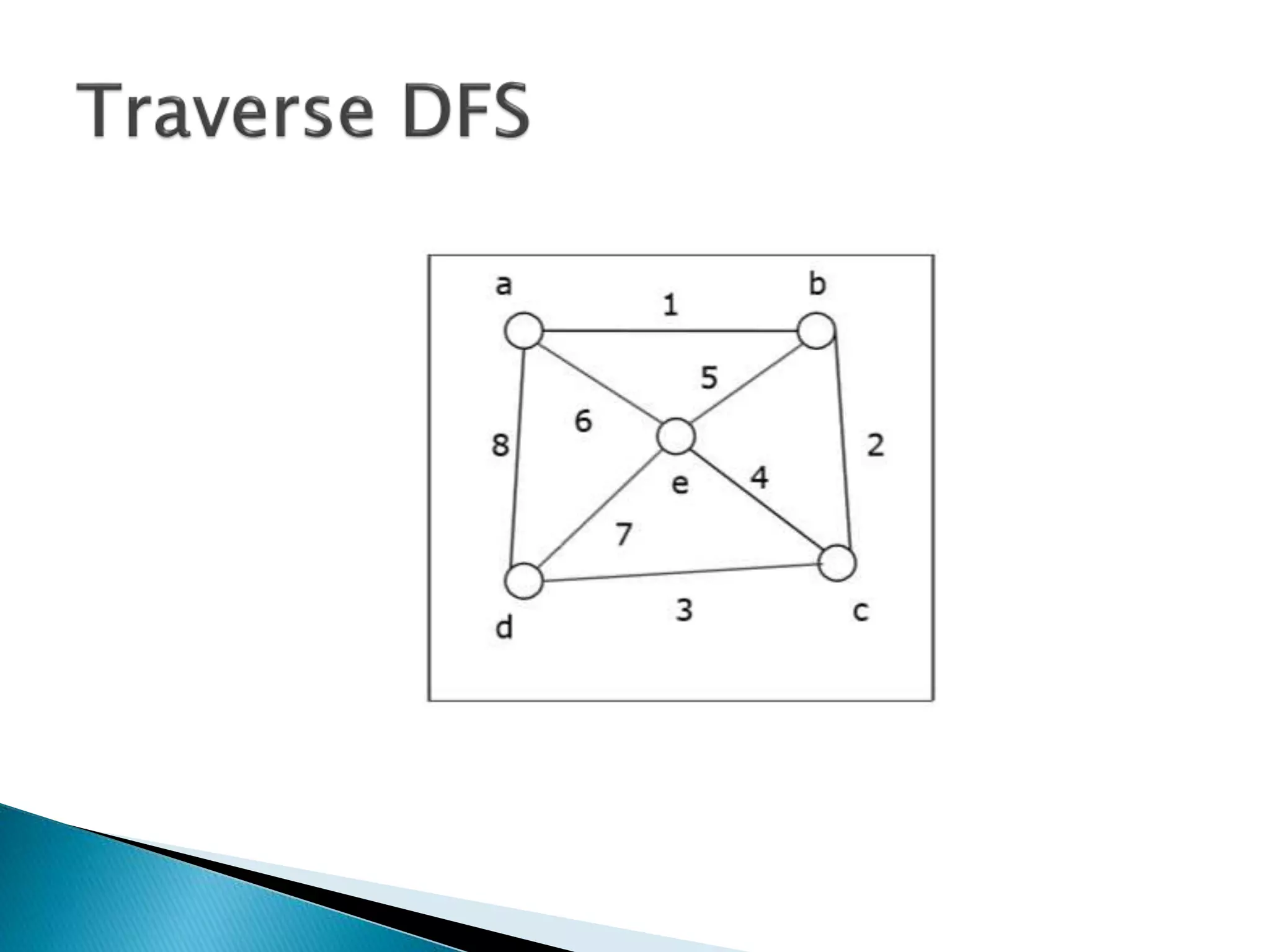
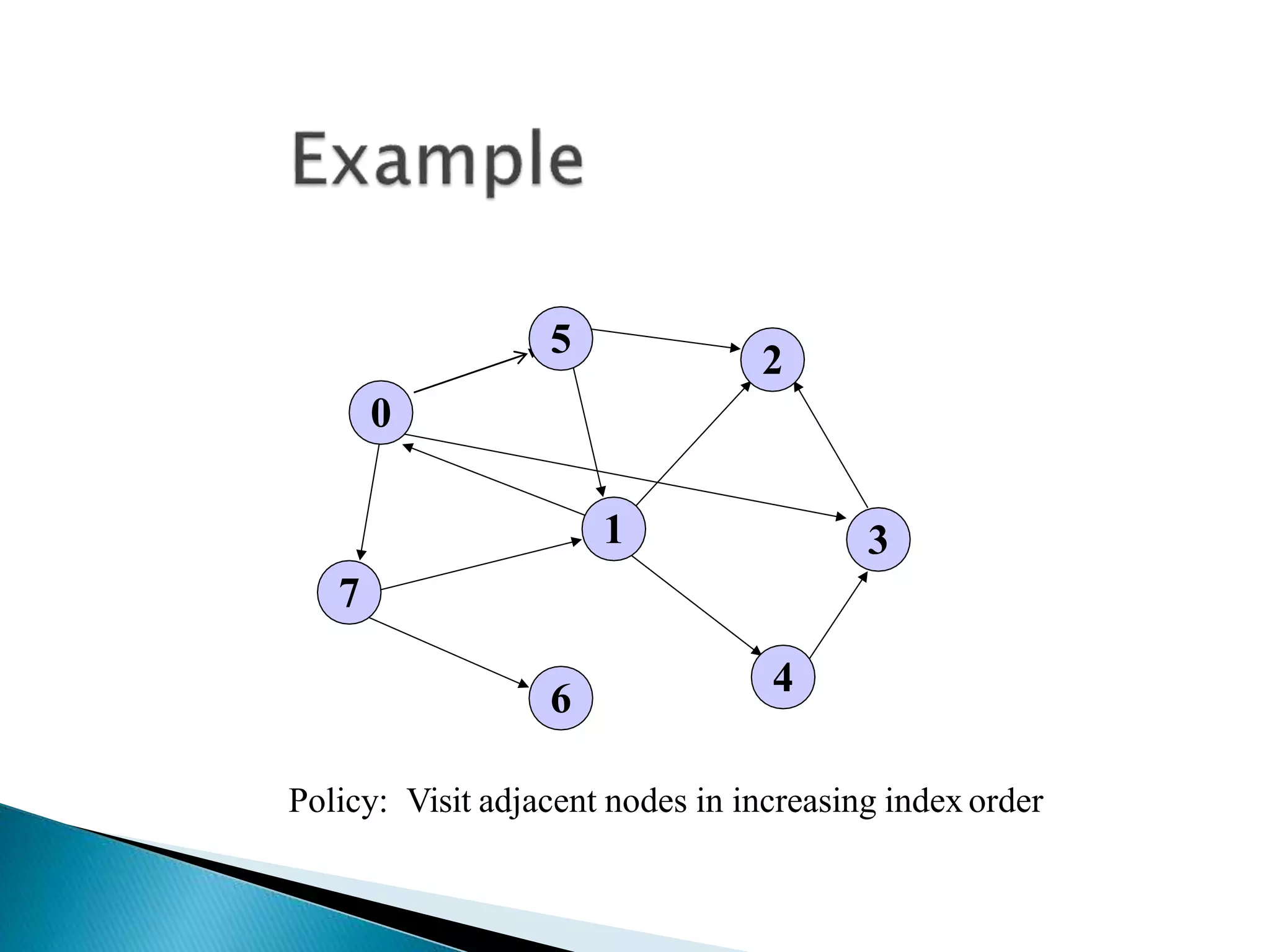
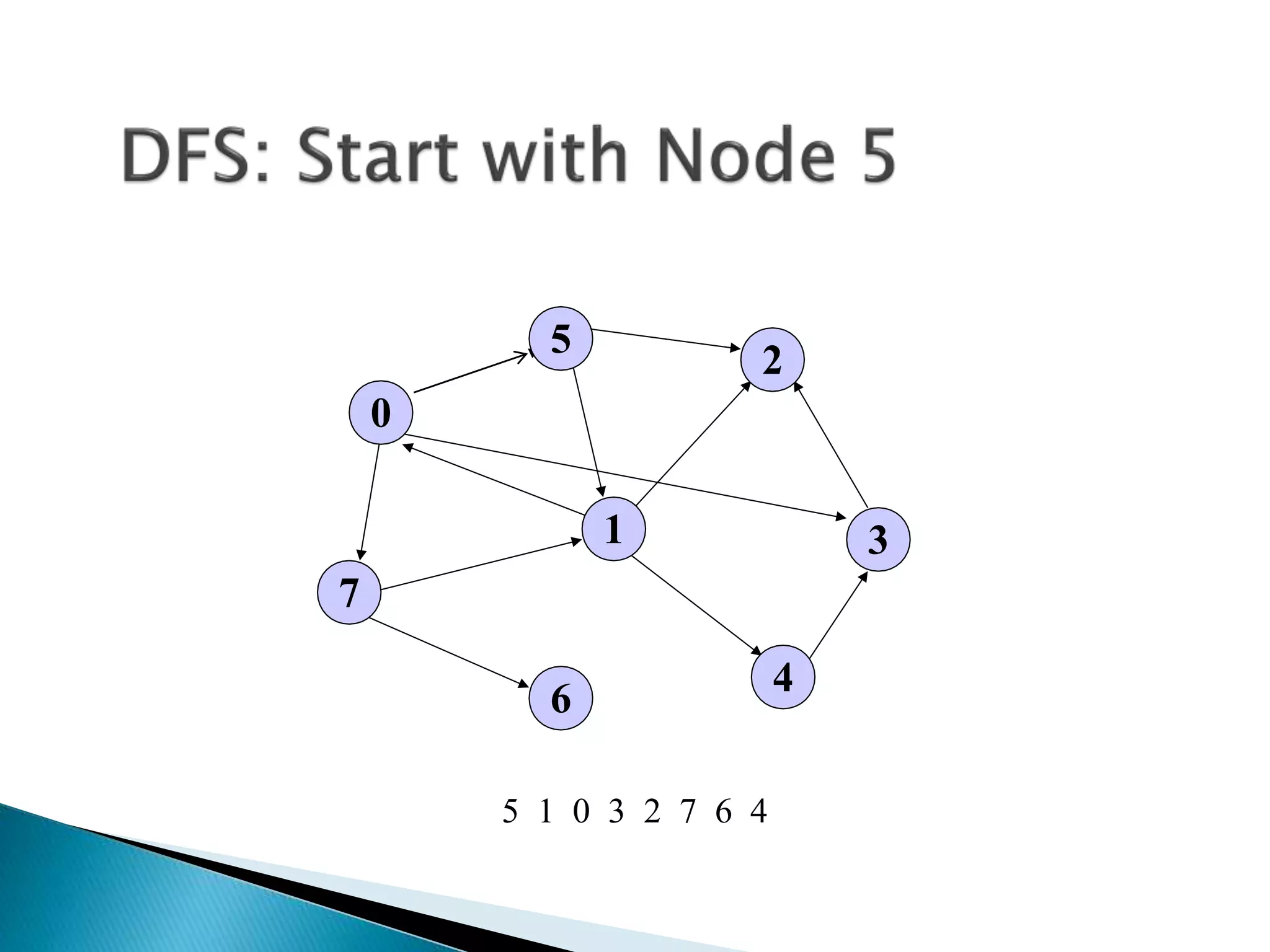
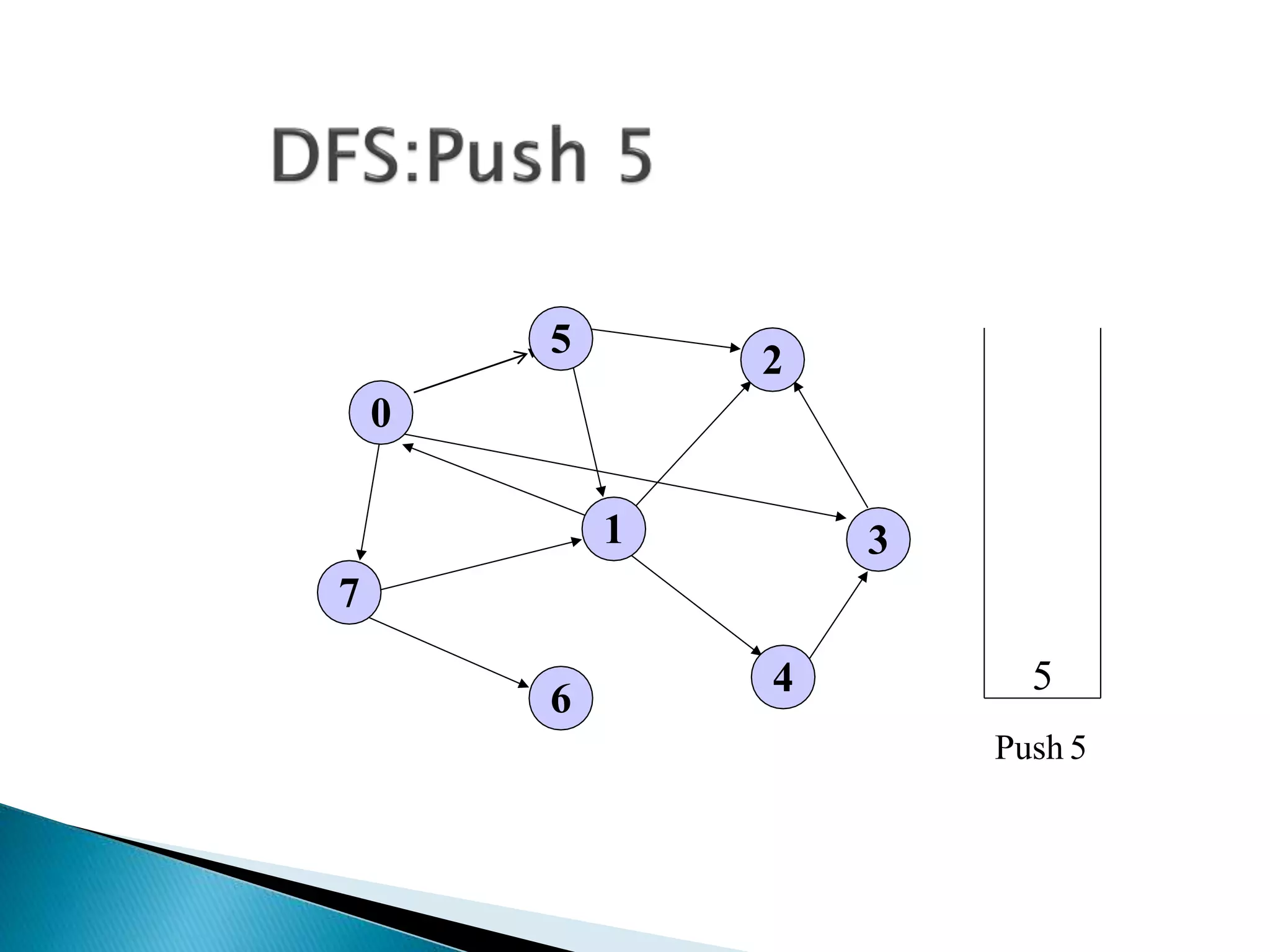
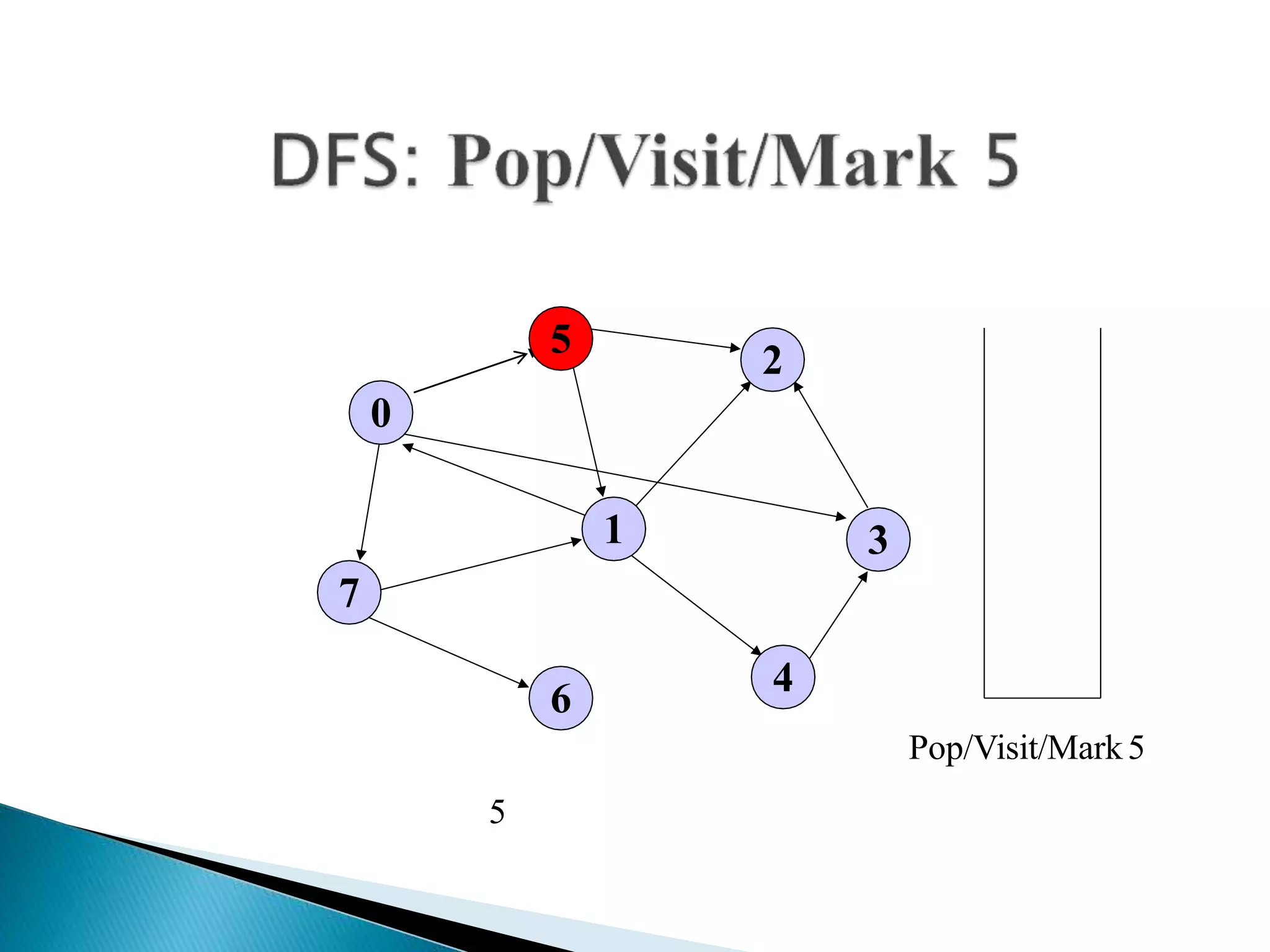
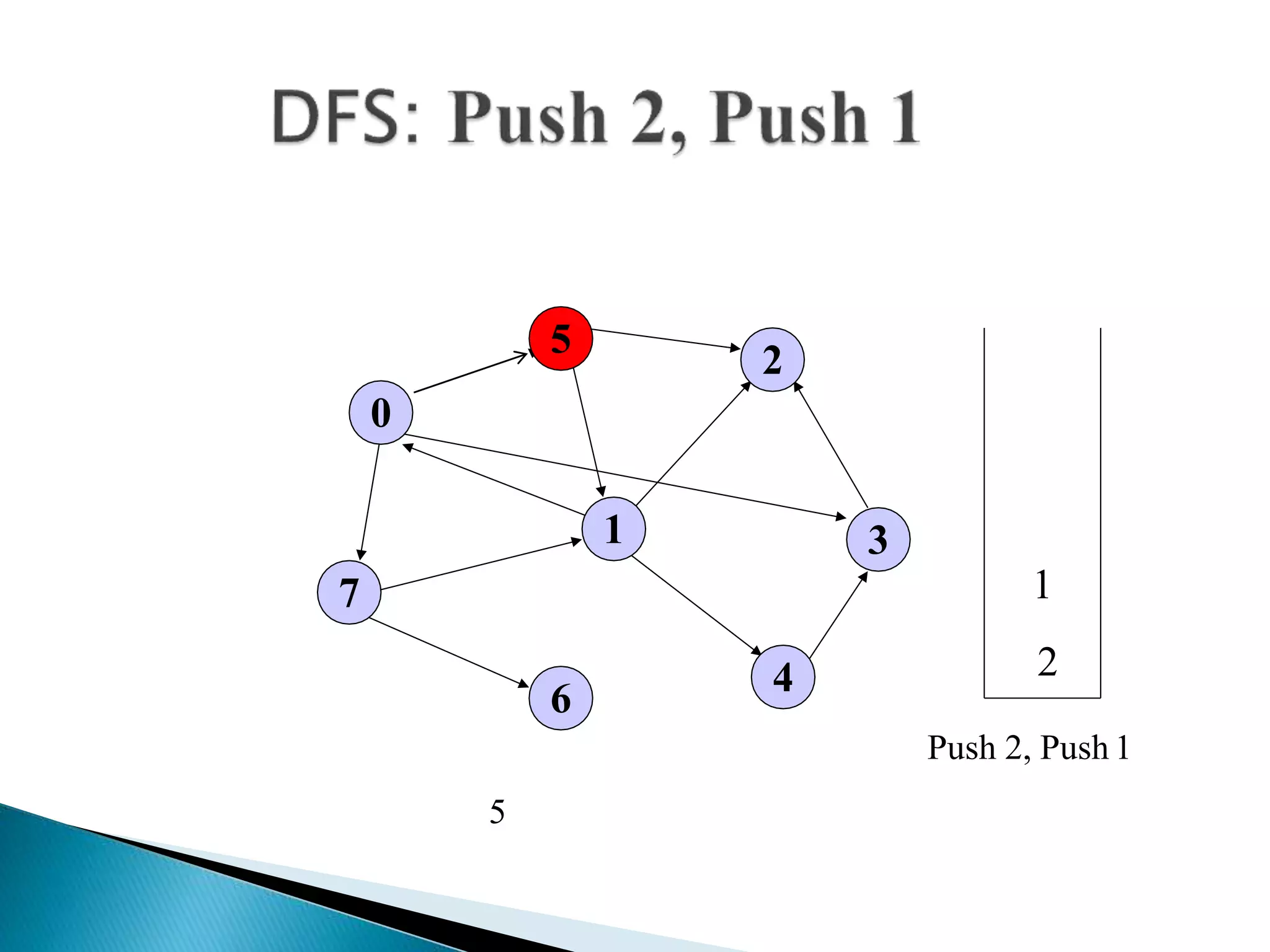
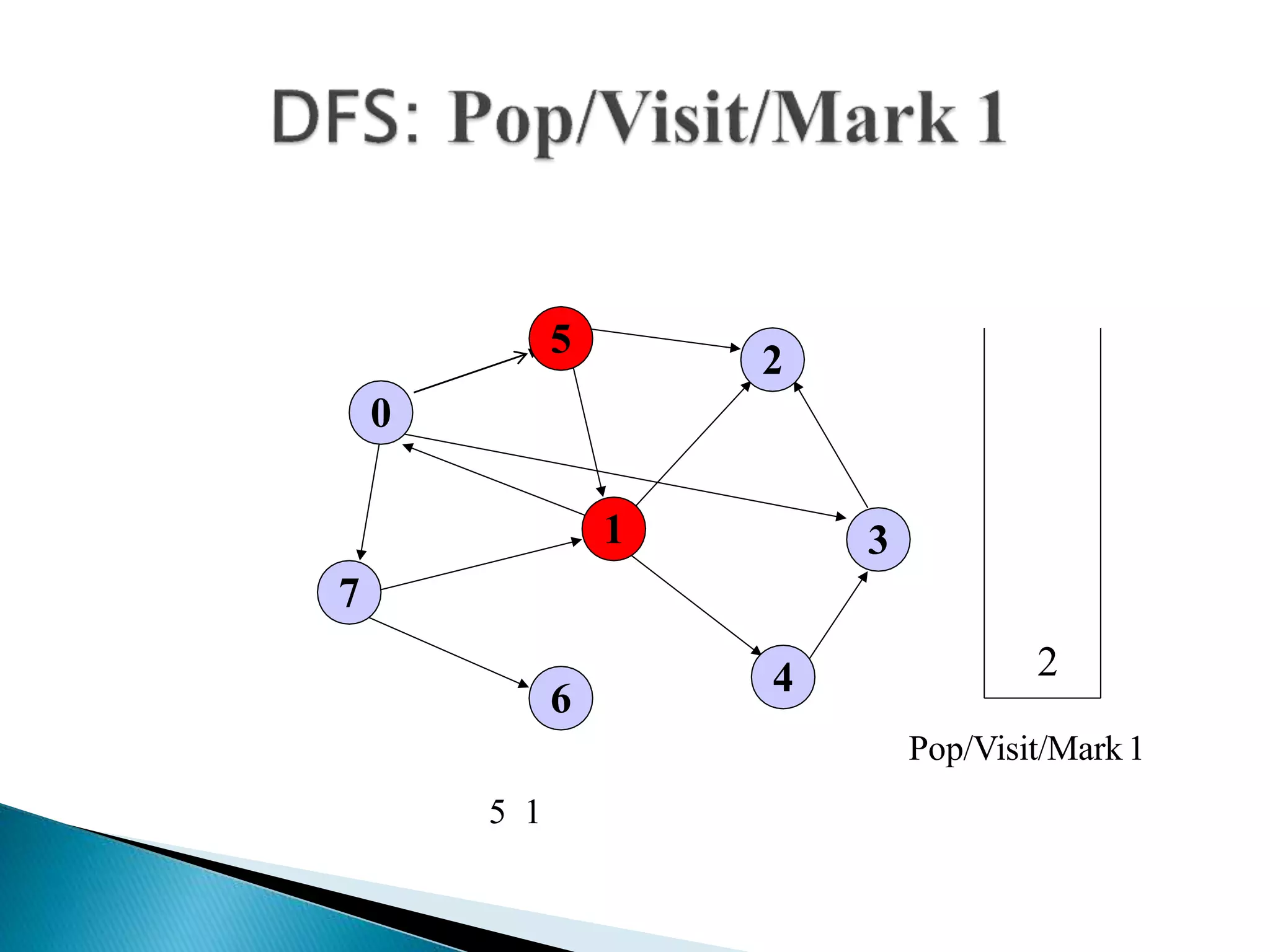
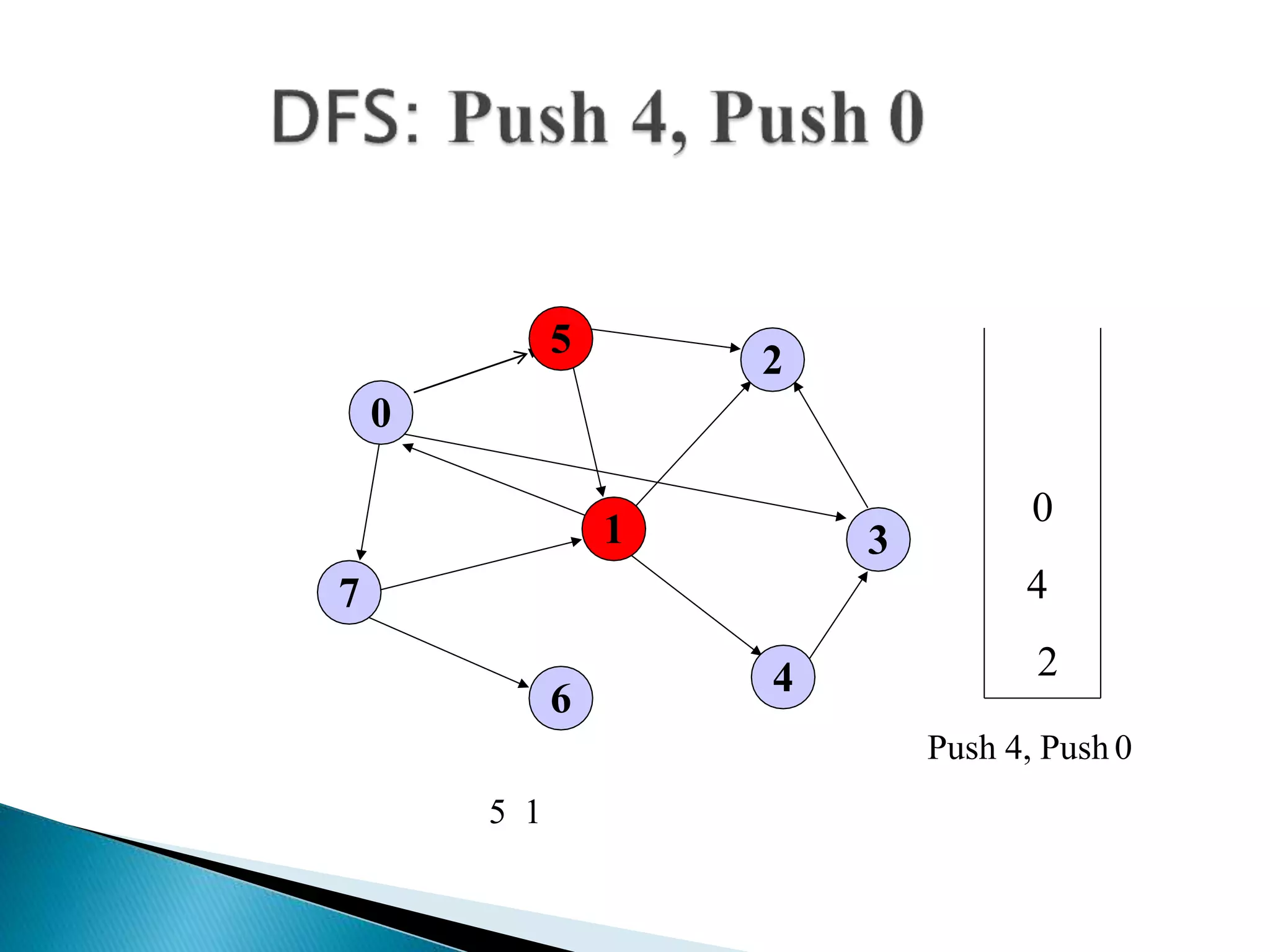
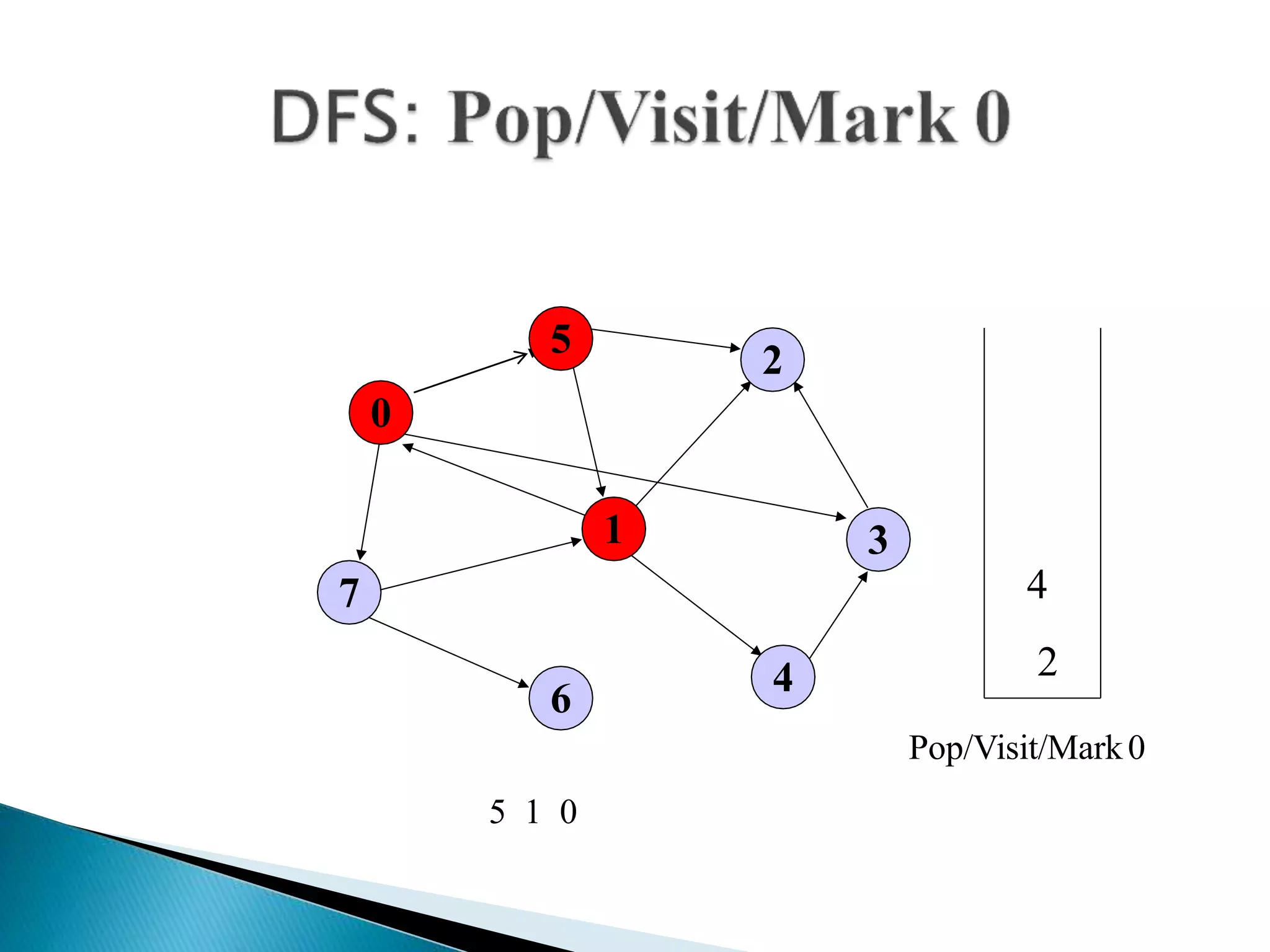
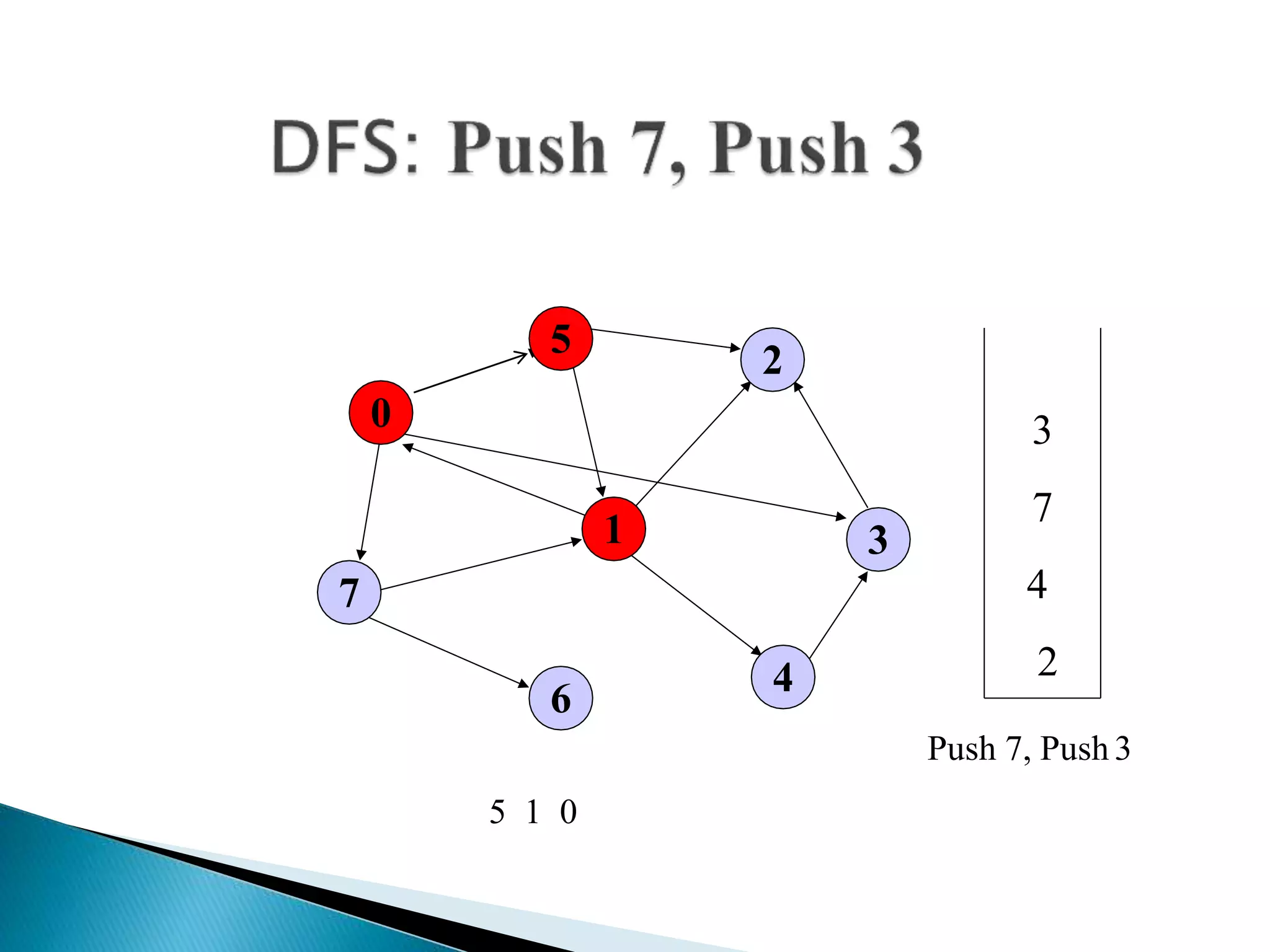
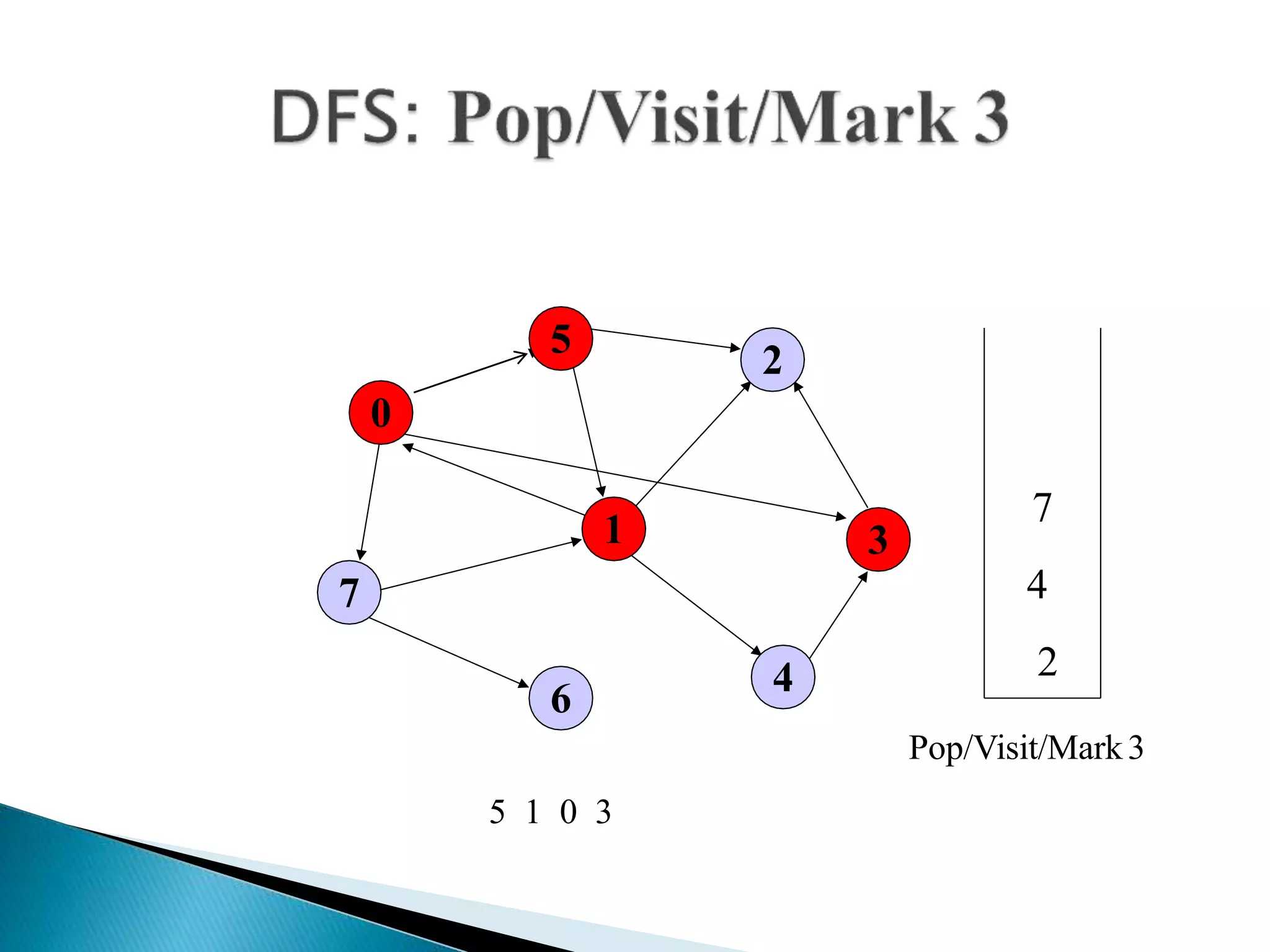
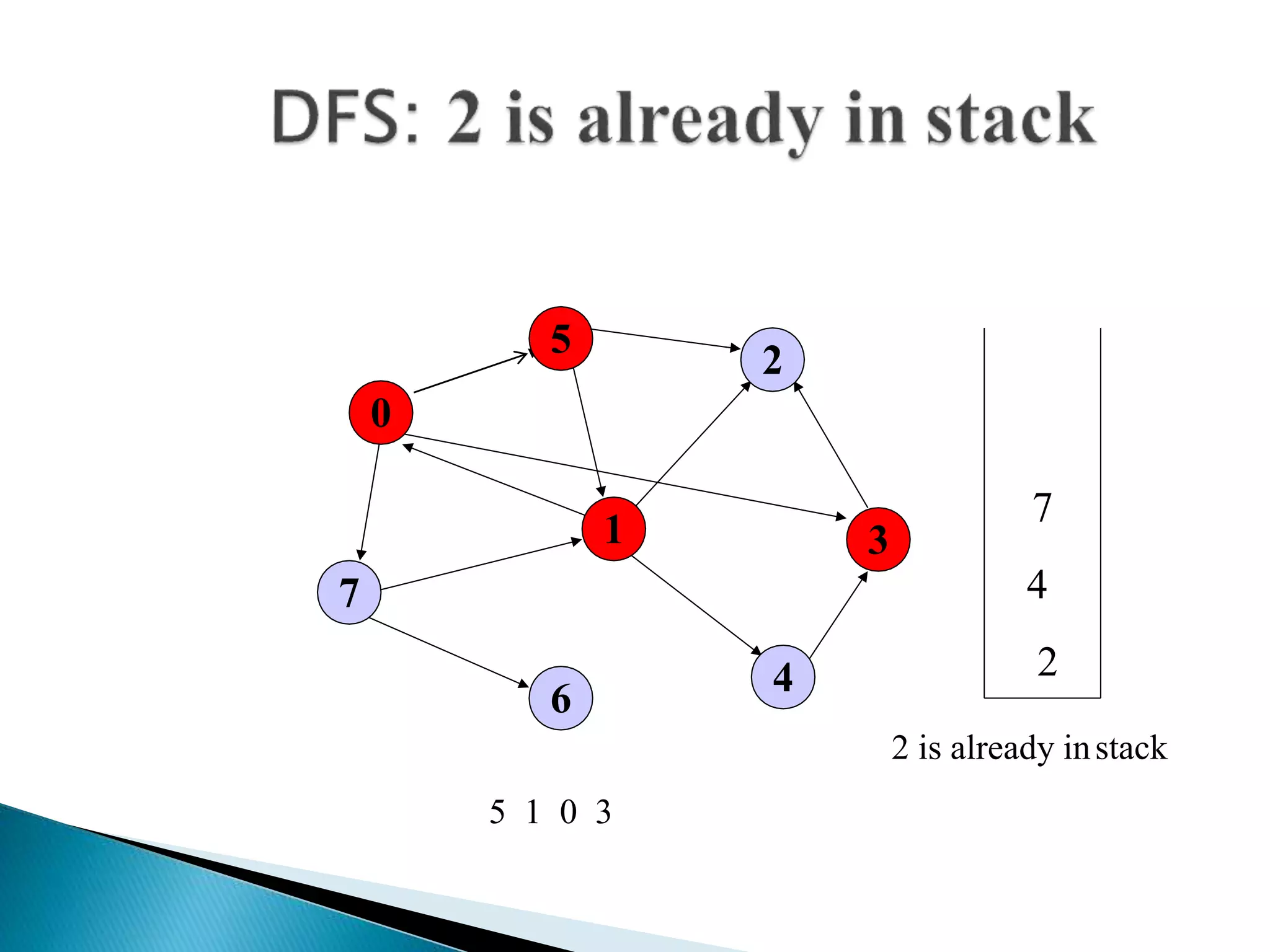
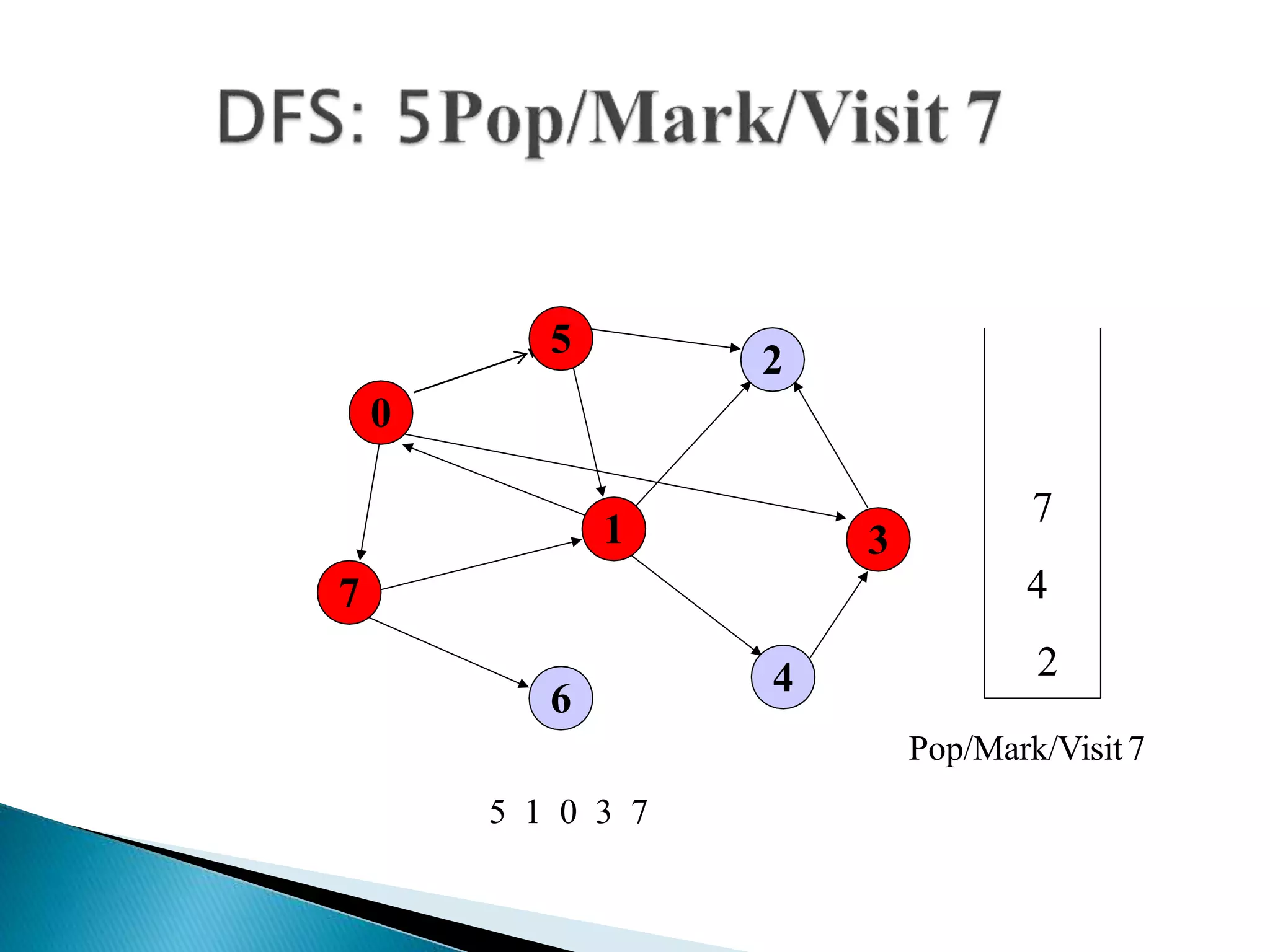
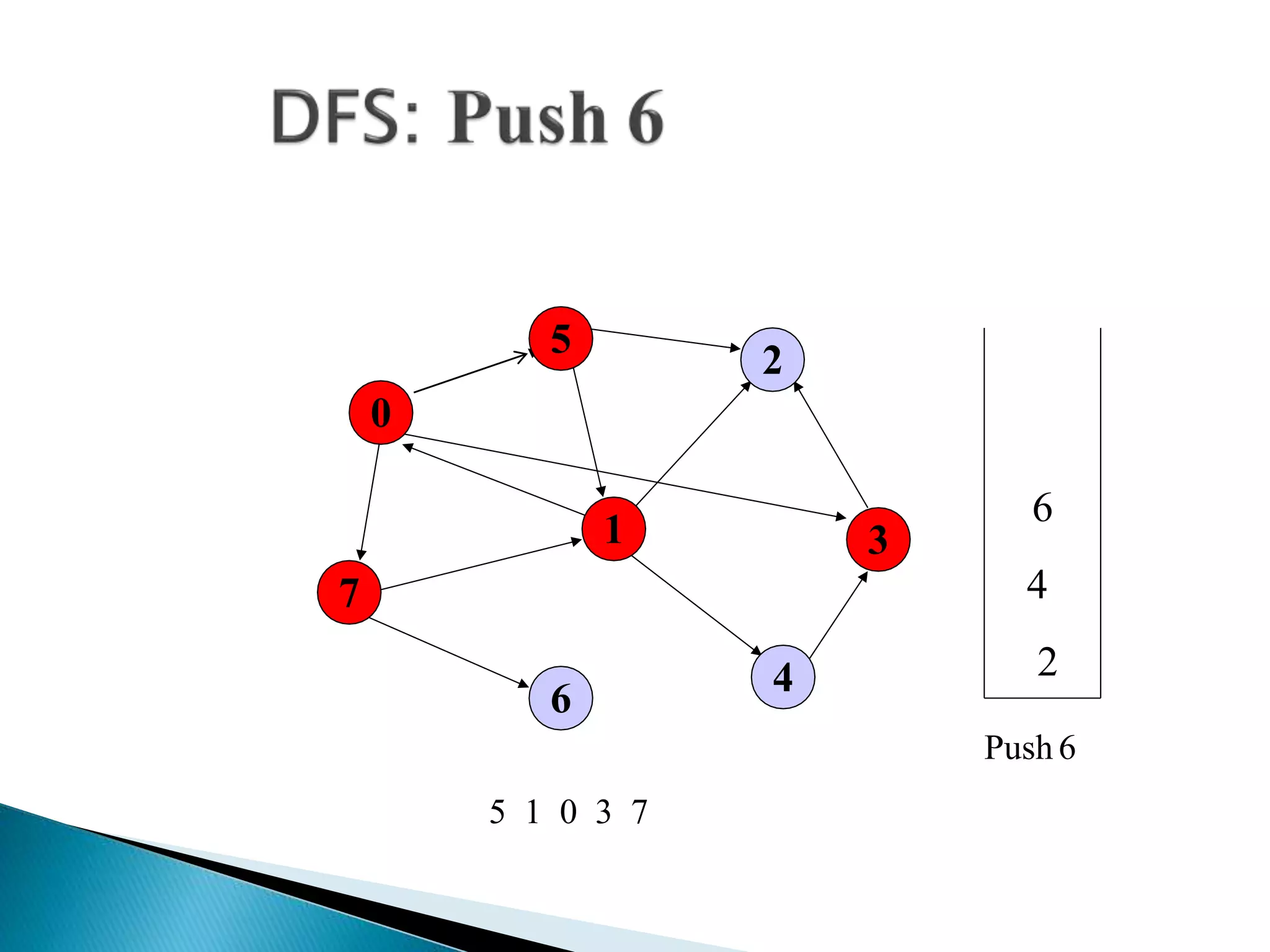
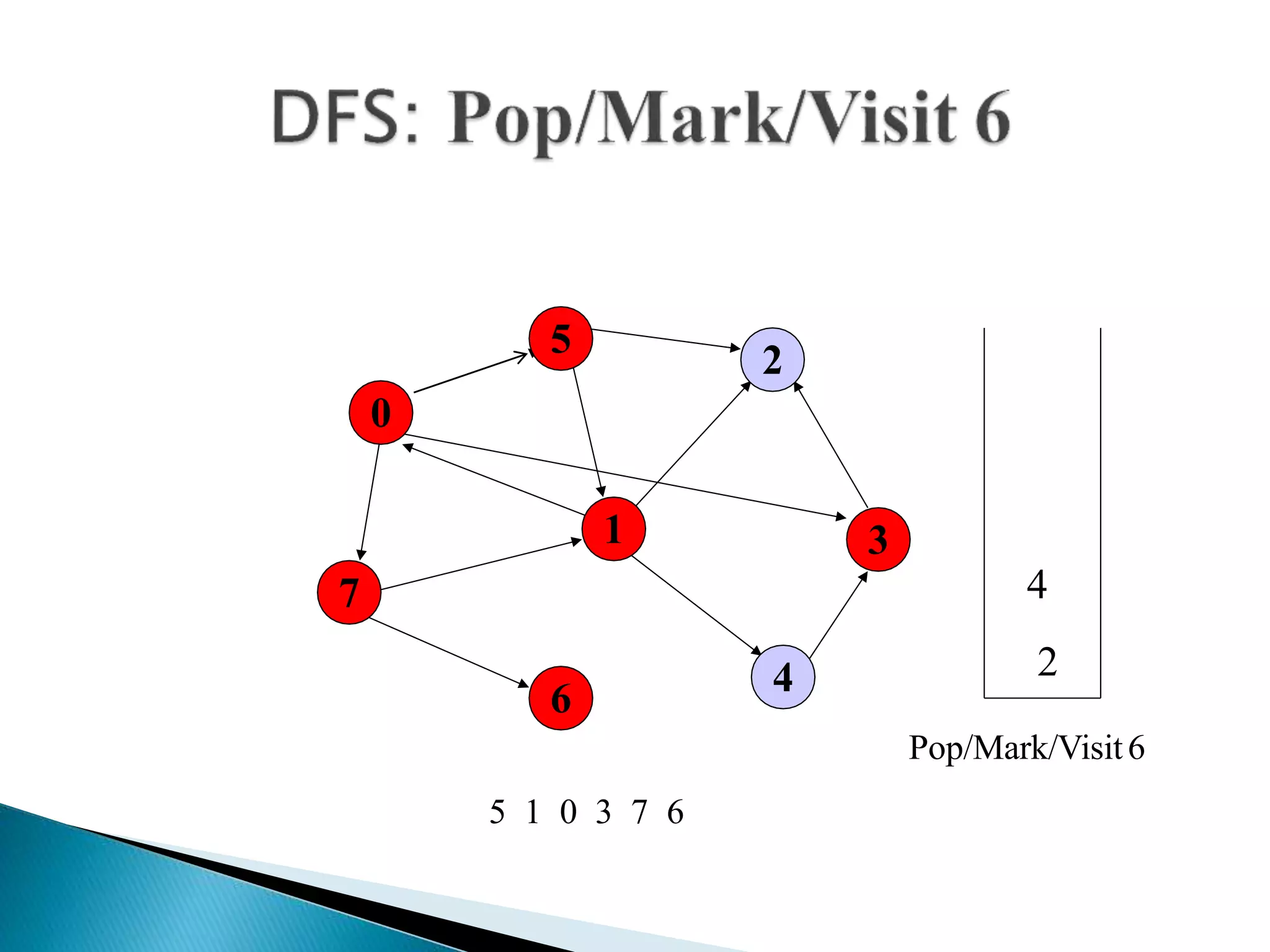
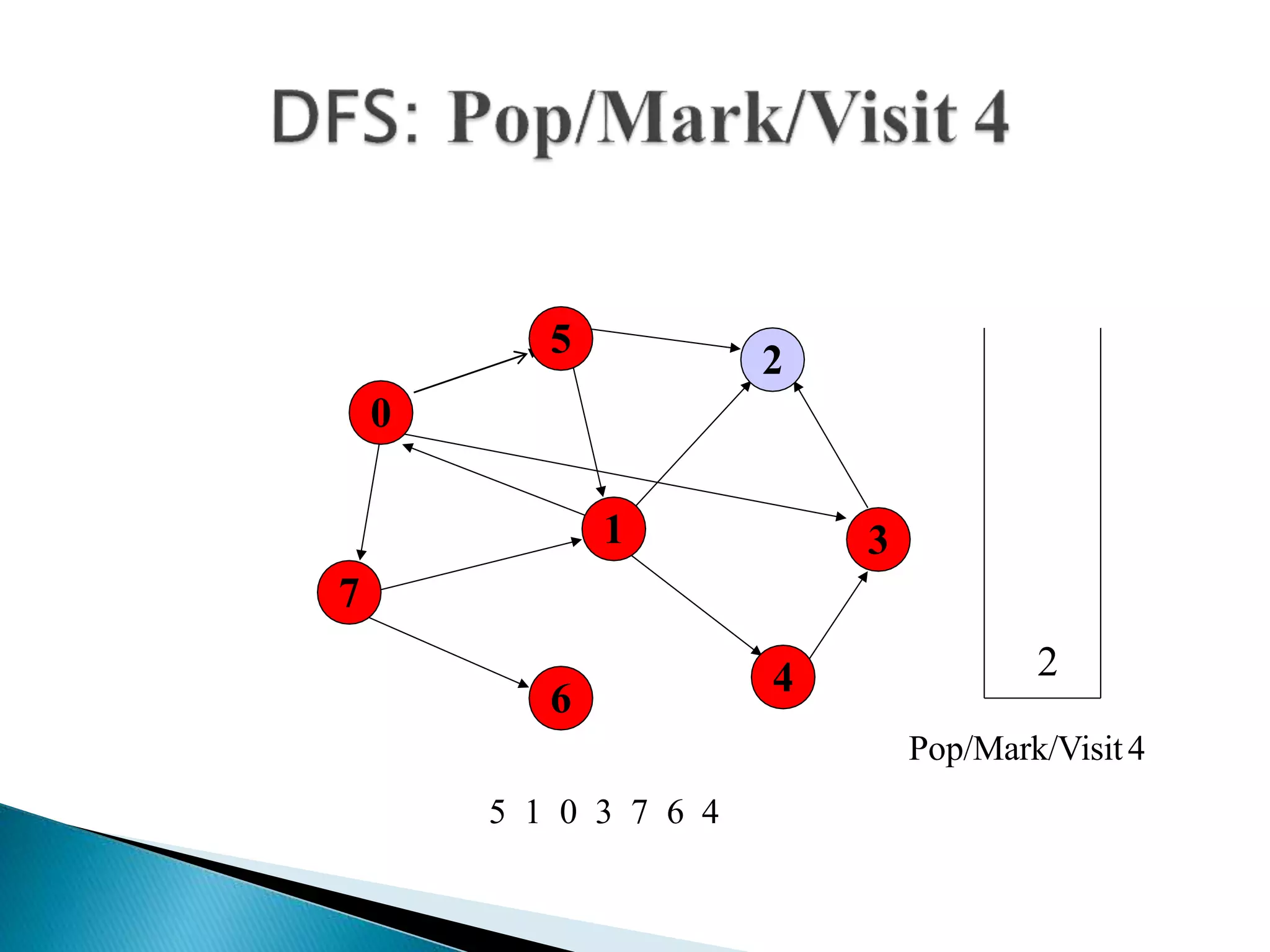
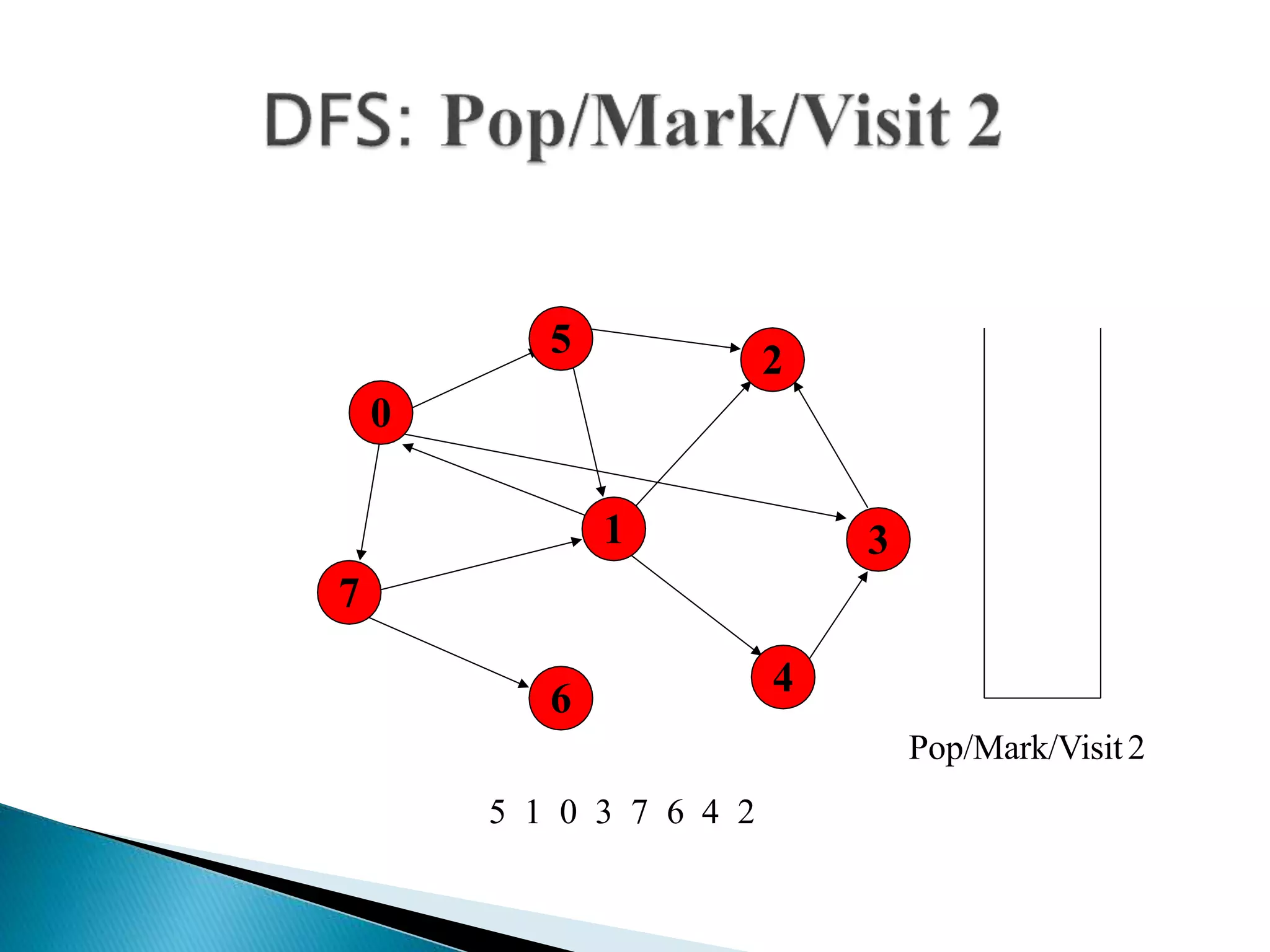
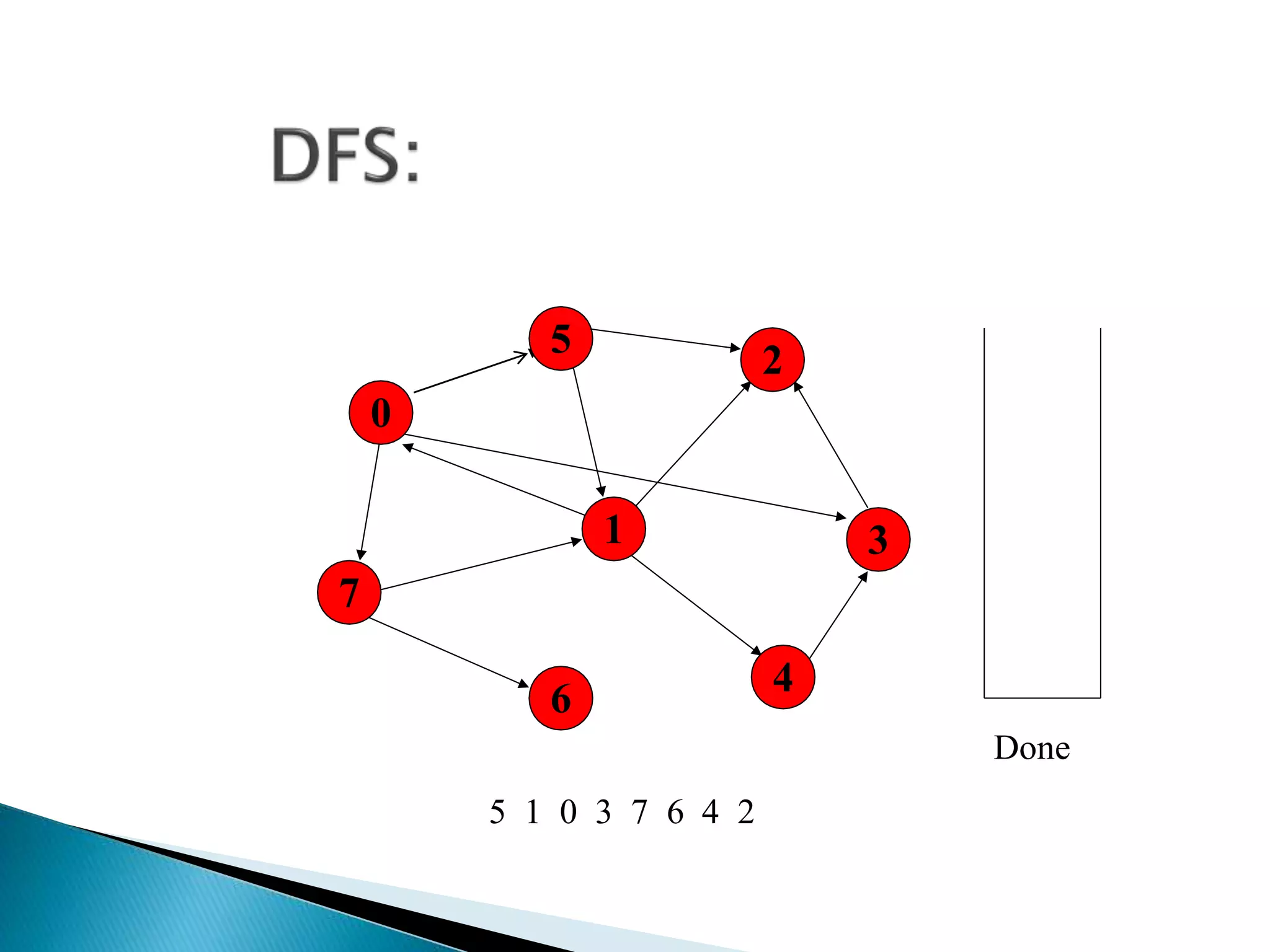
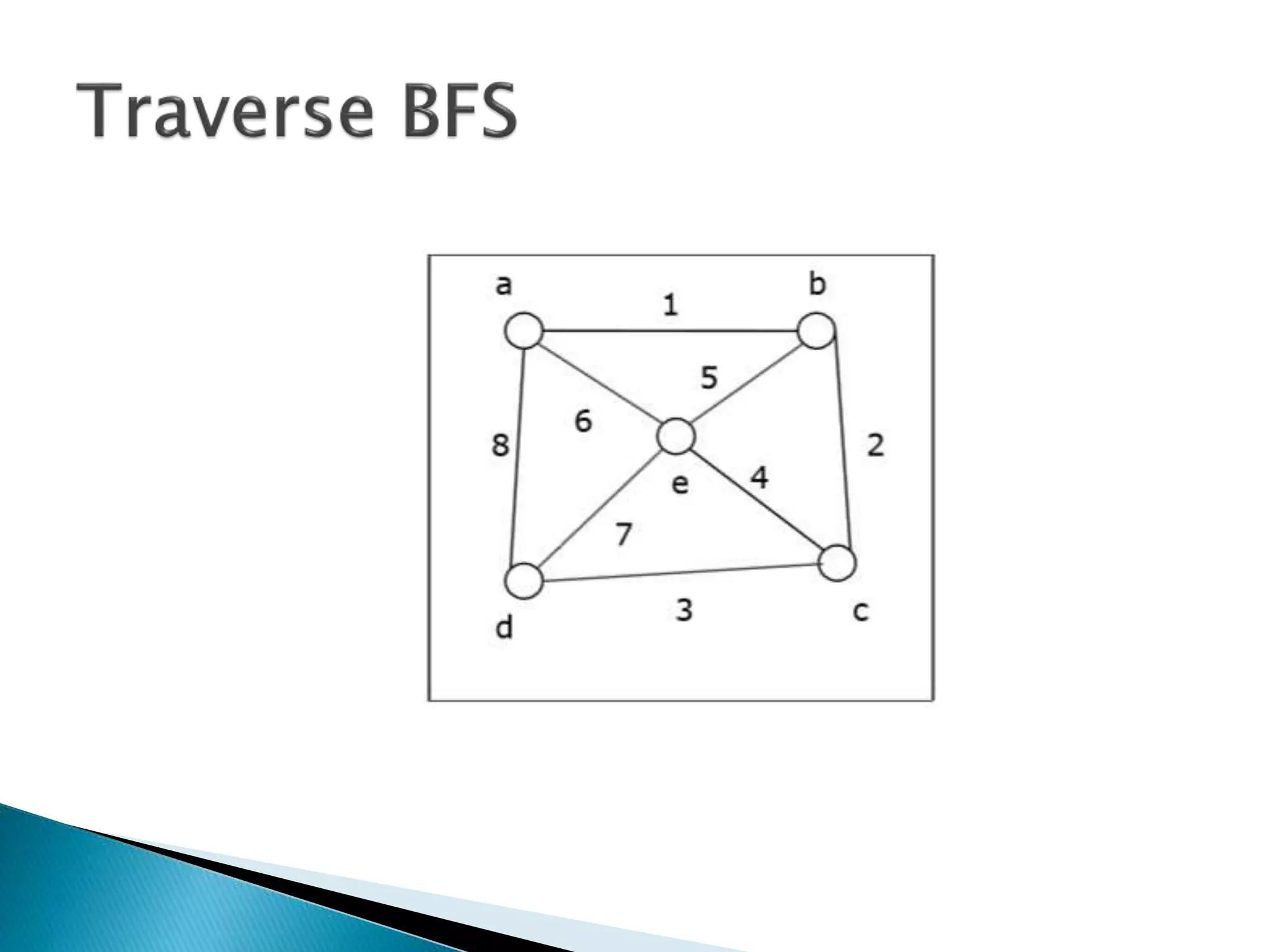
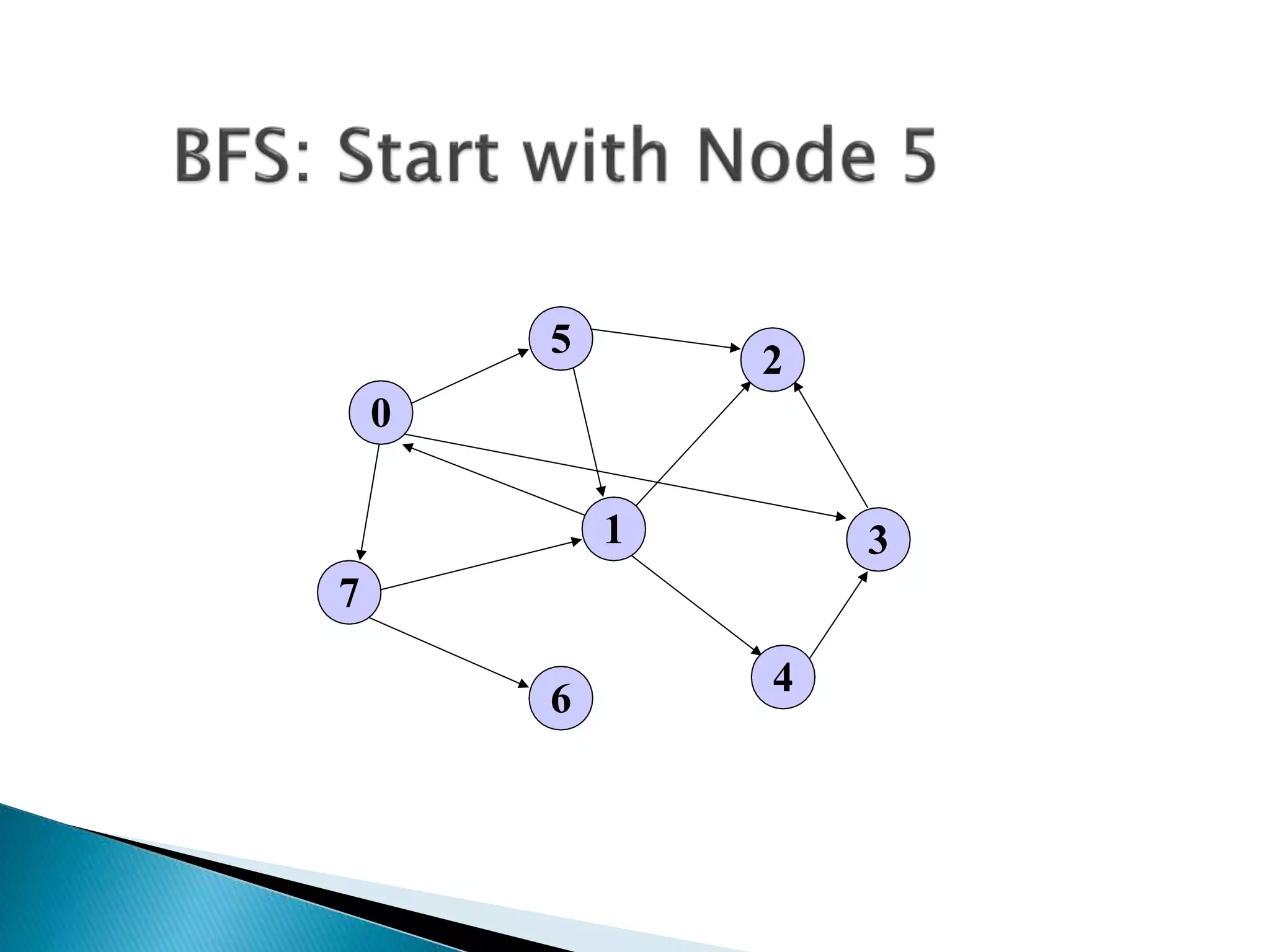
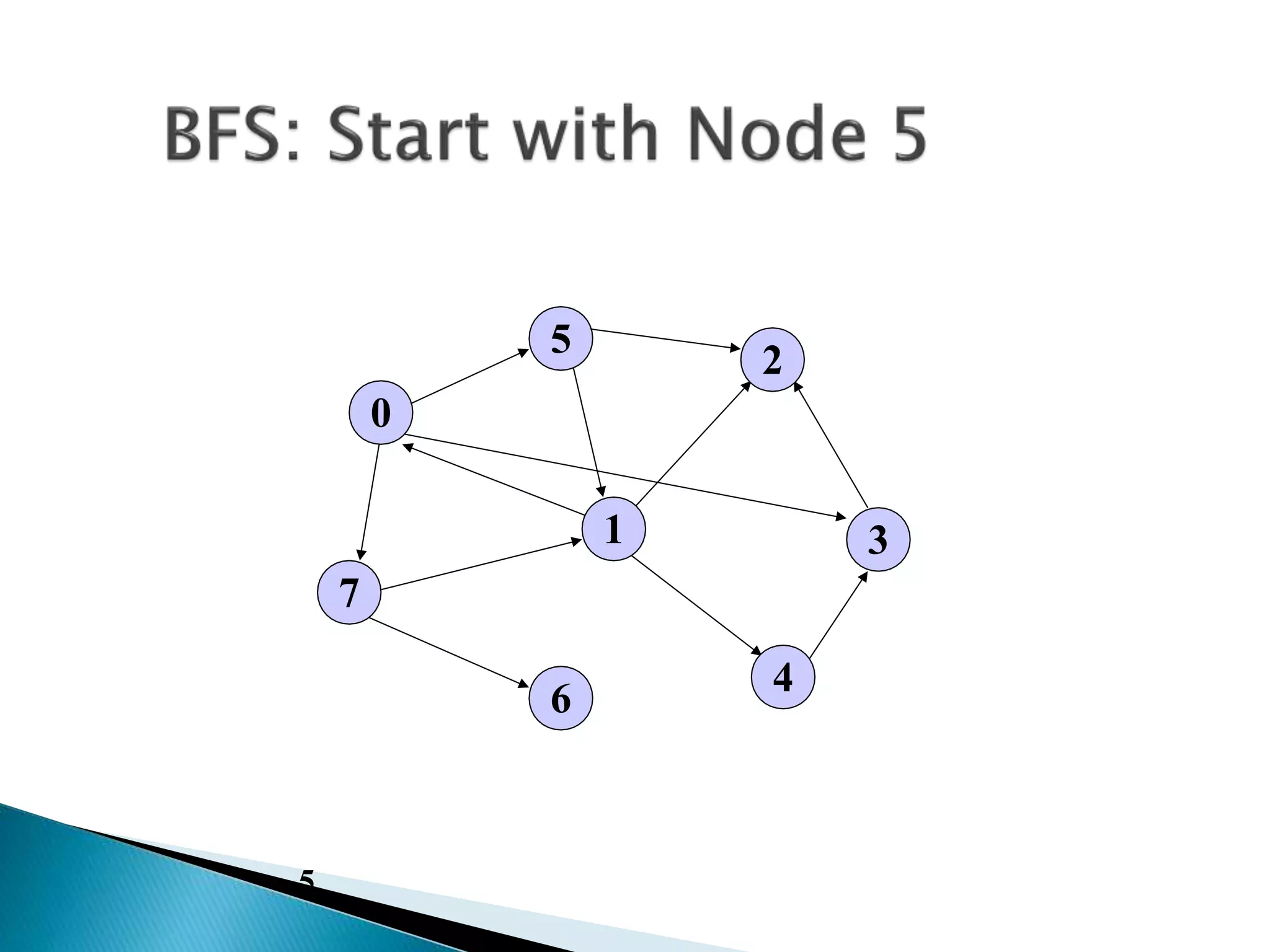
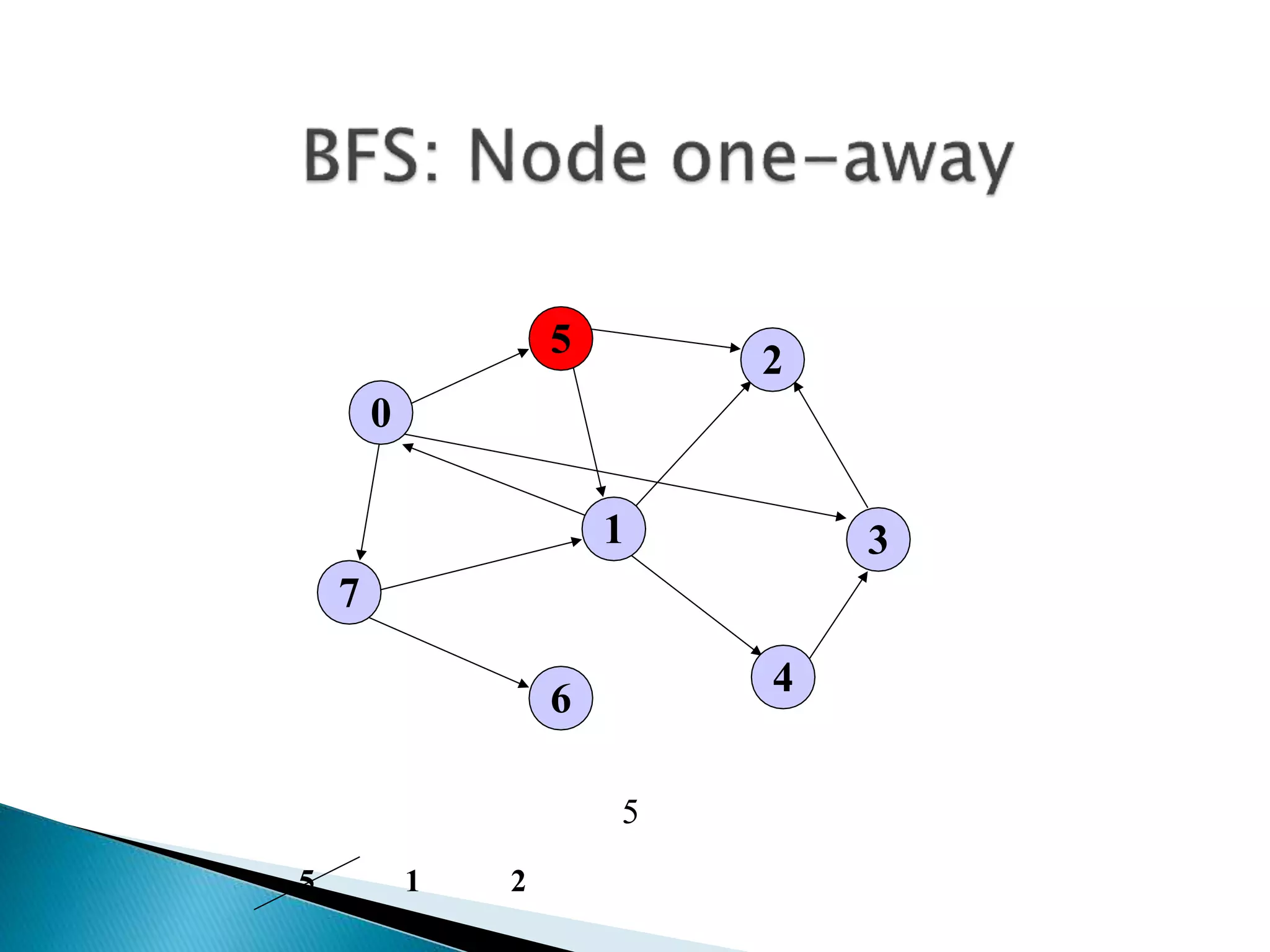
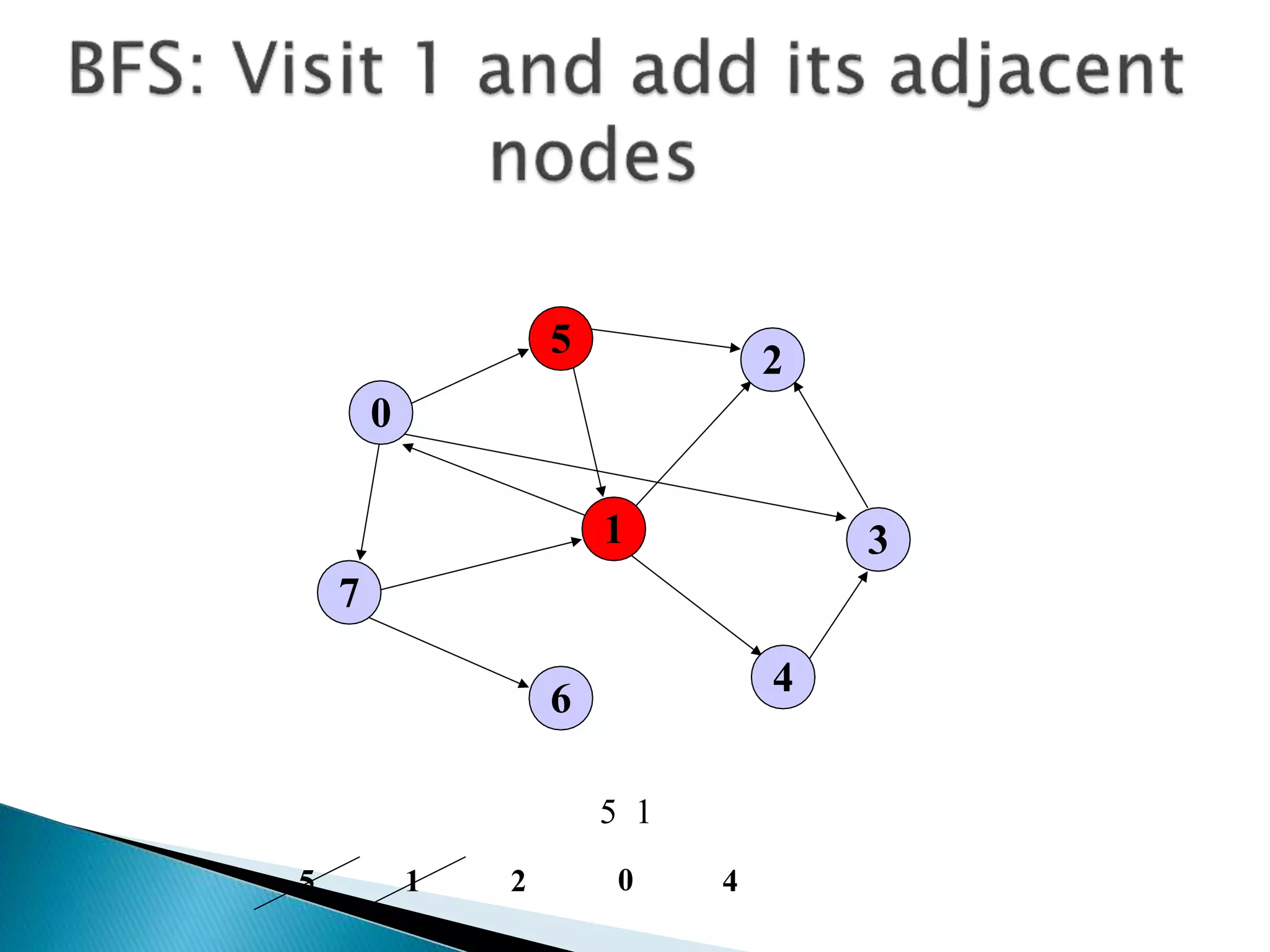
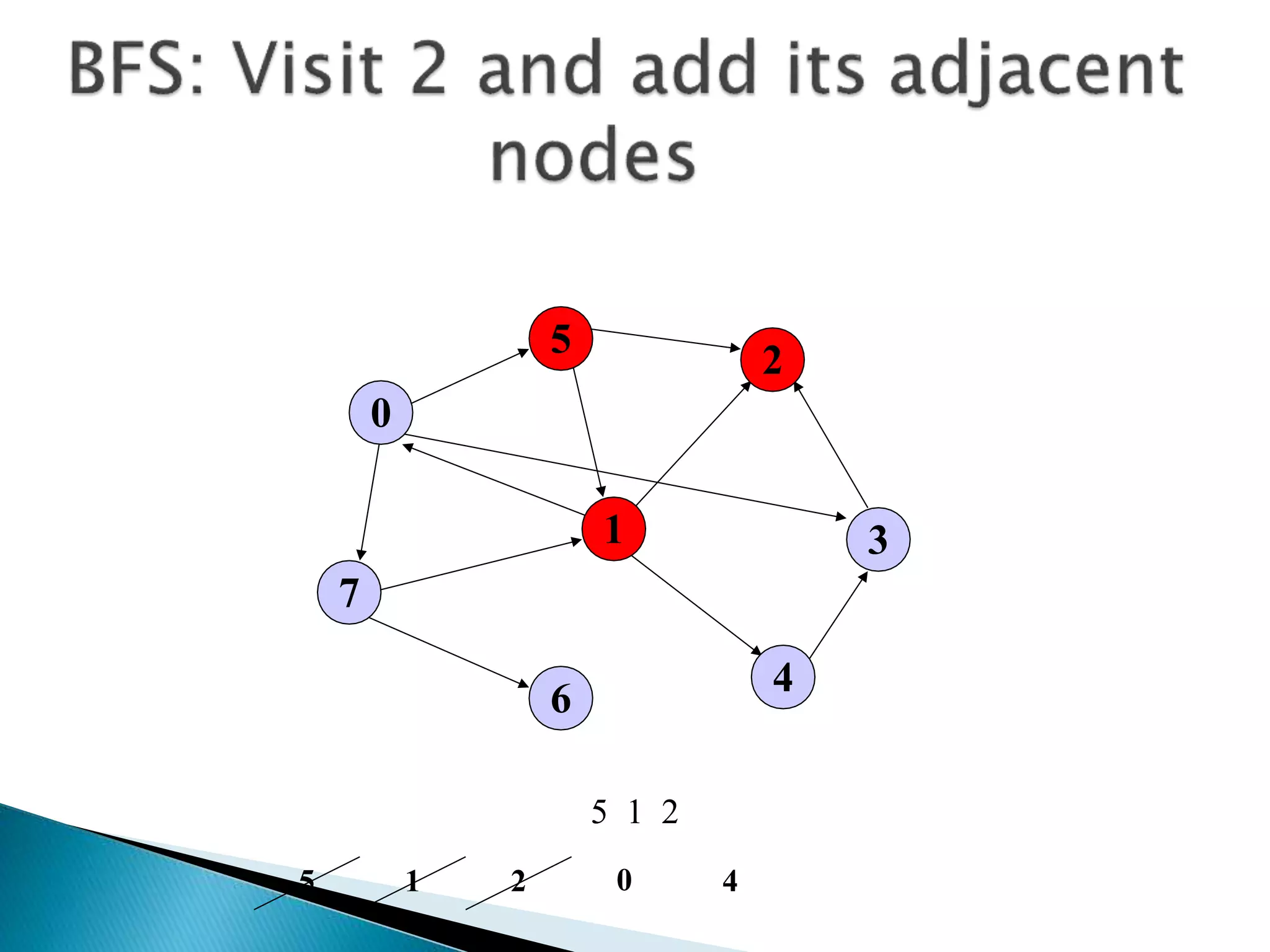
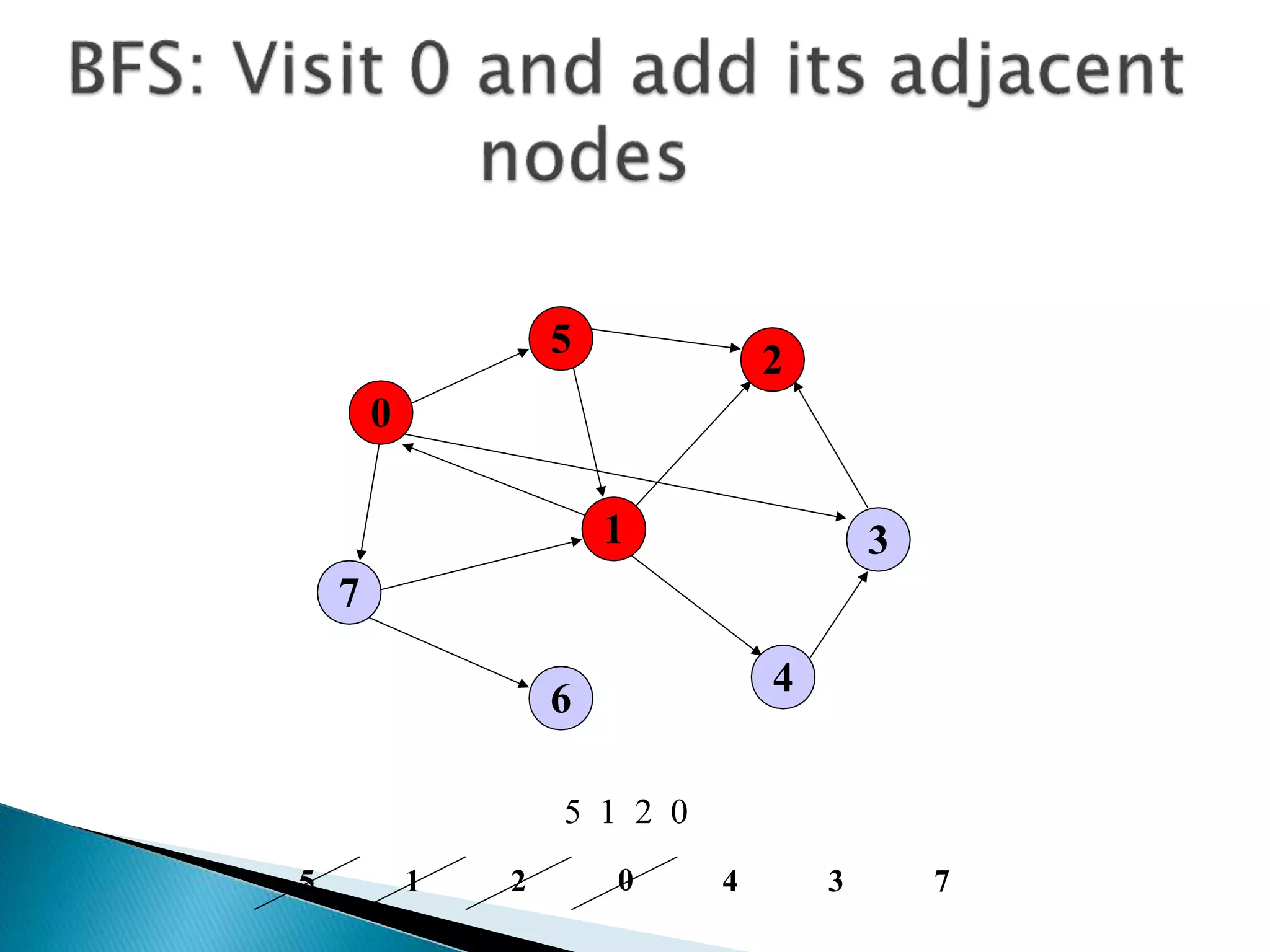
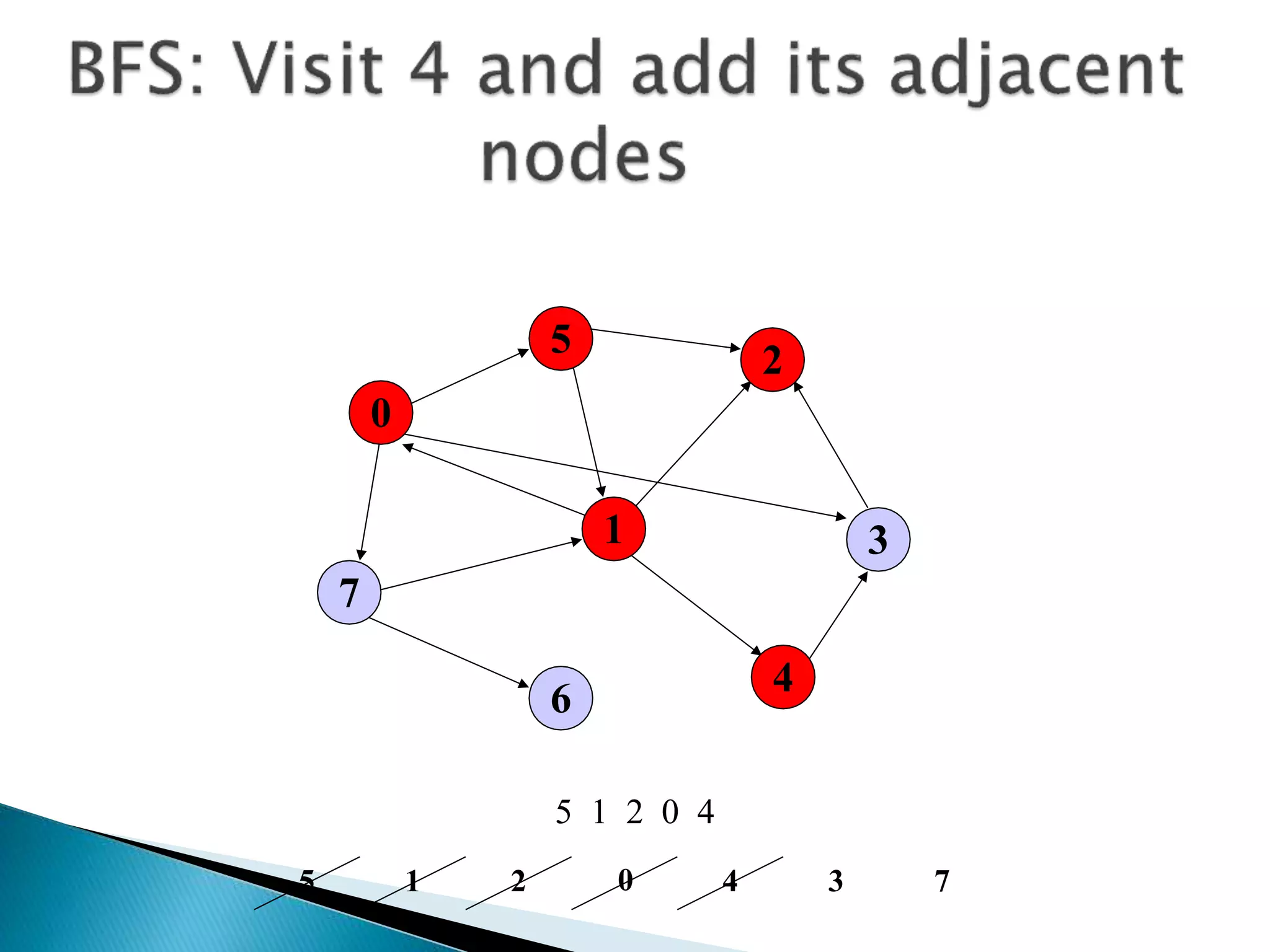
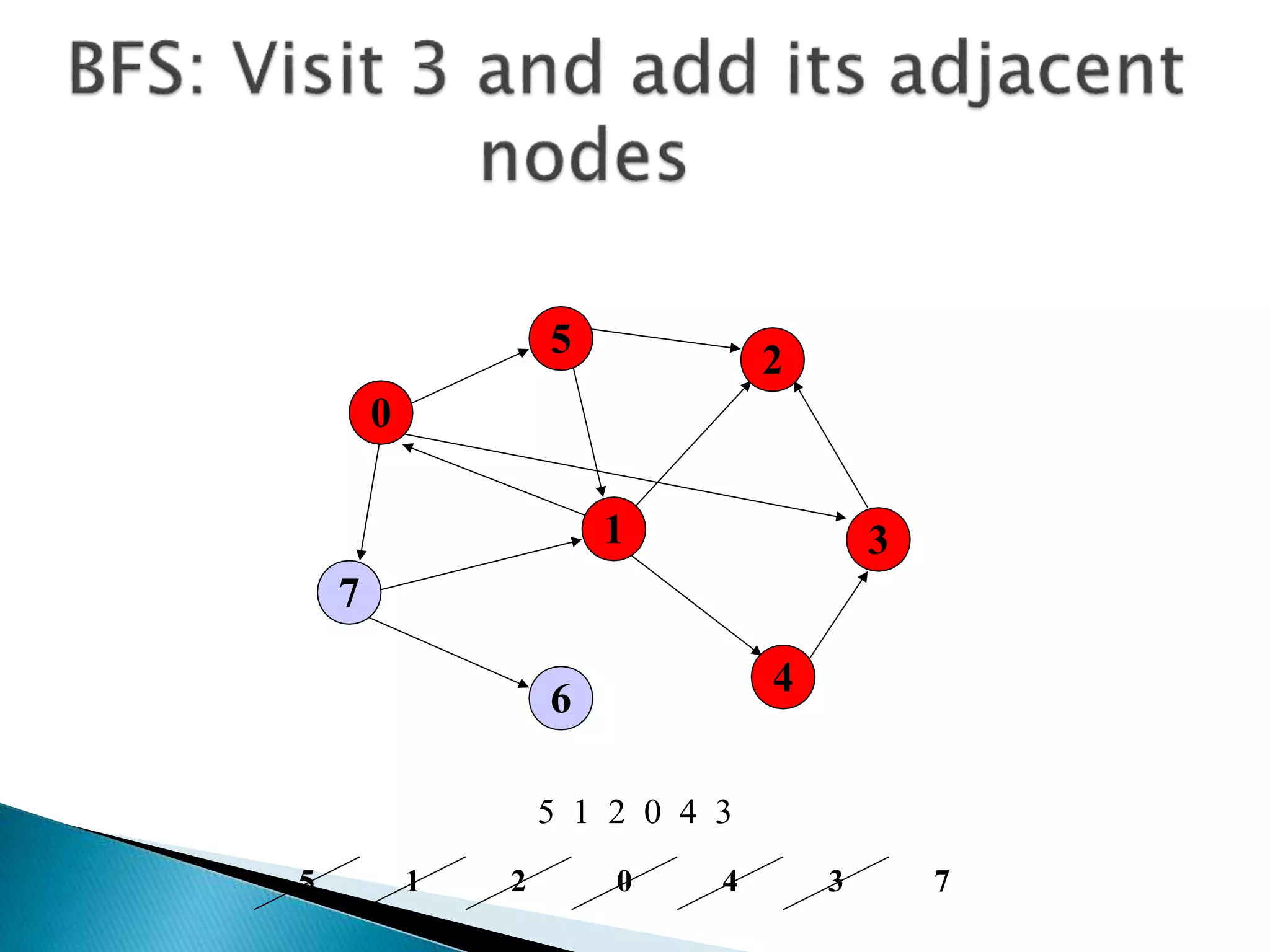
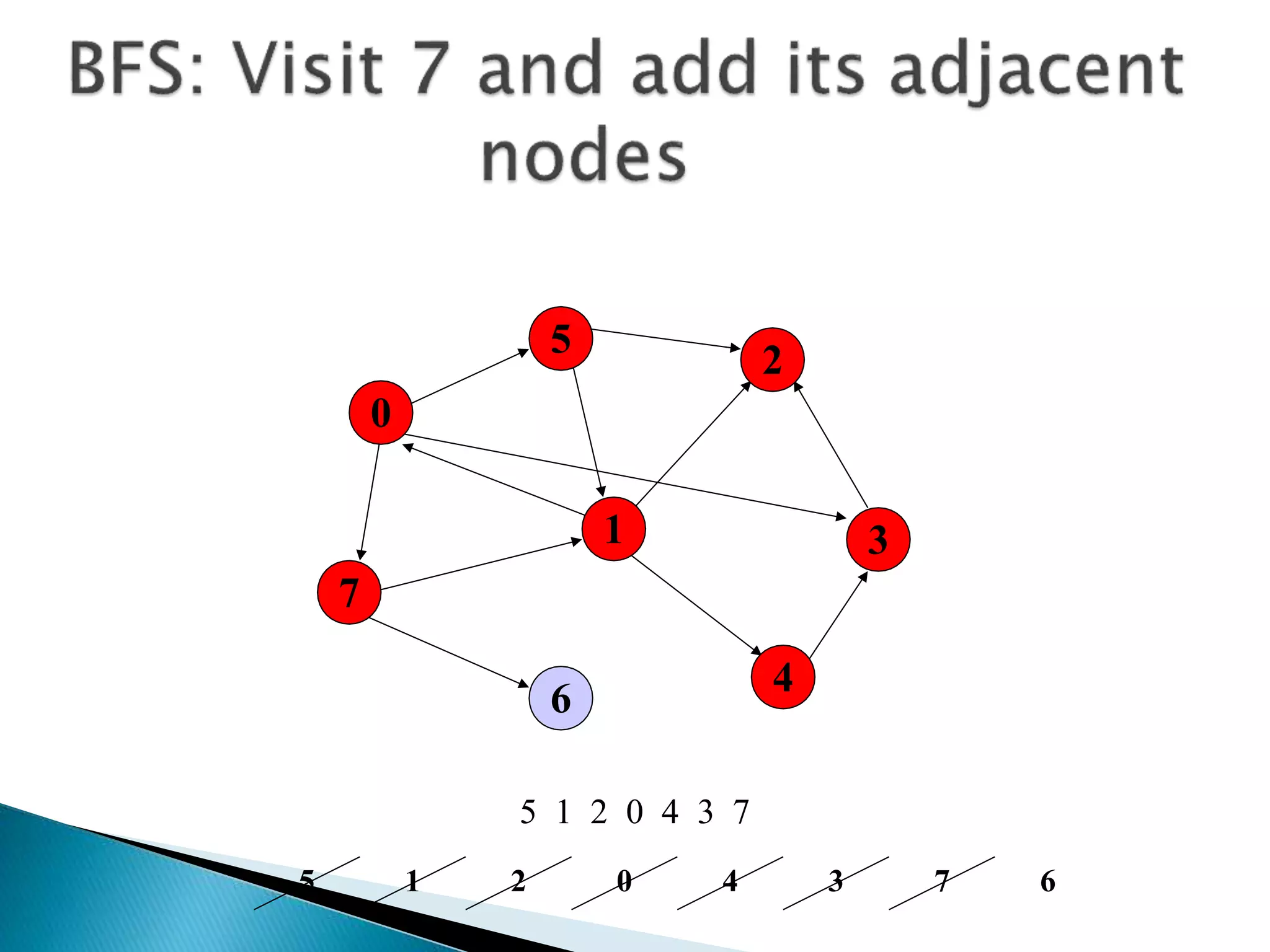
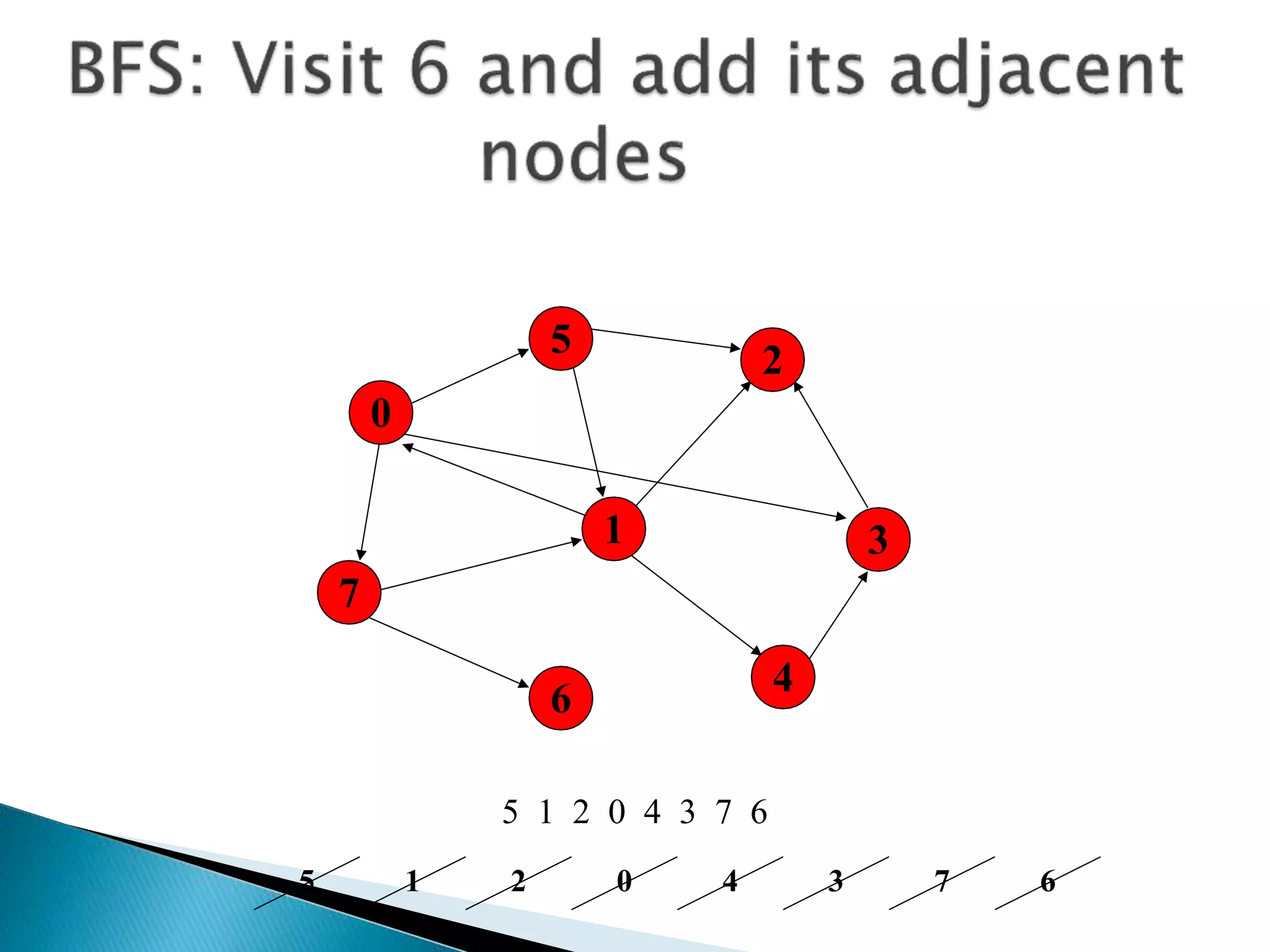
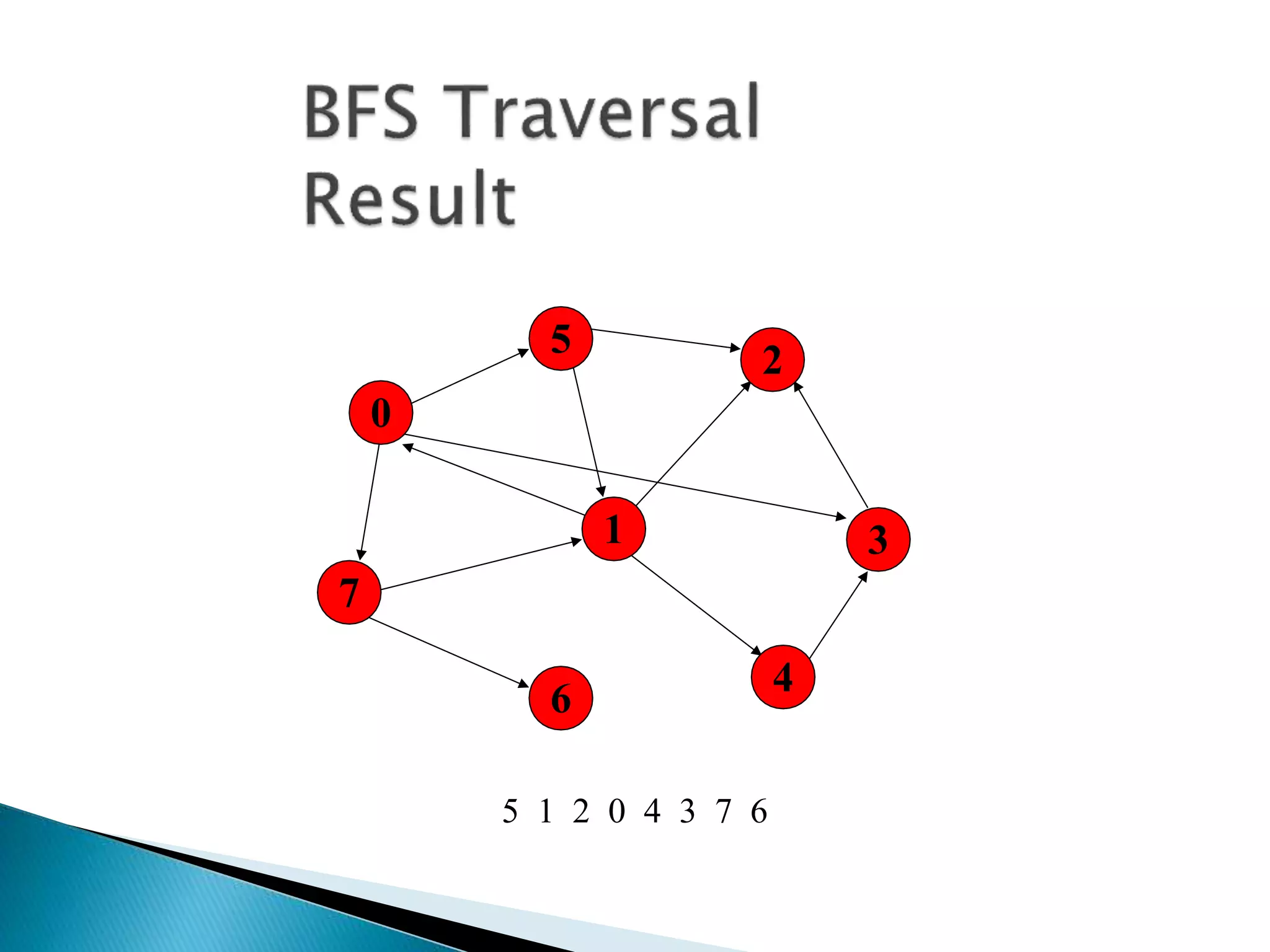
The document discusses graph traversal algorithms depth-first search (DFS) and breadth-first search (BFS). DFS uses a stack and traverses deeper nodes before shallower ones, outputting different traversal orders depending on the starting node. BFS uses a queue and traverses all neighbors of a node before moving to the next level, always outputting the same traversal order. Examples are given of applying DFS and BFS to a sample graph. Applications of the algorithms include computing distances, checking for cycles, and determining reachability between nodes.