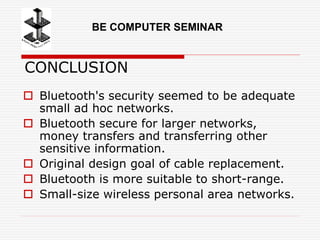
The document outlines a seminar presentation on Bluetooth security, covering its introduction, security framework, and applications. It discusses different security modes and levels, including link and service level security, as well as the benefits and use cases of Bluetooth technology. The conclusion mentions that while Bluetooth security is adequate for small networks, it may not be suitable for larger networks involving sensitive information.









![BE COMPUTER SEMINAR
BIBLIOGRAPHY
Jun-Zhao Sun, Douglas Howie, Antti Koivisto,
and Jaakko Sauvola. Design, Implementation,
And Evaluation Of Bluetooth Security, [referred
2002-01-07]
Saarinen M-J, A Software Implementation of
the Bluetooth Encryption, [referred 2000-03-15]
Muller T., Bluetooth Security Architecture:
Version1.0., Bluetooth Paper, Document #
1.C.116/1.0, July 15, 2000.](https://image.slidesharecdn.com/bluetoothsecurity-220417164937/85/Bluetooth-Security-PPT-17-320.jpg)

