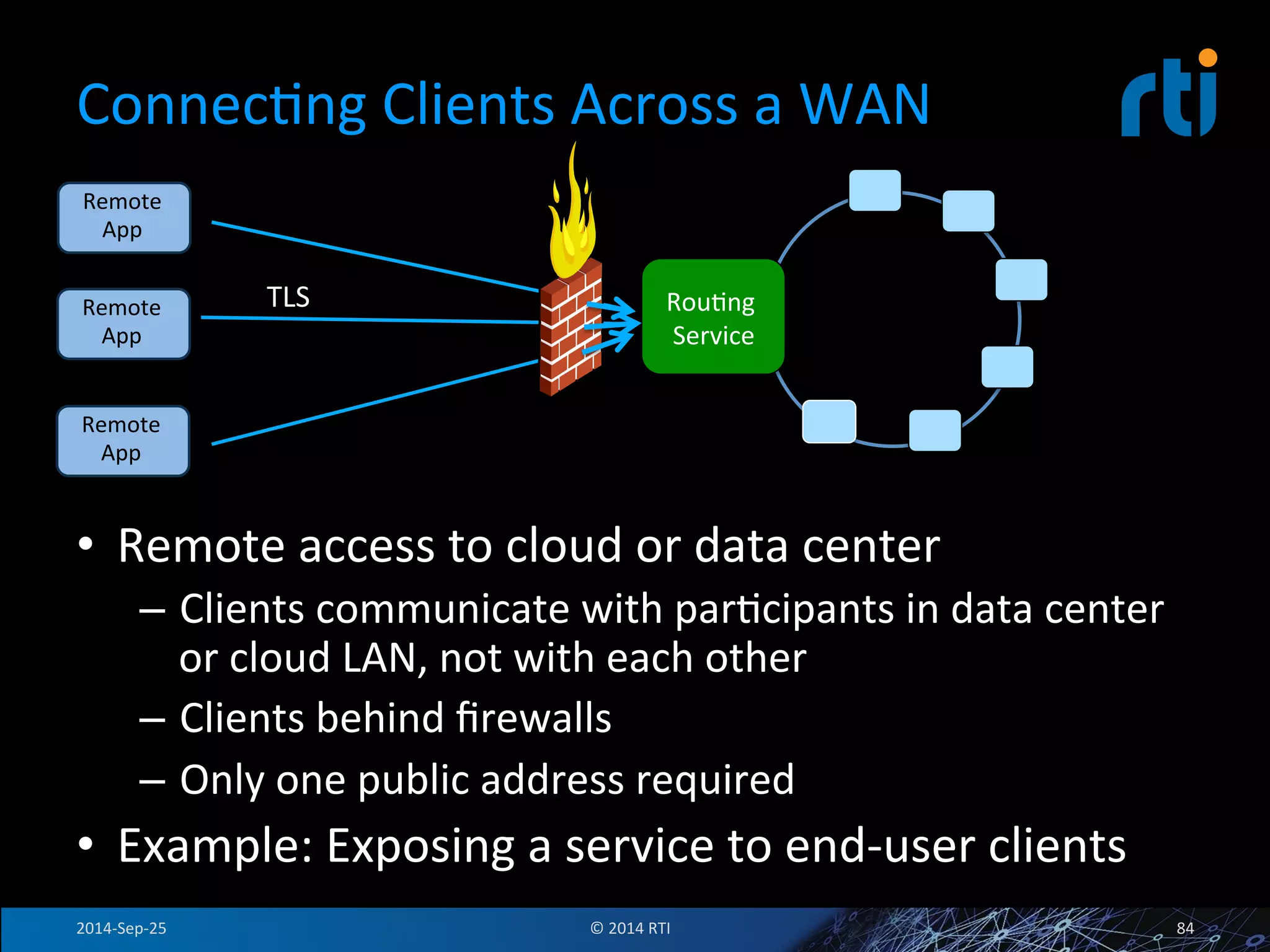
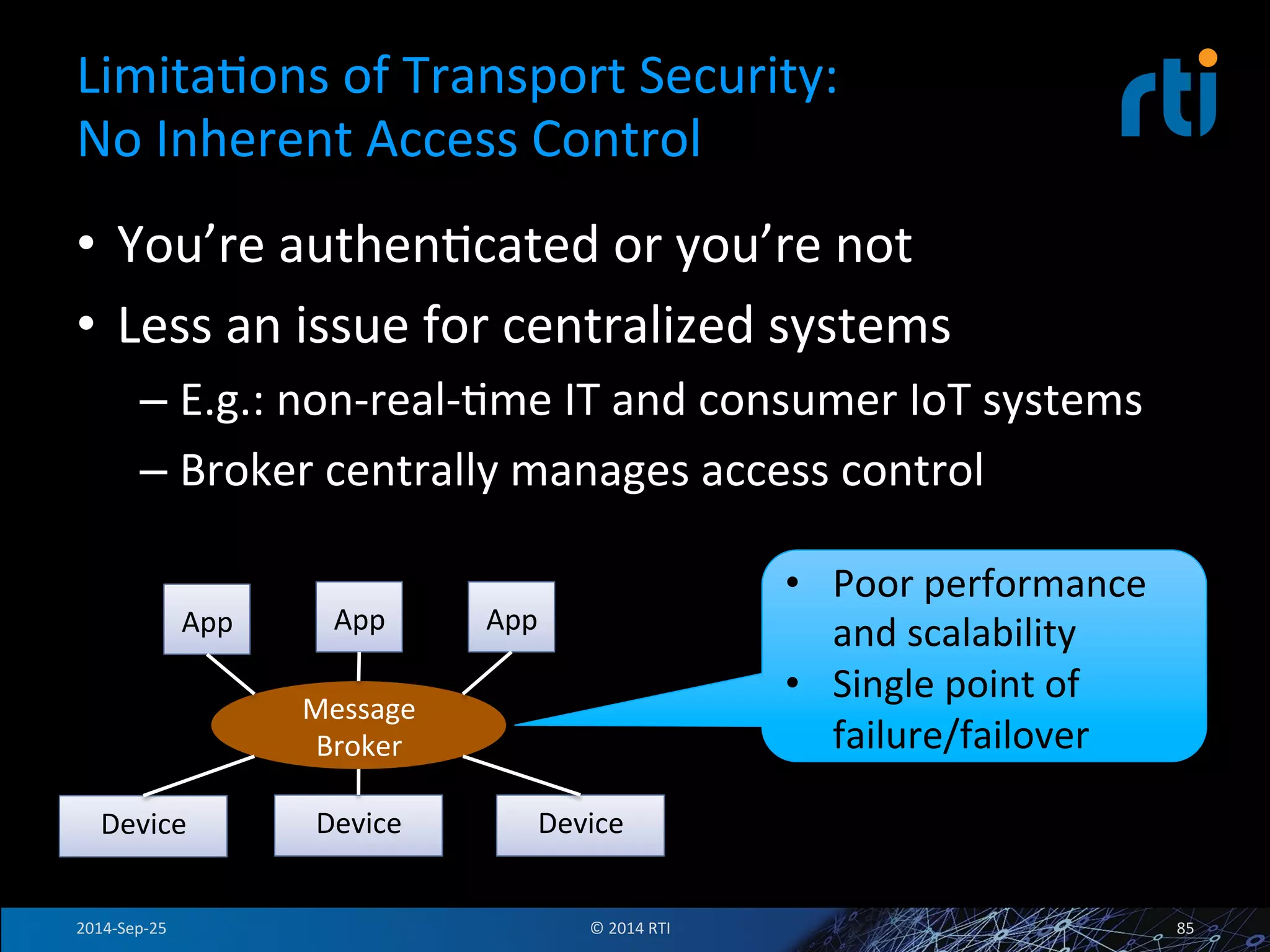
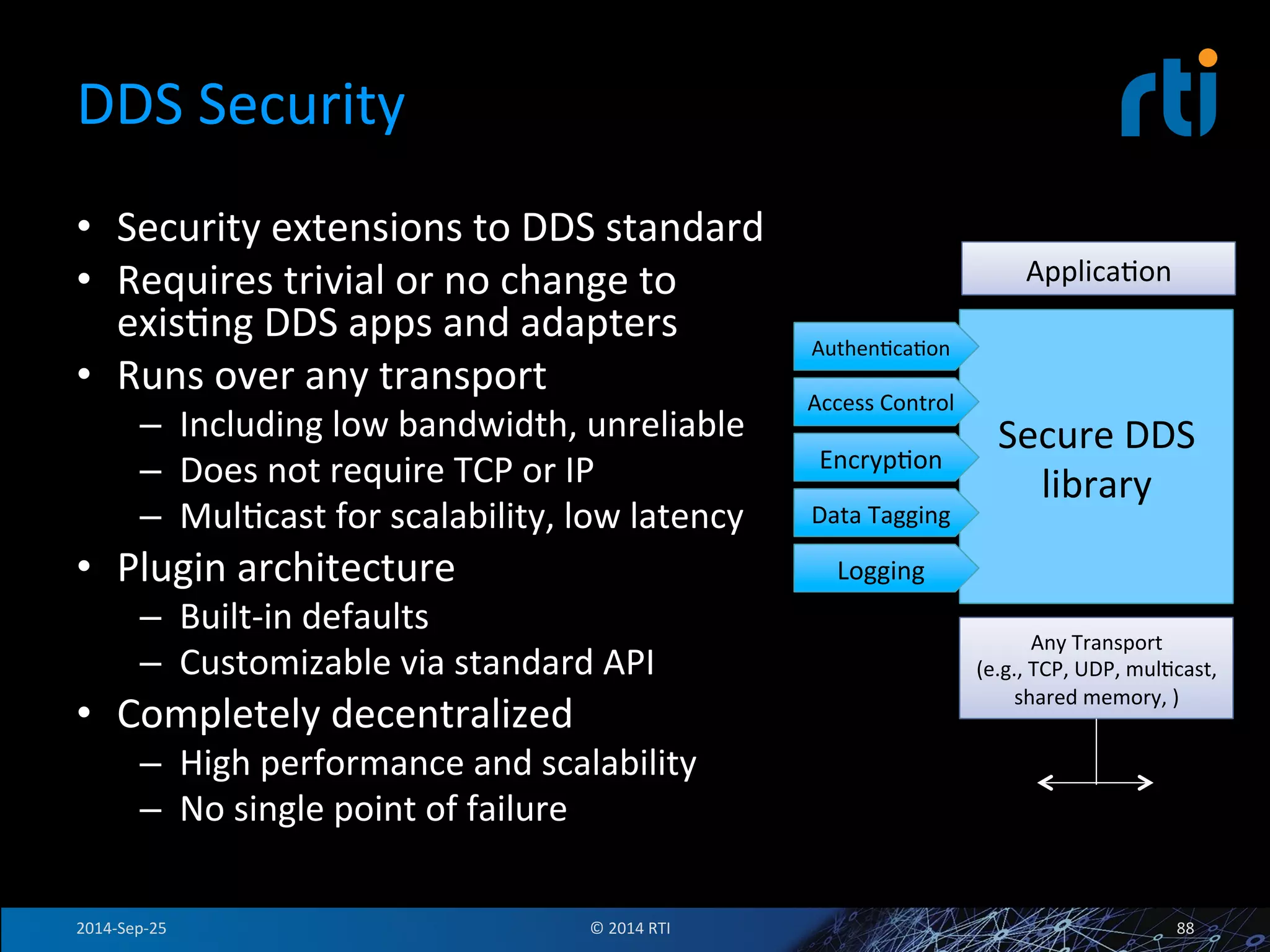
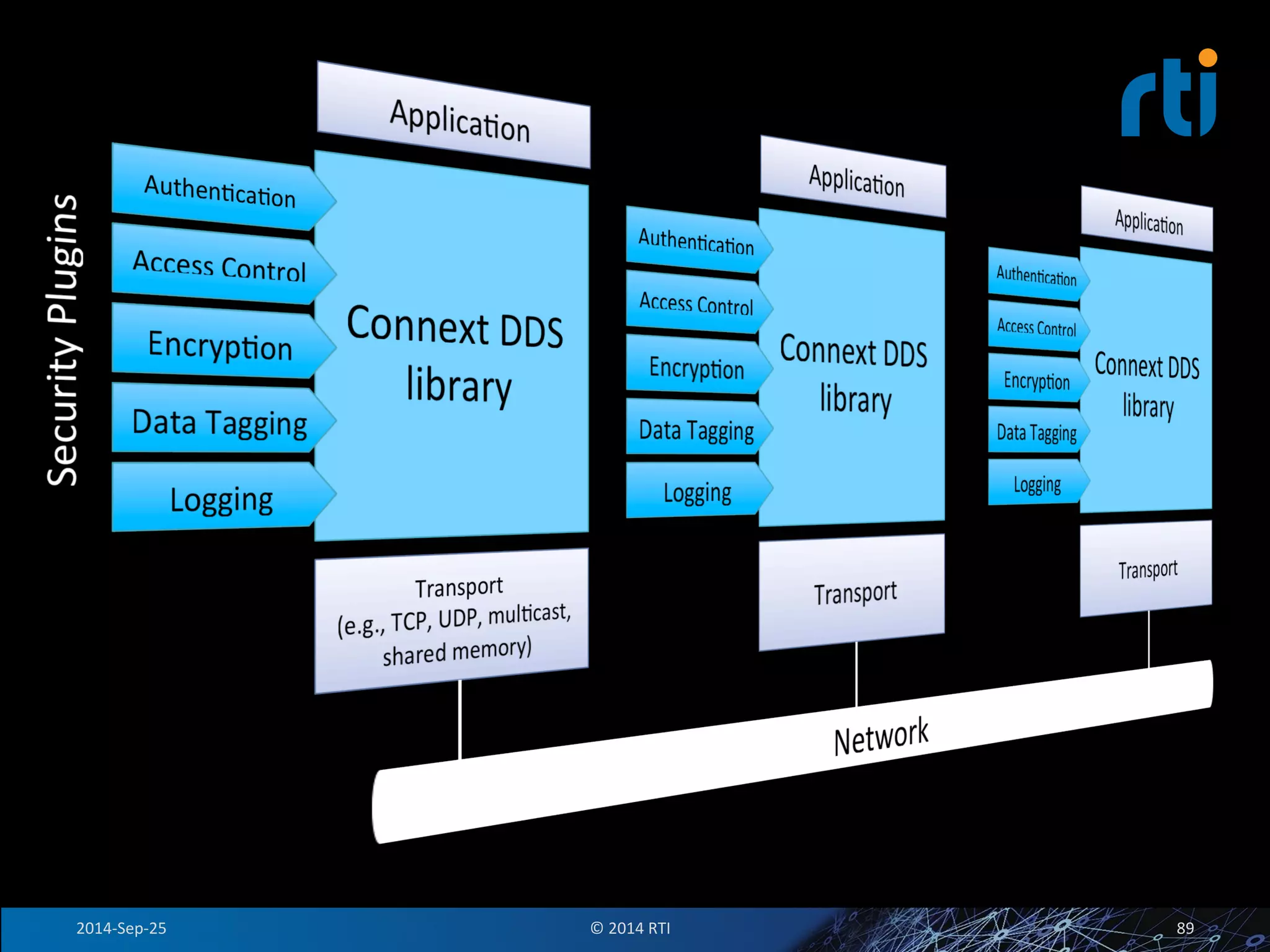
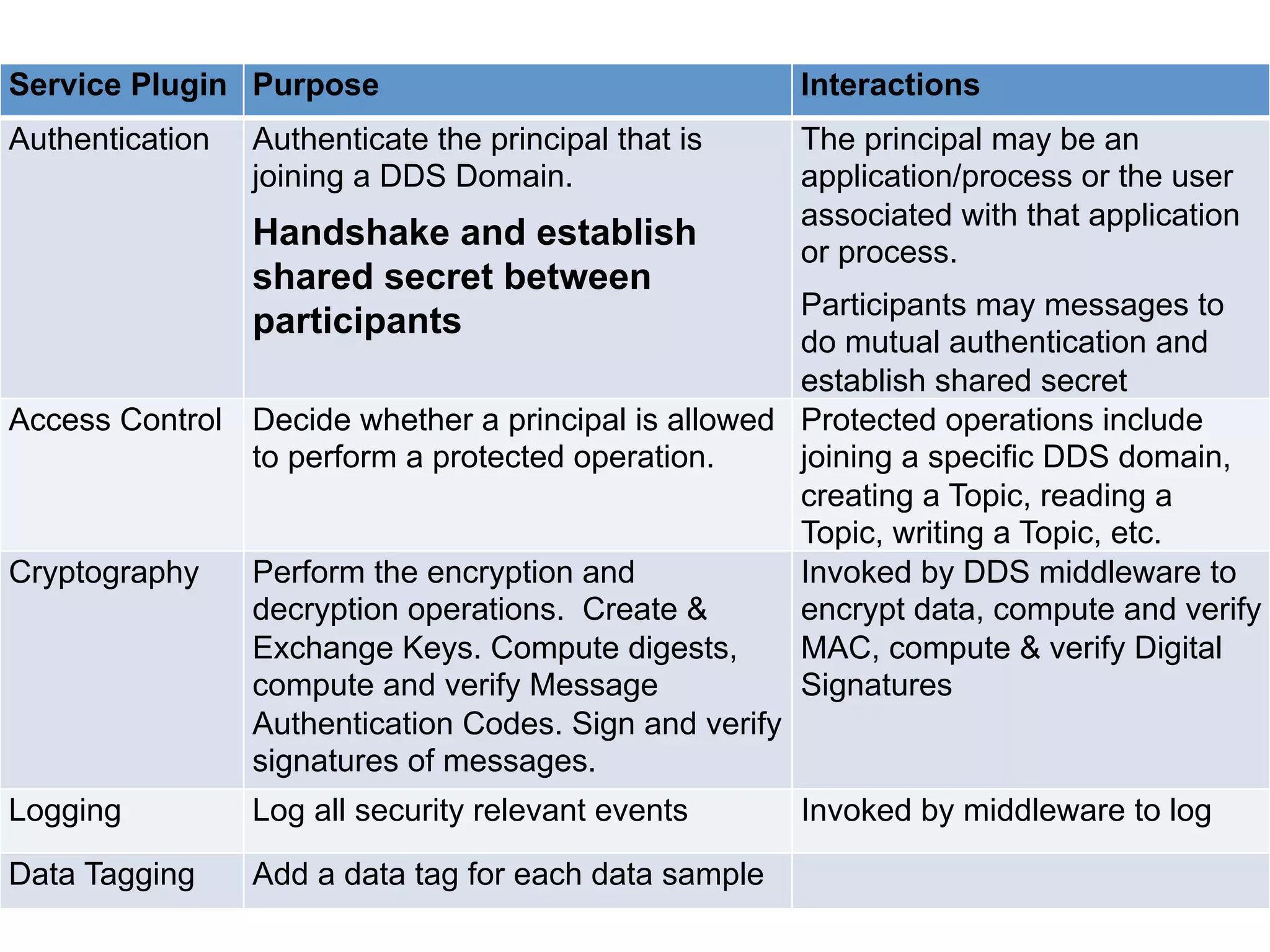
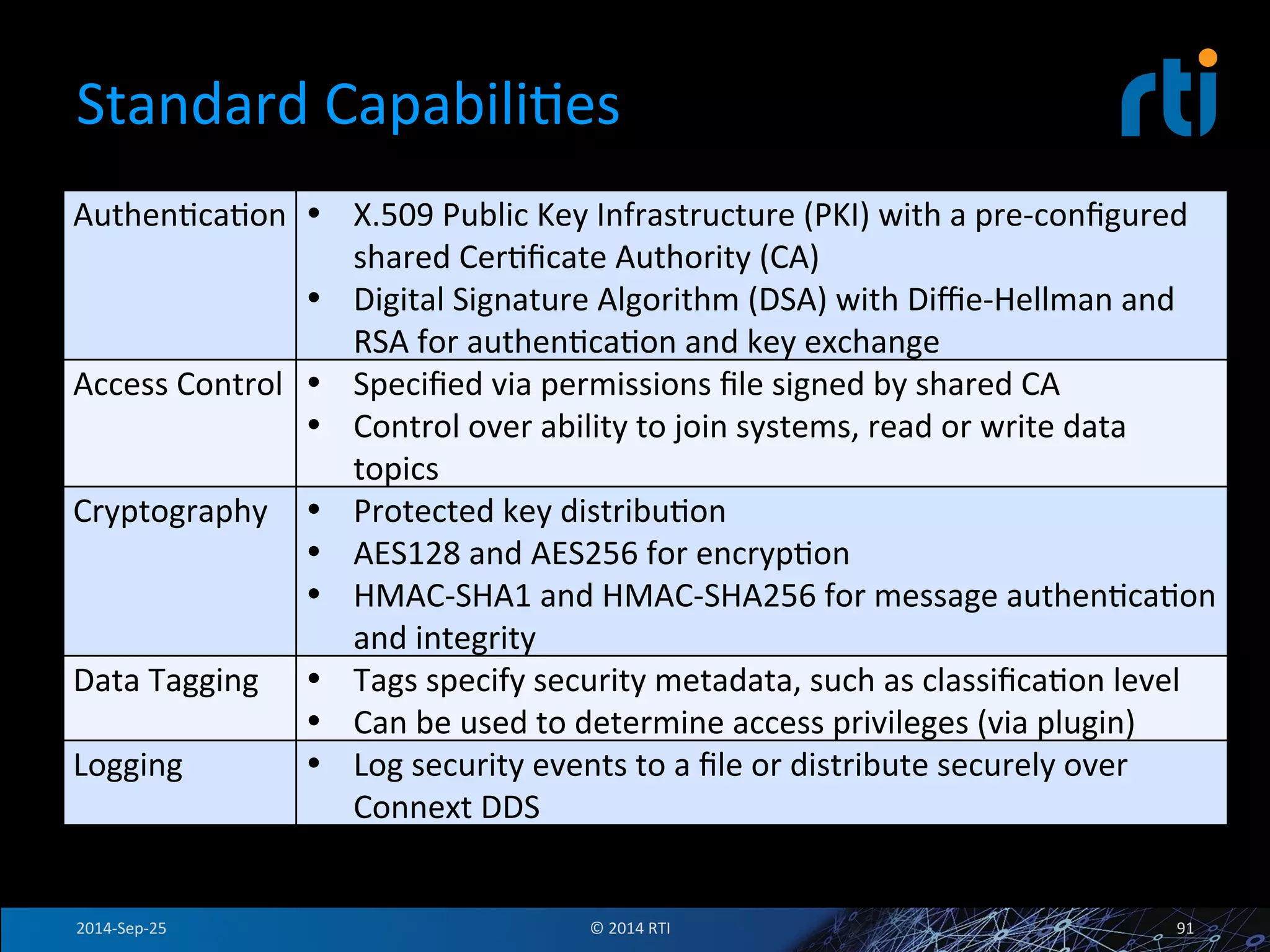
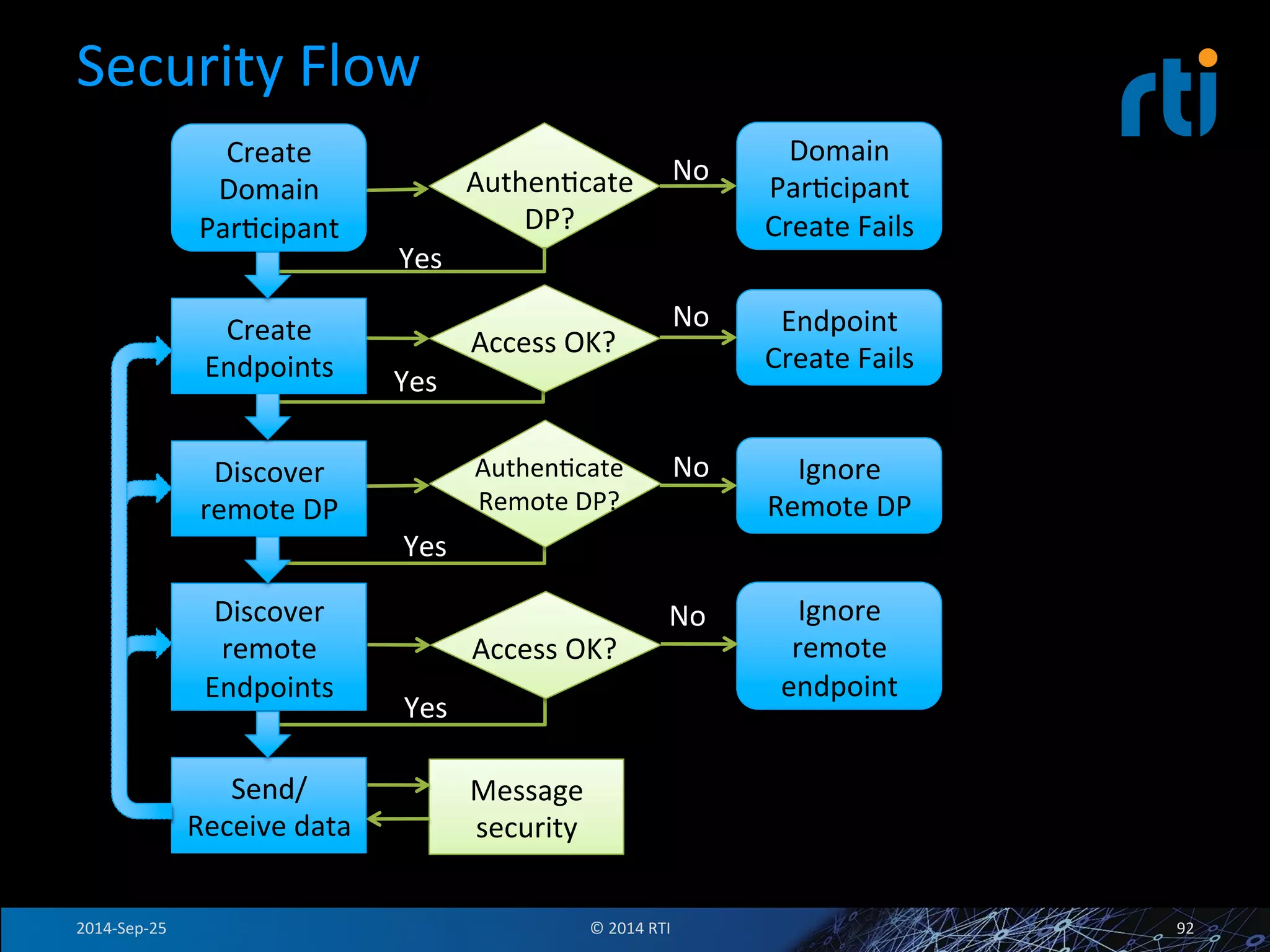
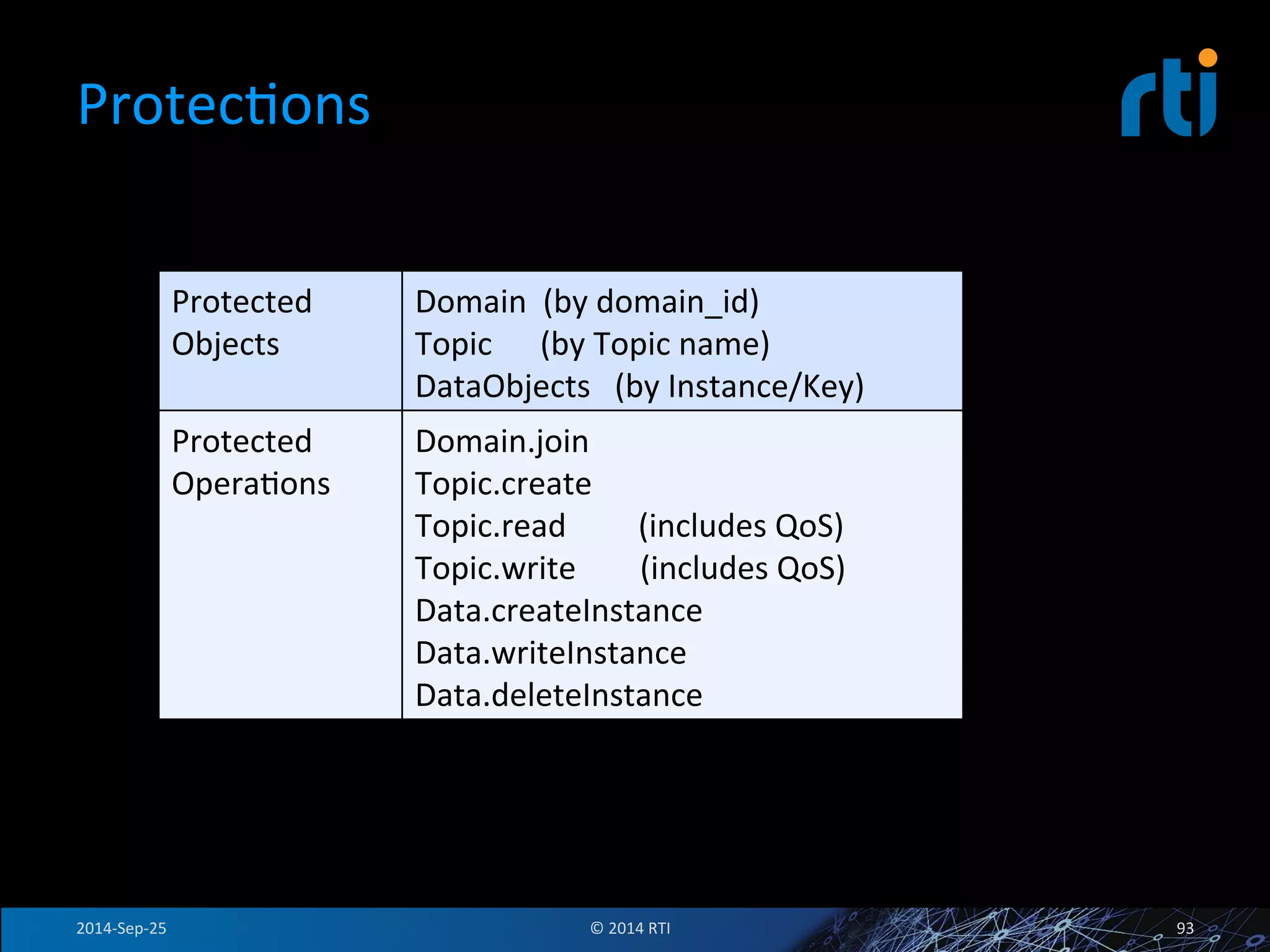
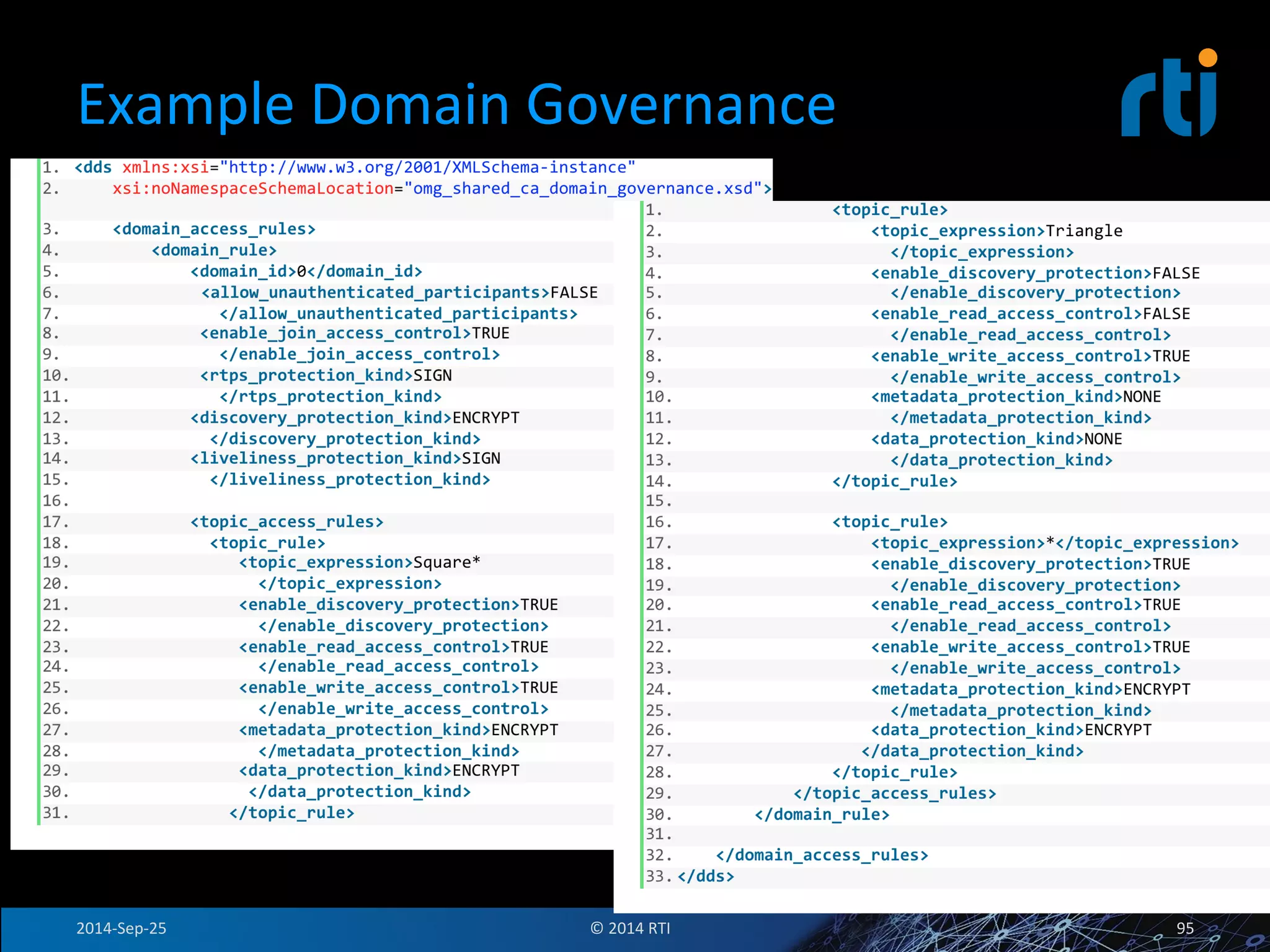
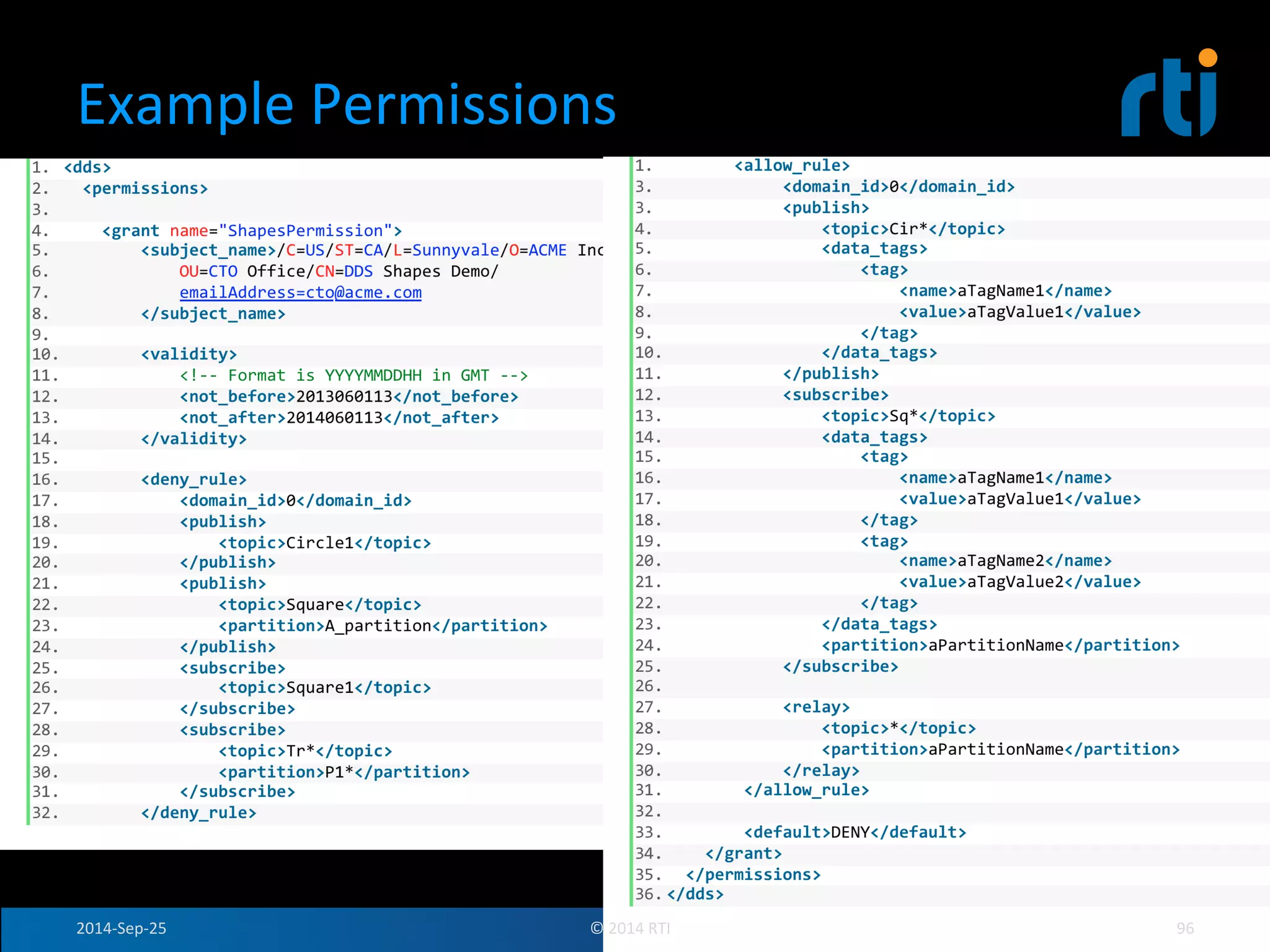
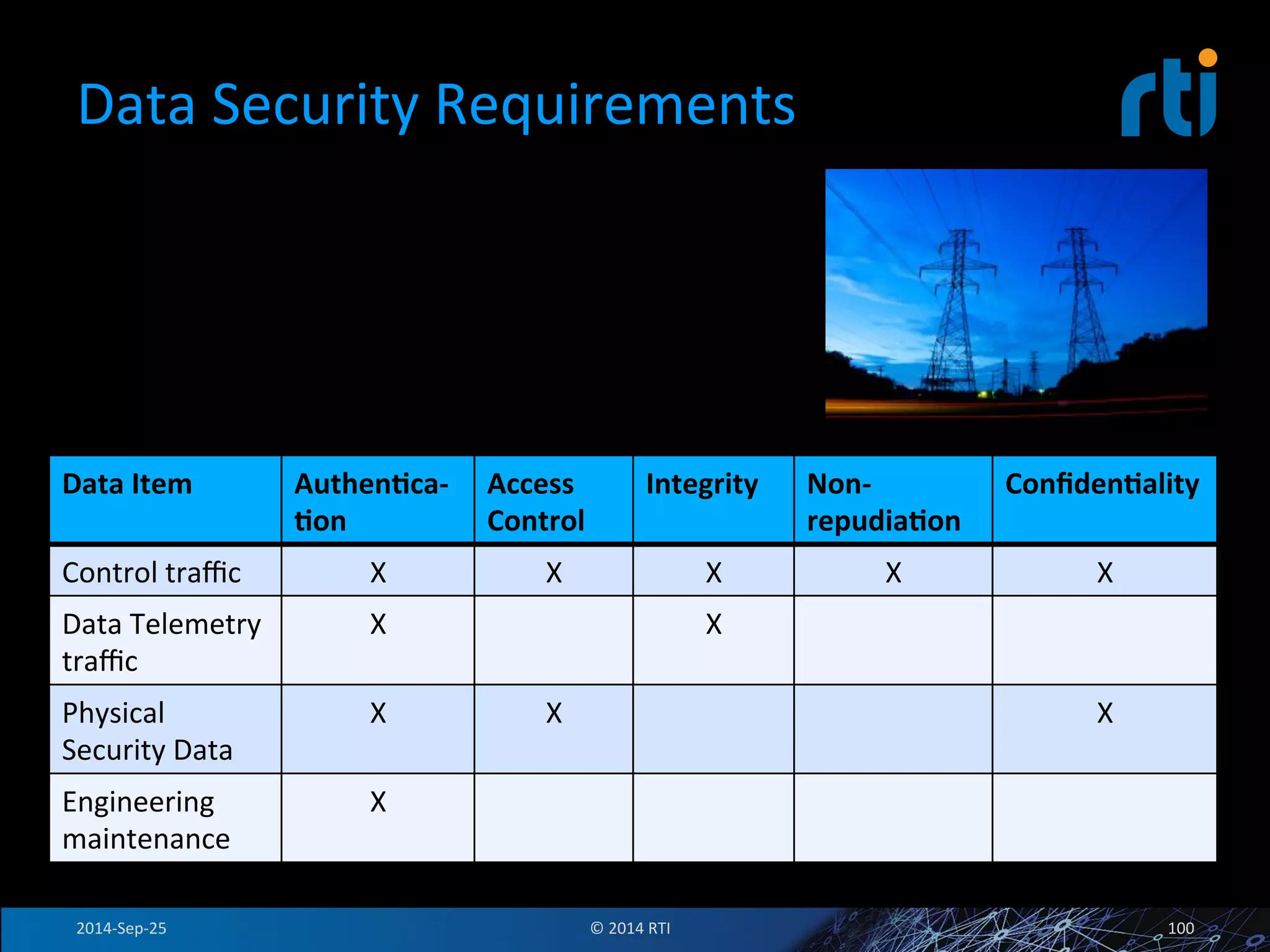
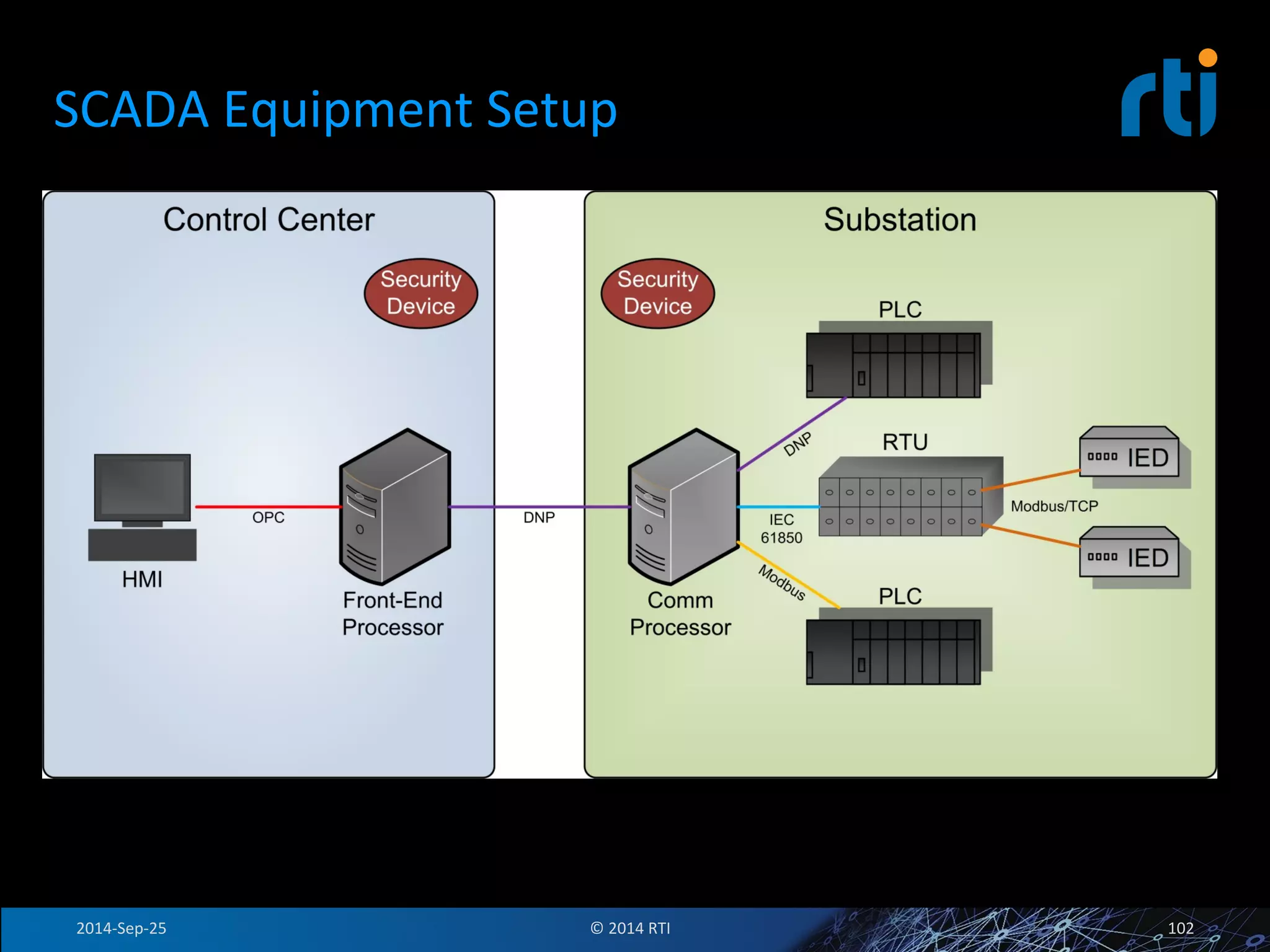
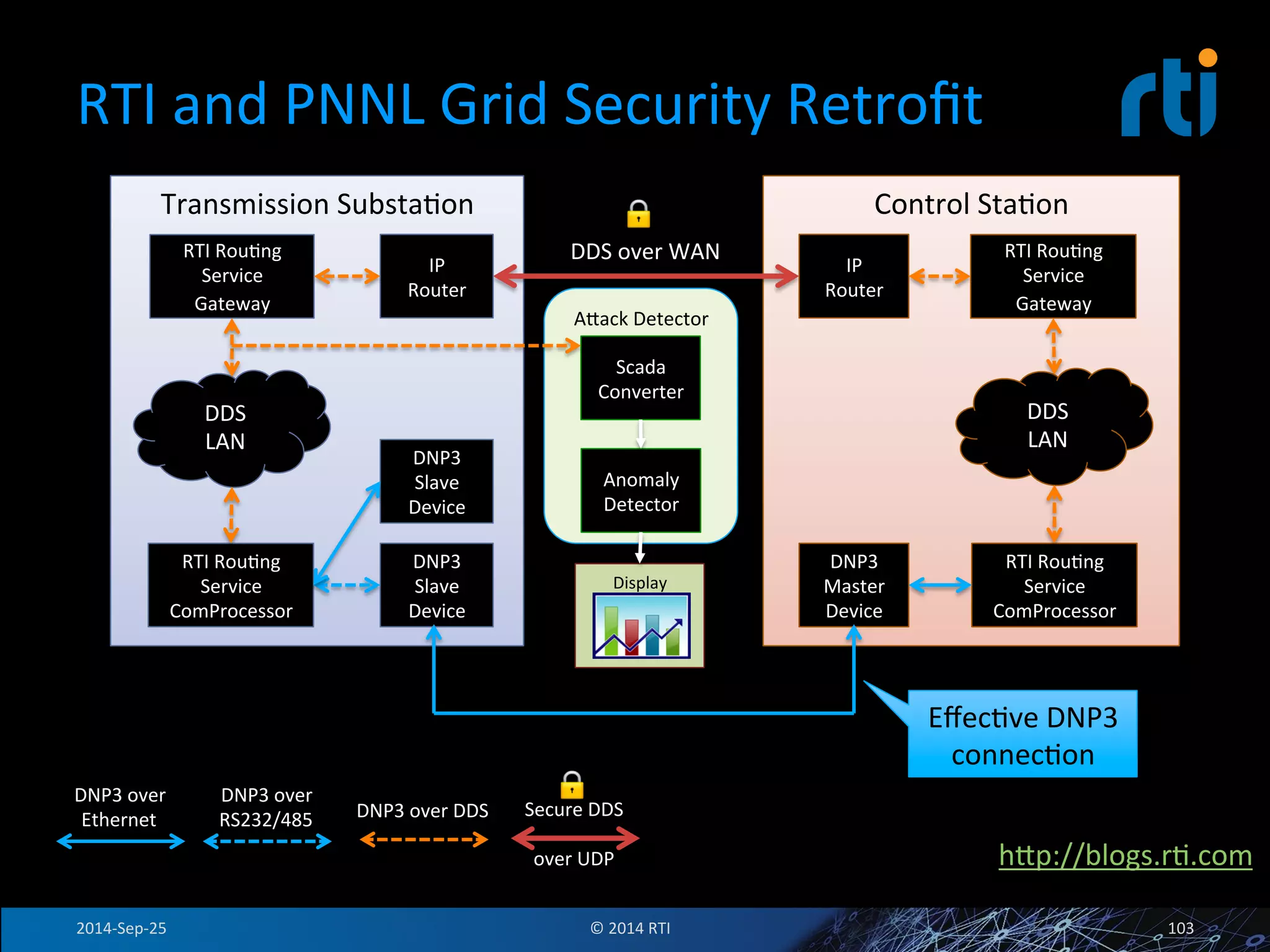
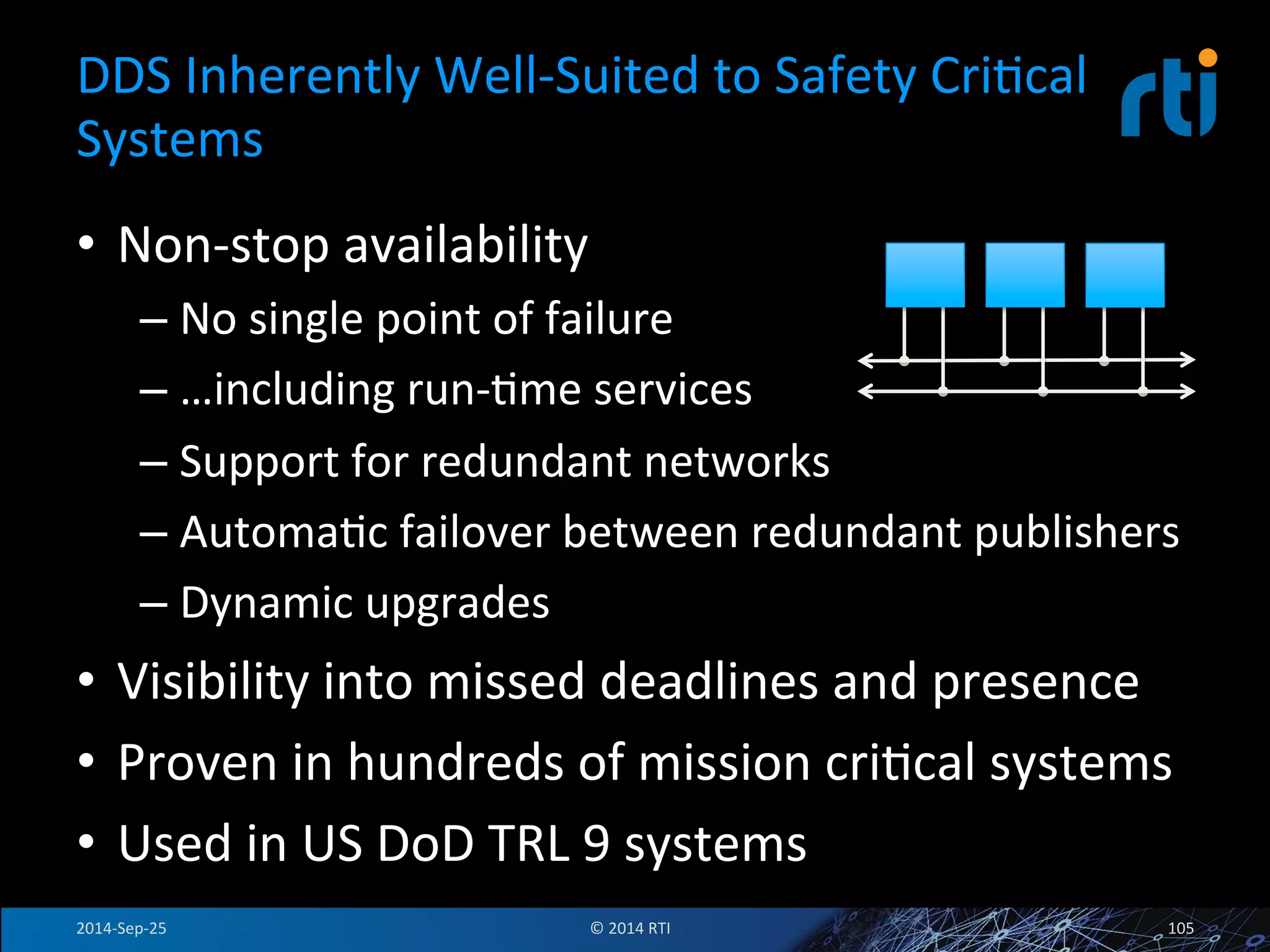
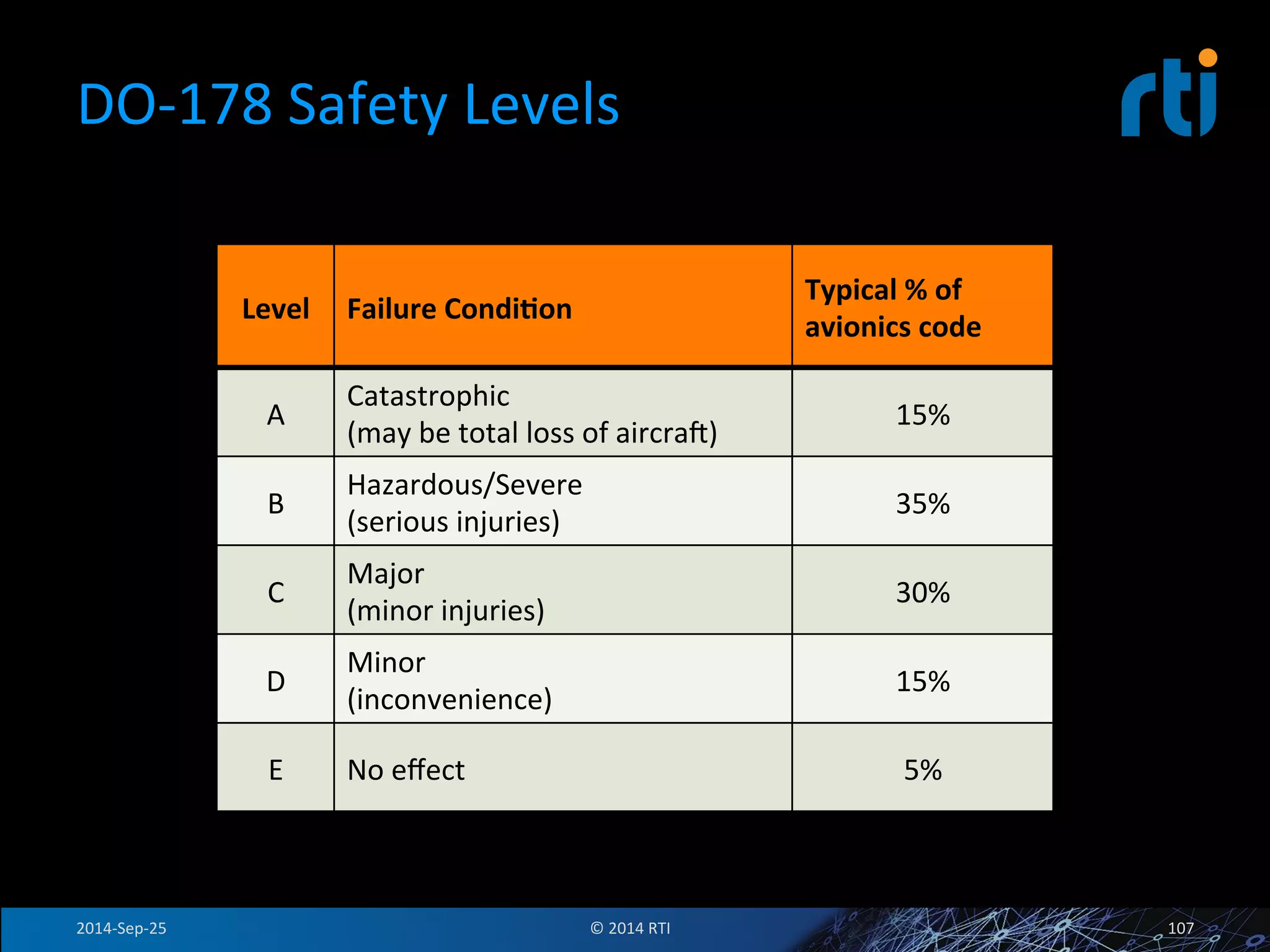
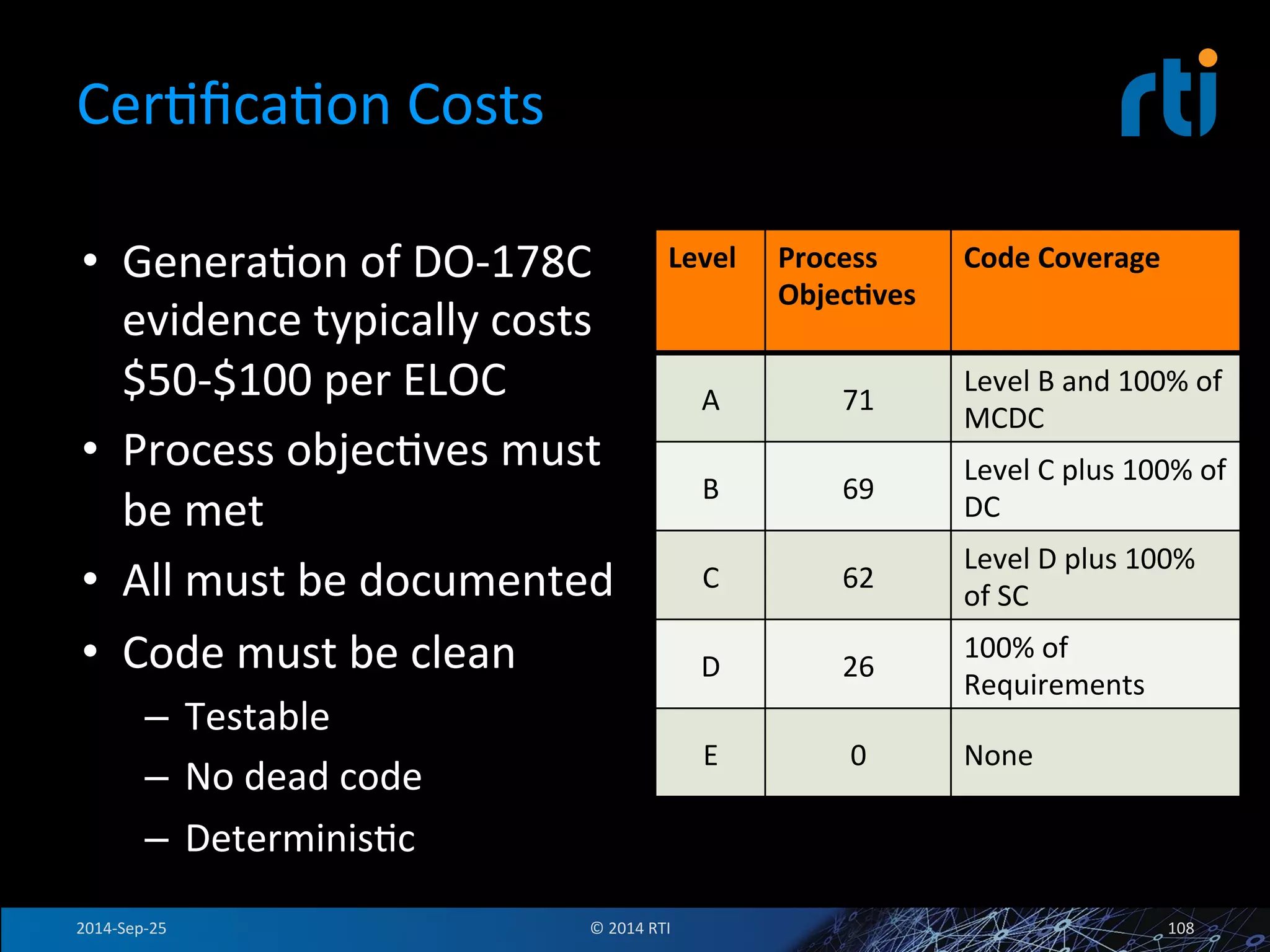
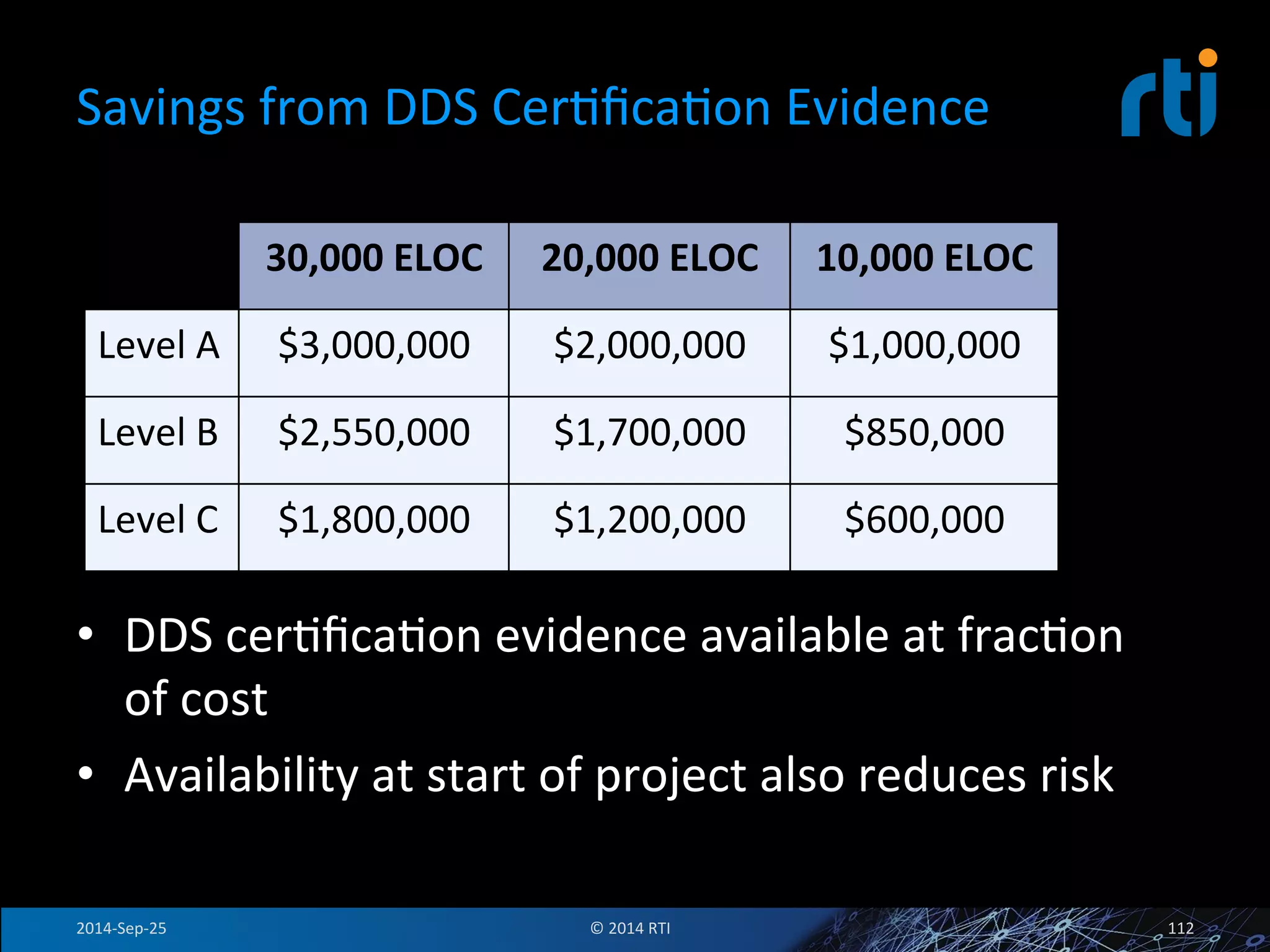
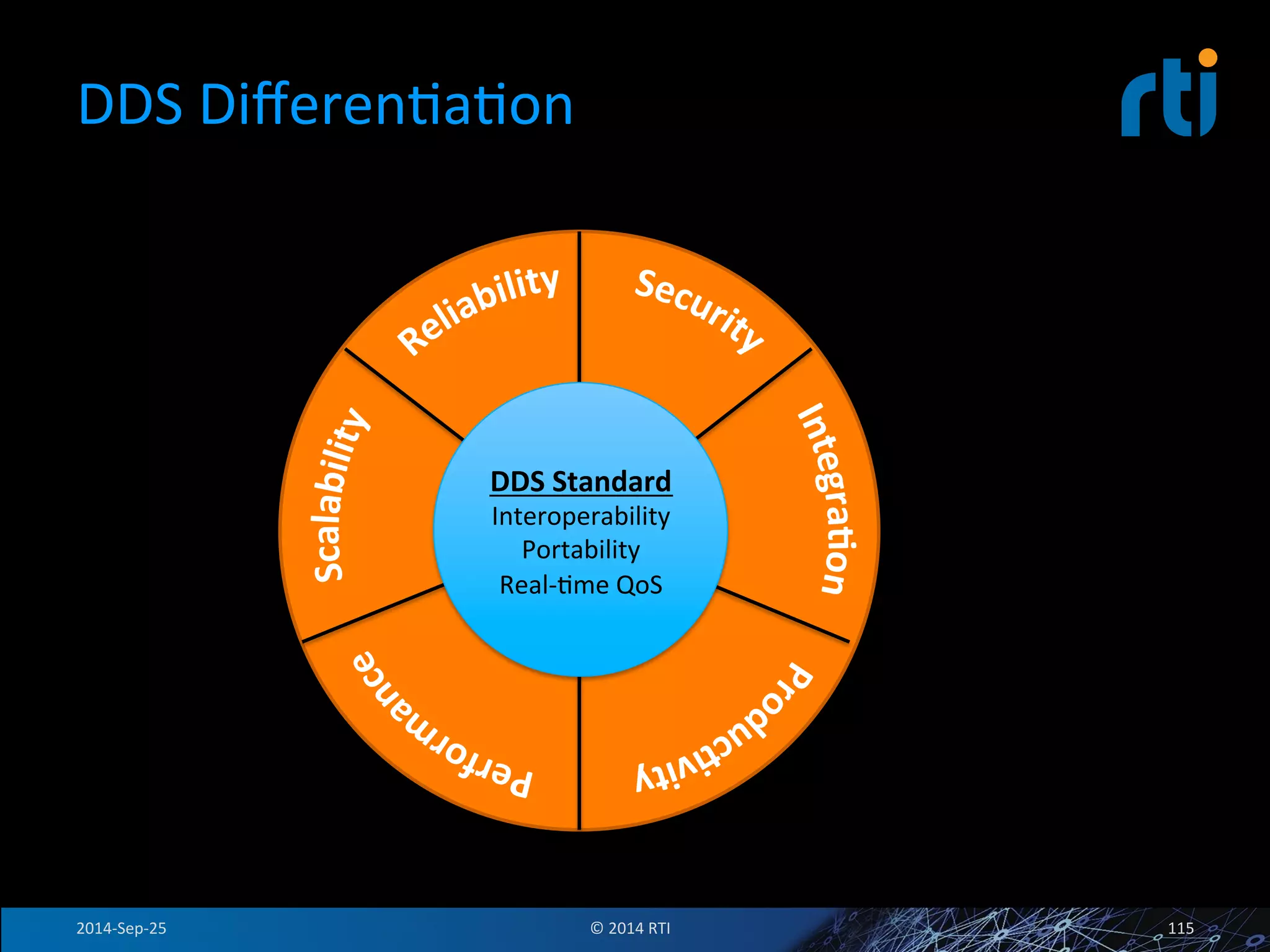
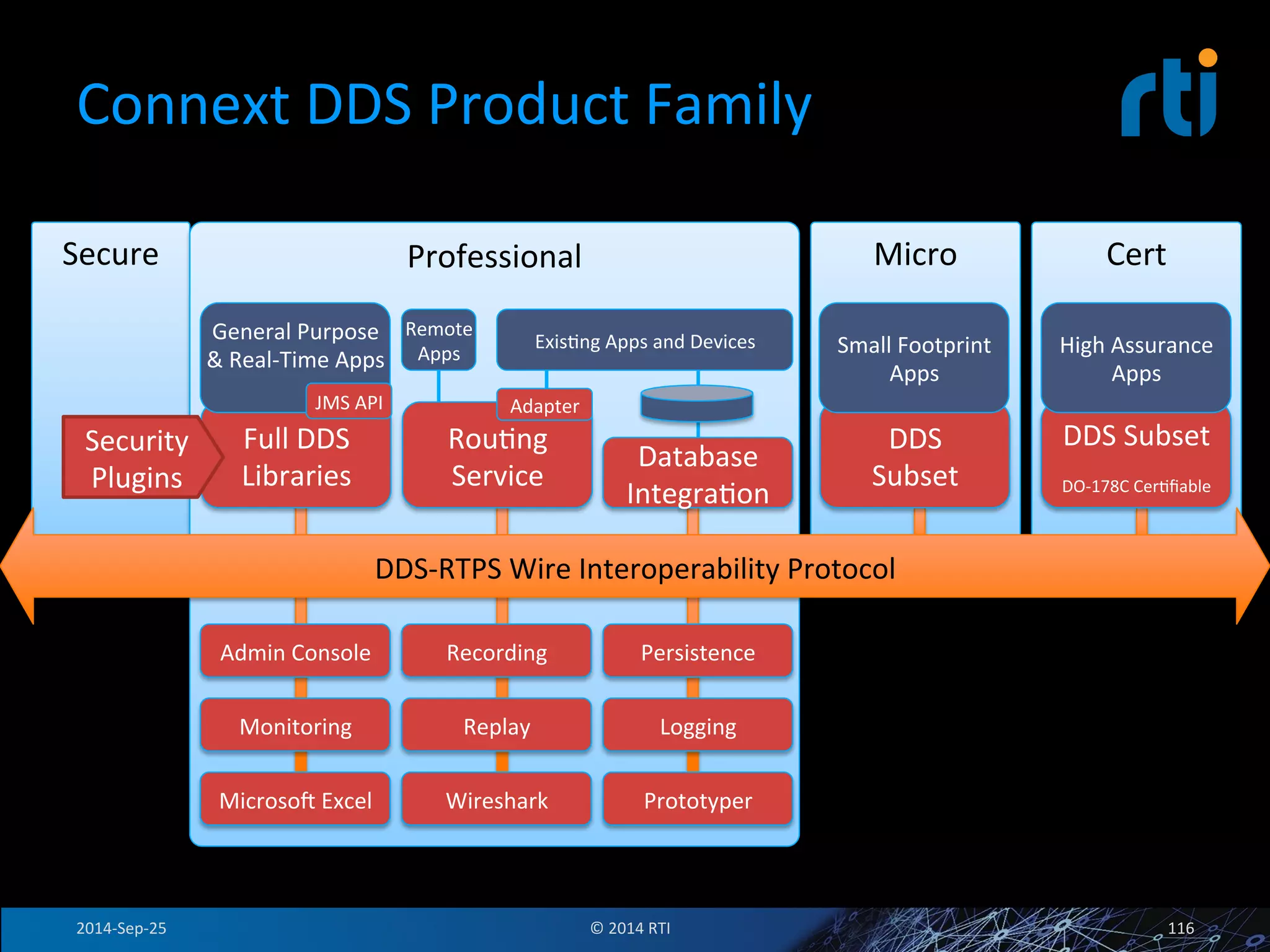
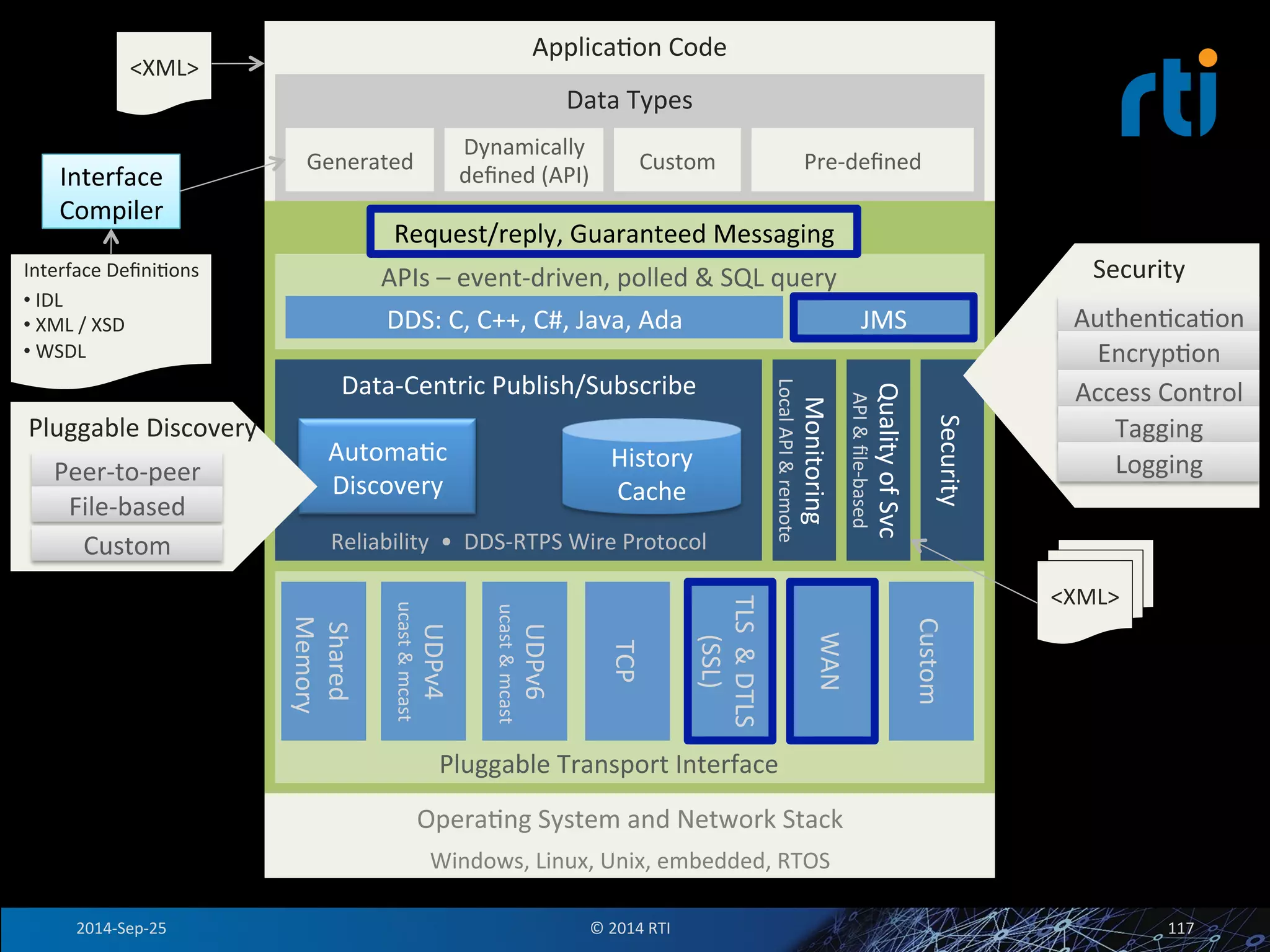
The document discusses the use of the Data Distribution Service (DDS) and DDS middleware to implement open architecture requirements for distributed systems. DDS provides a publish-subscribe communication model that loosely couples applications and supports interoperability, real-time performance, reliability, and flexibility to integrate new components. The presentation provides examples of how DDS has been used in defense and aerospace systems to meet open architecture mandates.