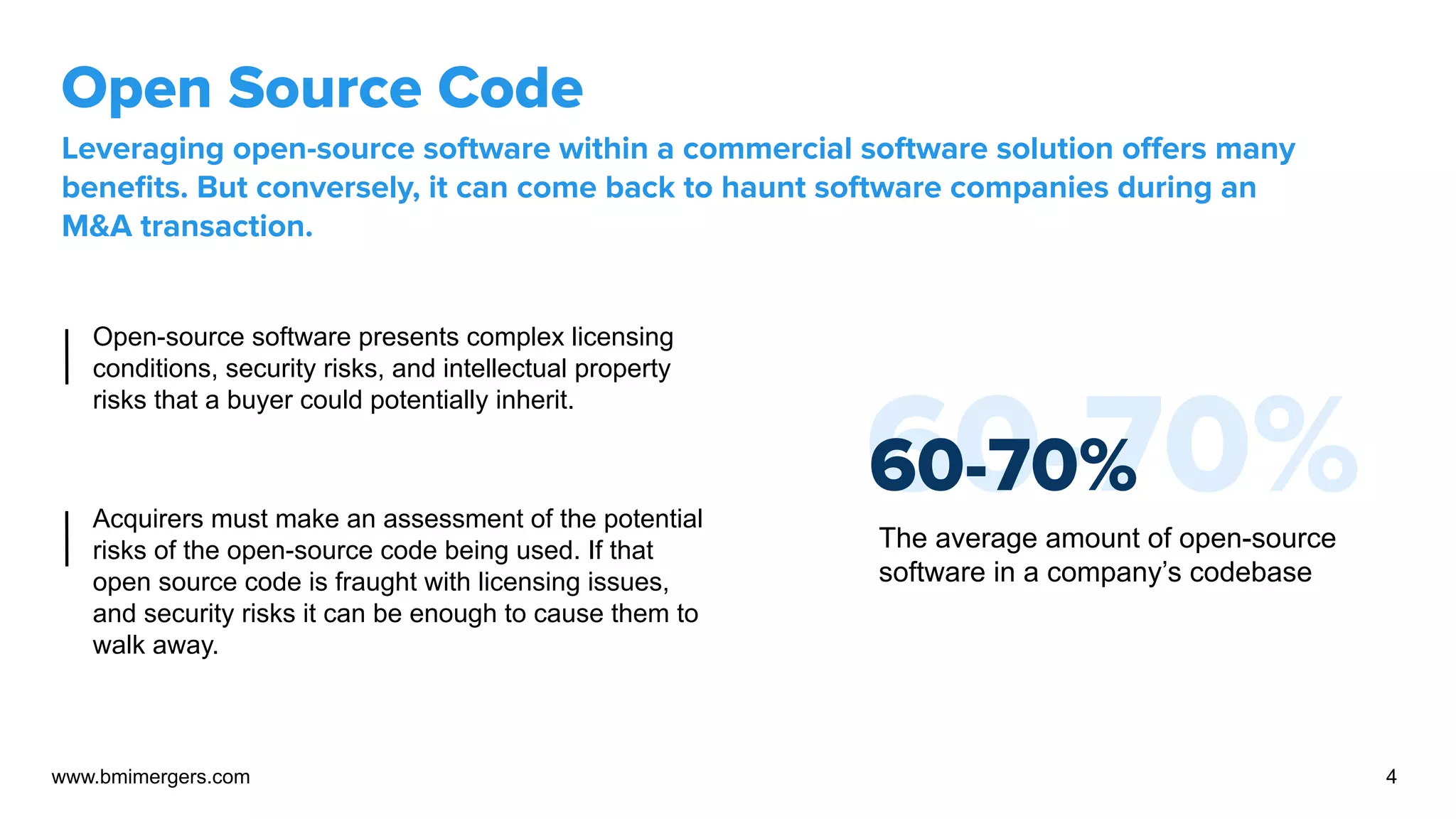
The document discusses the critical importance of assessing software code and architecture during the mergers and acquisitions (M&A) process in the technology sector. It emphasizes the potential risks associated with poorly written source code, technical debt, and open-source software that can affect the acquirer's decision. Additionally, it highlights the necessity of conducting thorough technical audits and penetration tests to uncover vulnerabilities and ensure proper preparation for a successful acquisition.