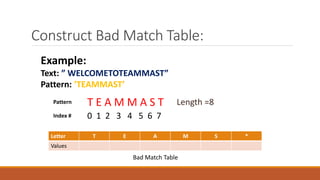
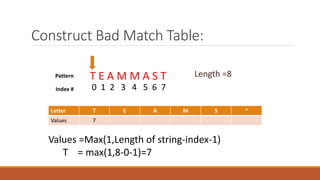
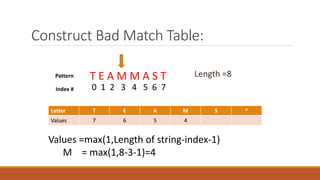
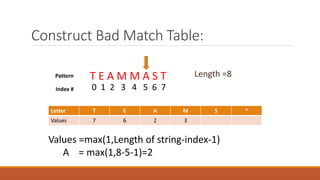
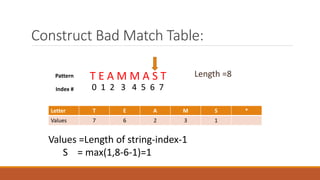
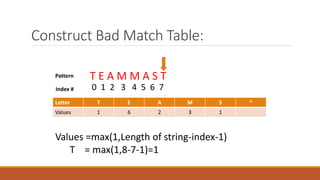
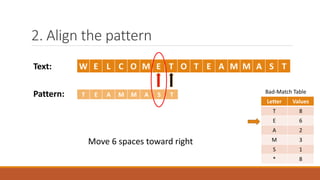
The Boyer-Moore string matching algorithm was developed in 1977 and is considered one of the most efficient string matching algorithms. It works by scanning the pattern from right to left and shifting the pattern by multiple characters if a mismatch is found, using preprocessing tables. The algorithm constructs a bad character shift table during preprocessing that stores the maximum number of positions a mismatched character can shift the pattern. It then aligns the pattern with the text and checks for matches, shifting the pattern right by the value in the table if a mismatch occurs.