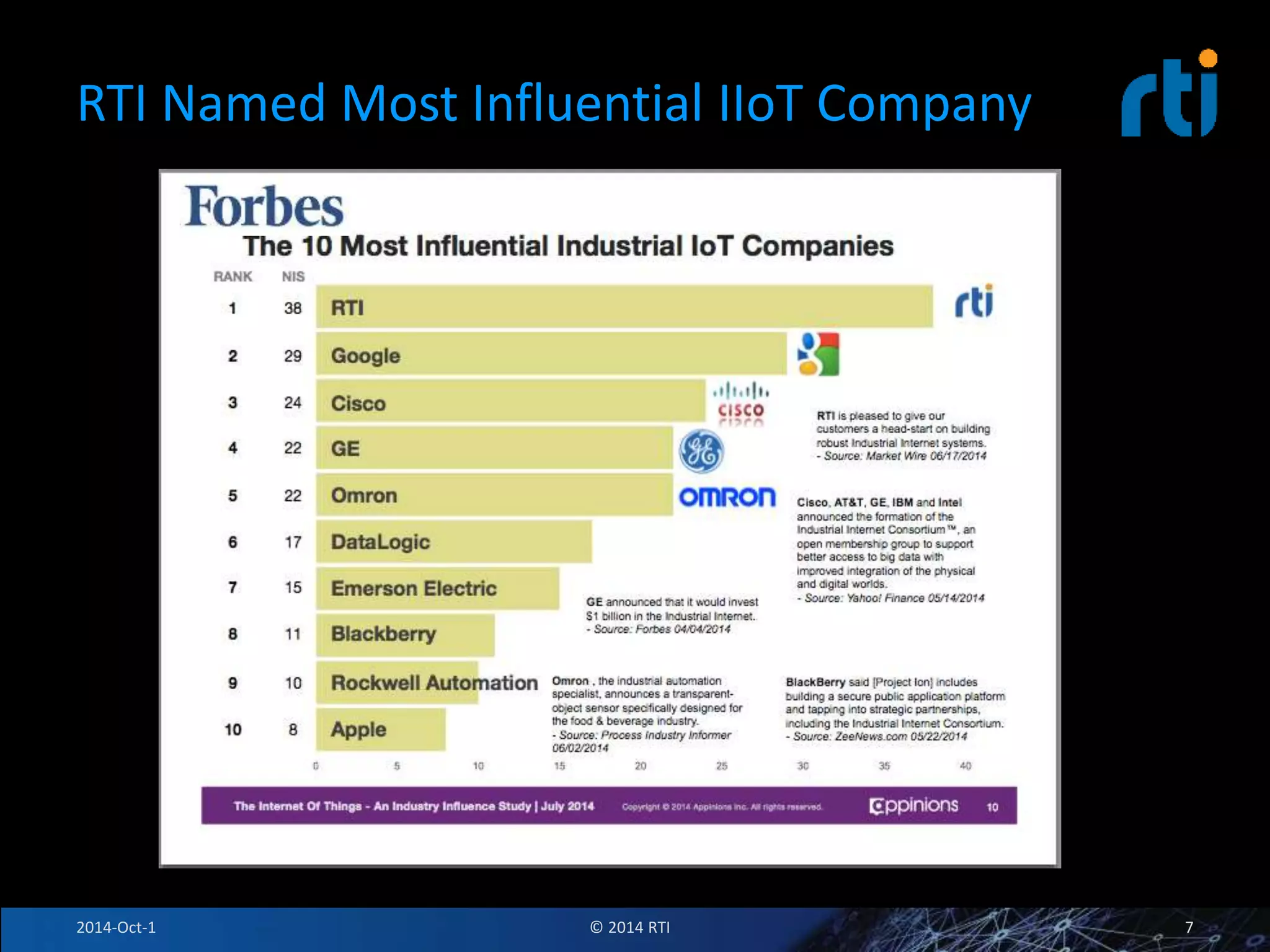
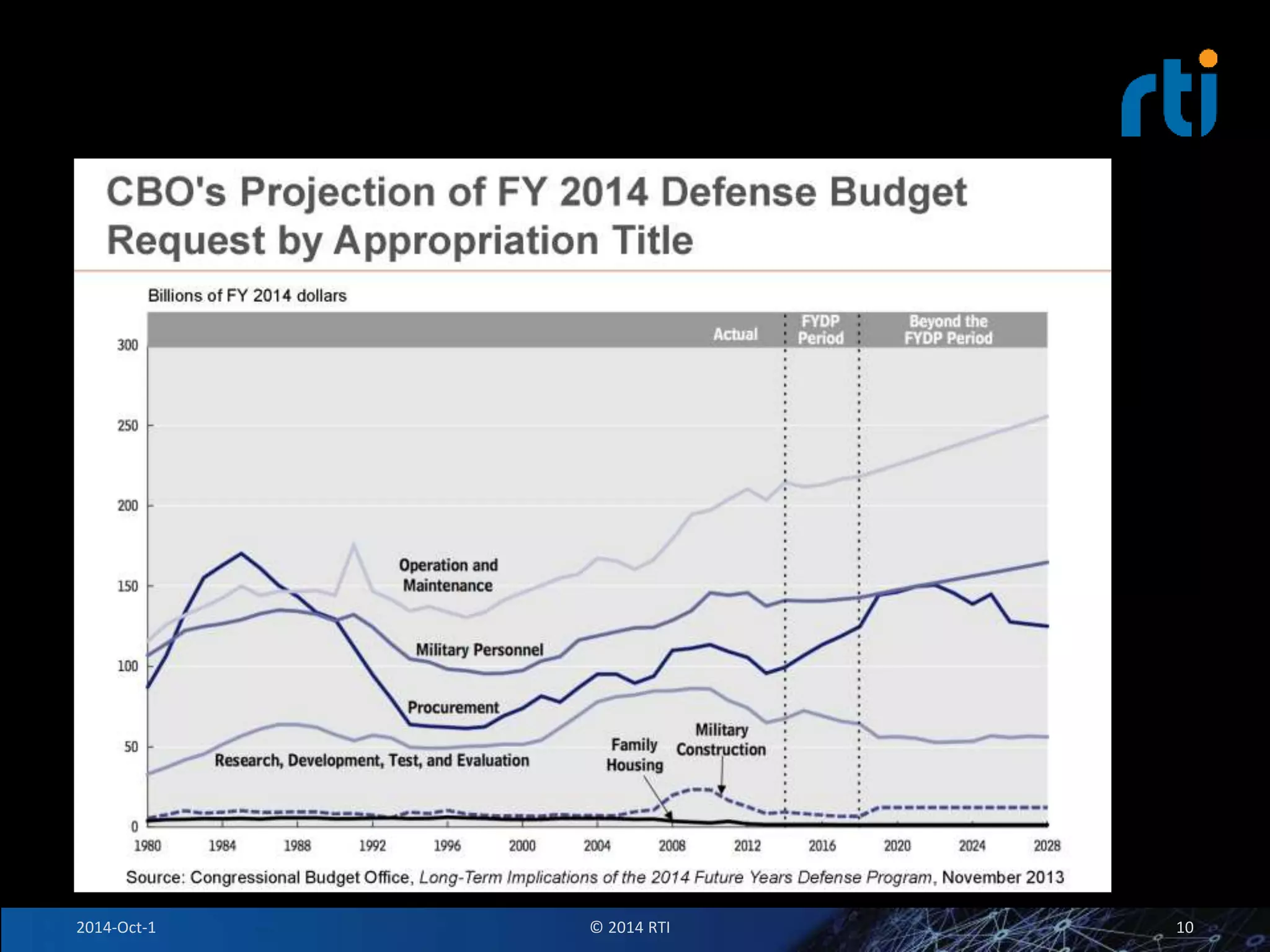
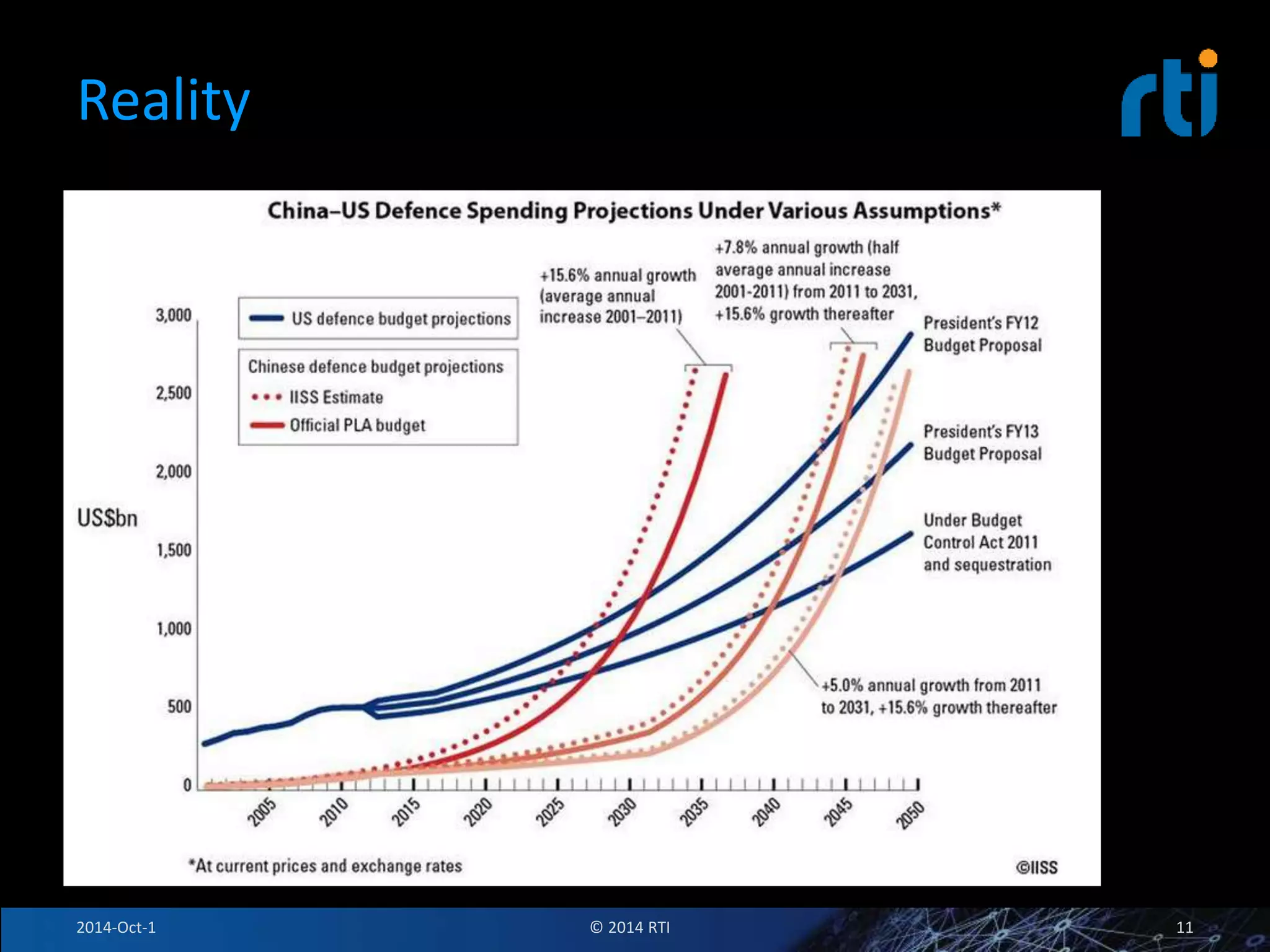
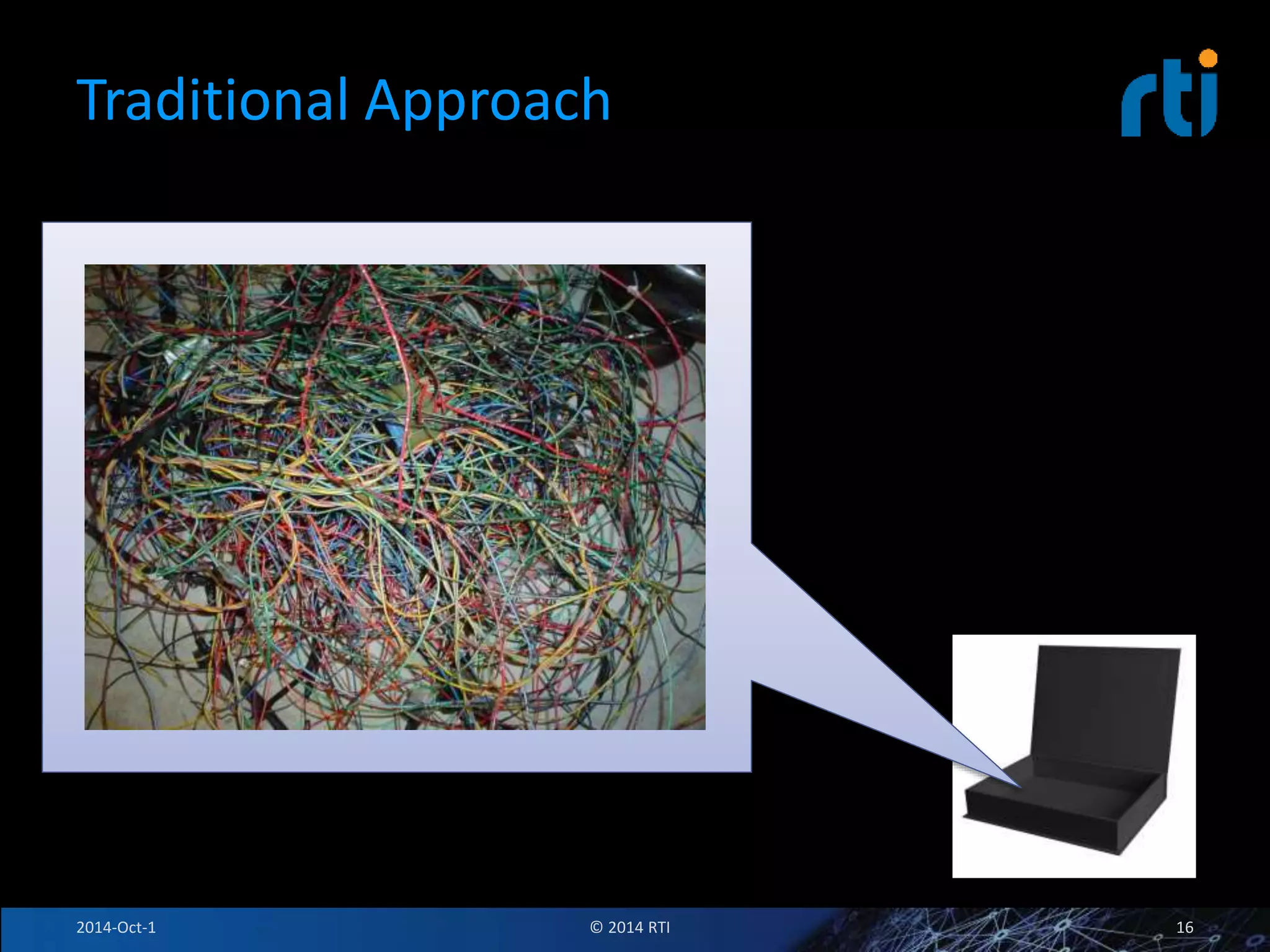
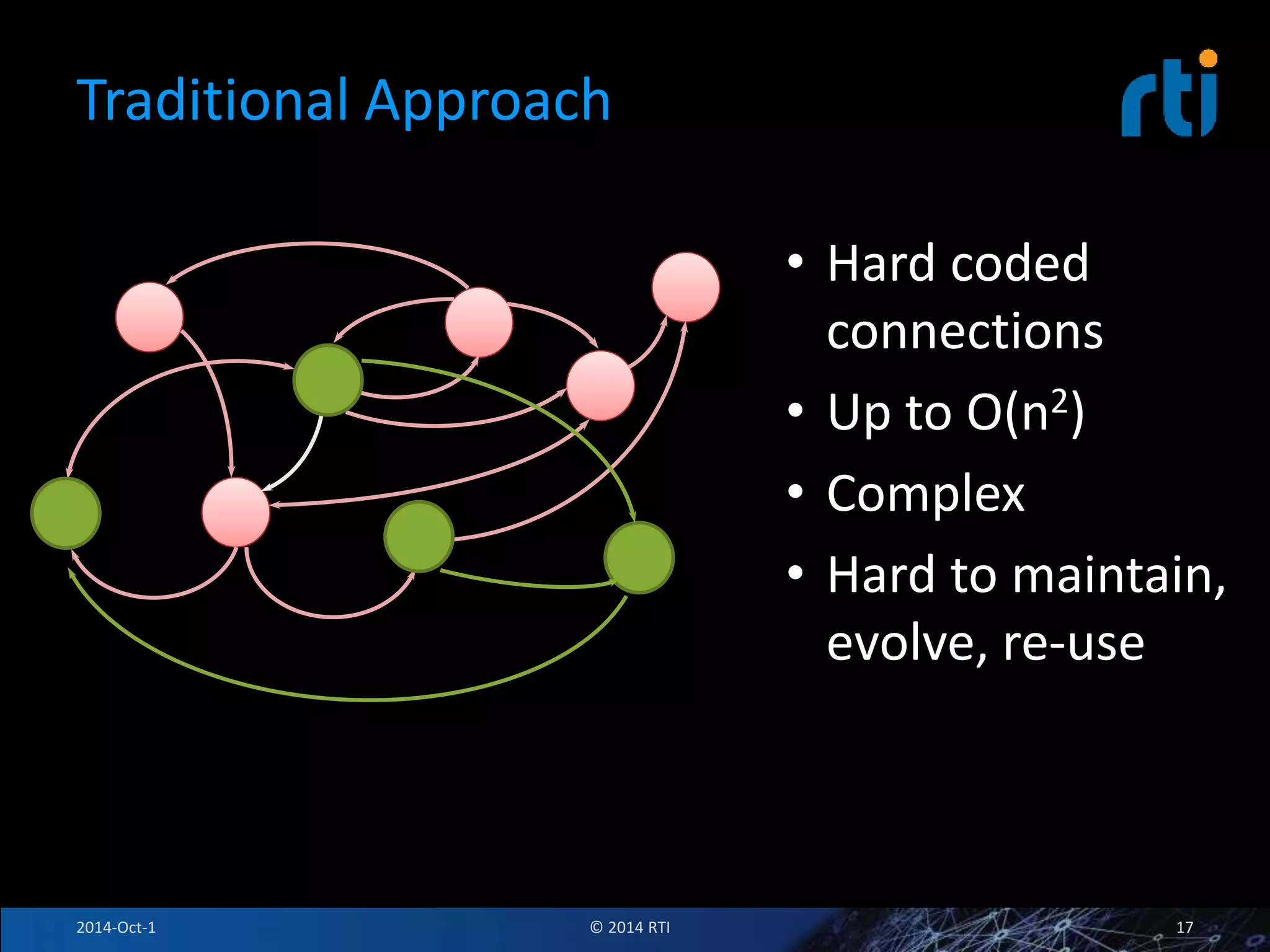
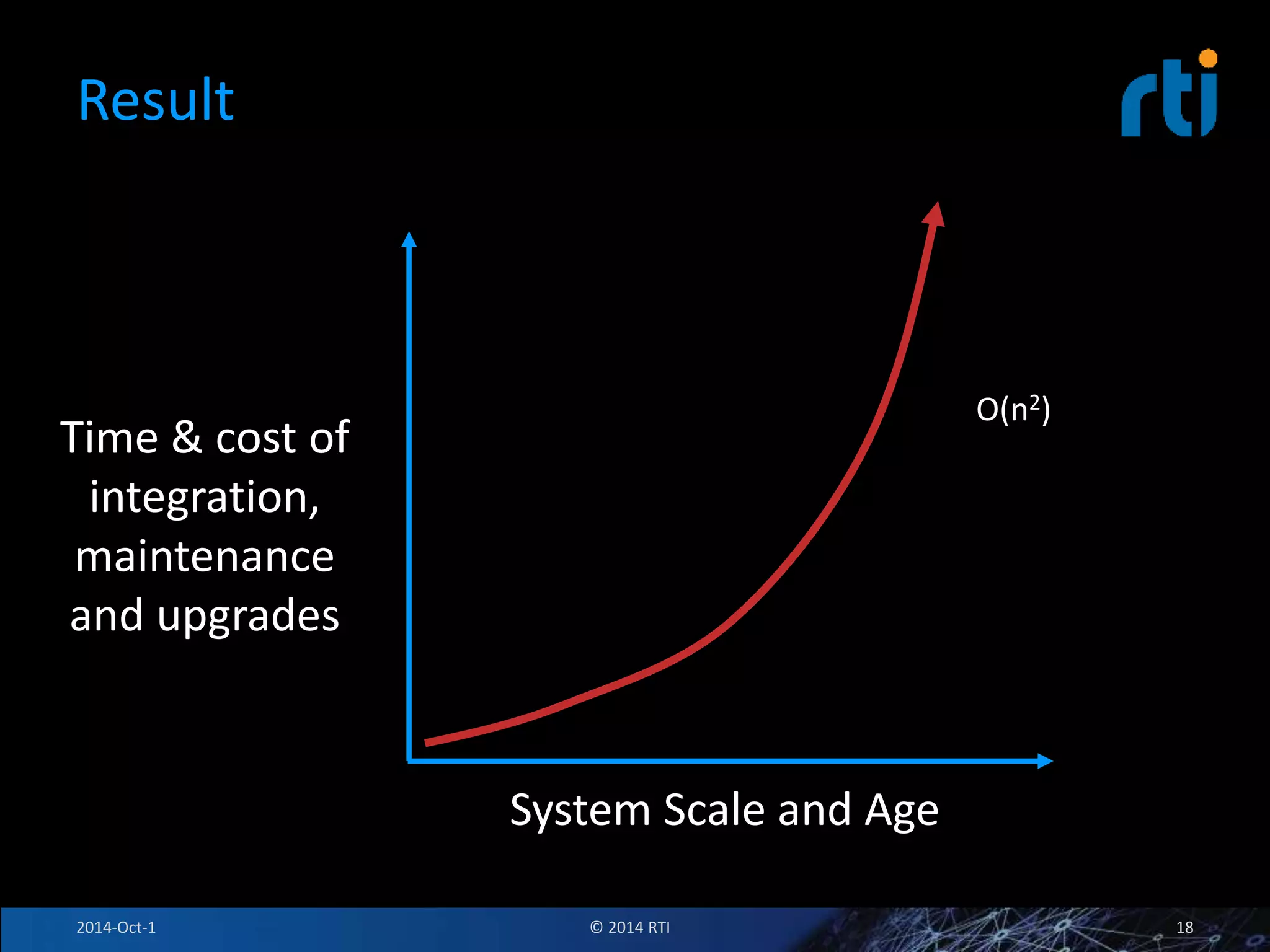
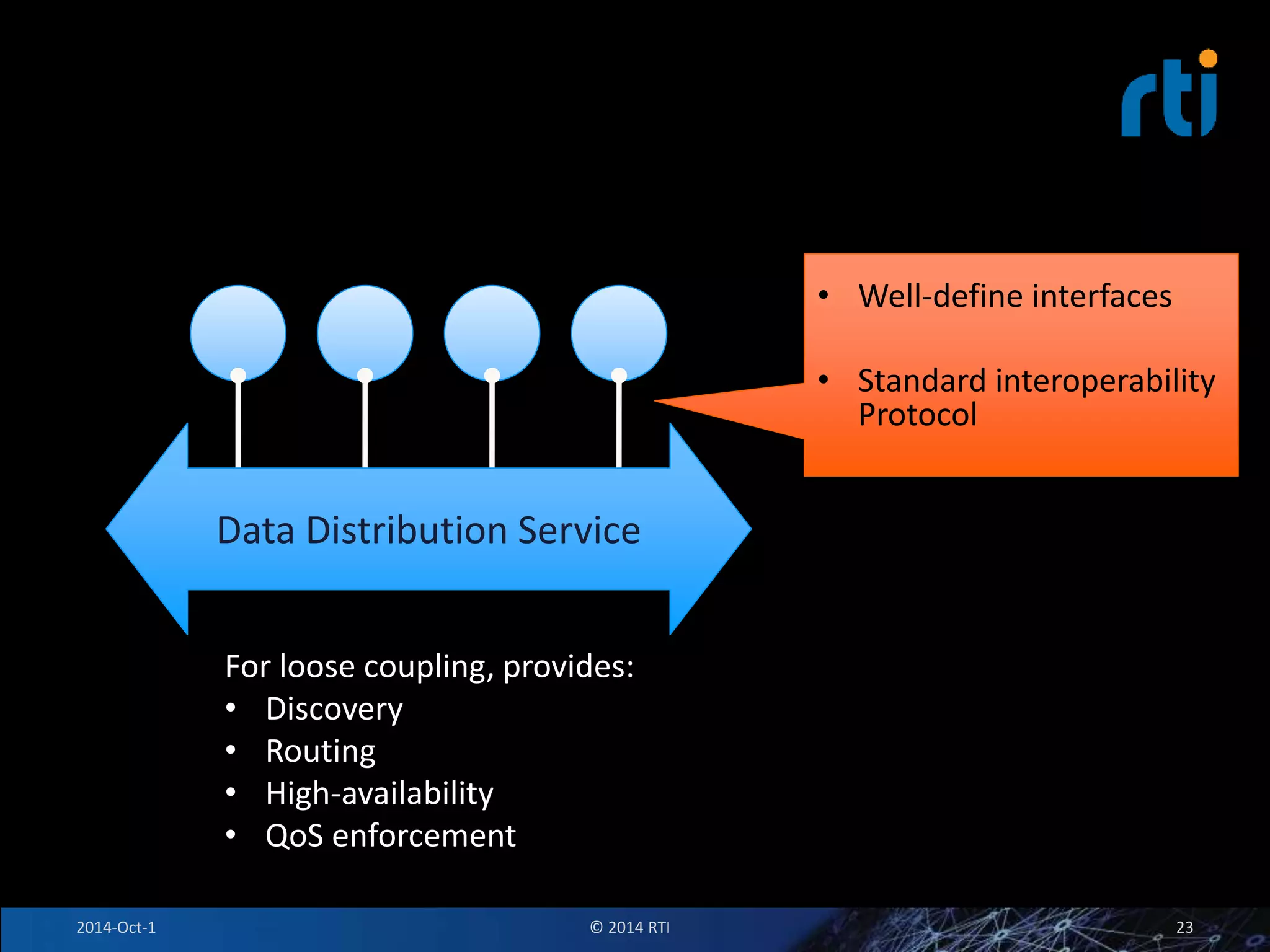
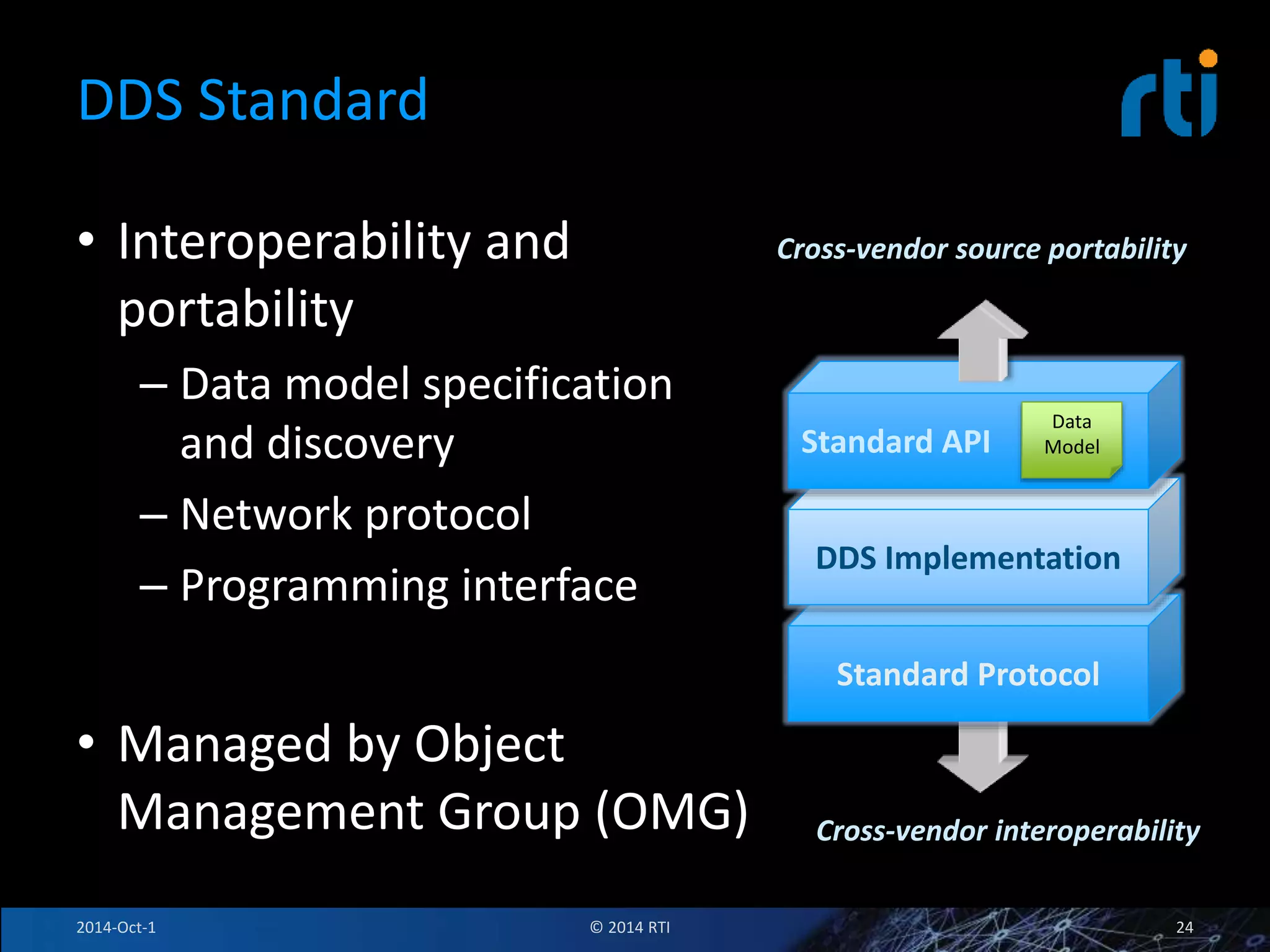
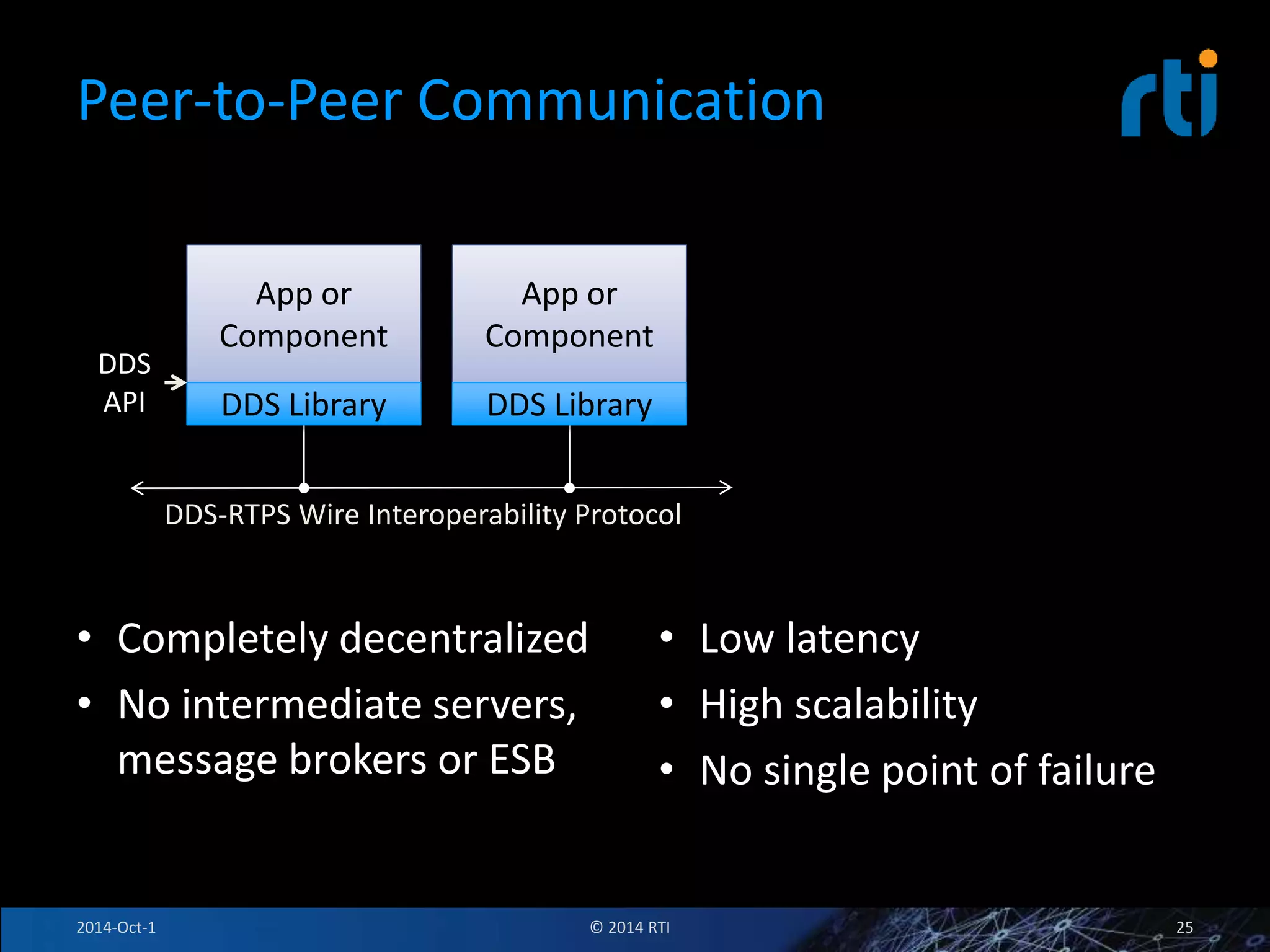
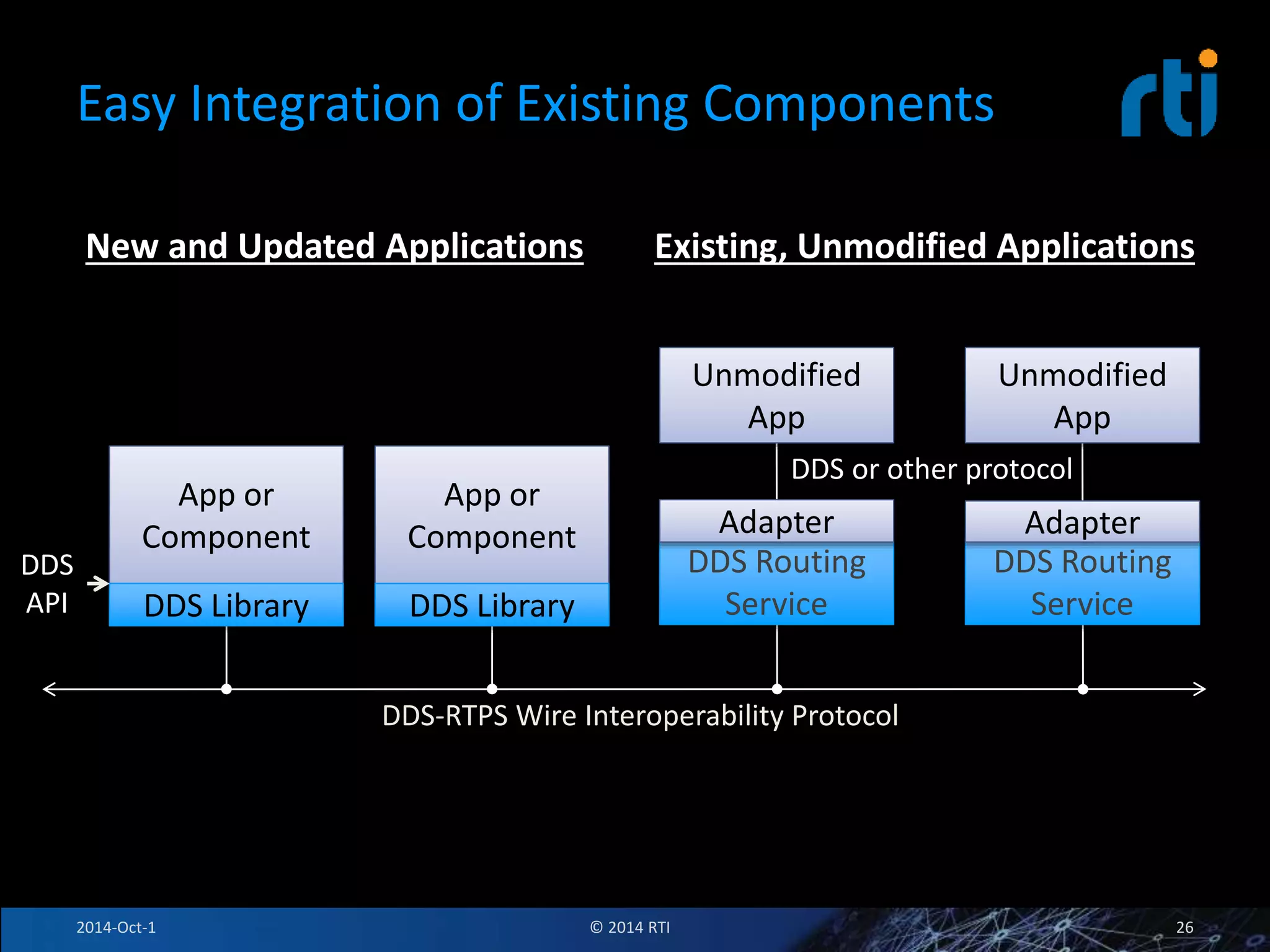
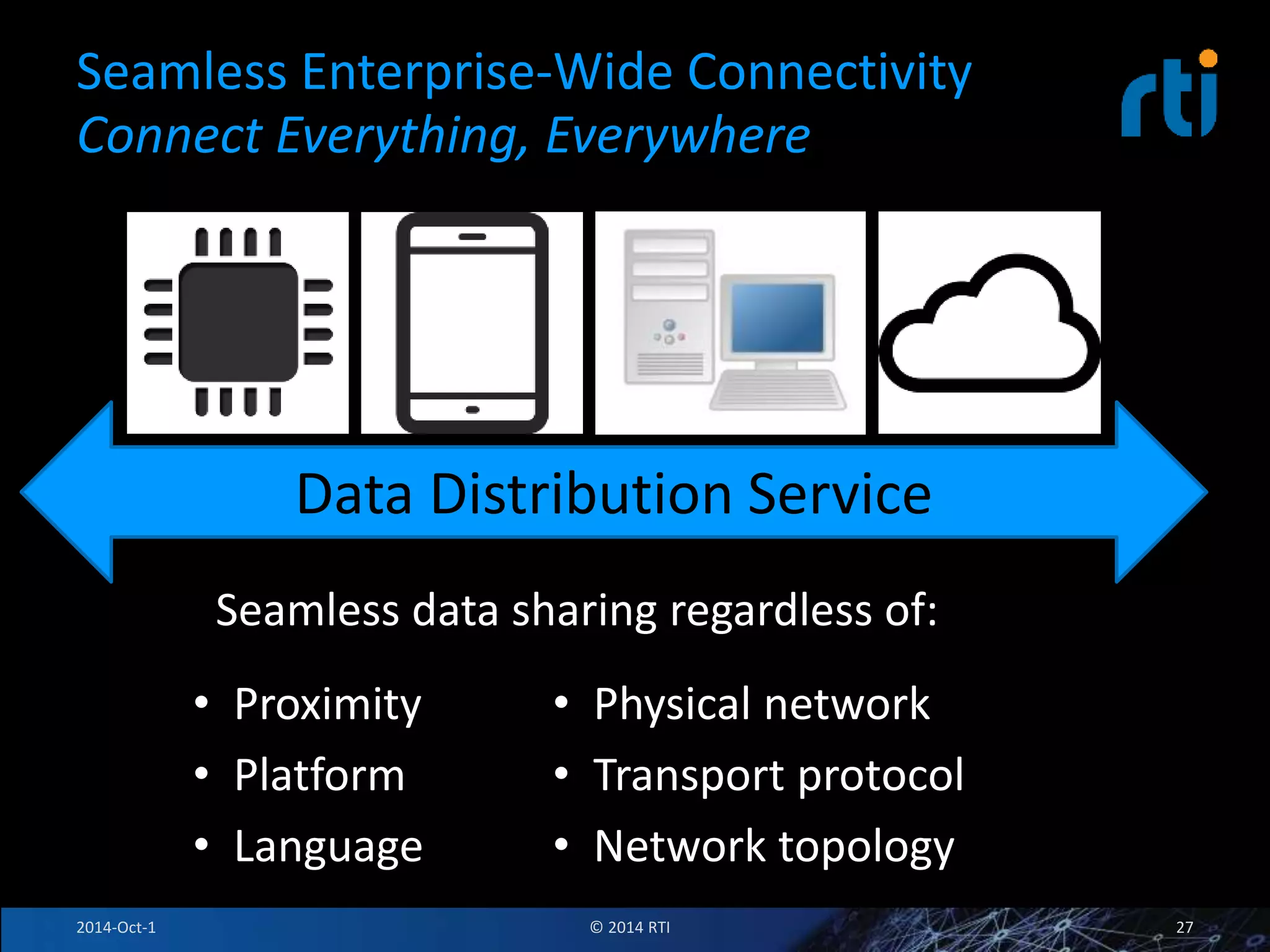
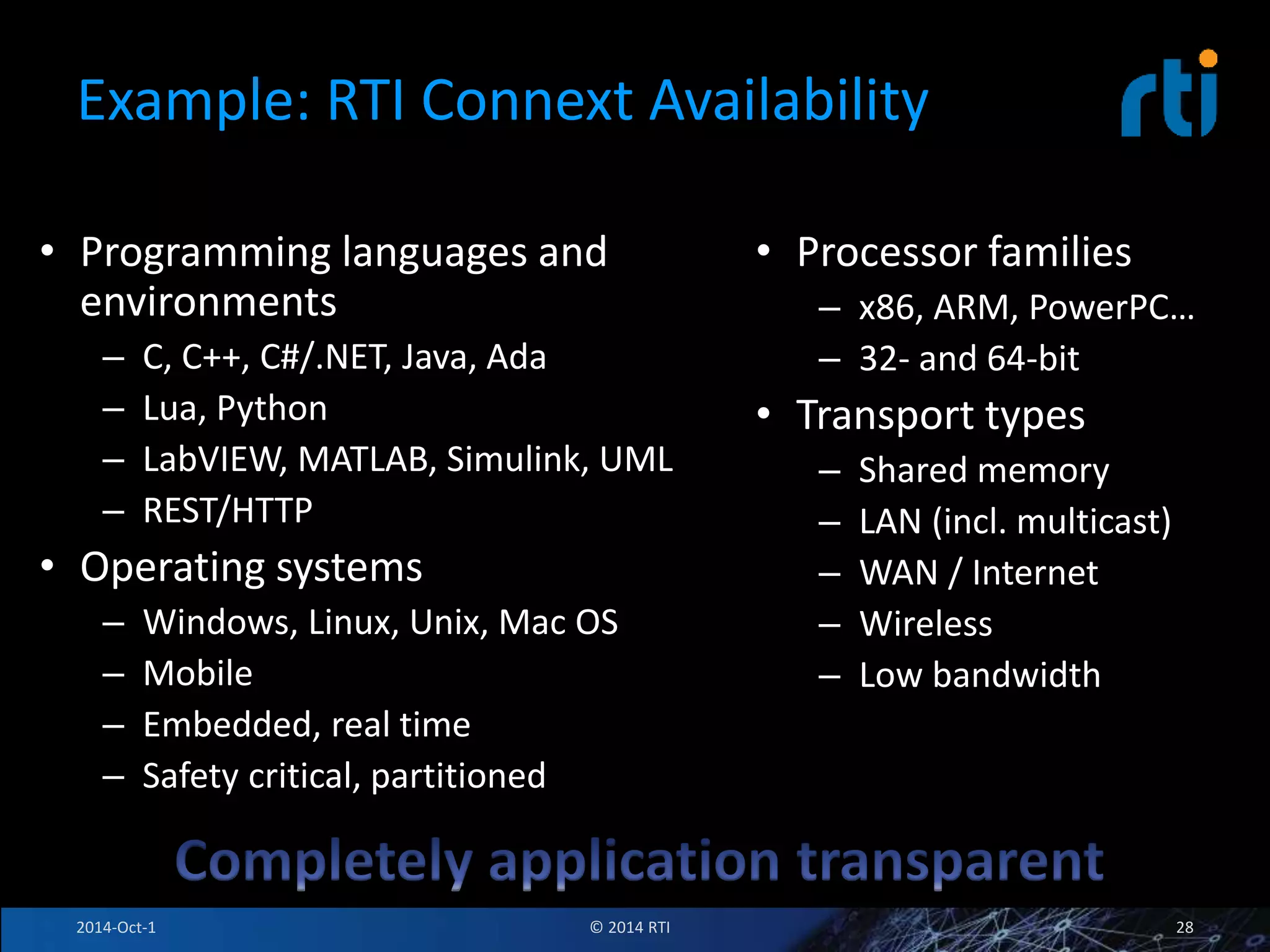
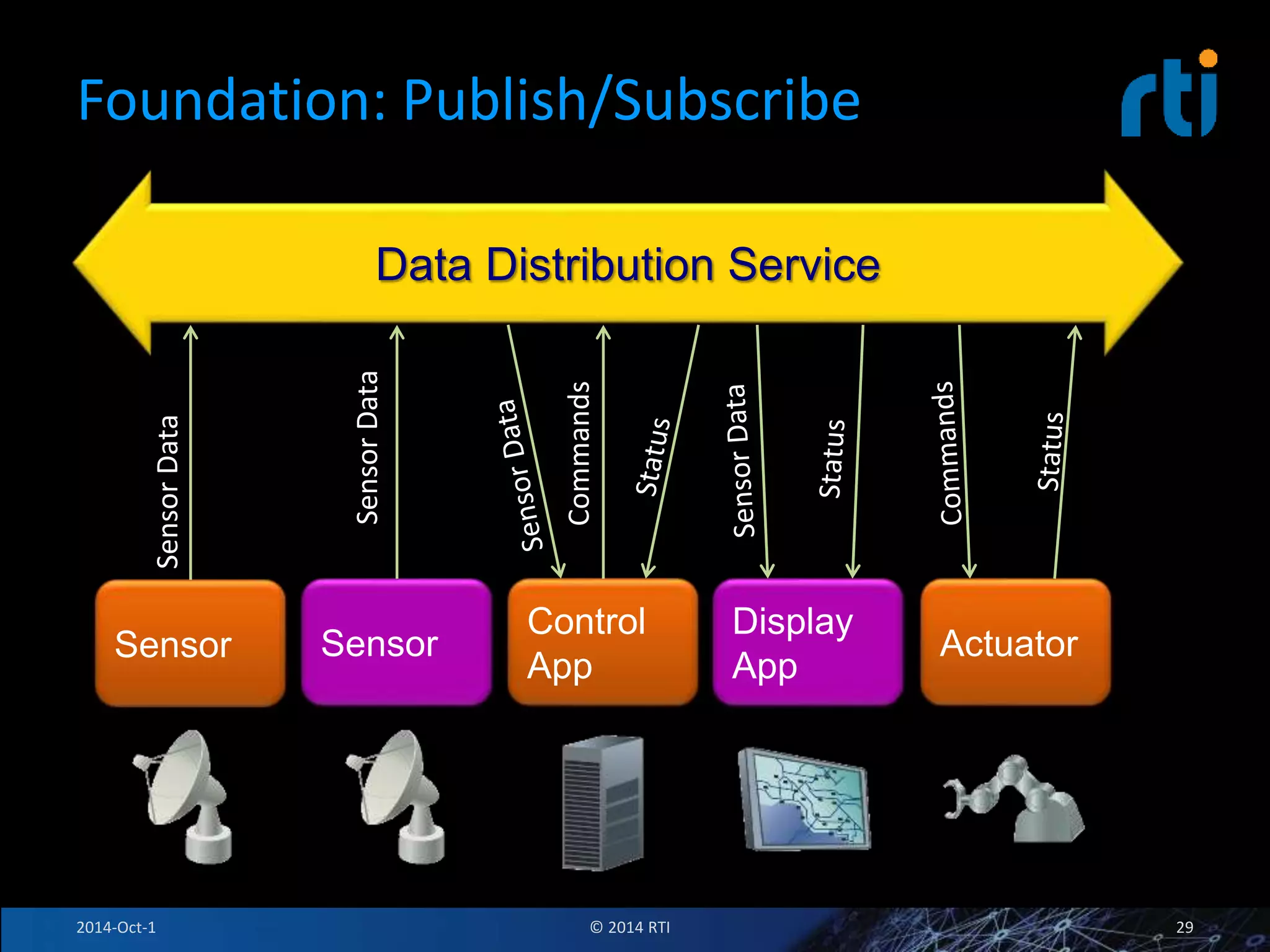
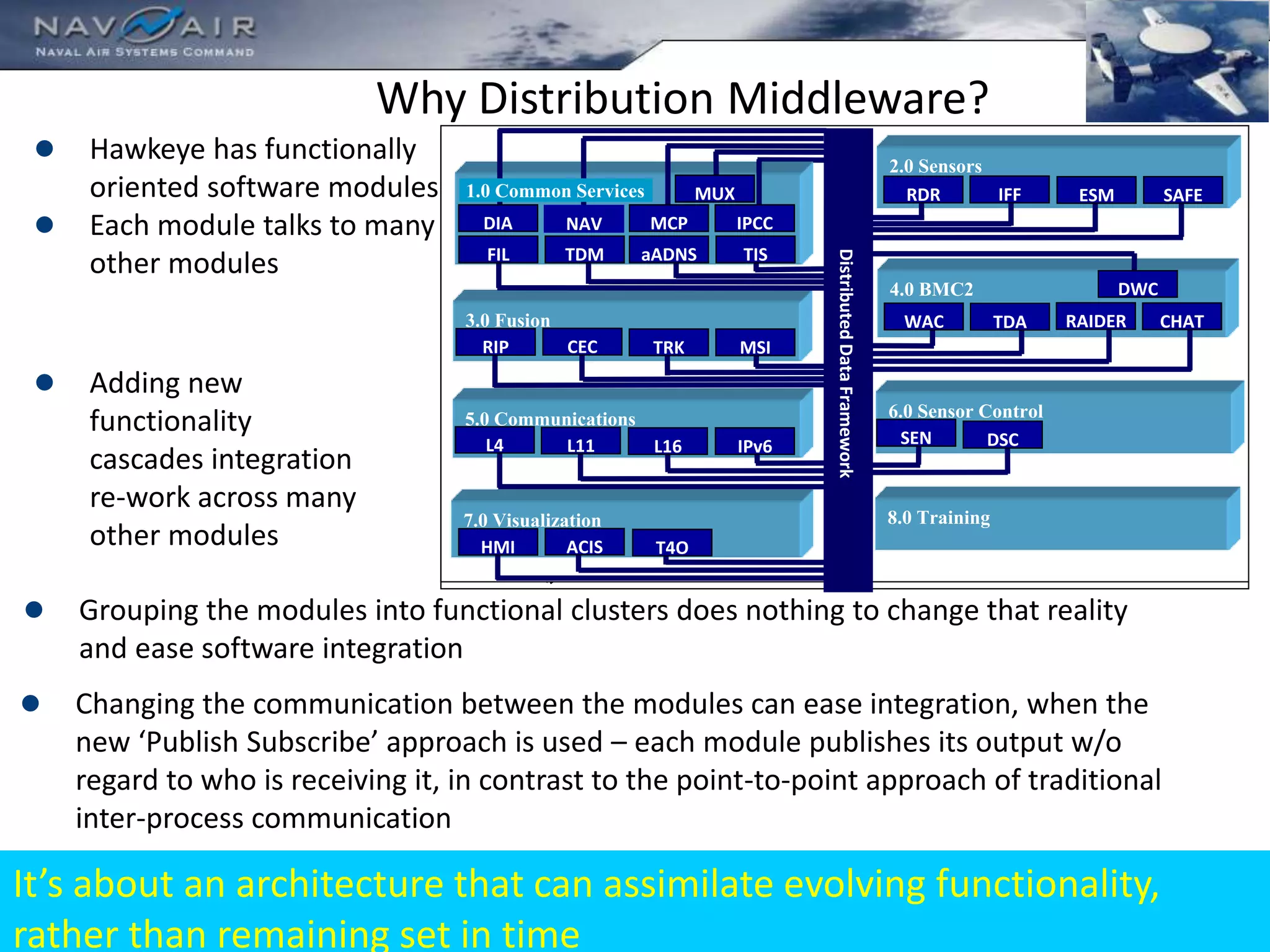
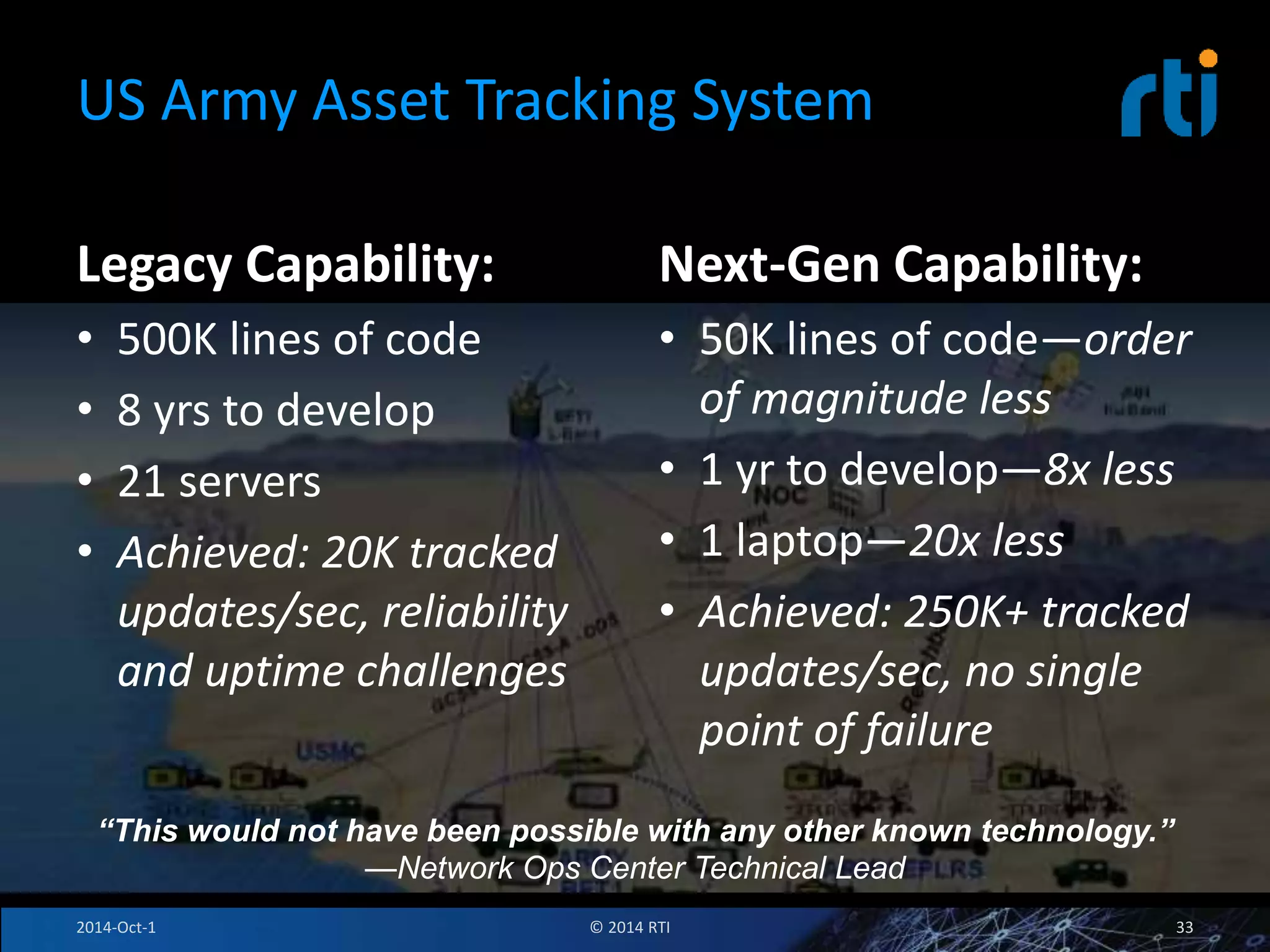
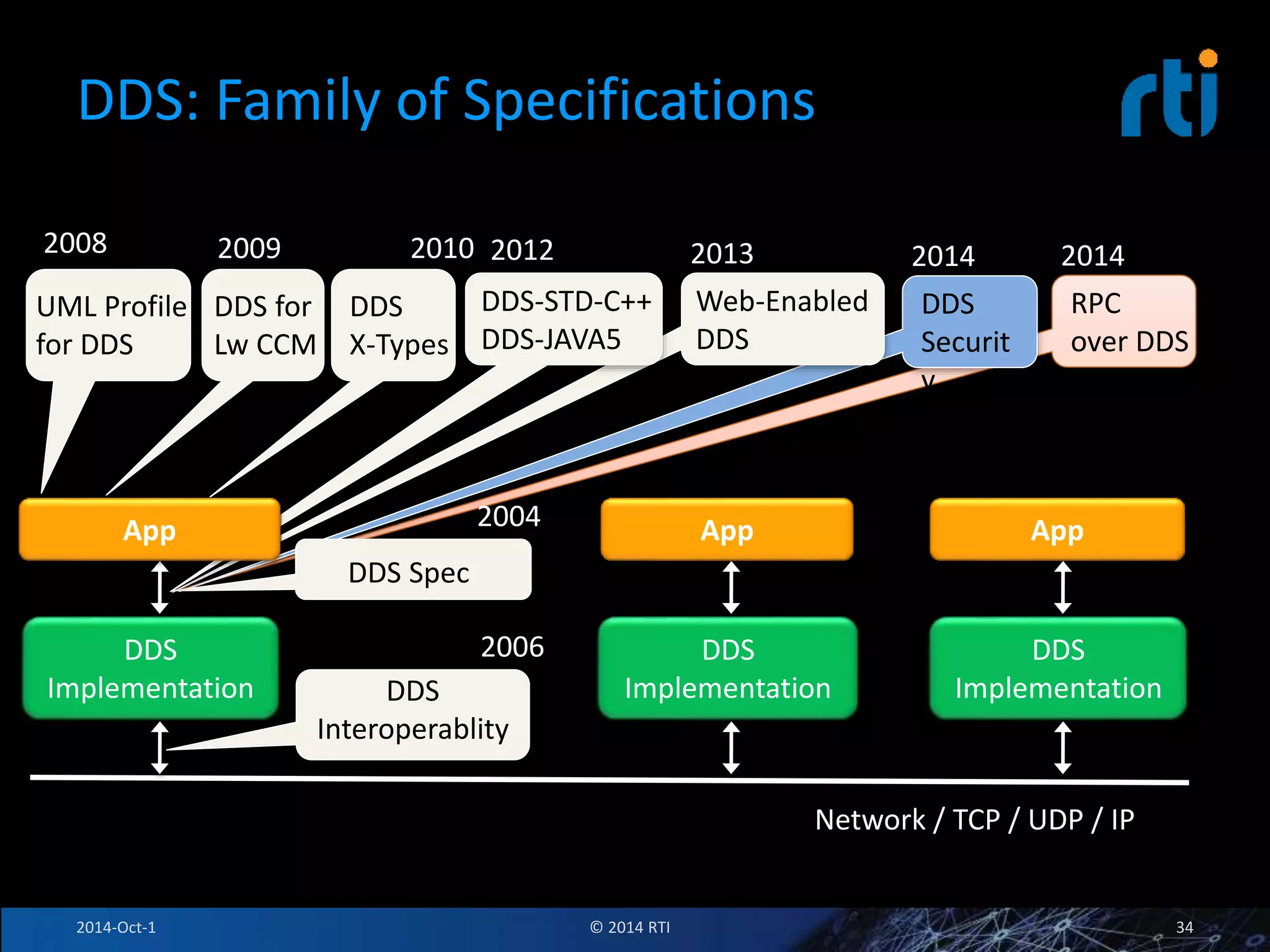
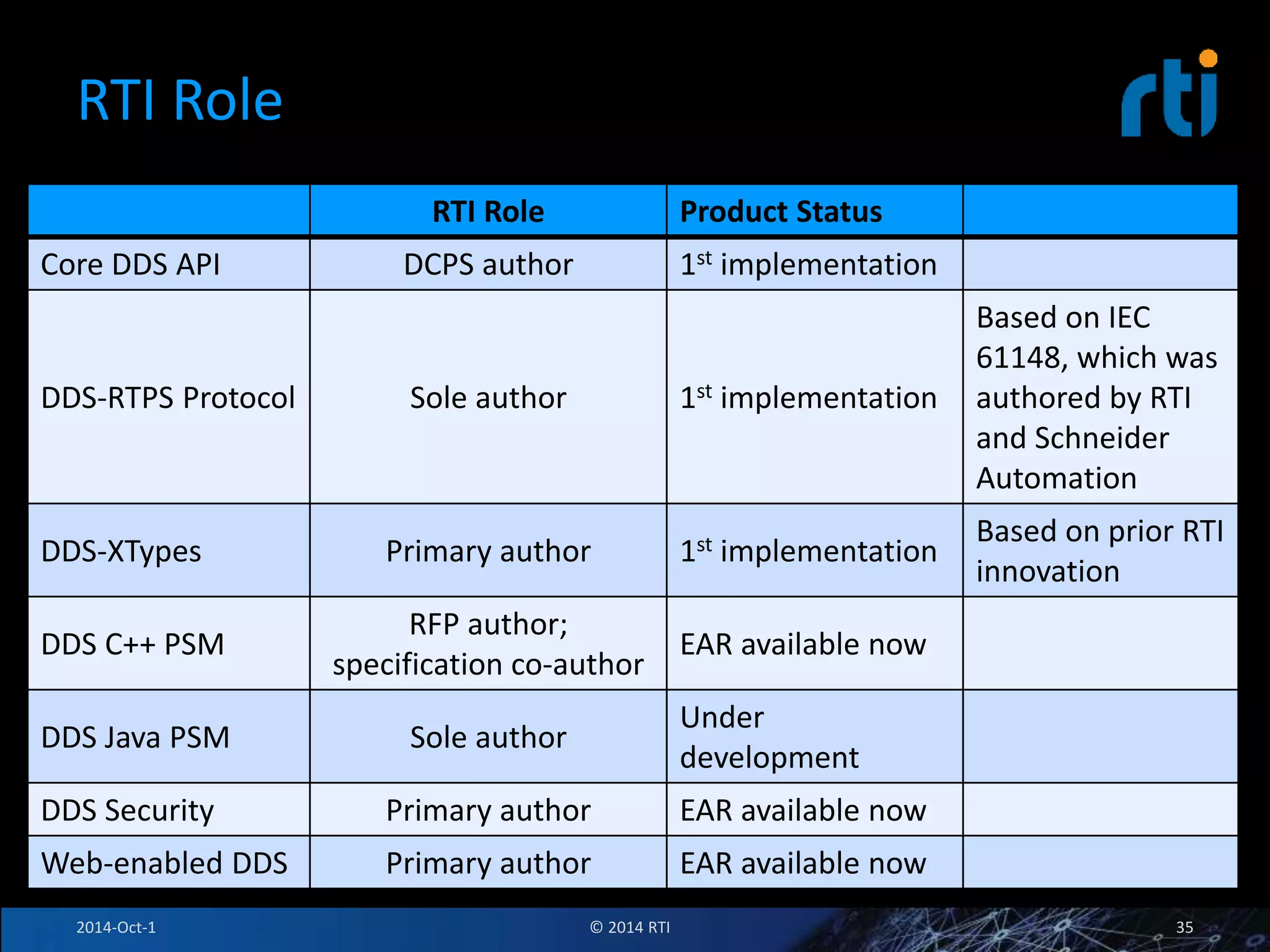
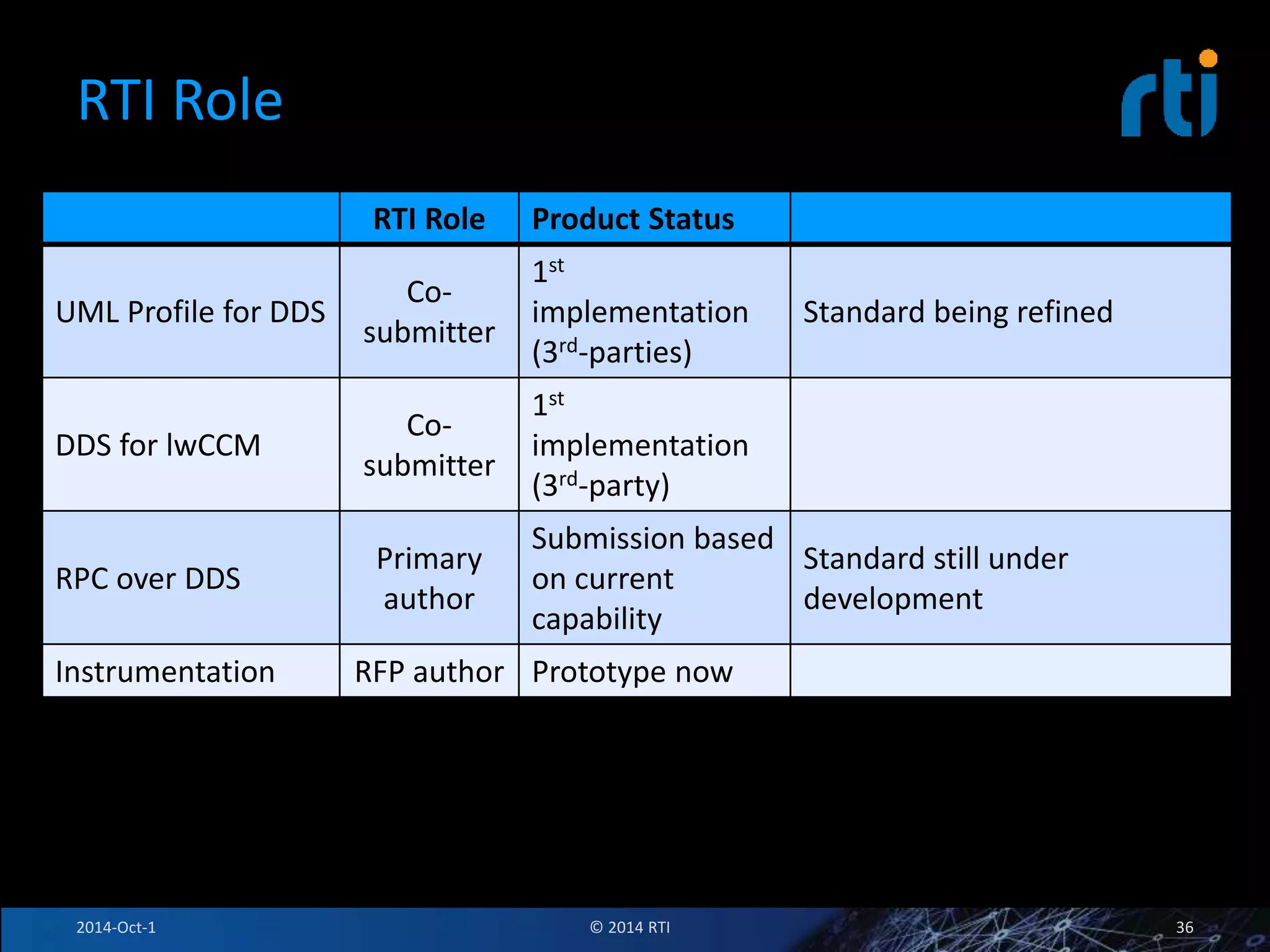
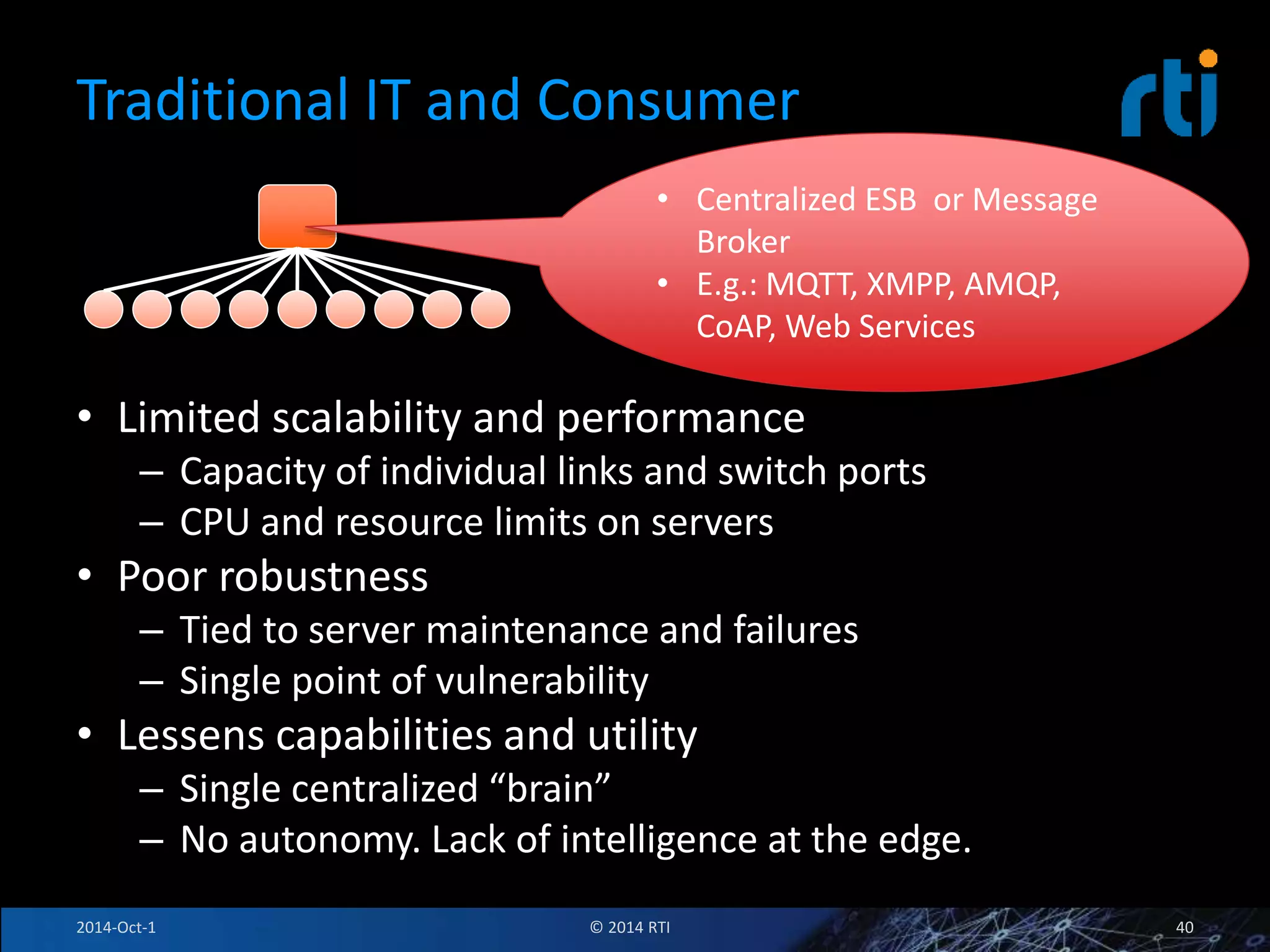
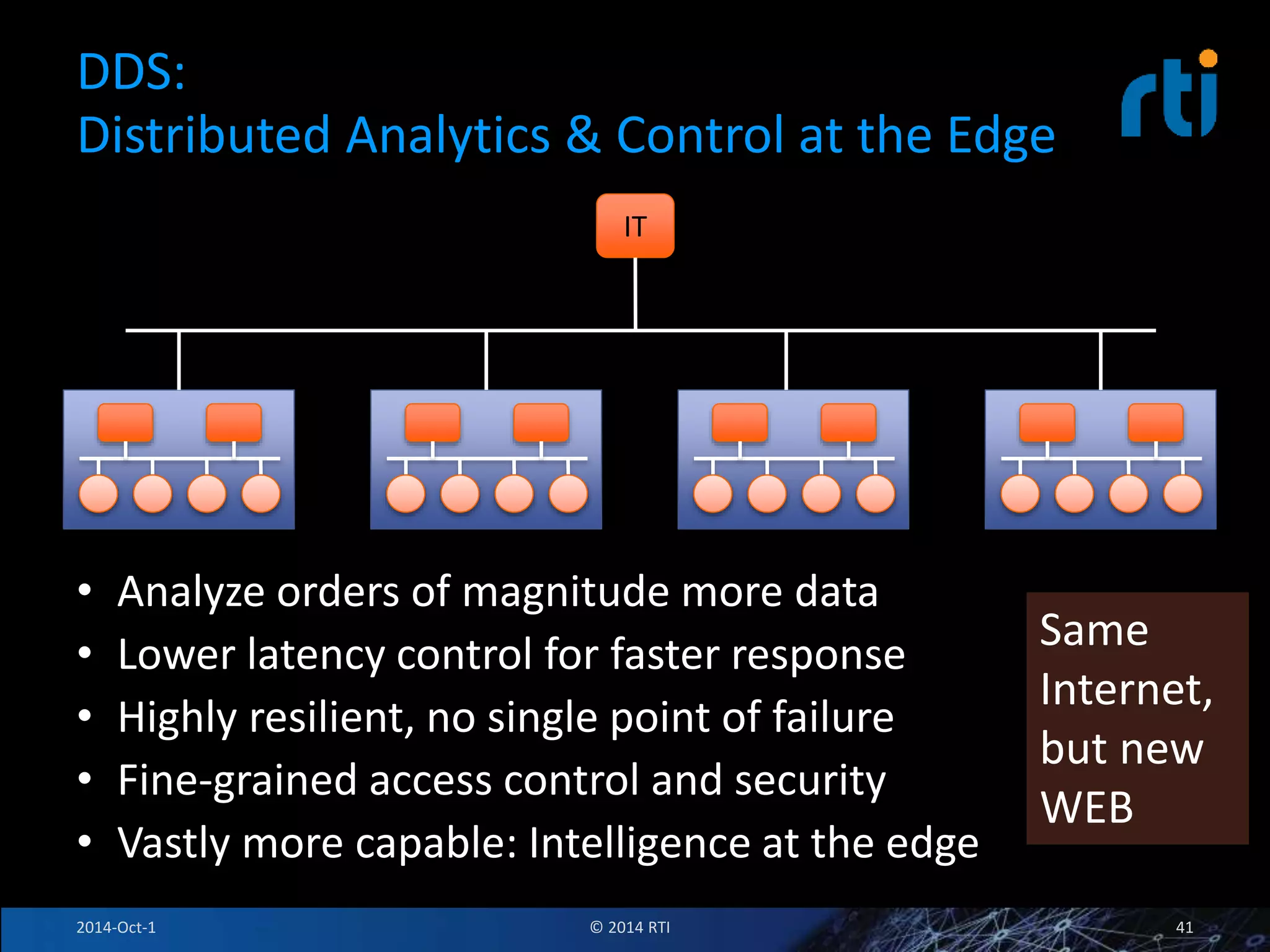
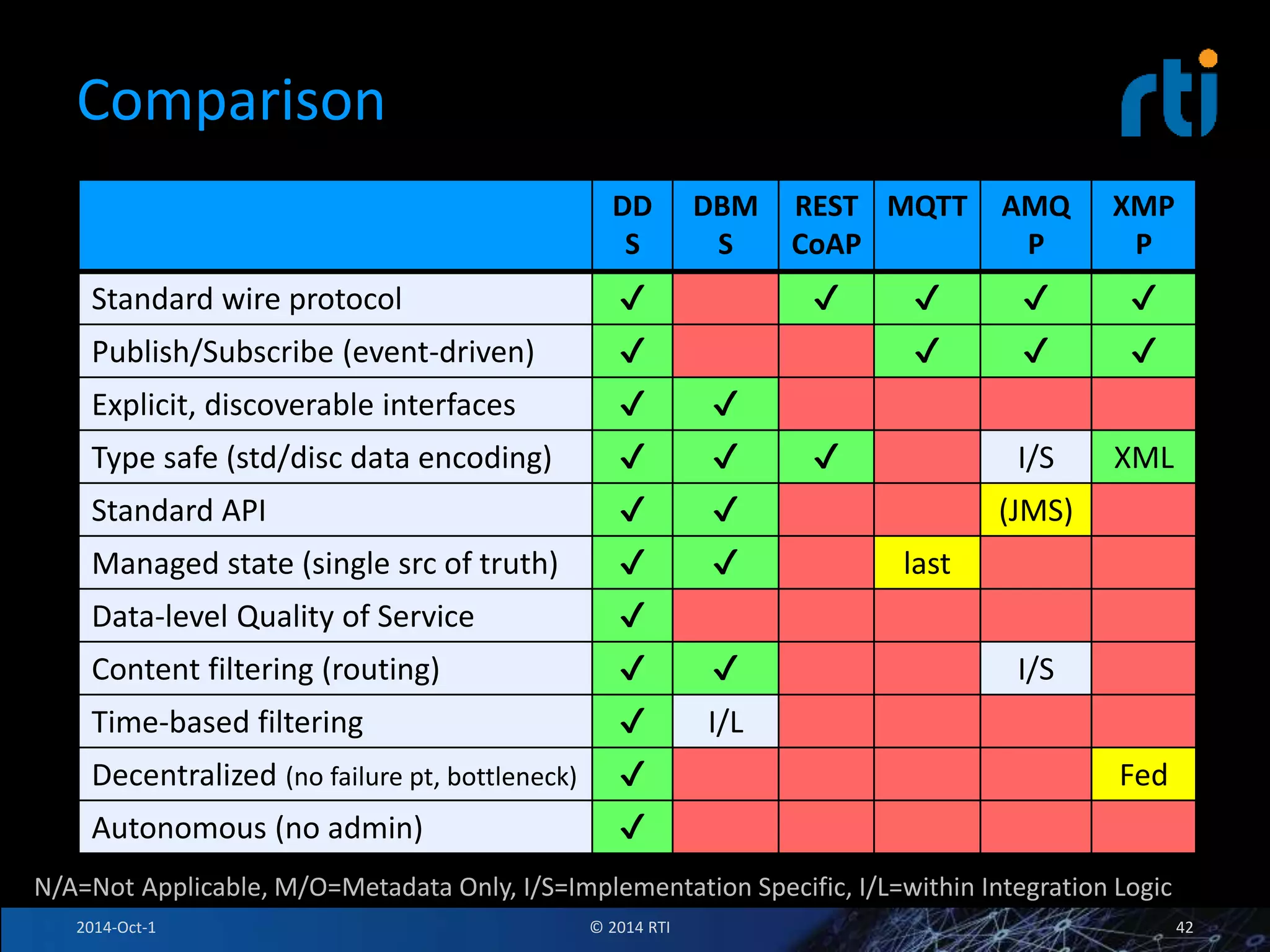
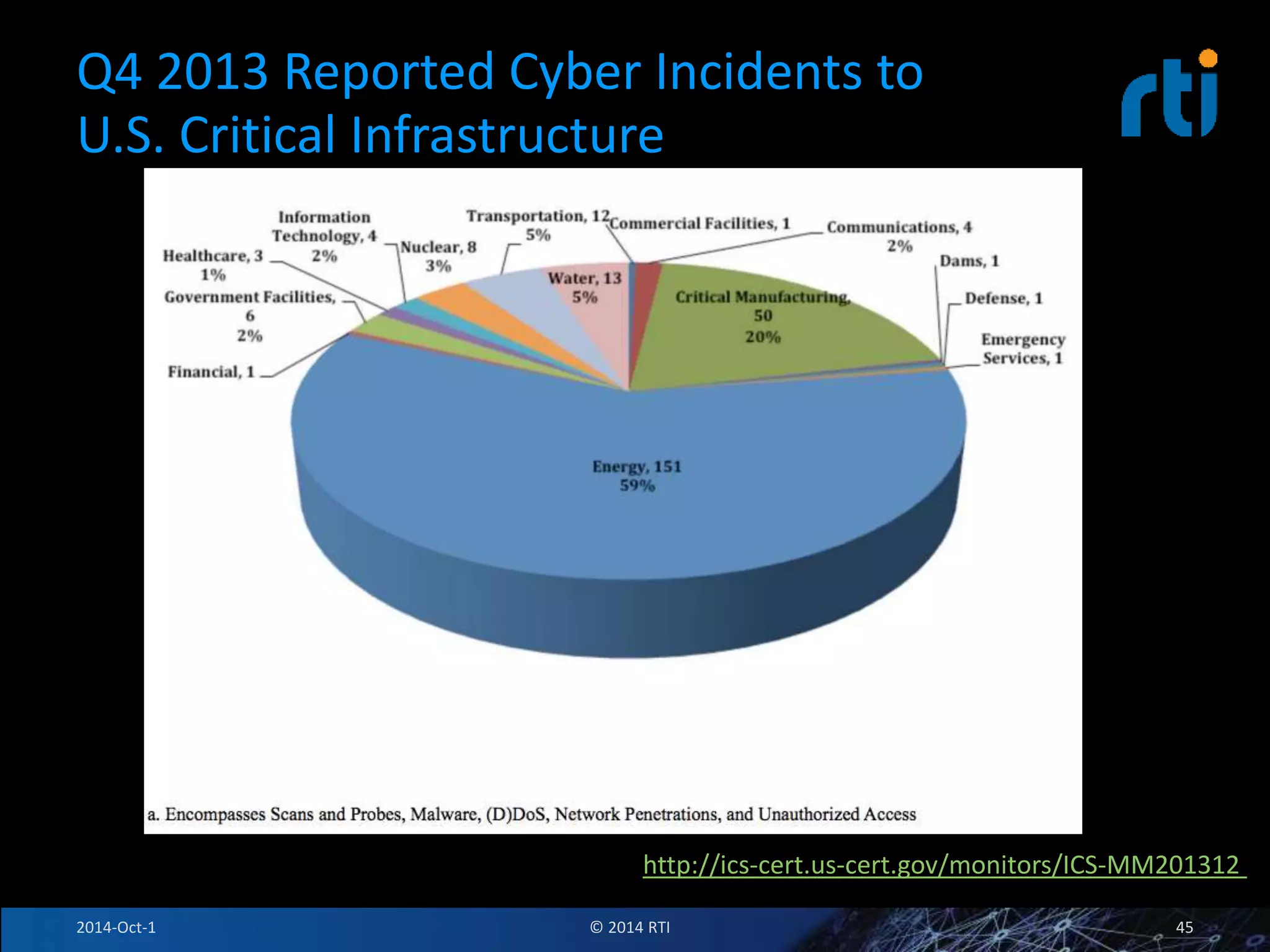
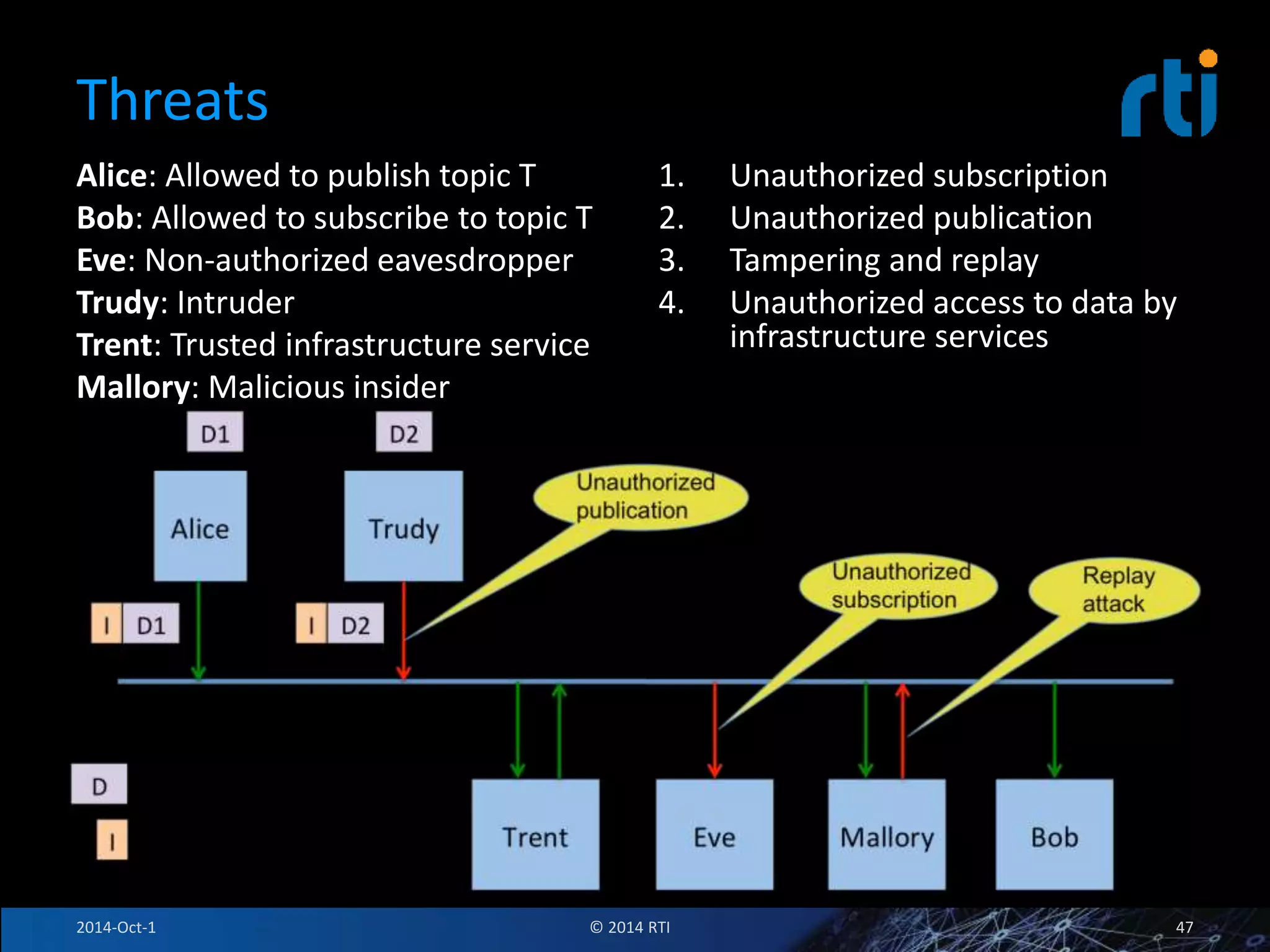
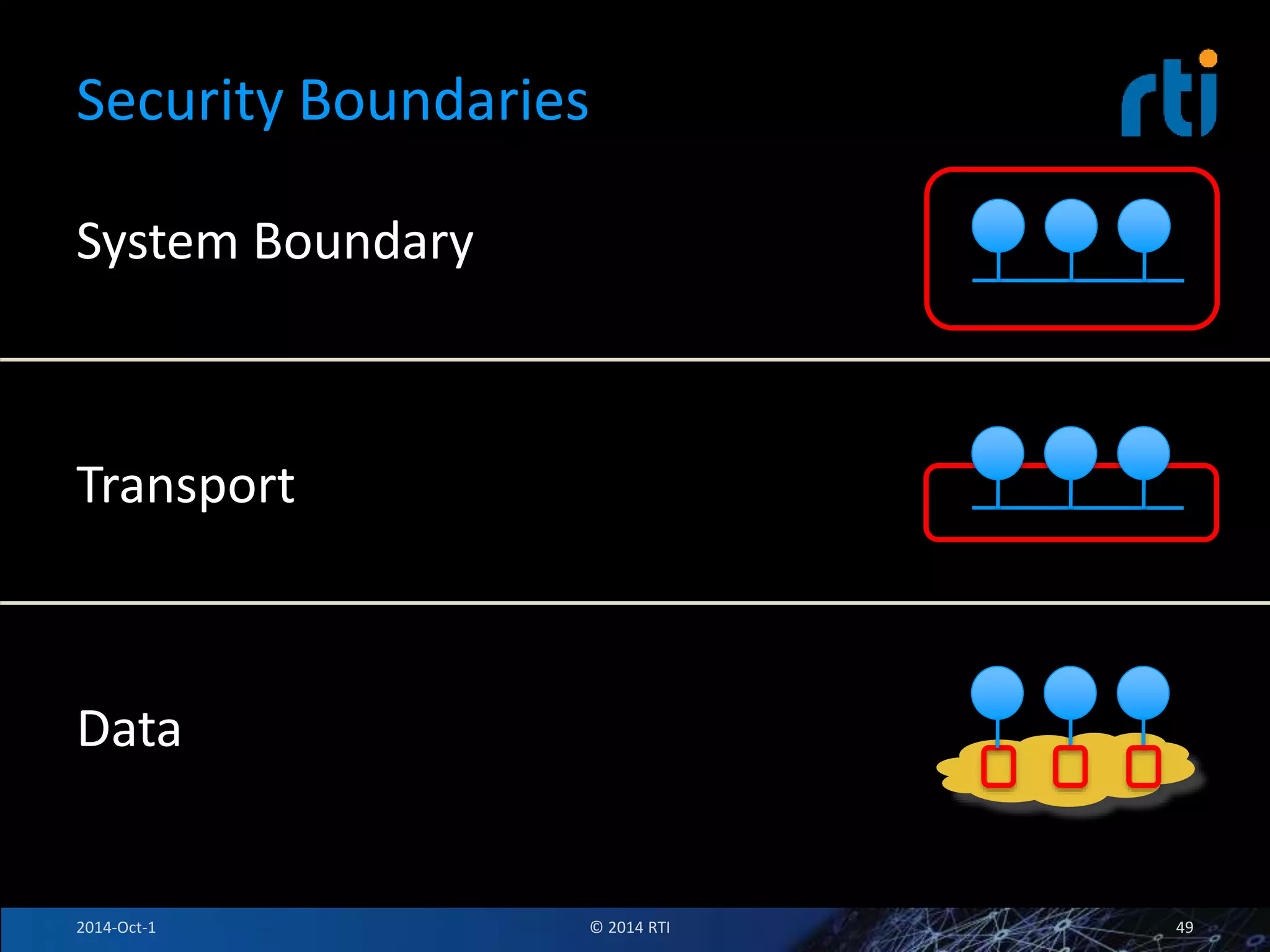
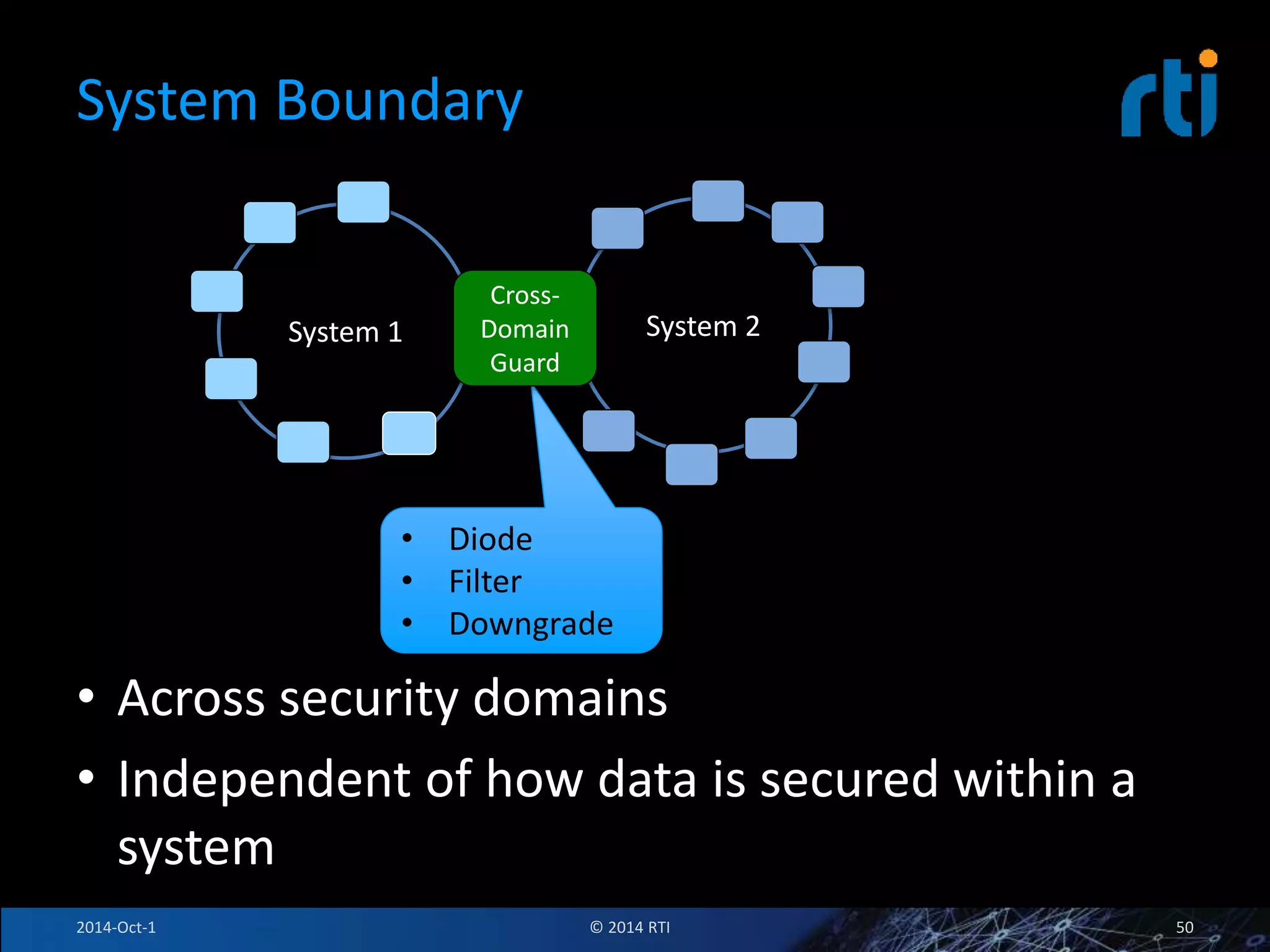
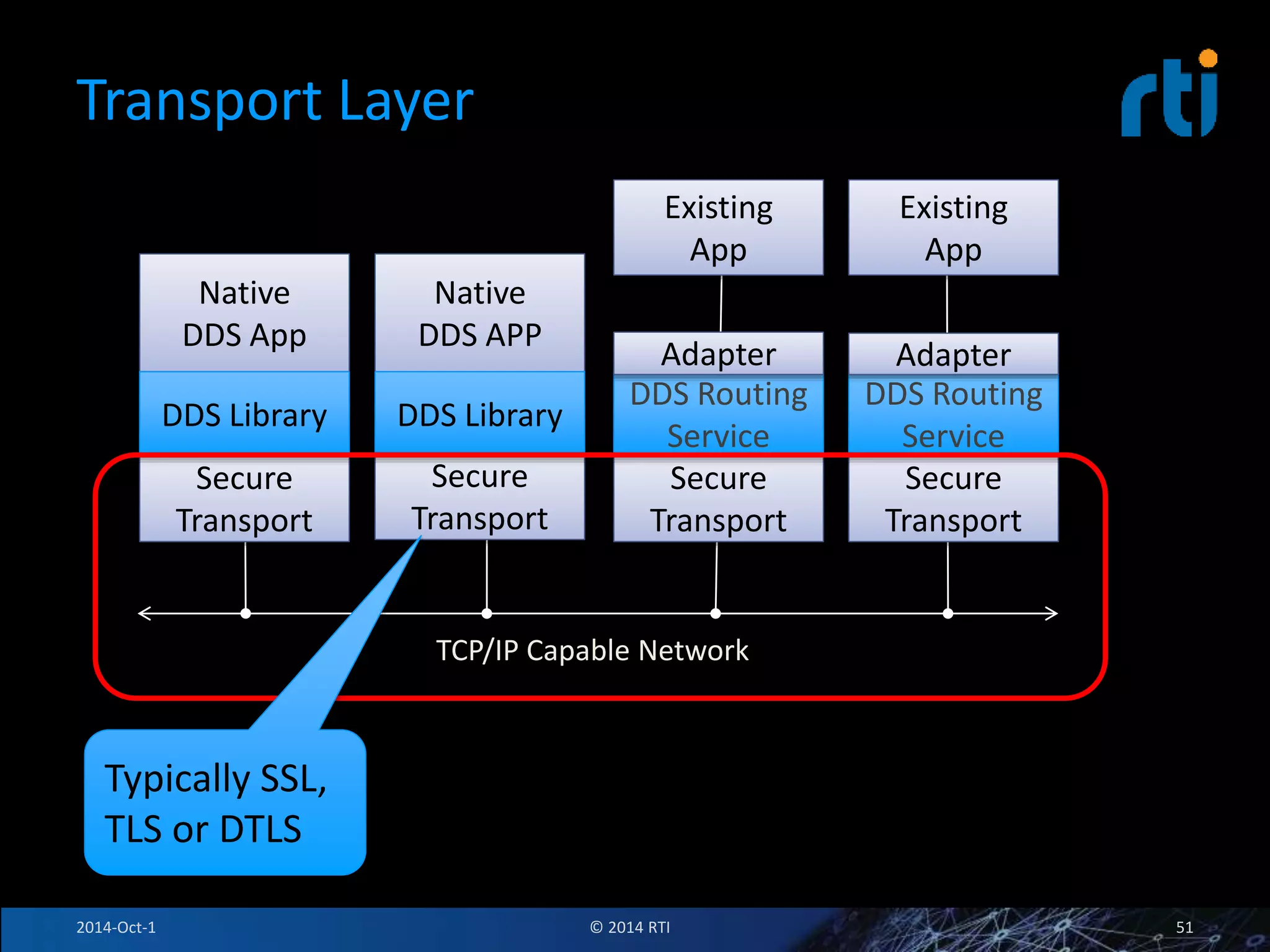
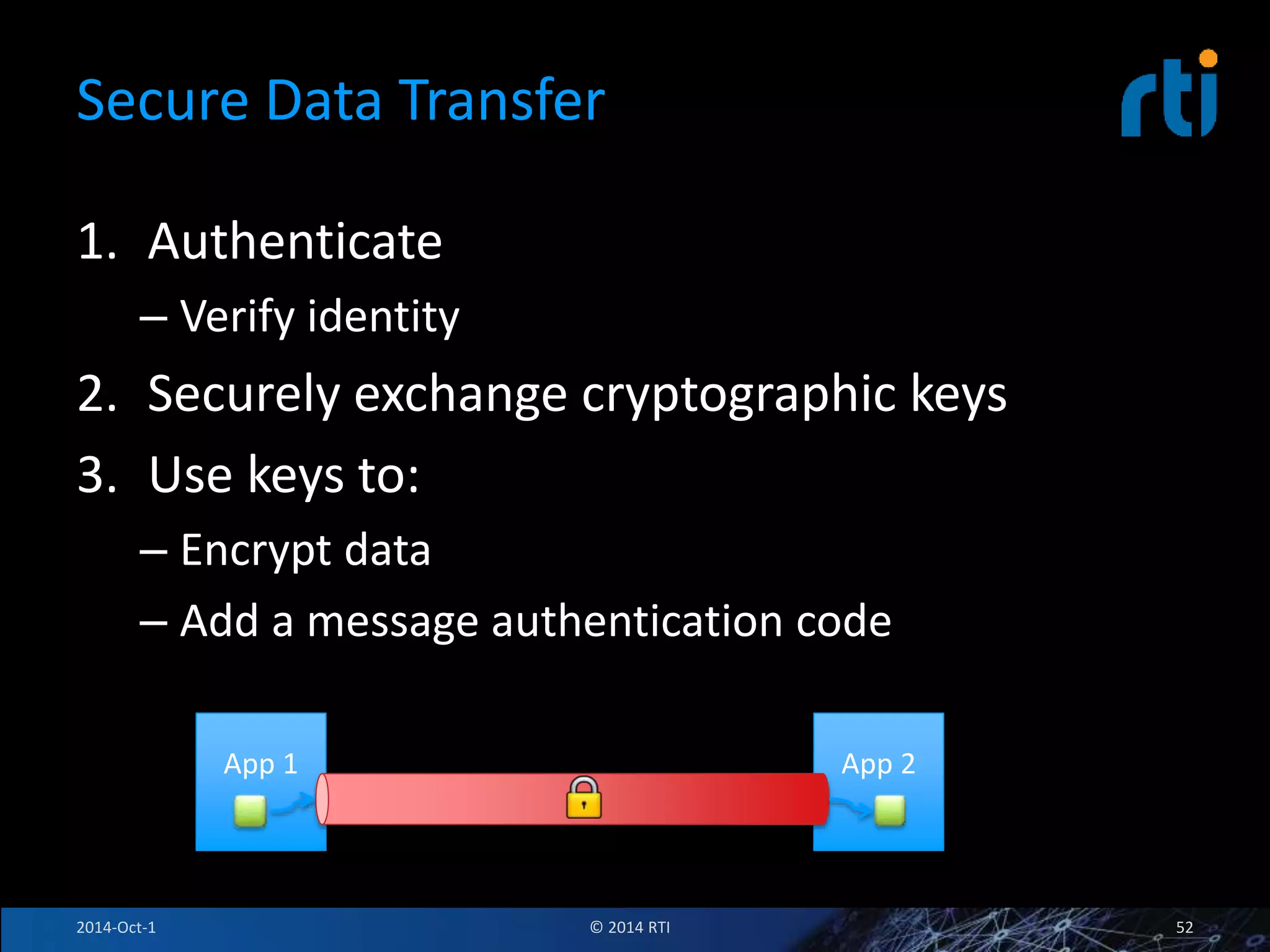
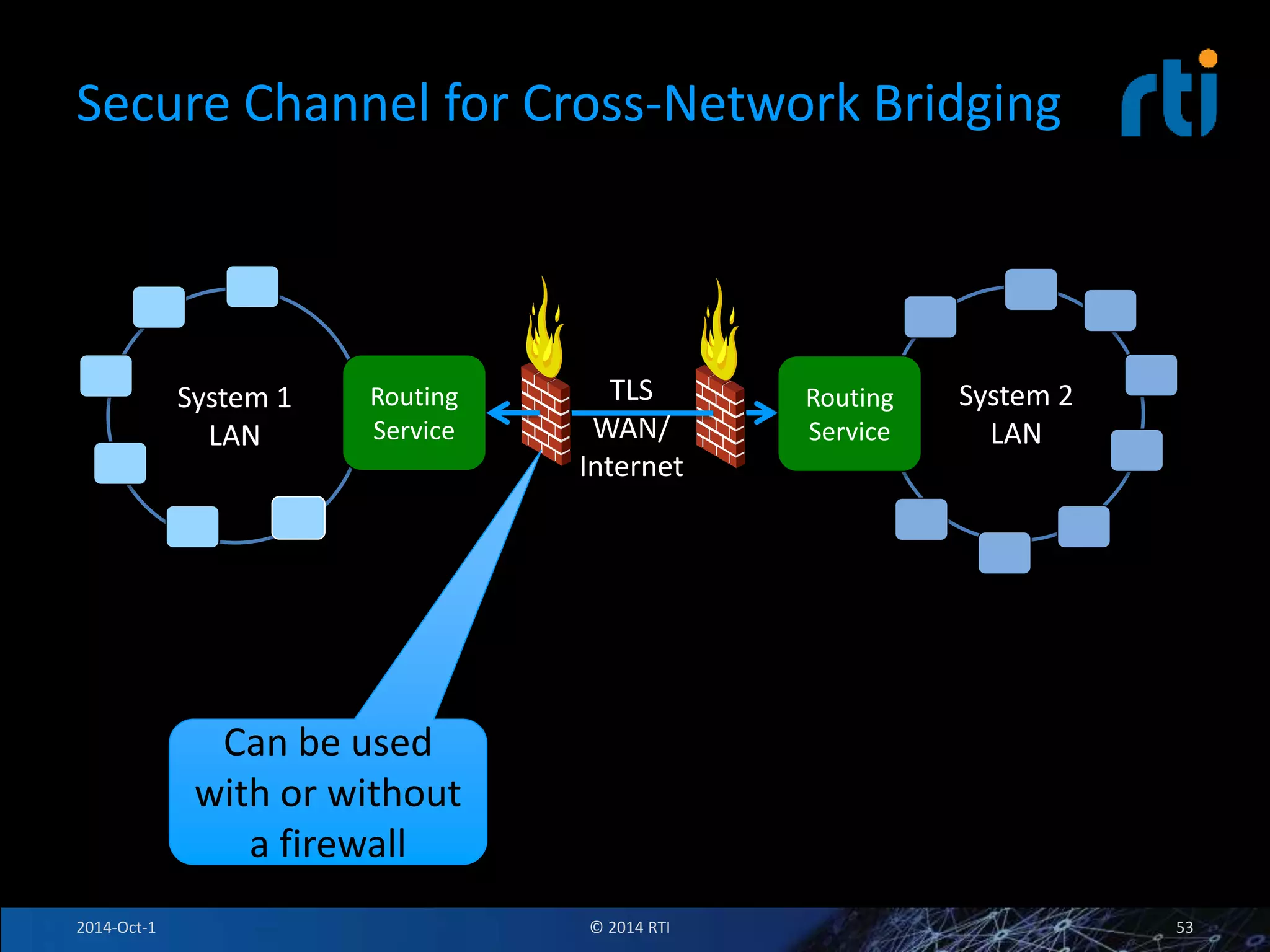
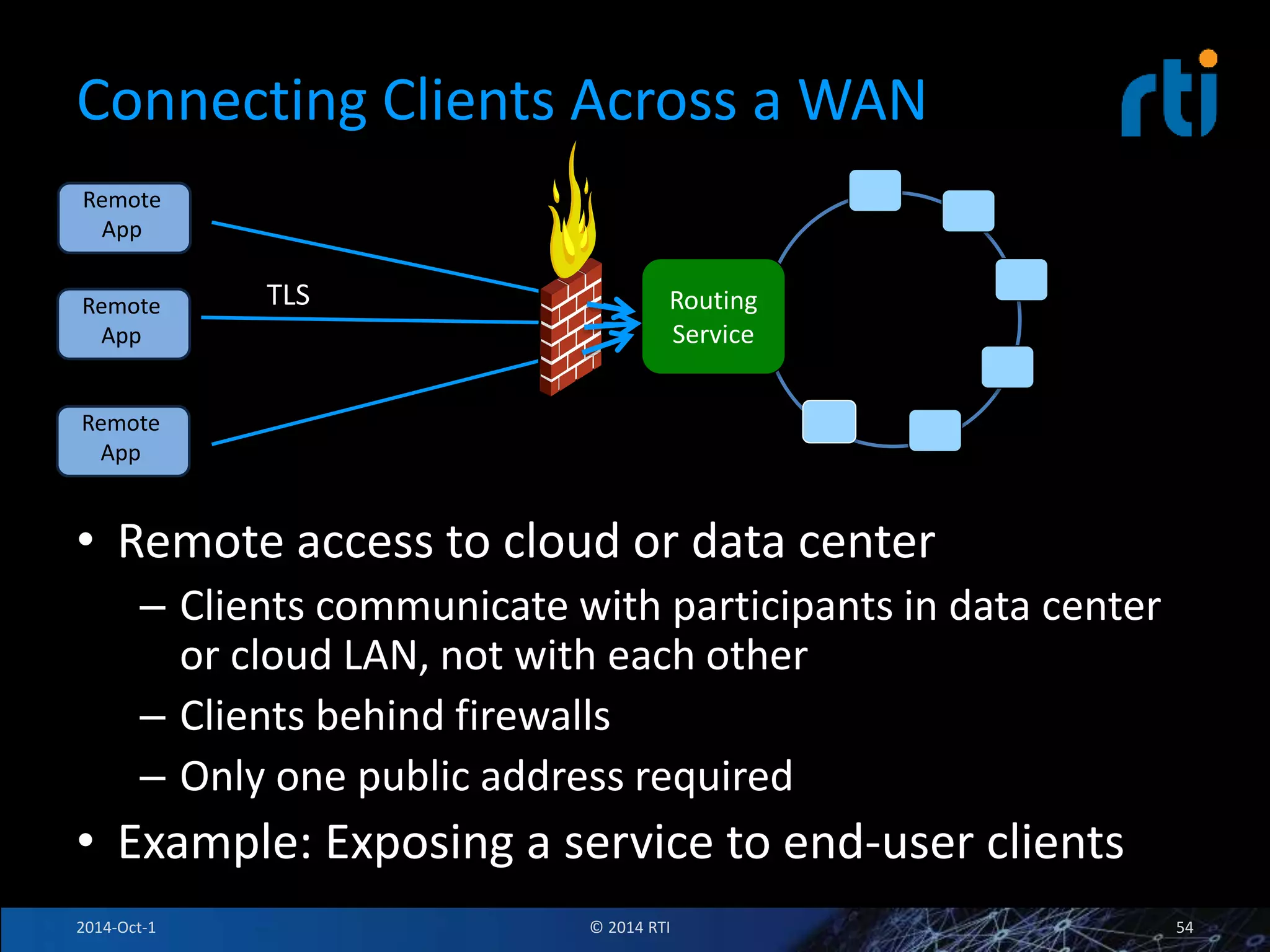
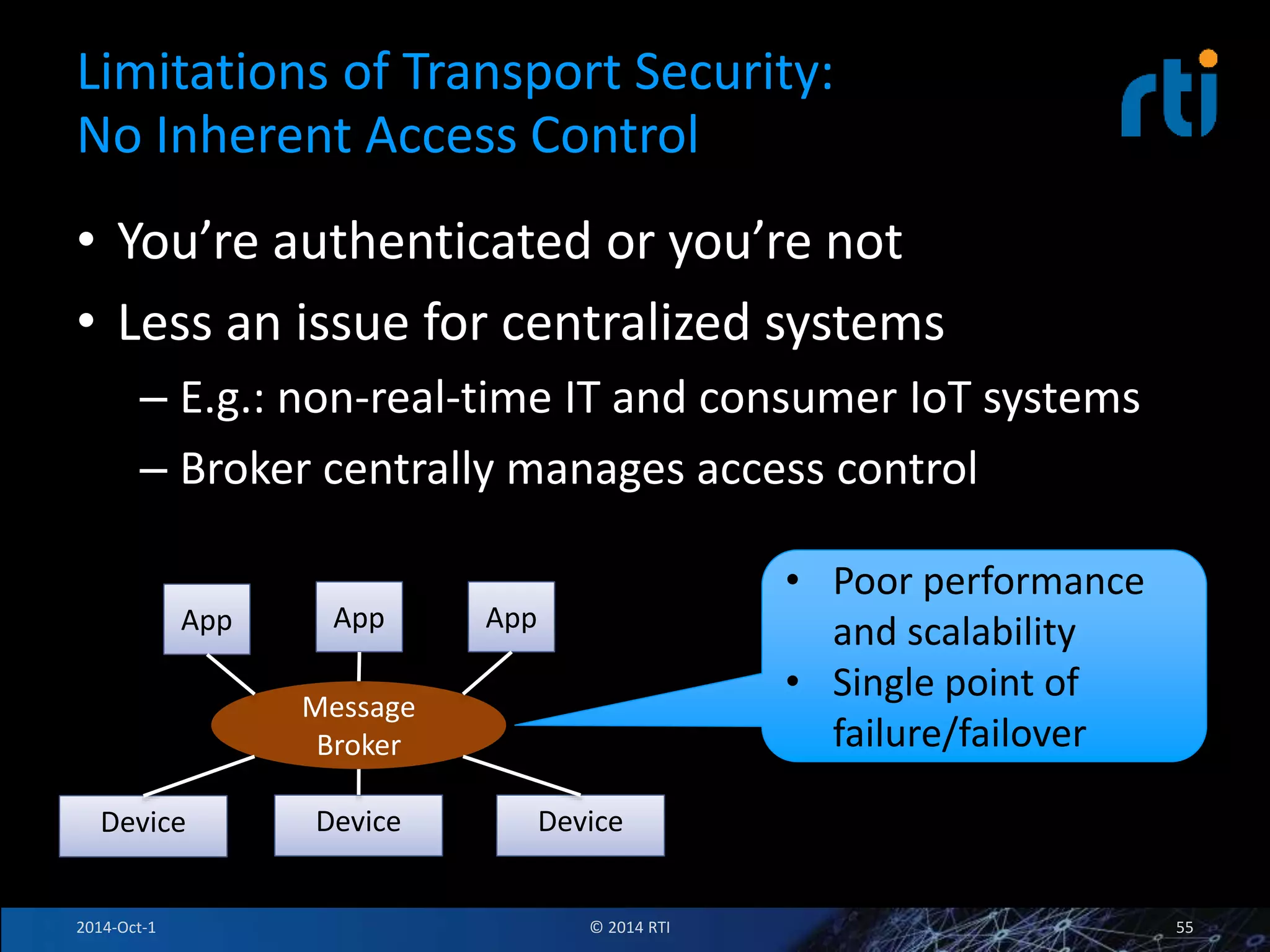
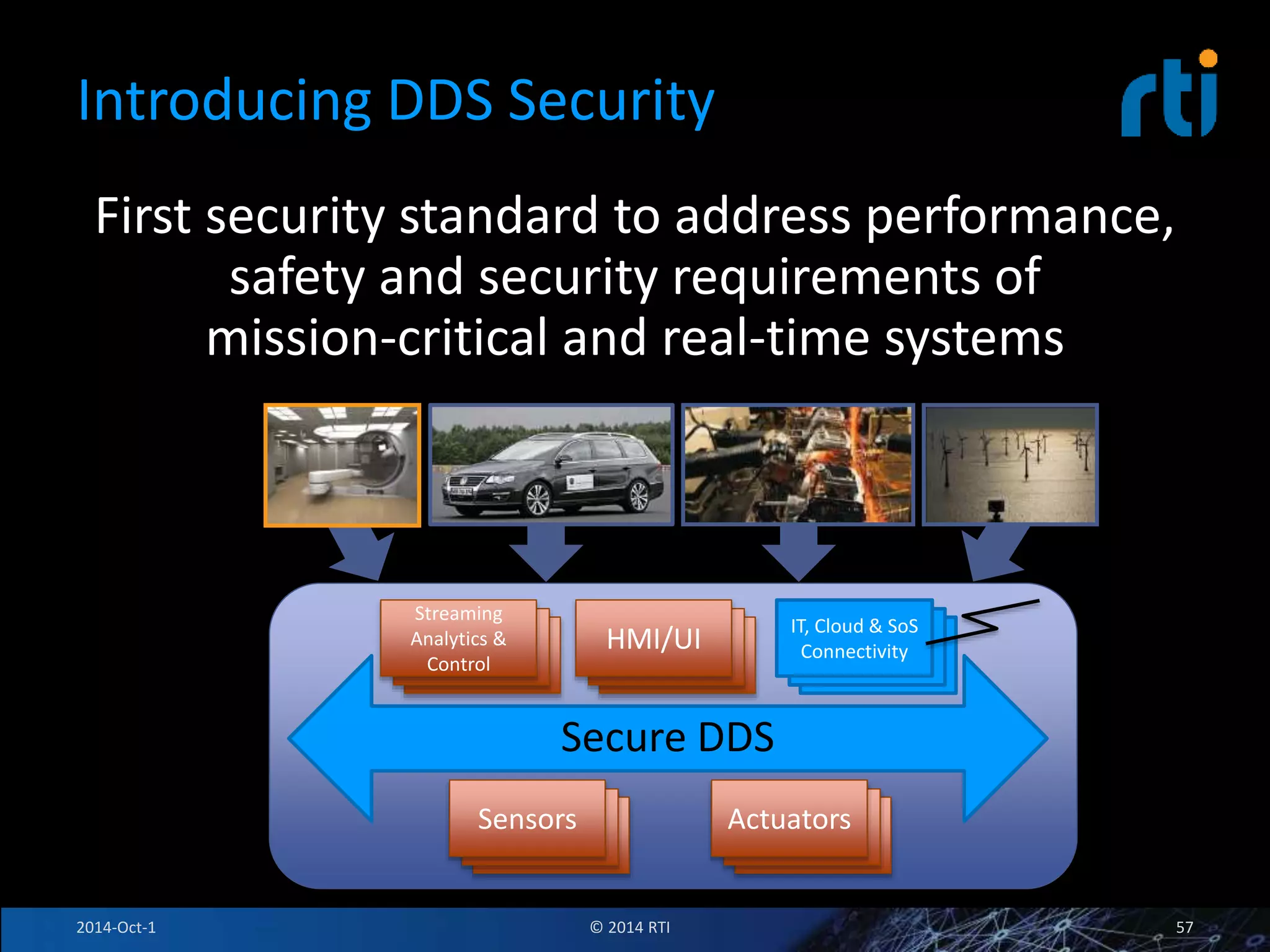
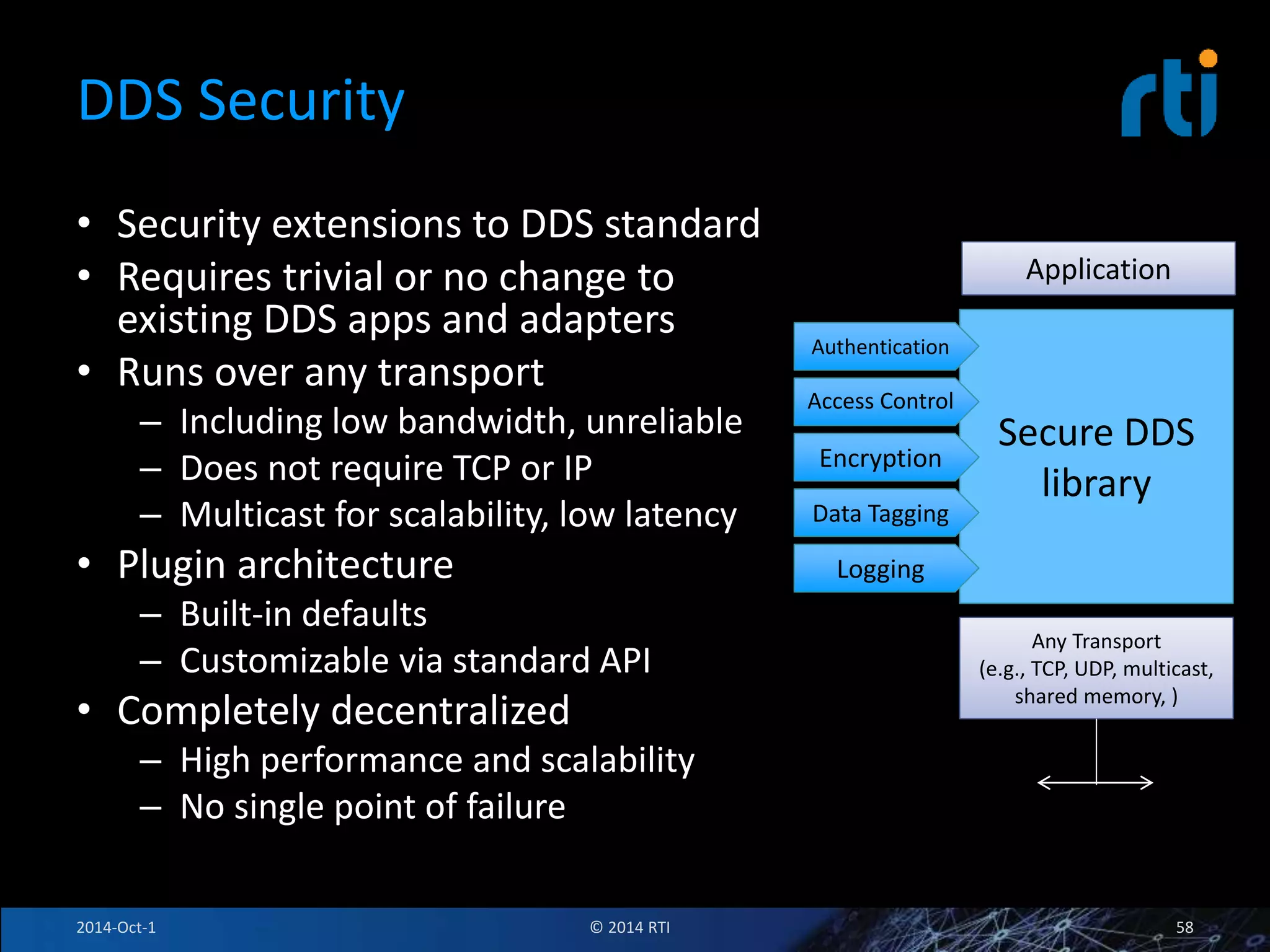
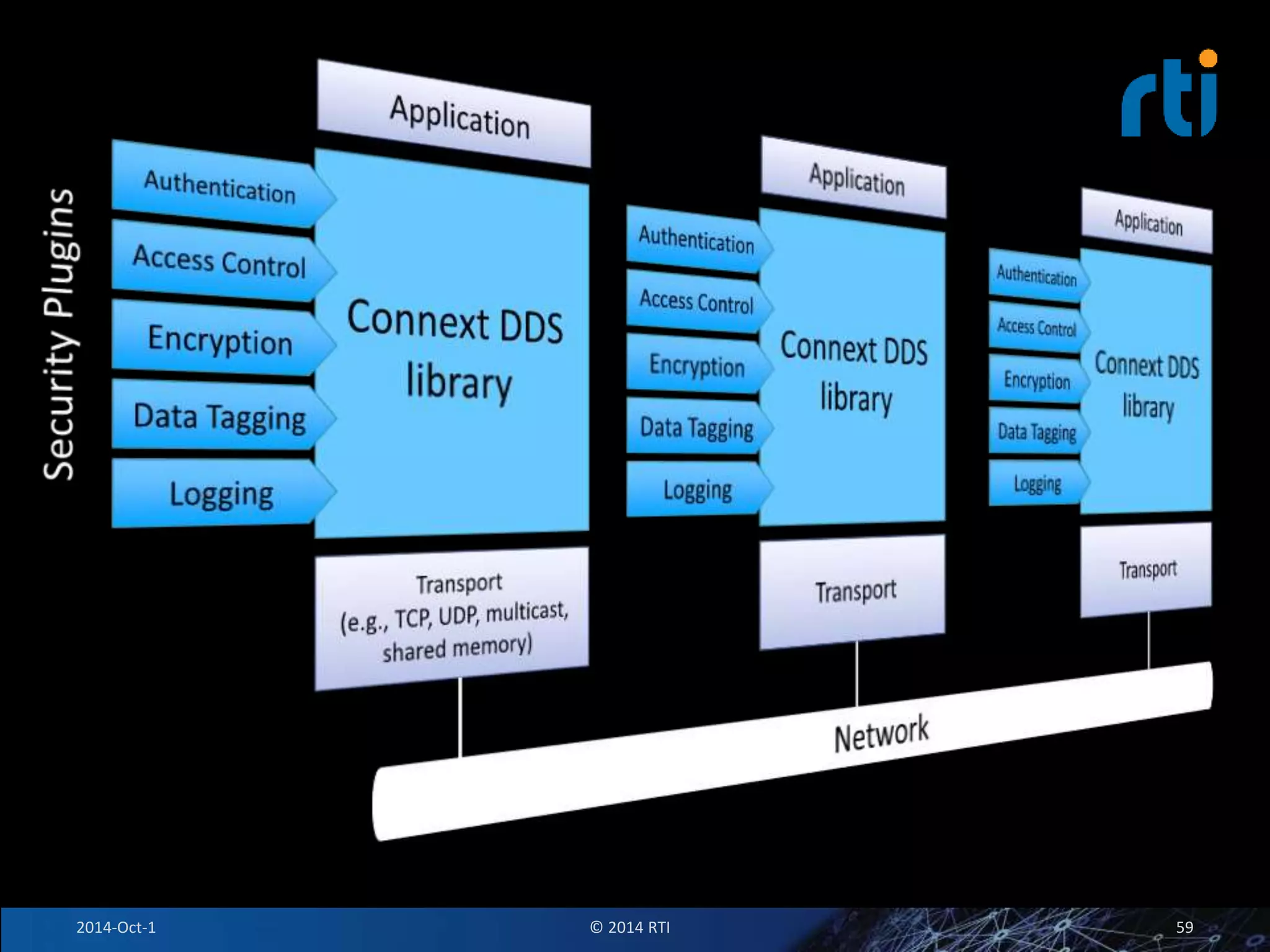
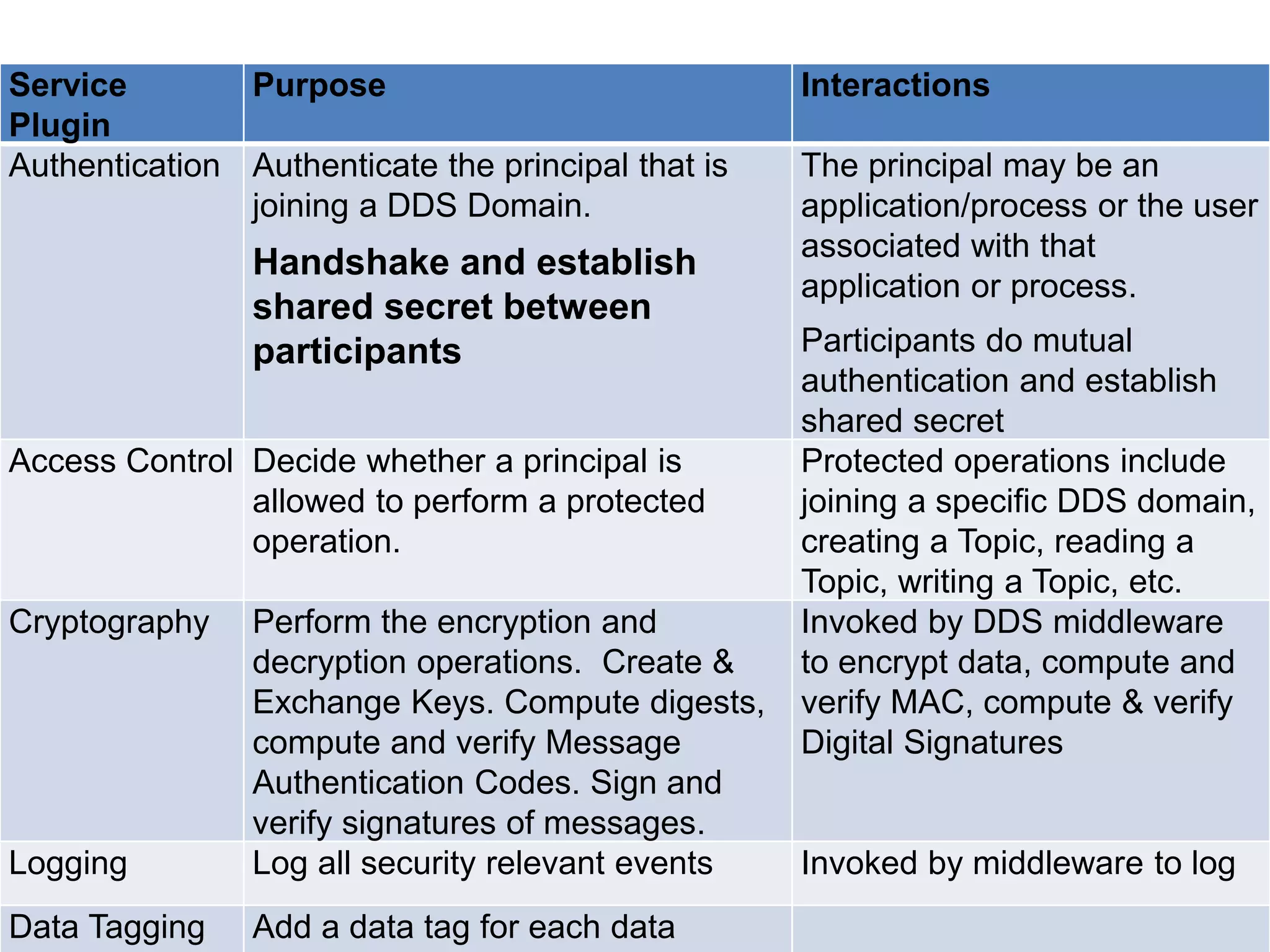
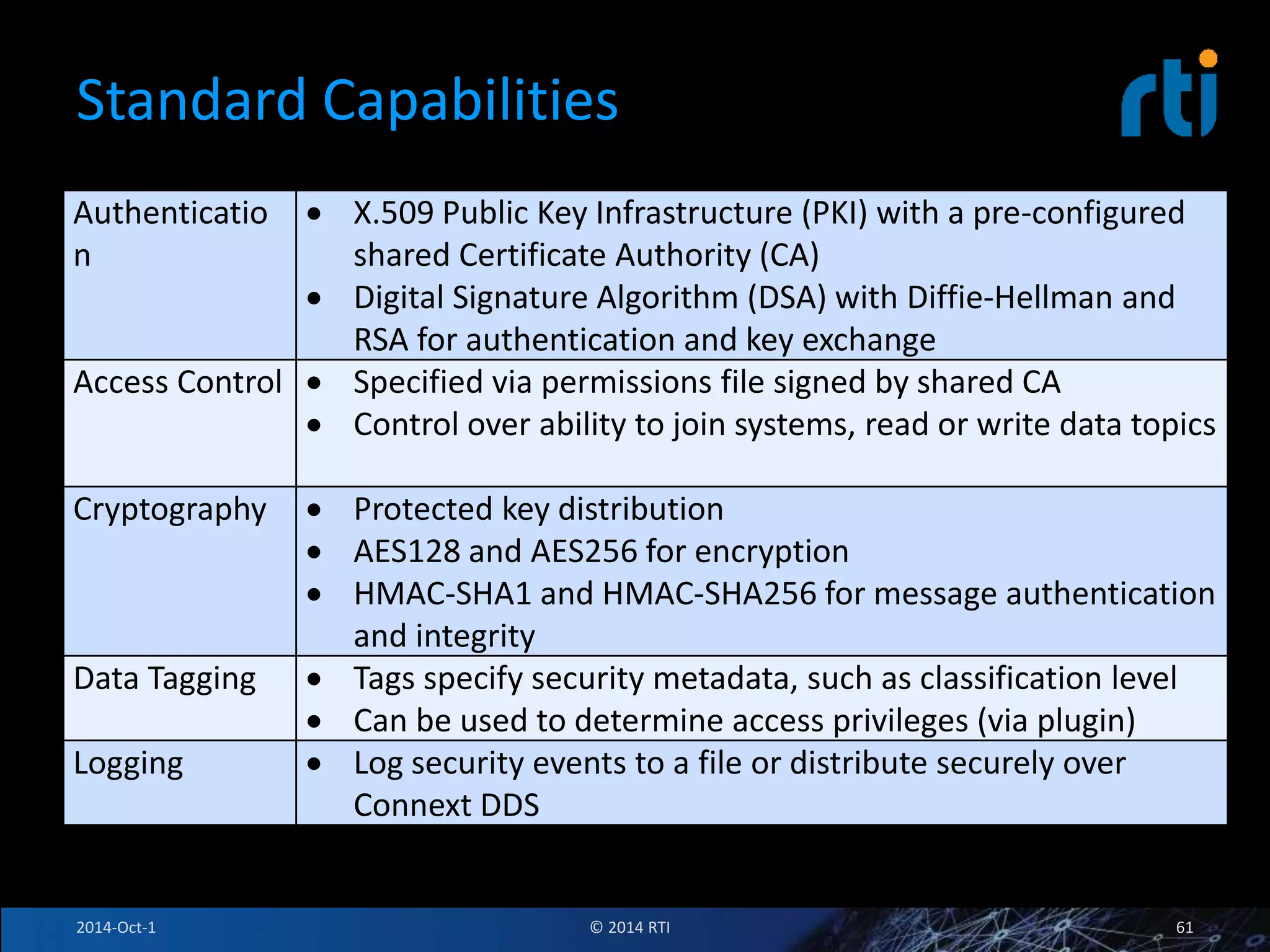
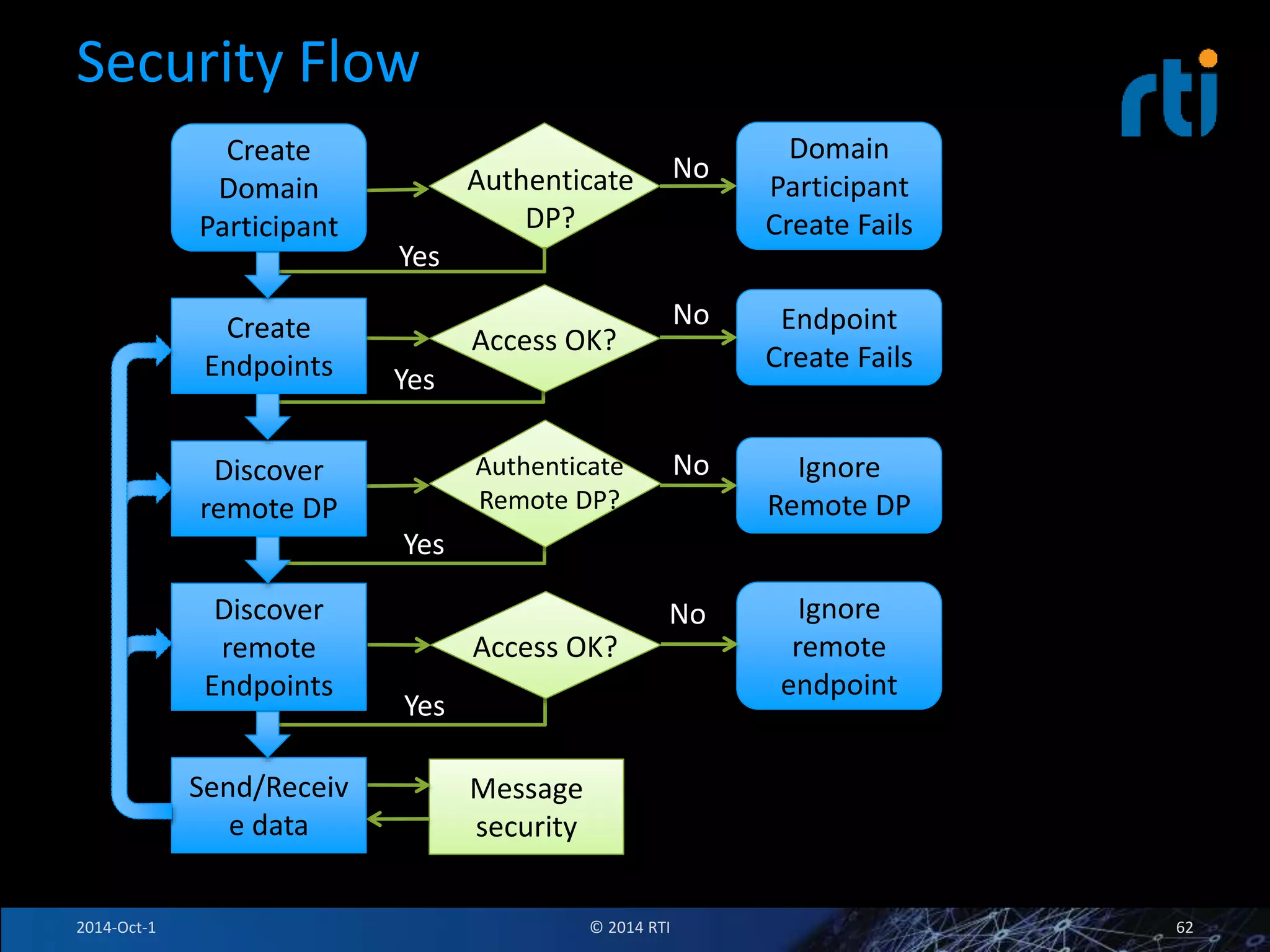
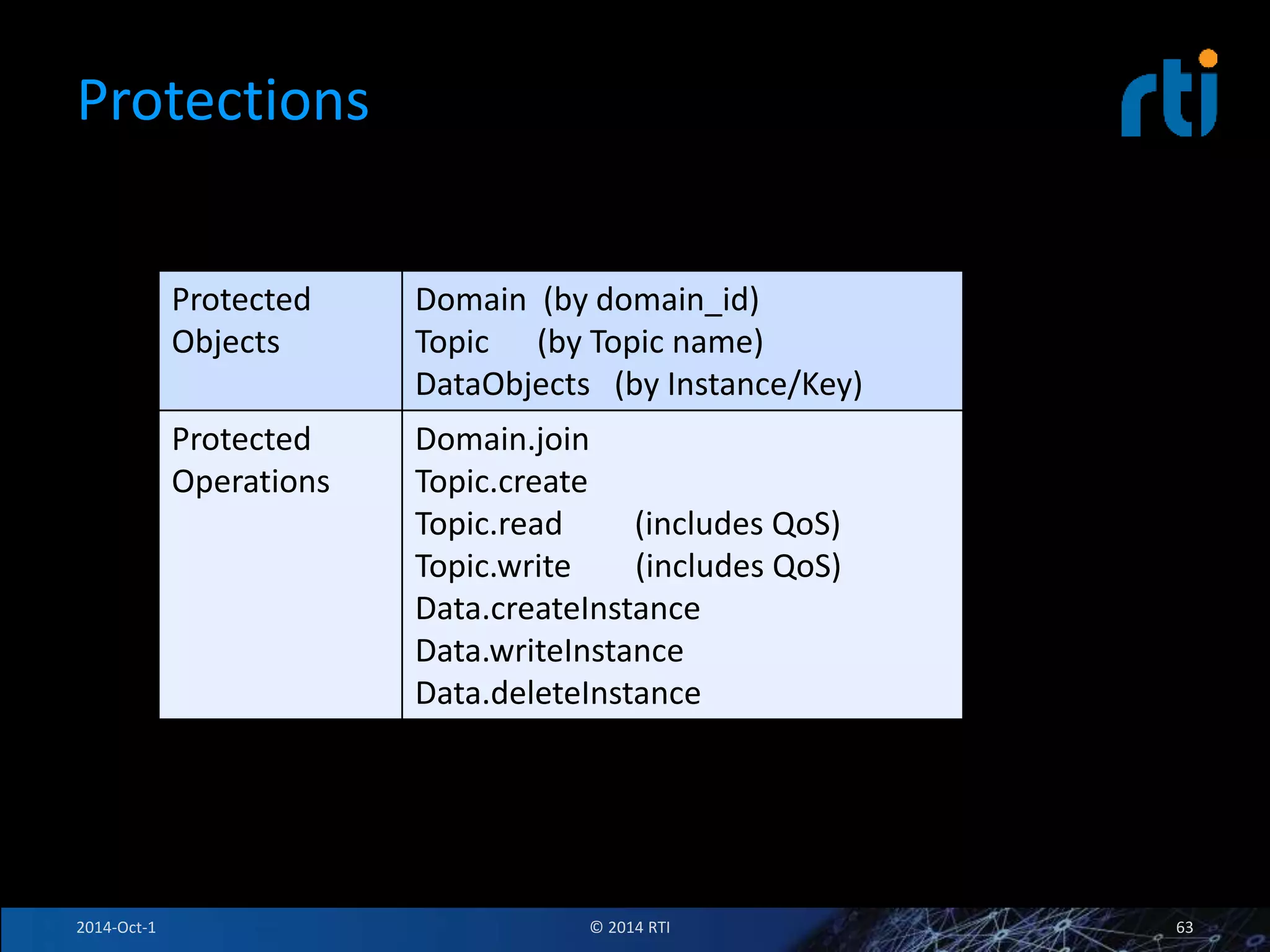
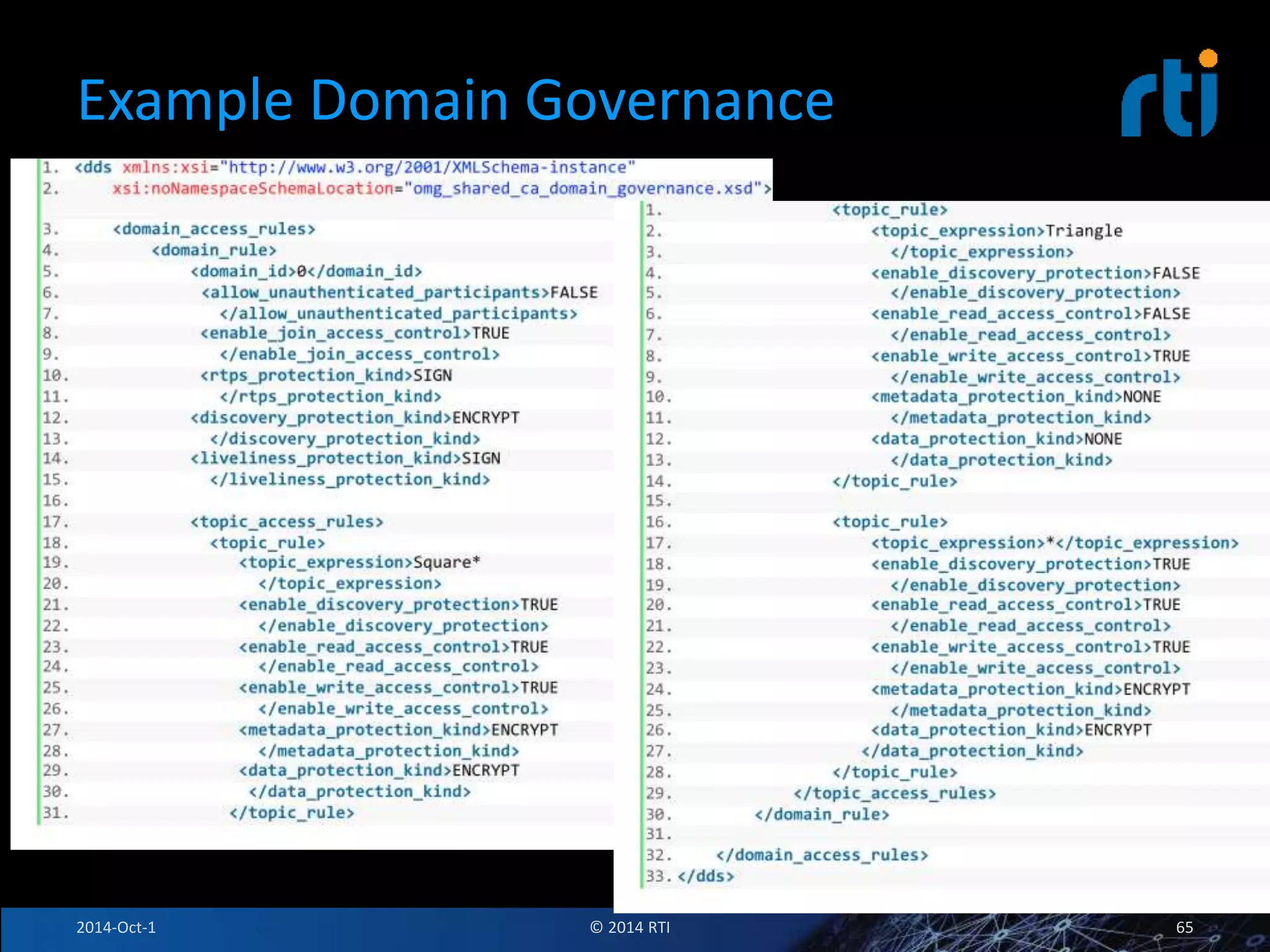
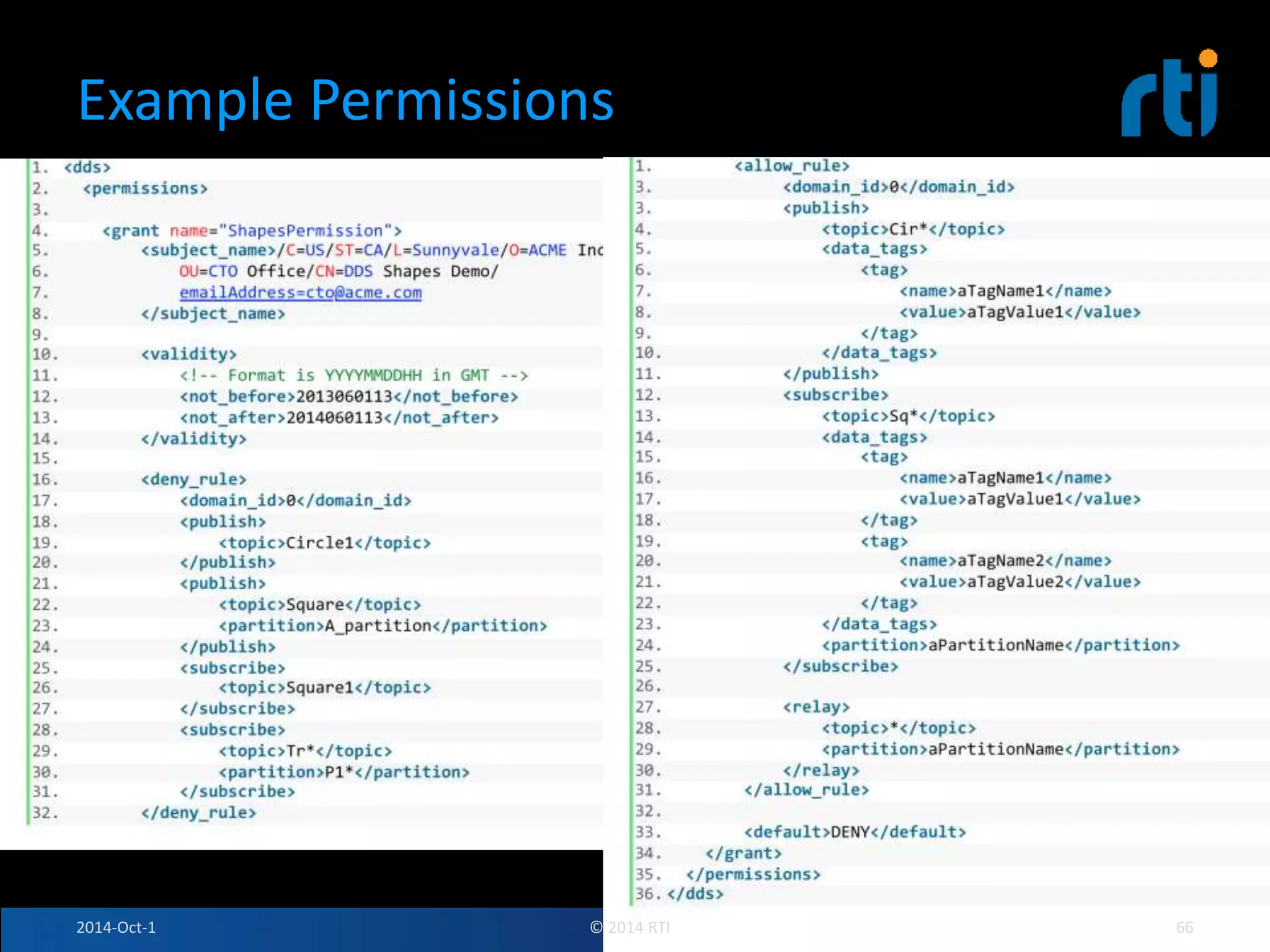
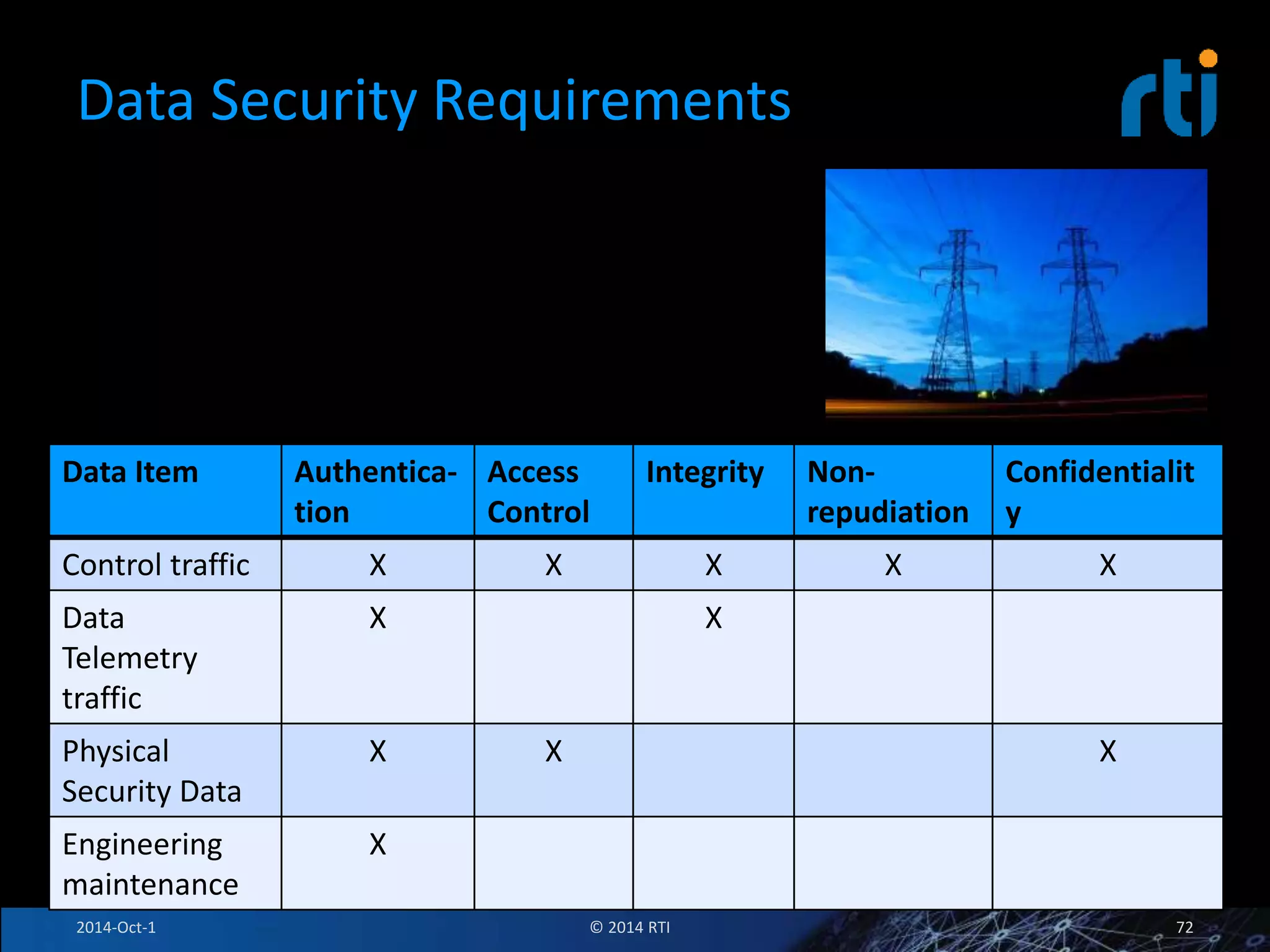
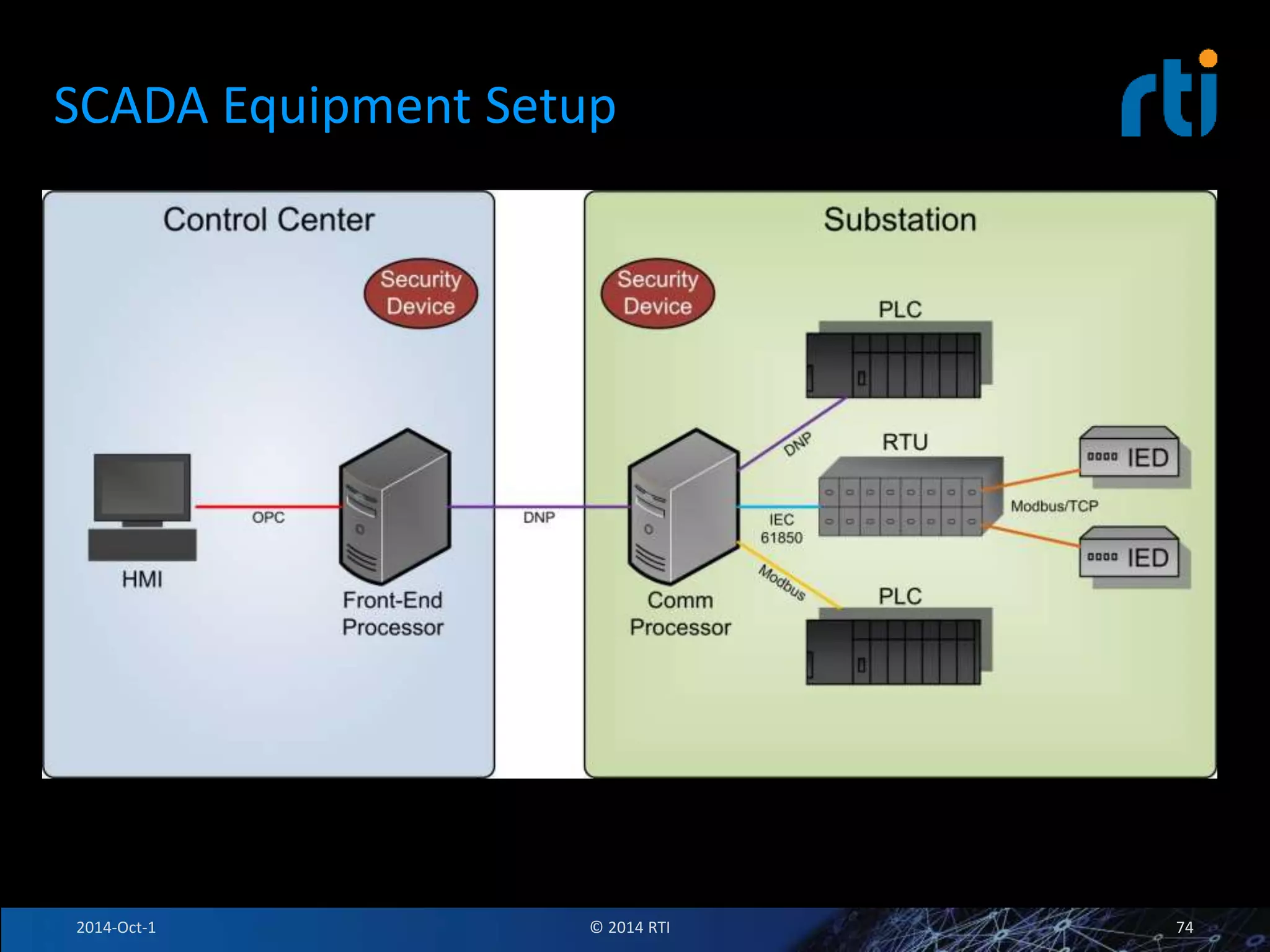
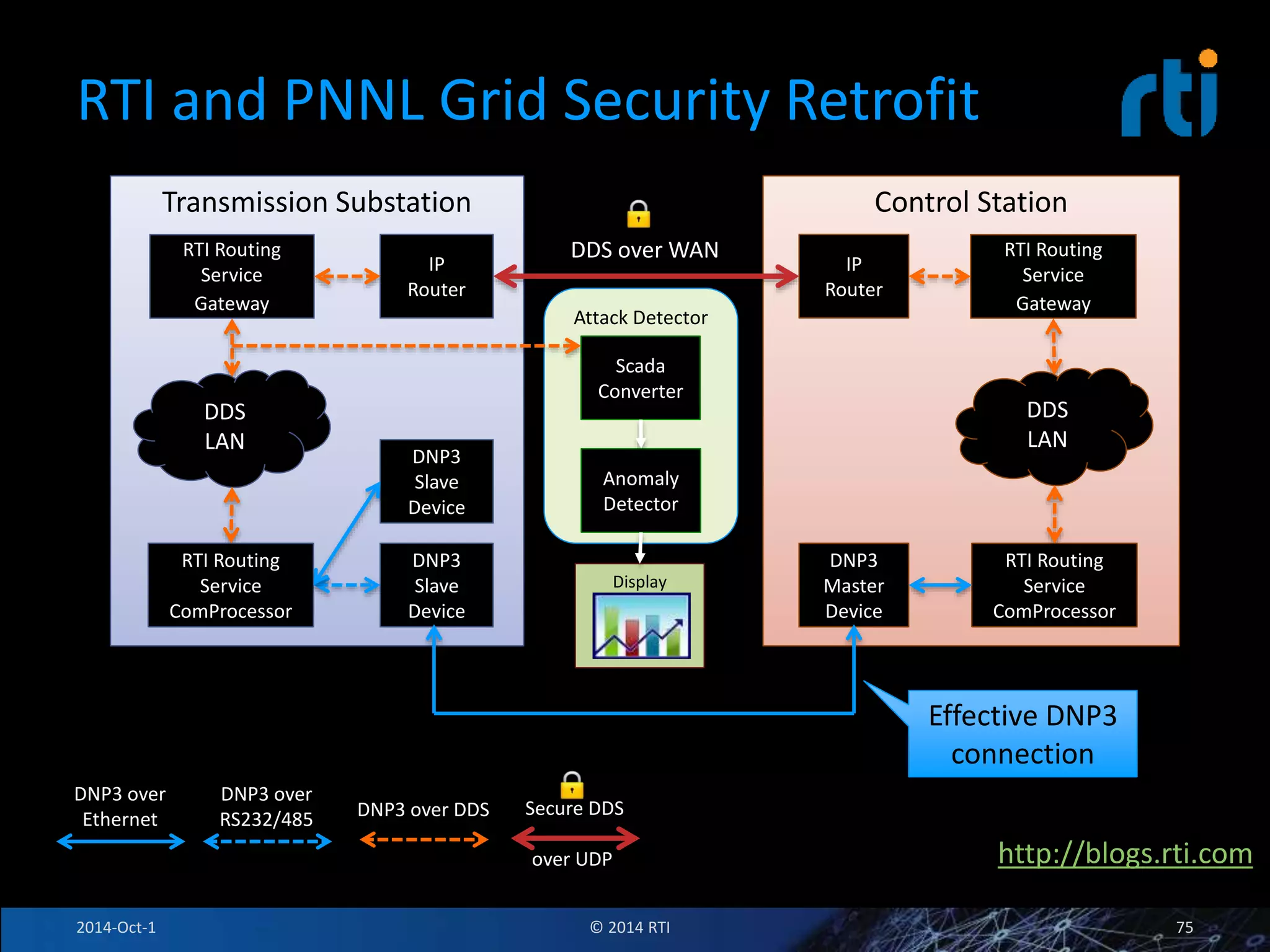
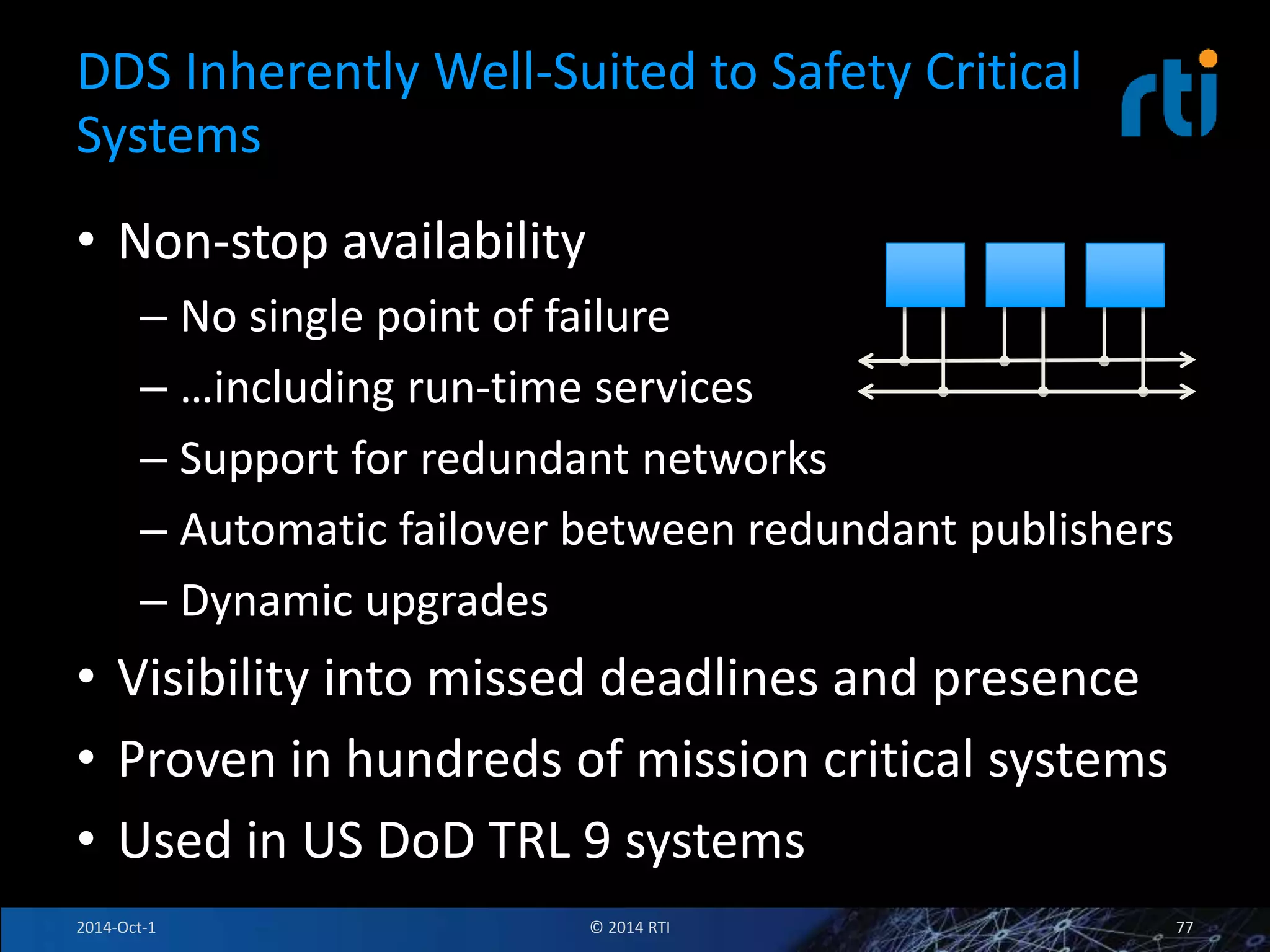
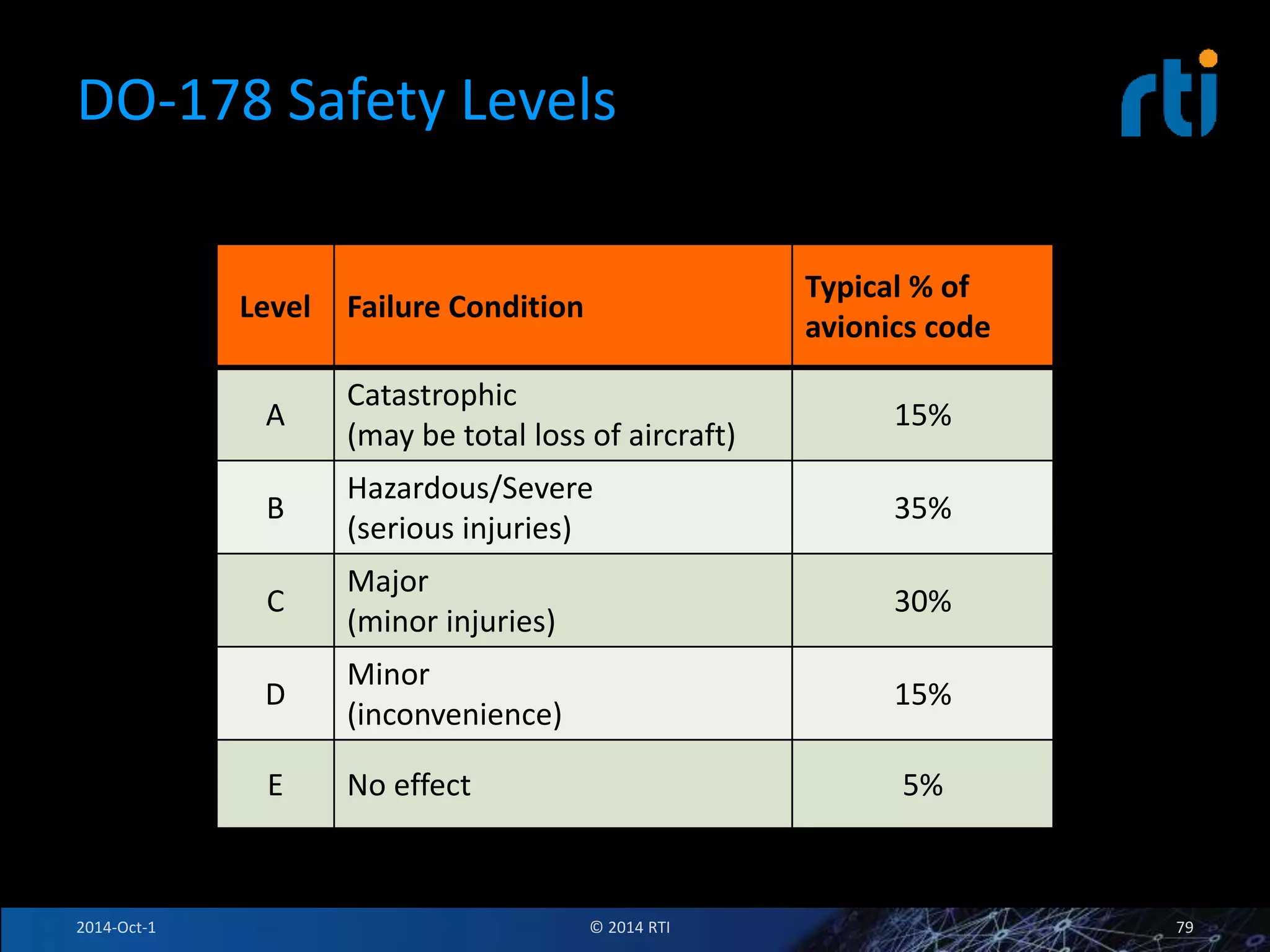
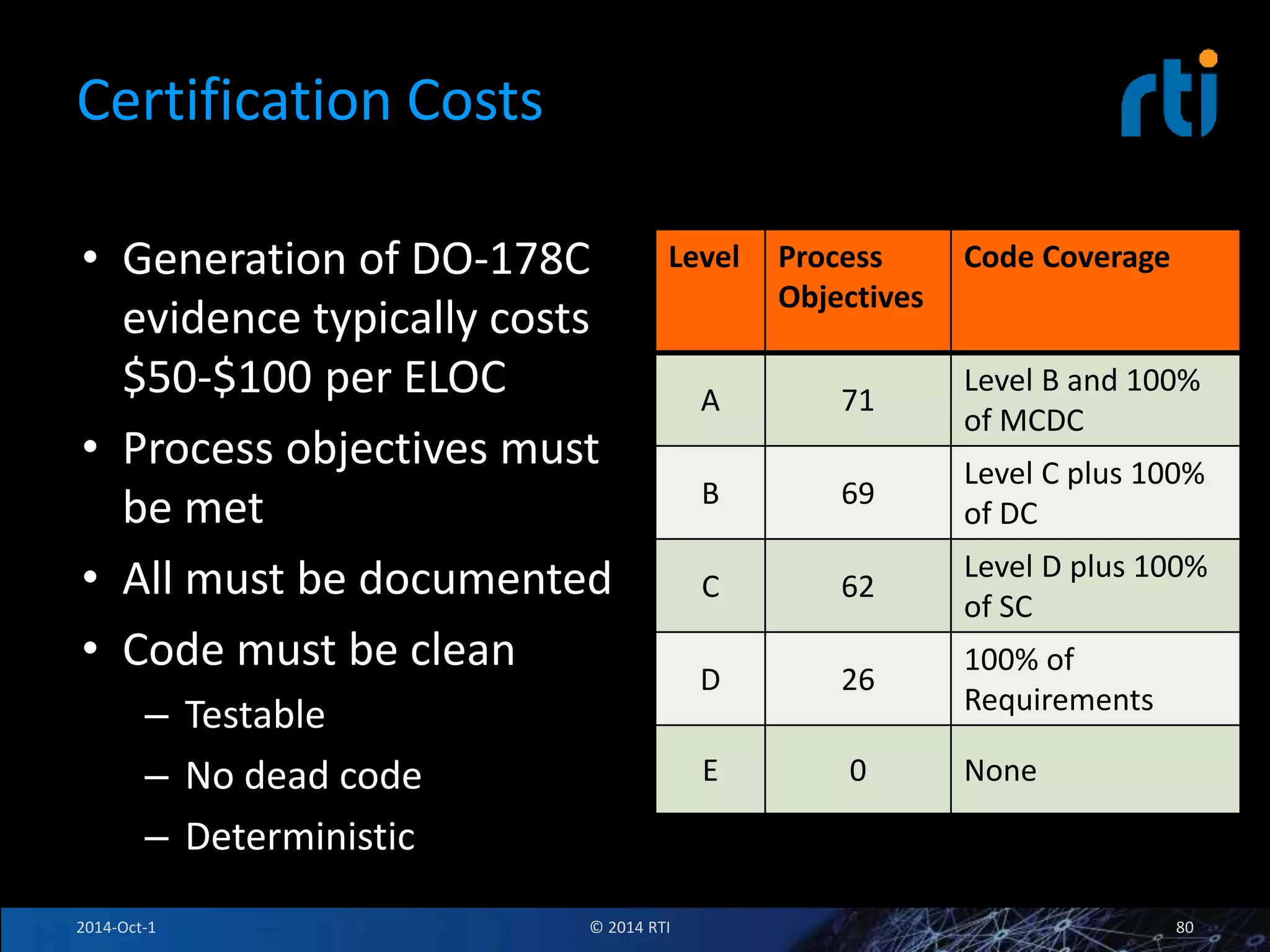
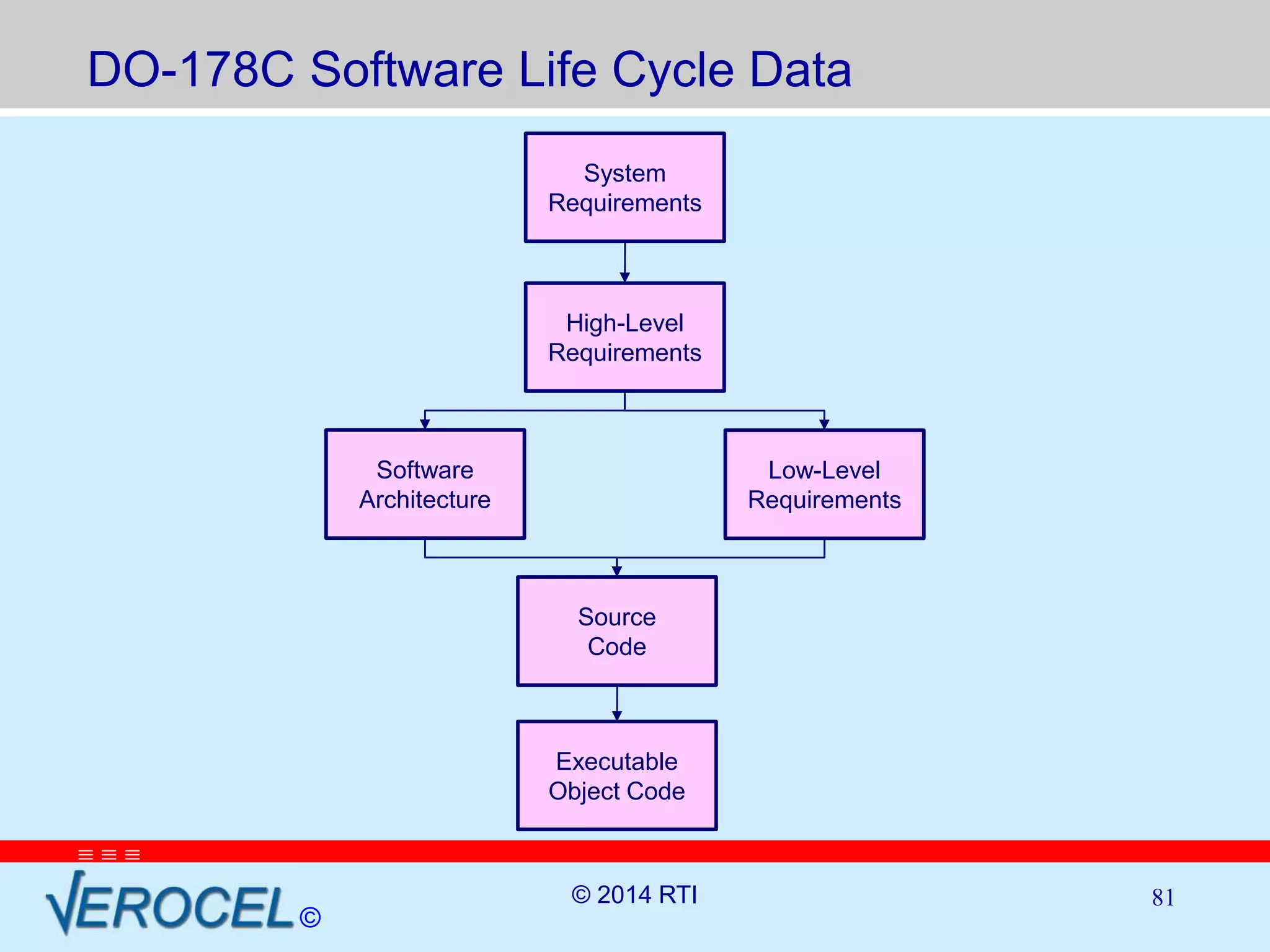
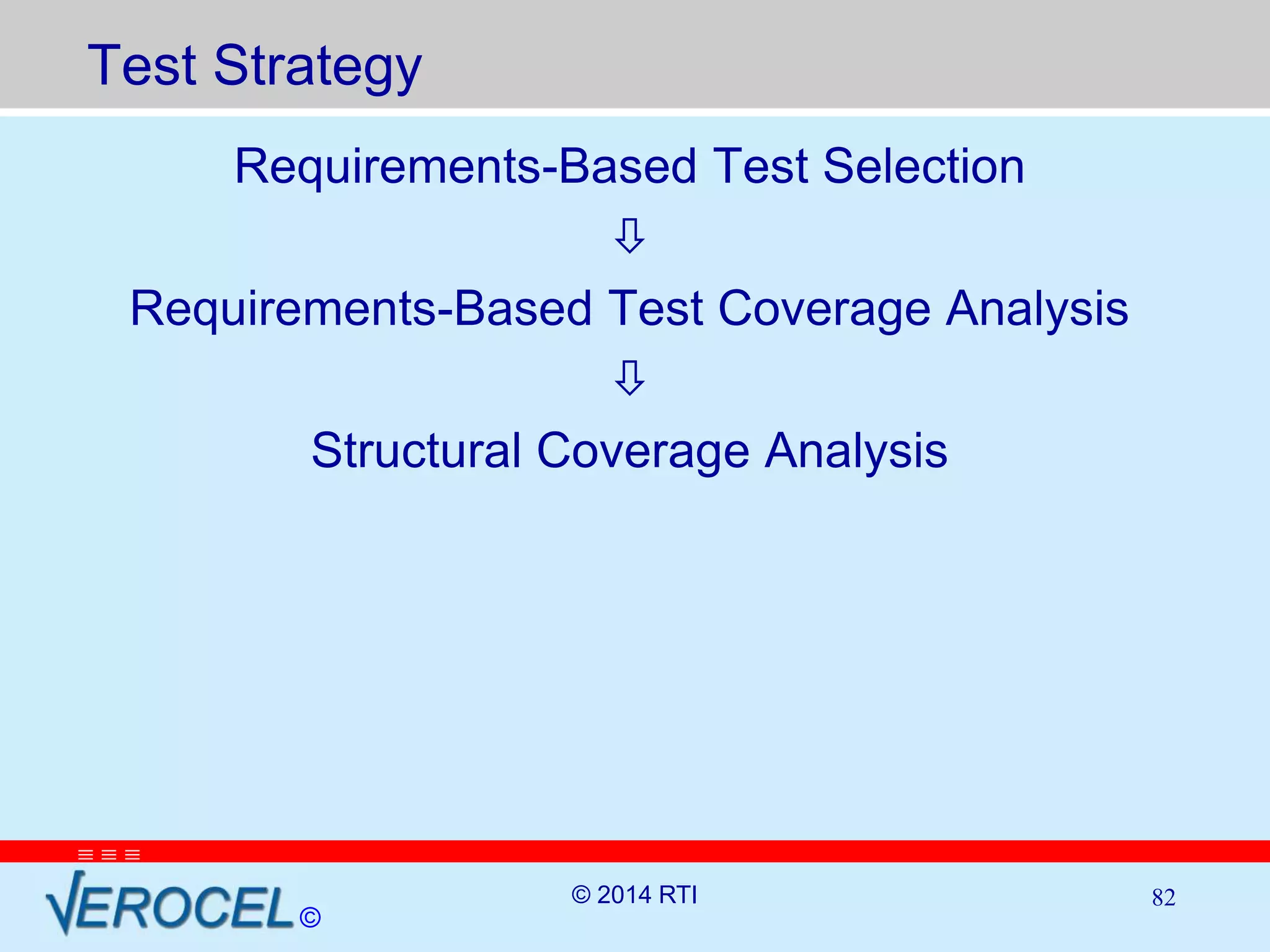
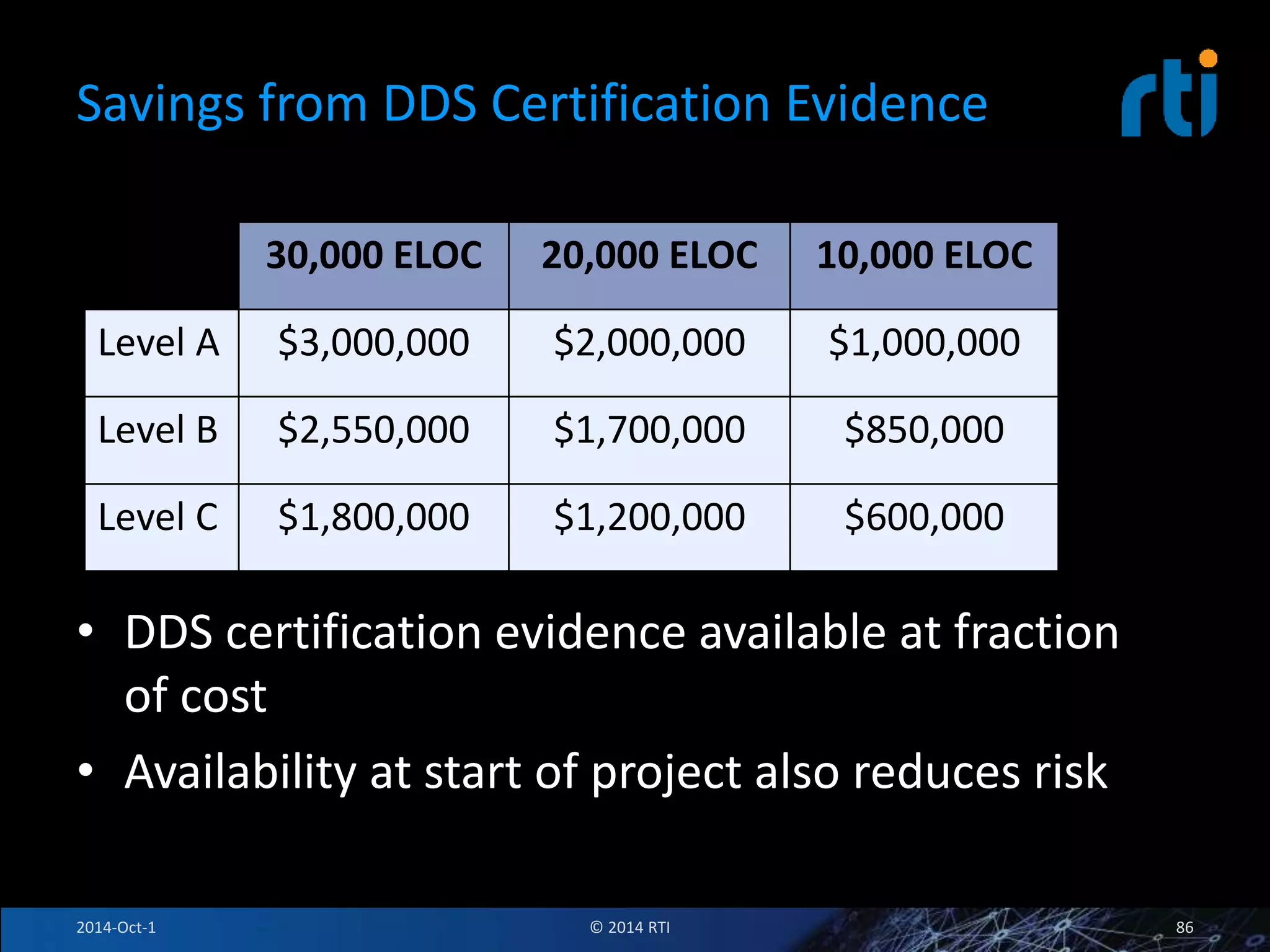
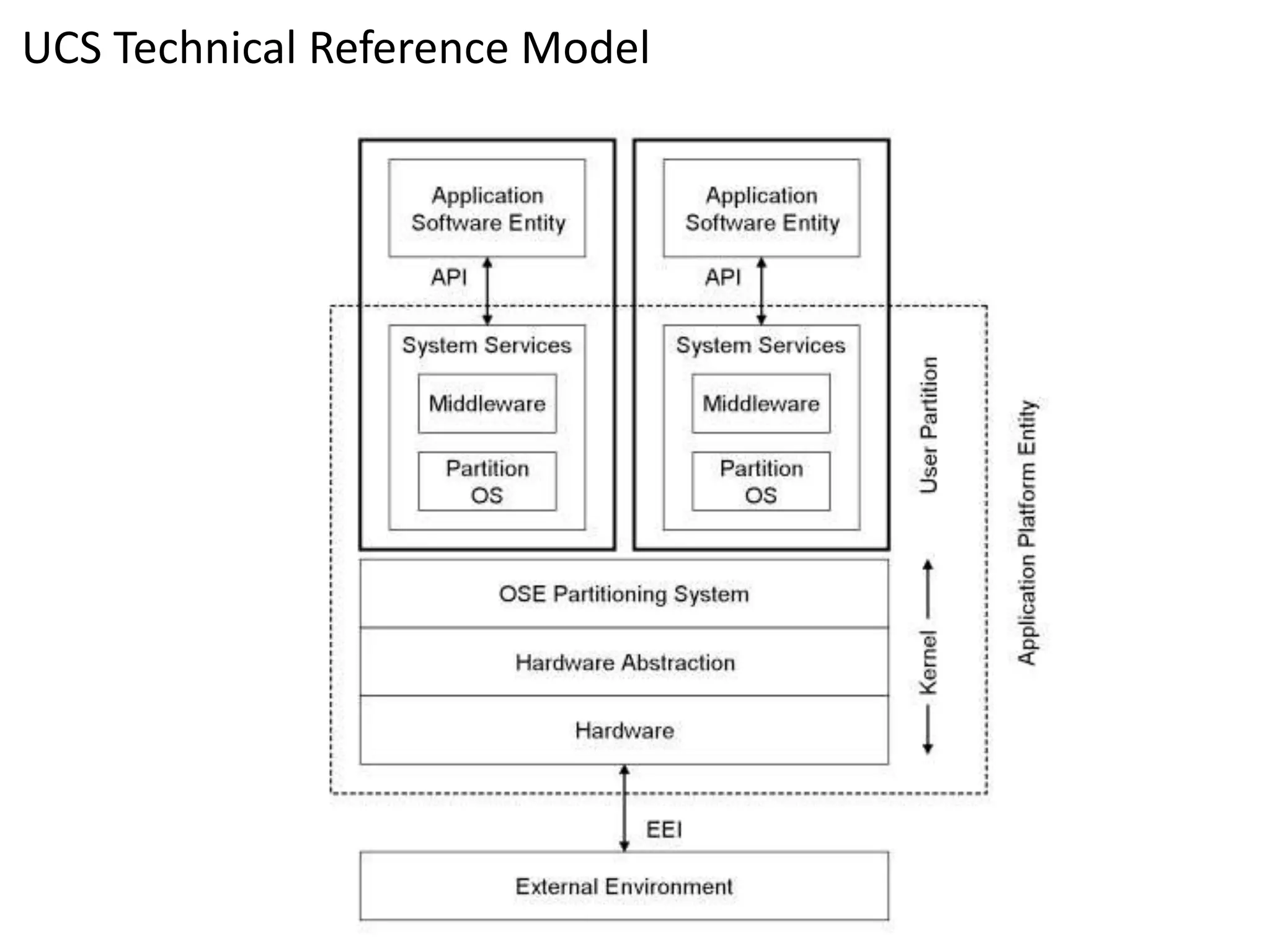
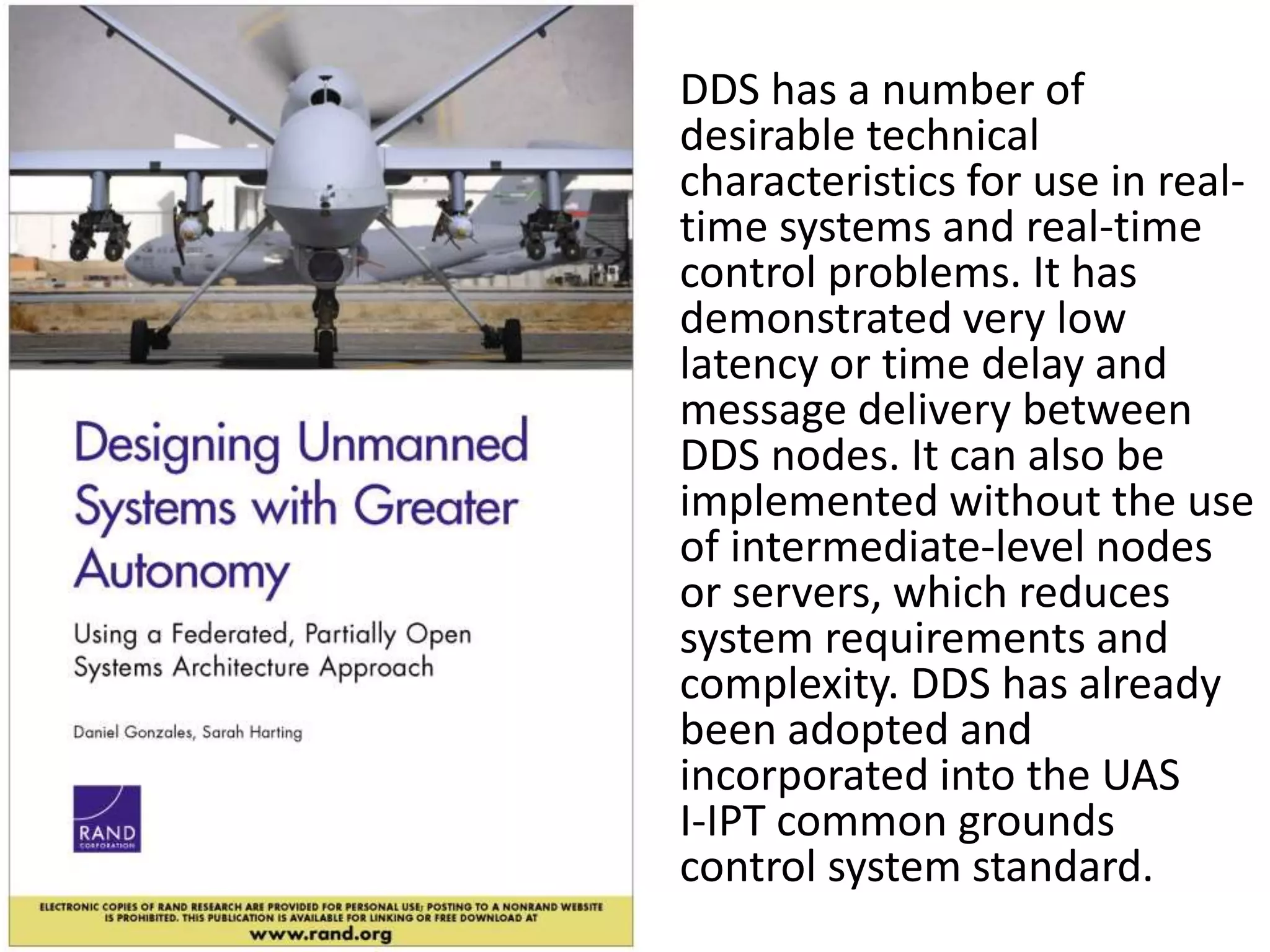
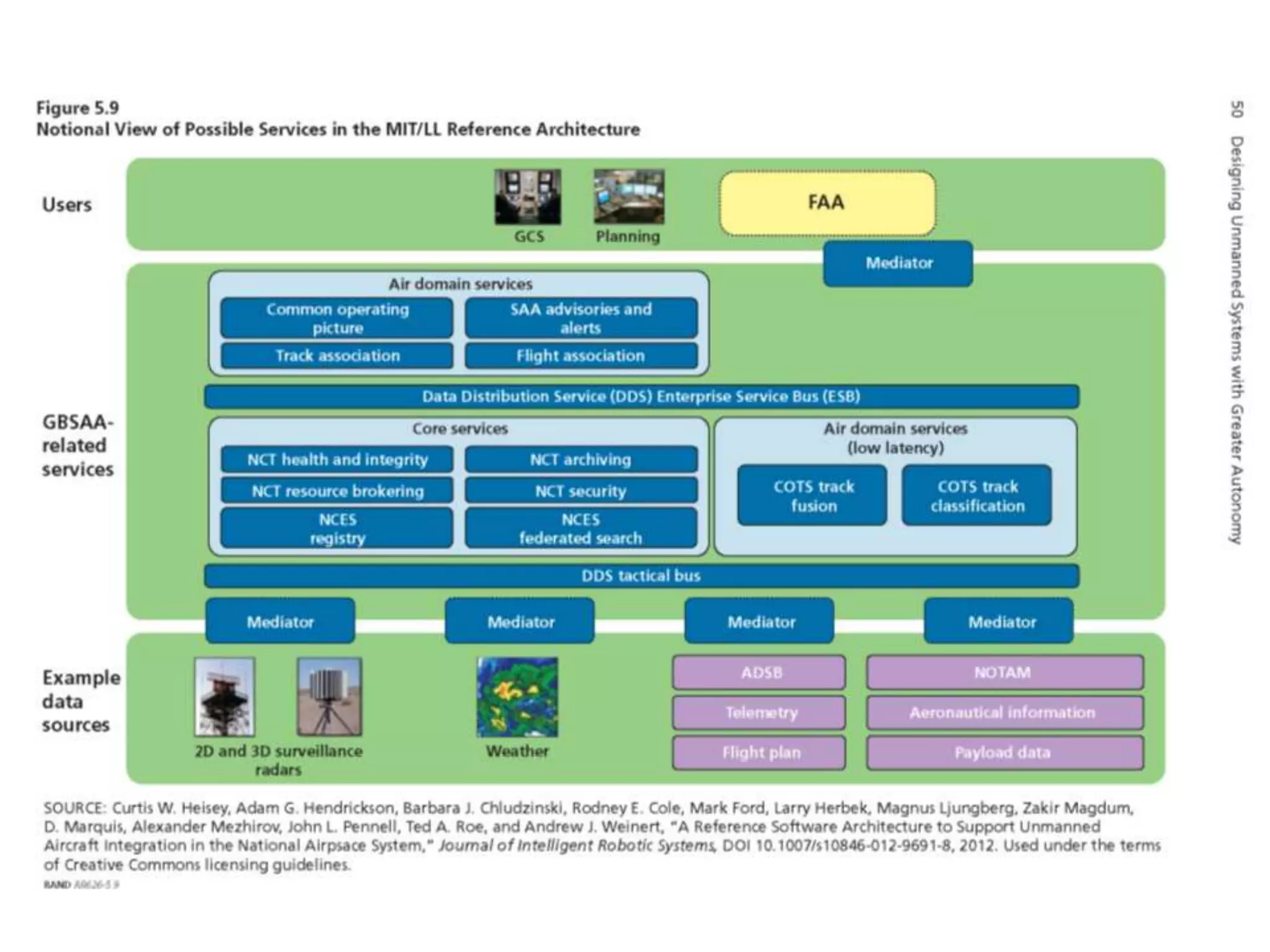
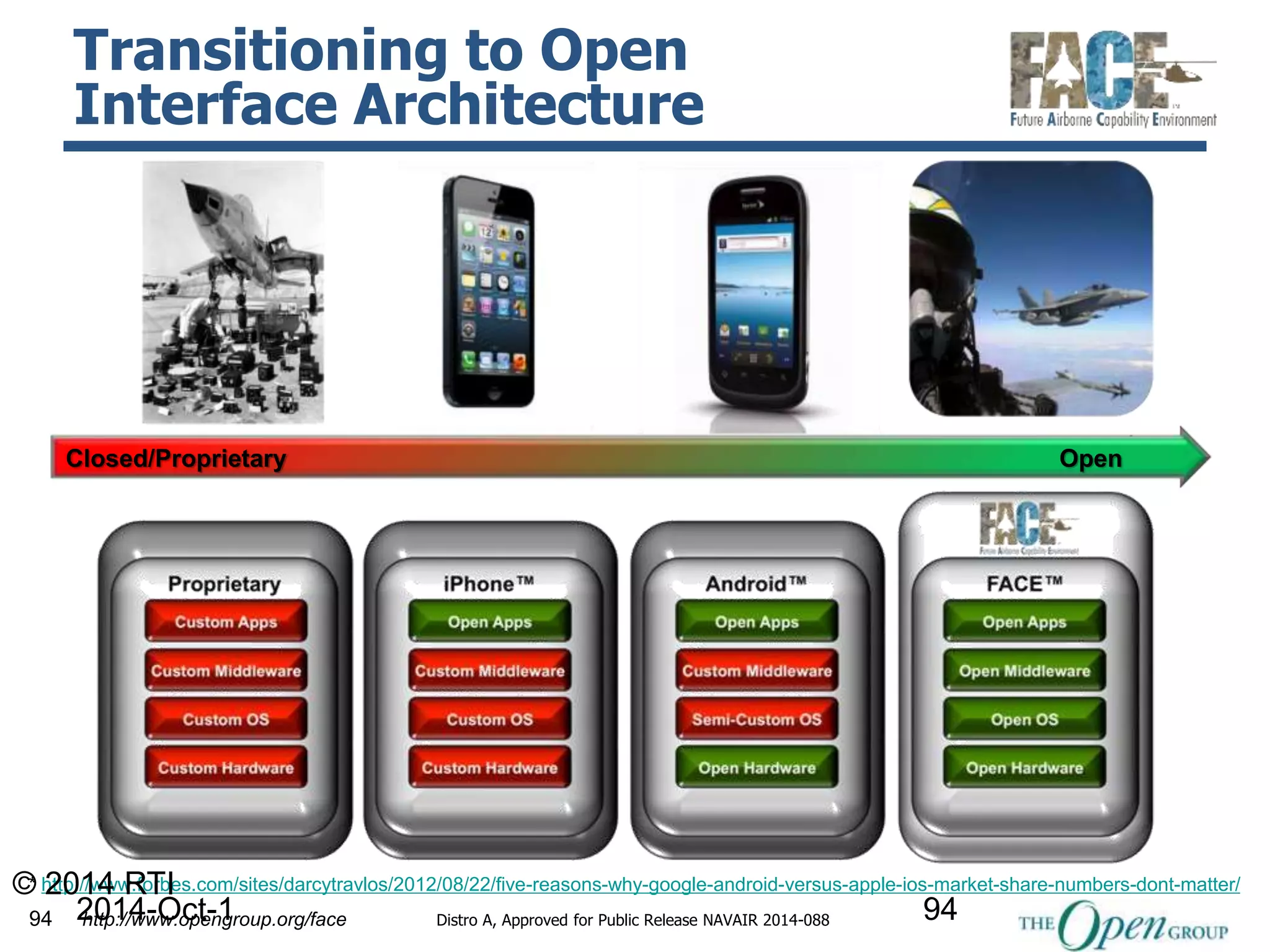
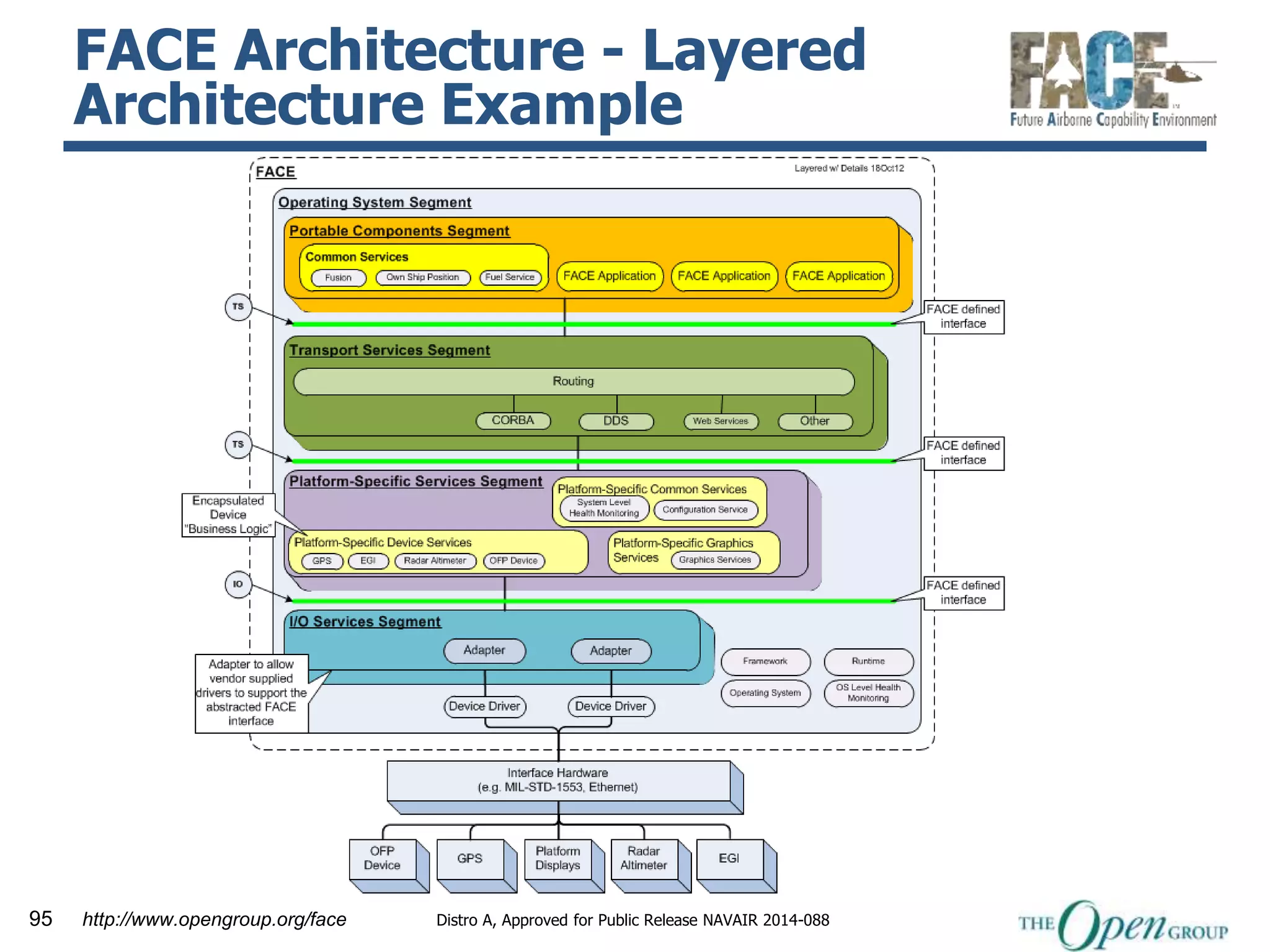
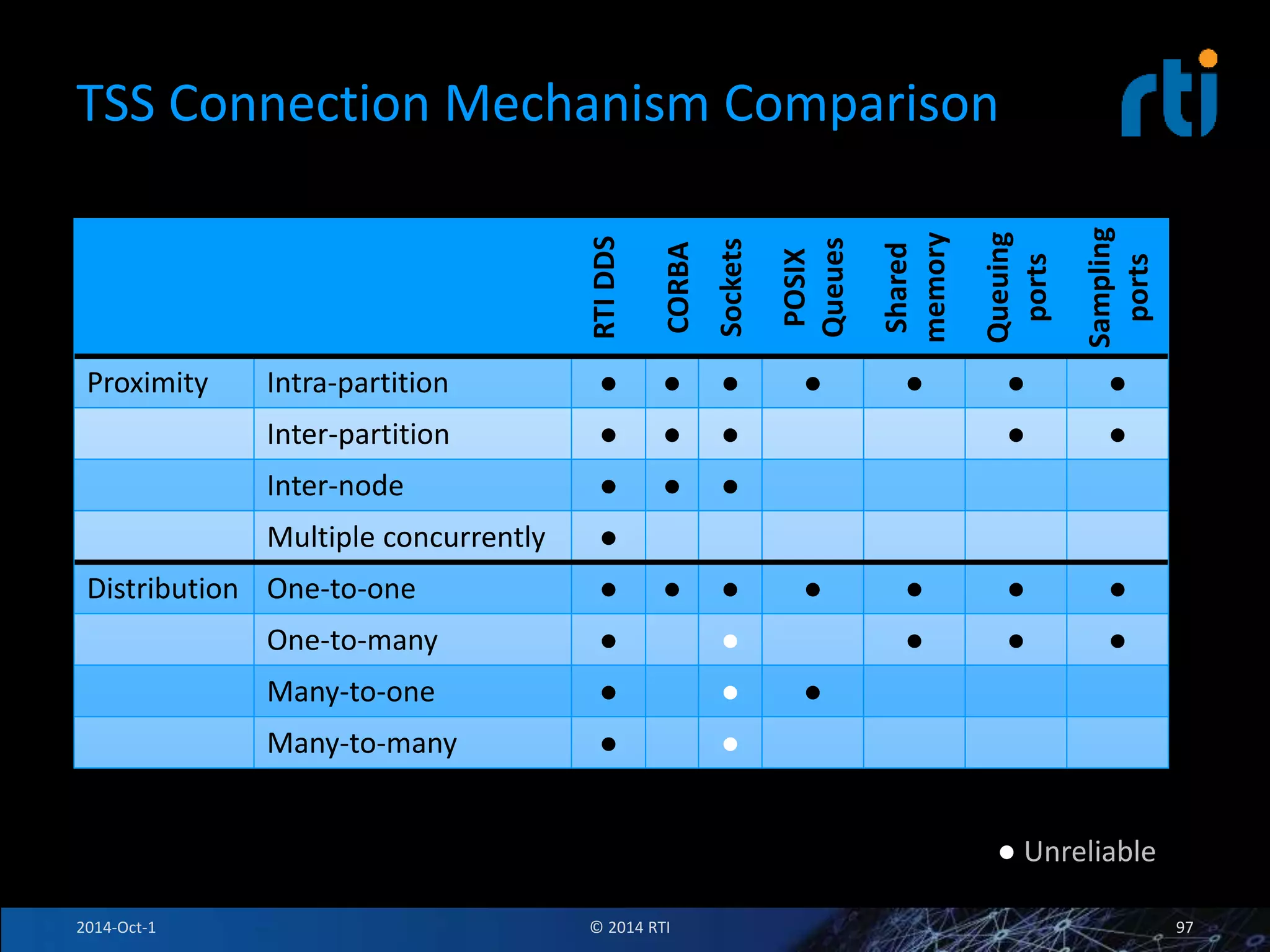
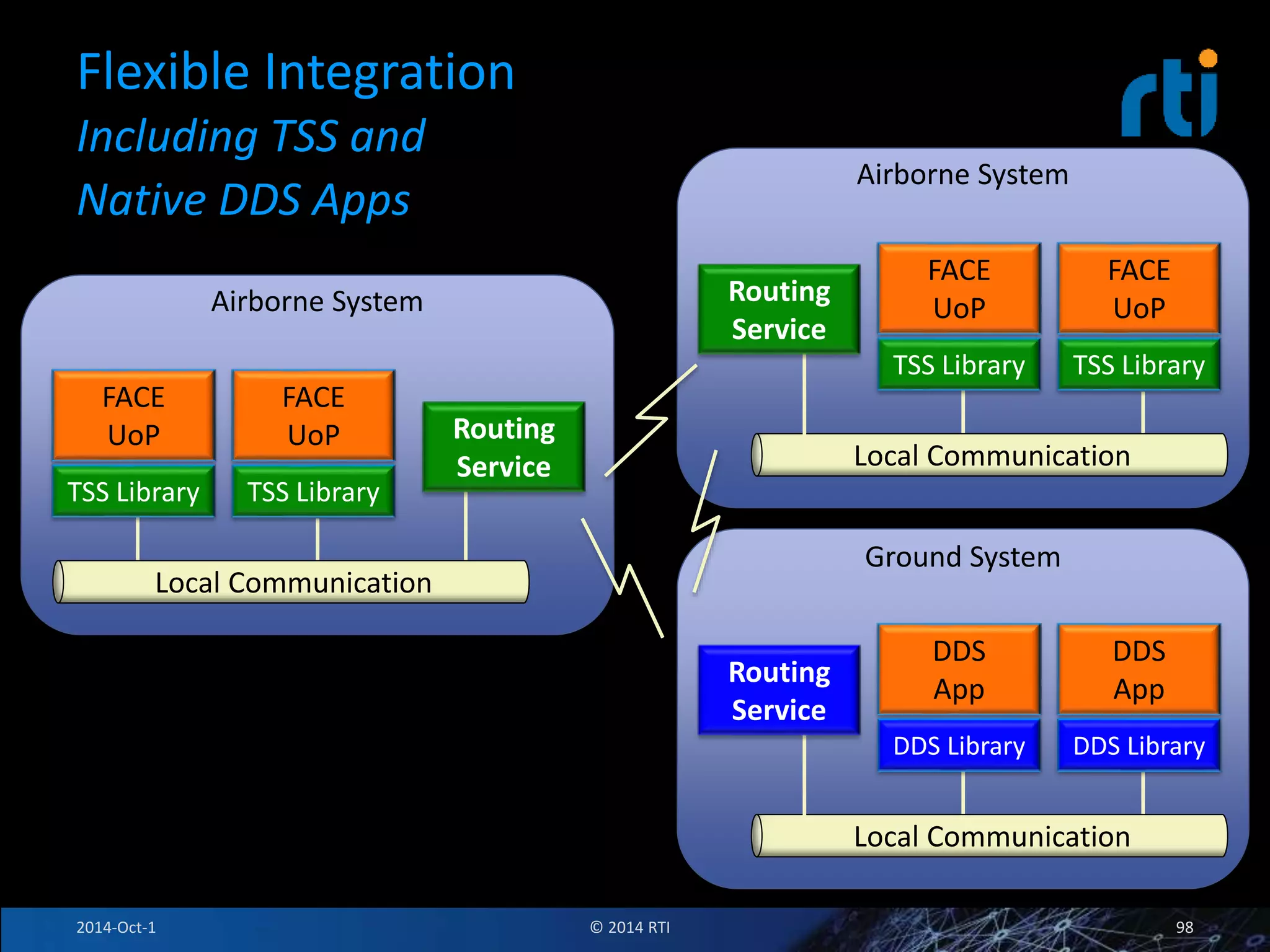
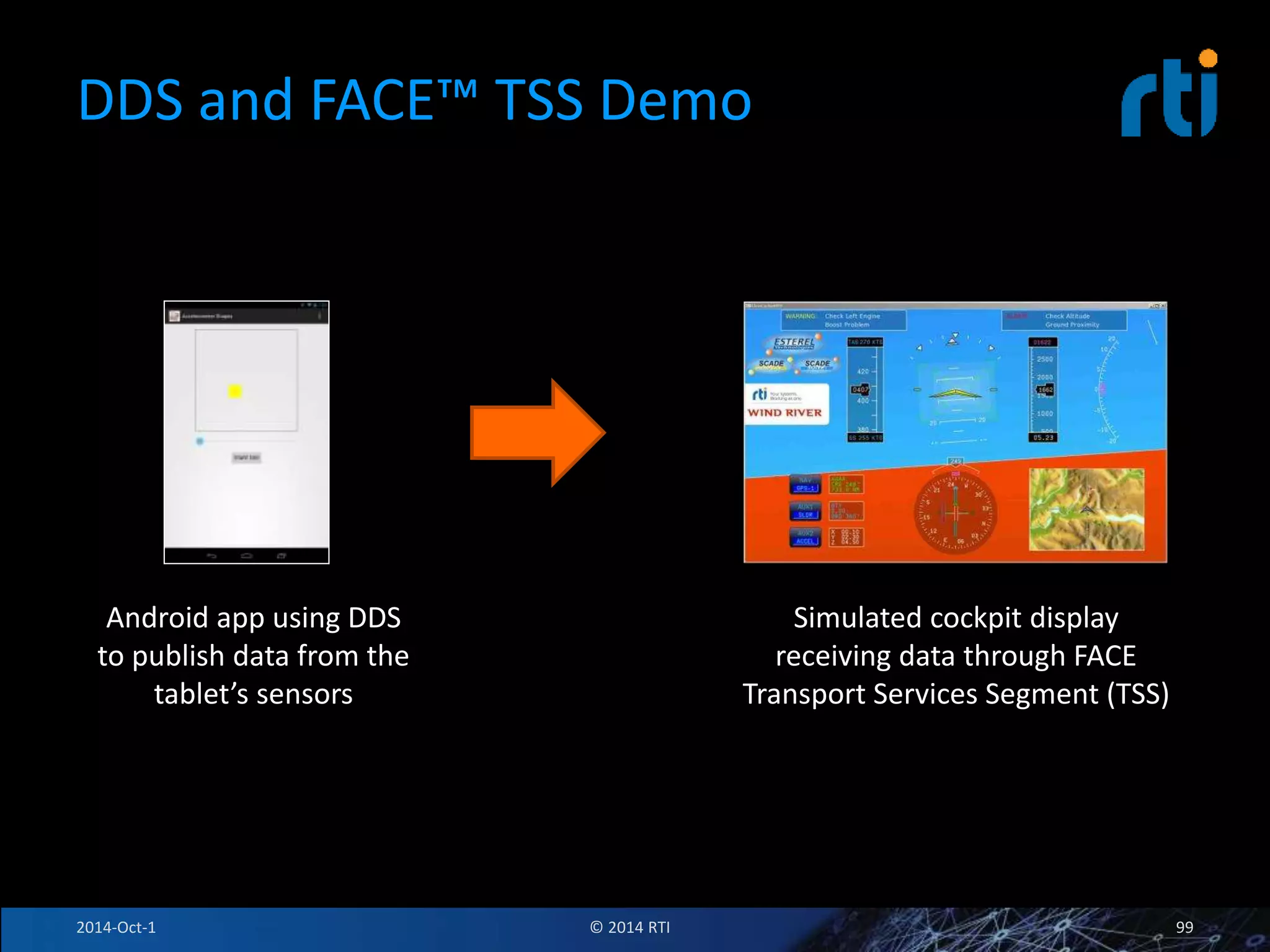
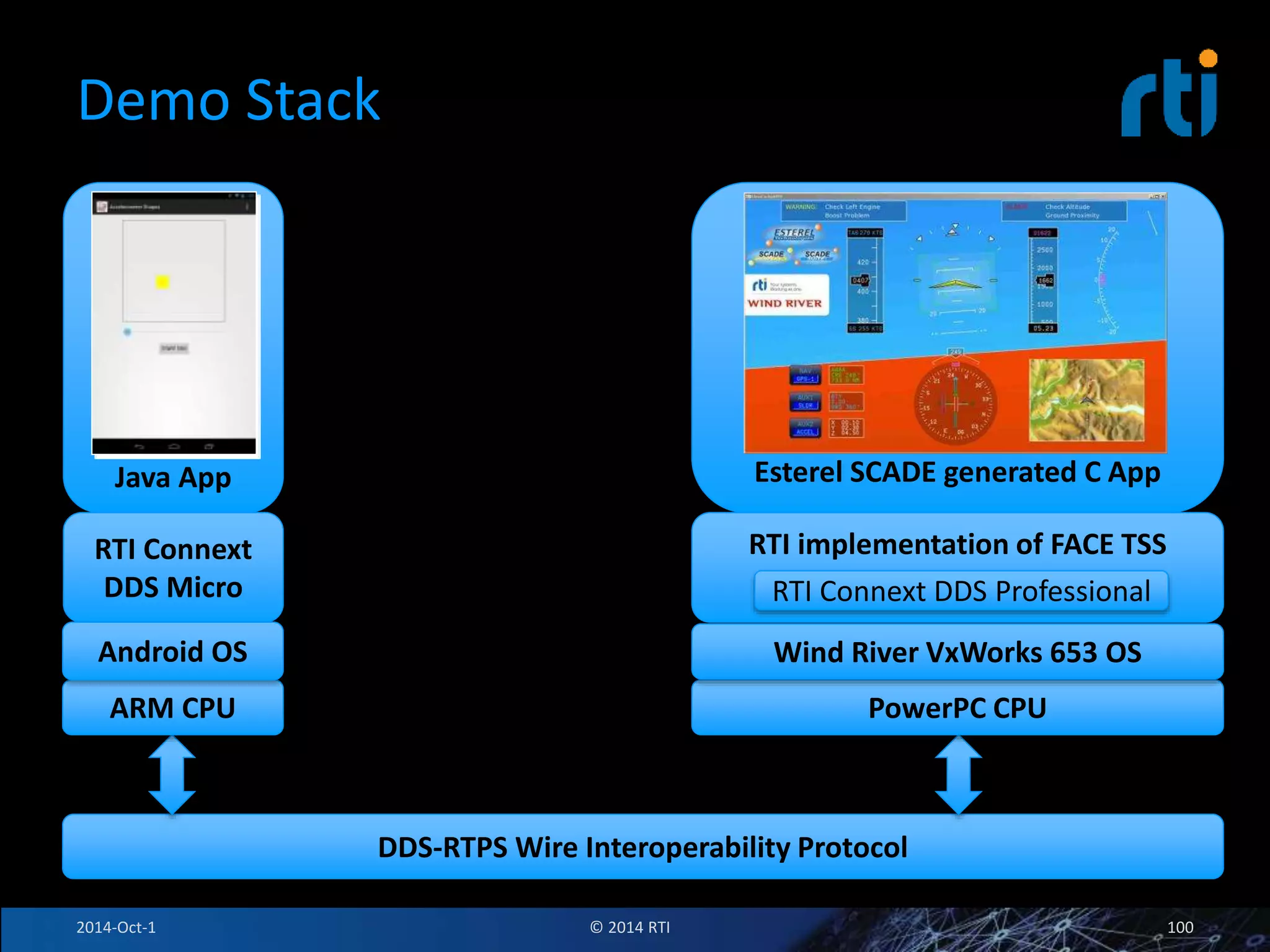
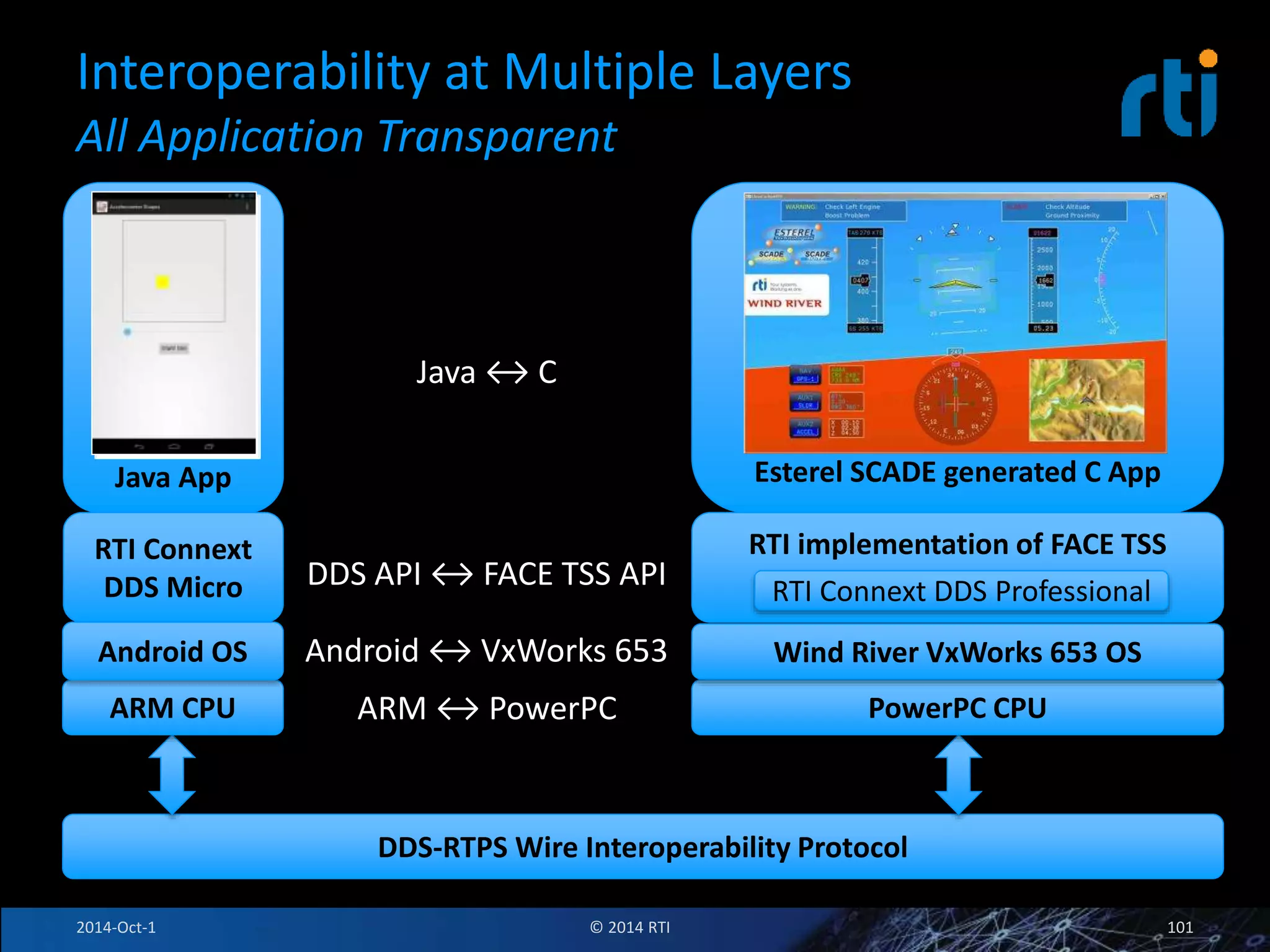
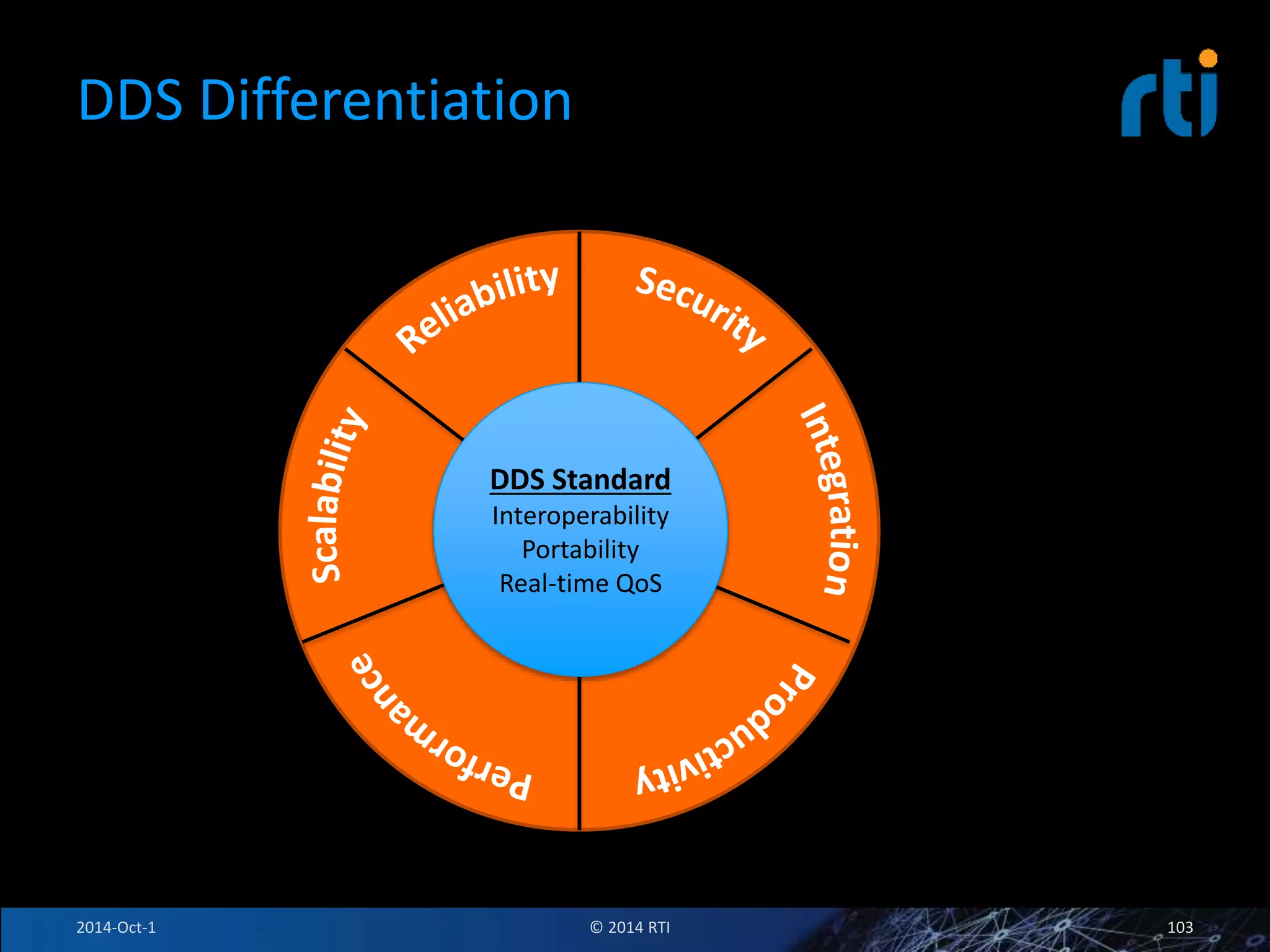
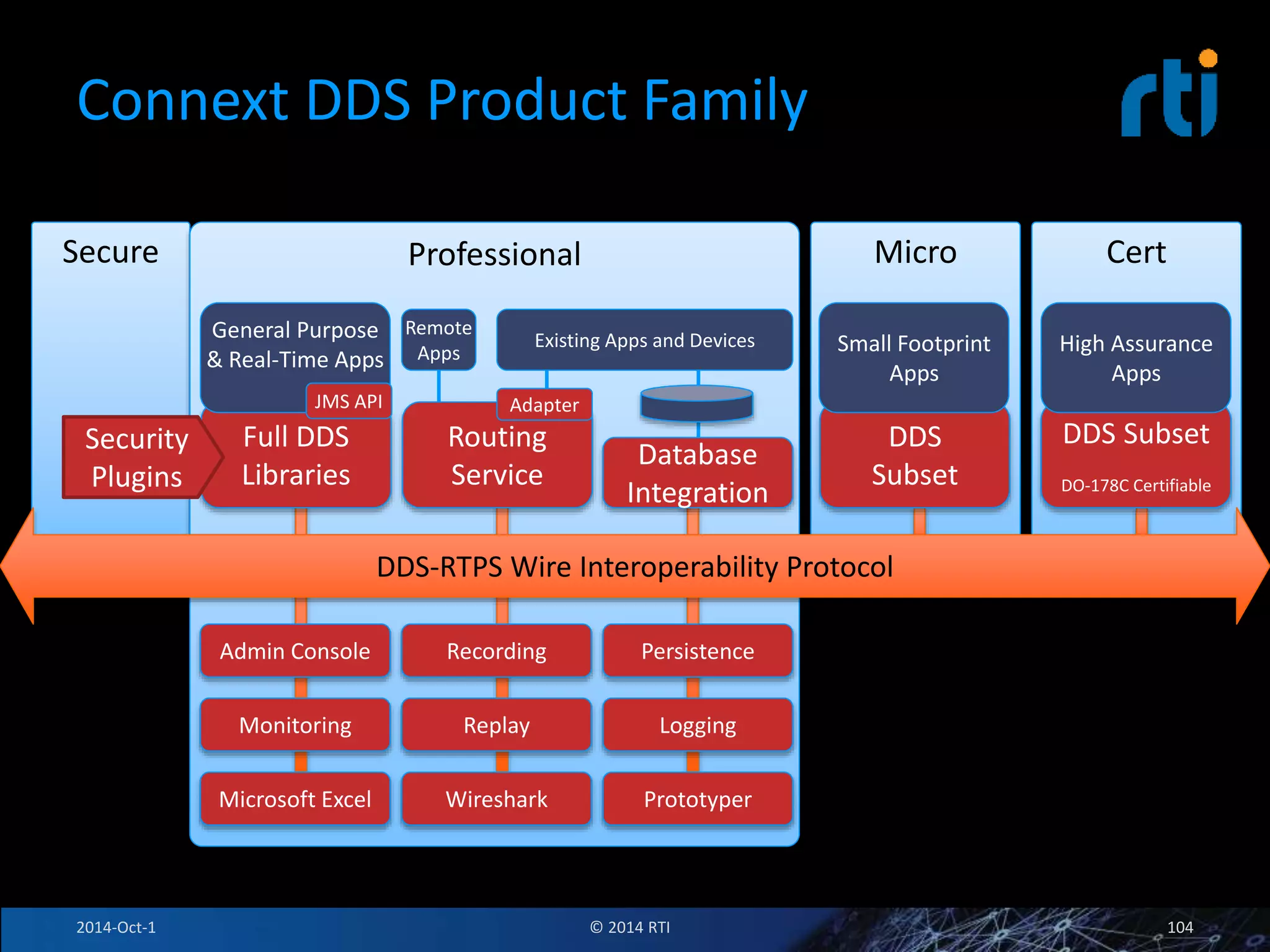
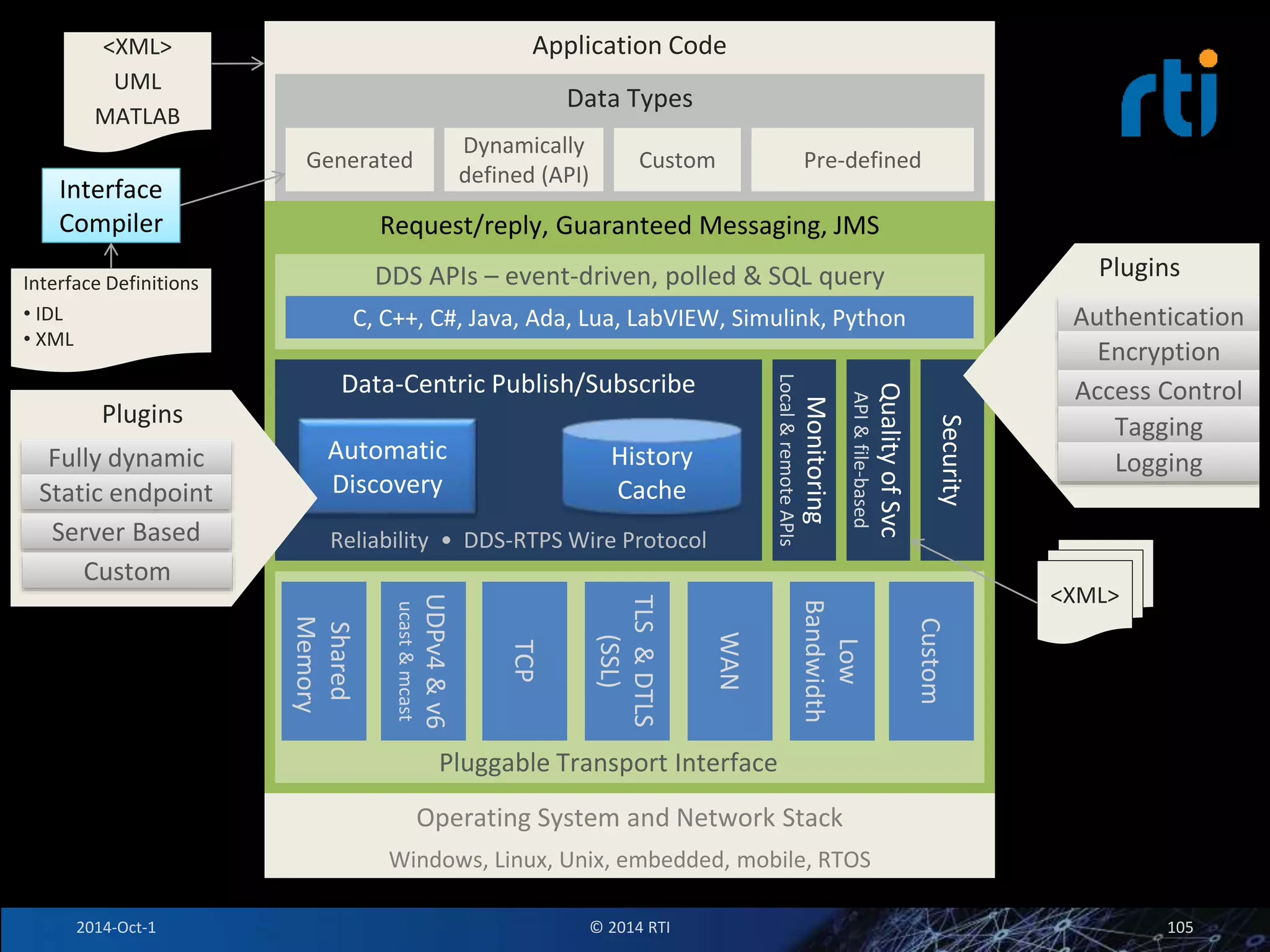
The document discusses RTI and its Data Distribution Service (DDS) middleware. DDS provides publish-subscribe communication that is decentralized, scalable, and supports real-time and mission-critical systems. It addresses challenges with traditional approaches that are point-to-point and have single points of failure. DDS is used widely in industries such as defense, automotive, and medical. The document also covers open architecture requirements and how DDS supports security features to address cyber threats.