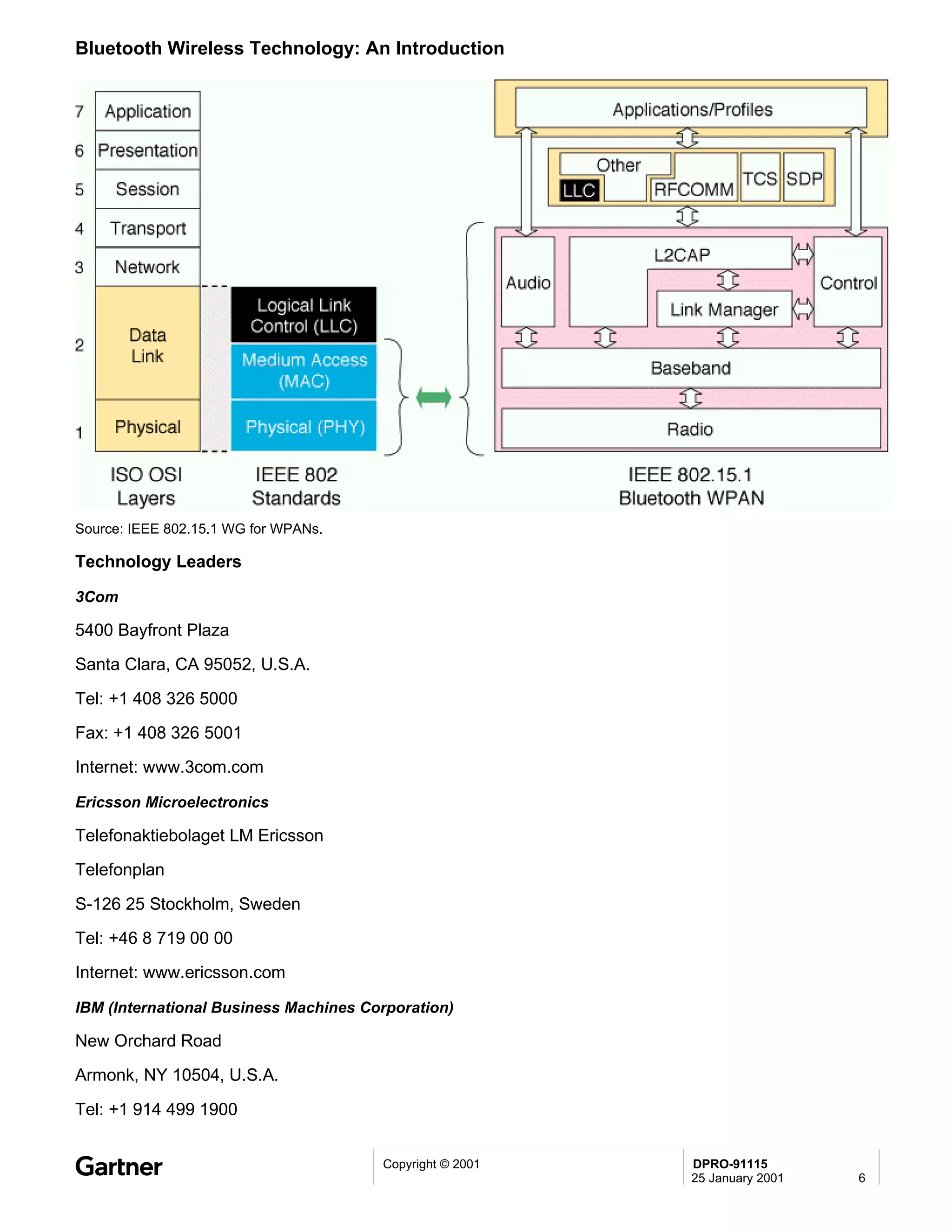
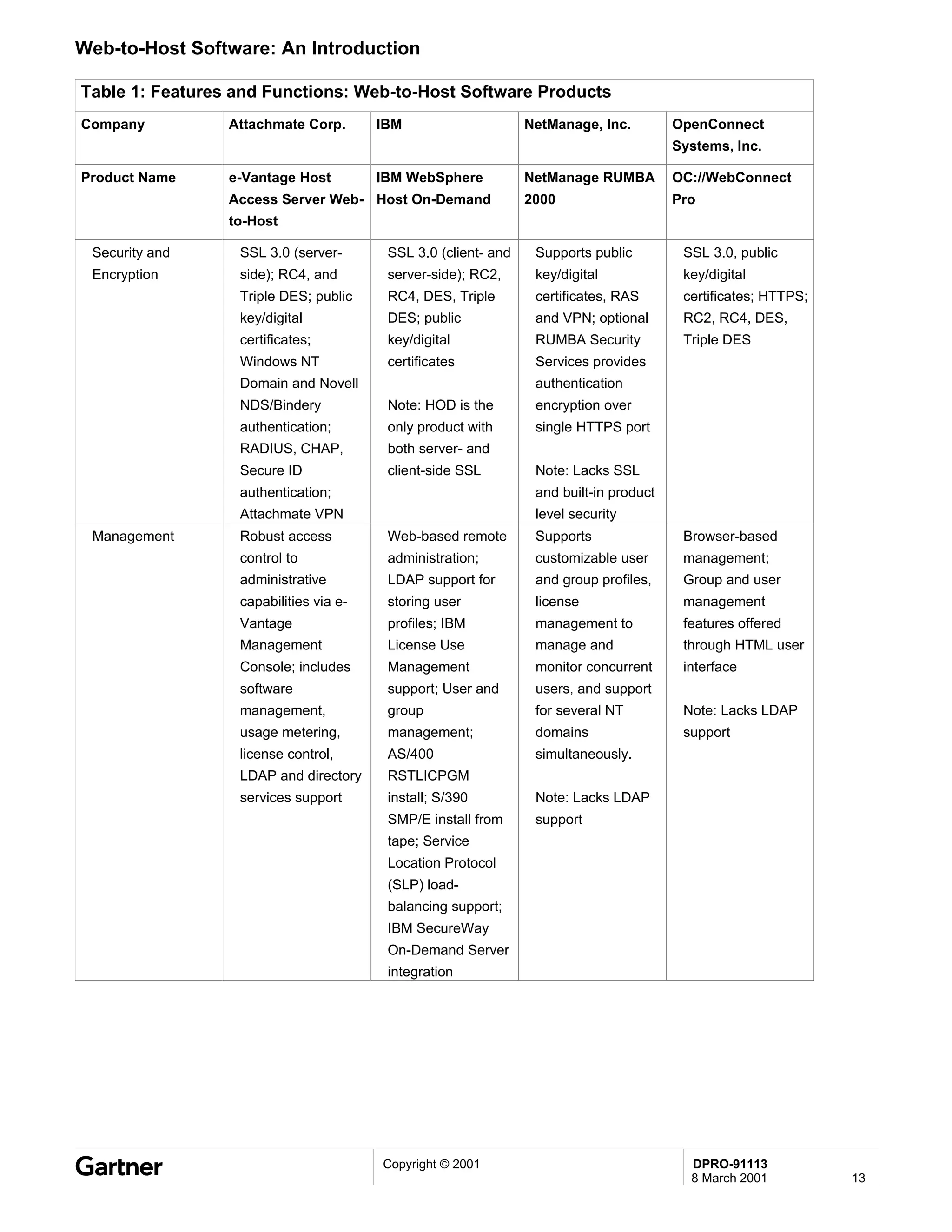
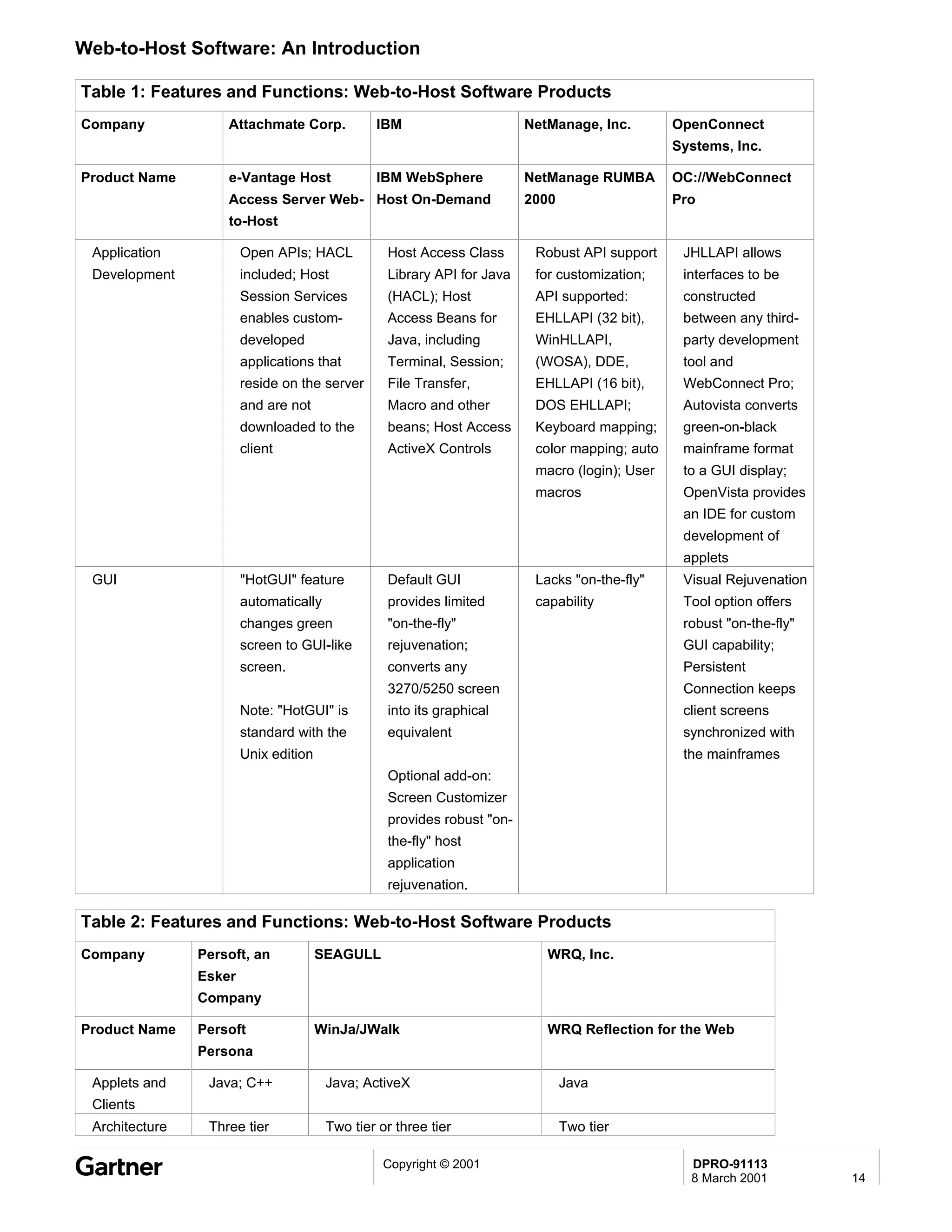
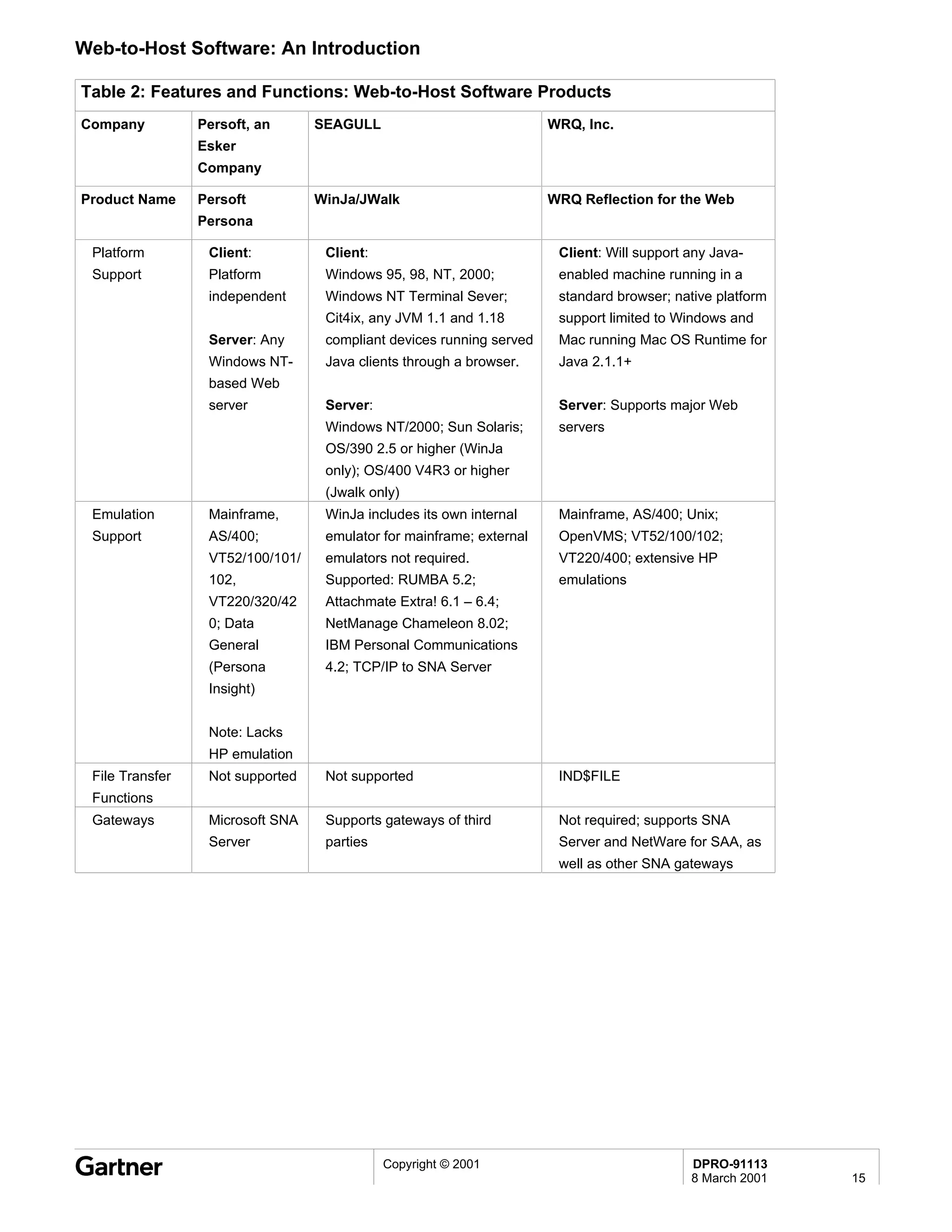
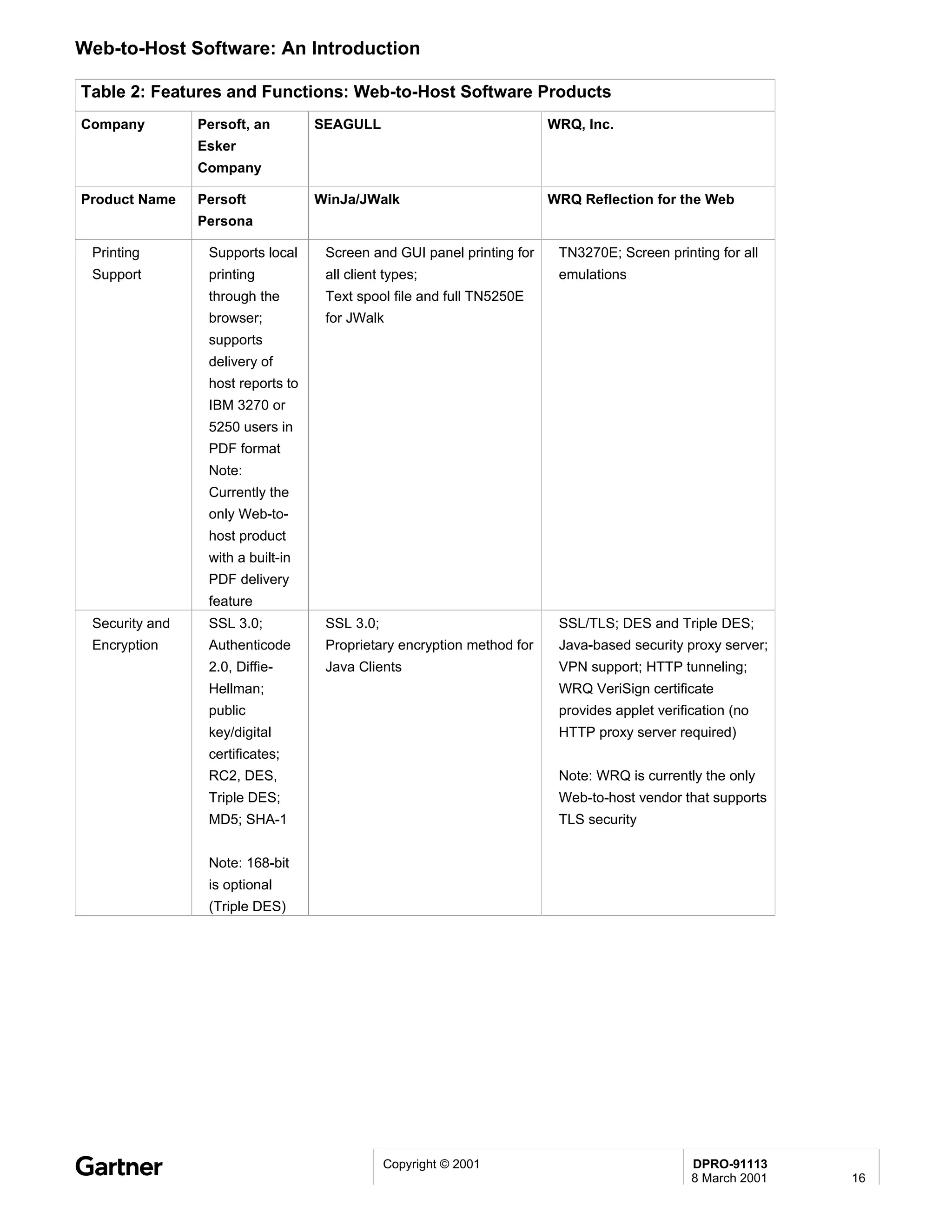
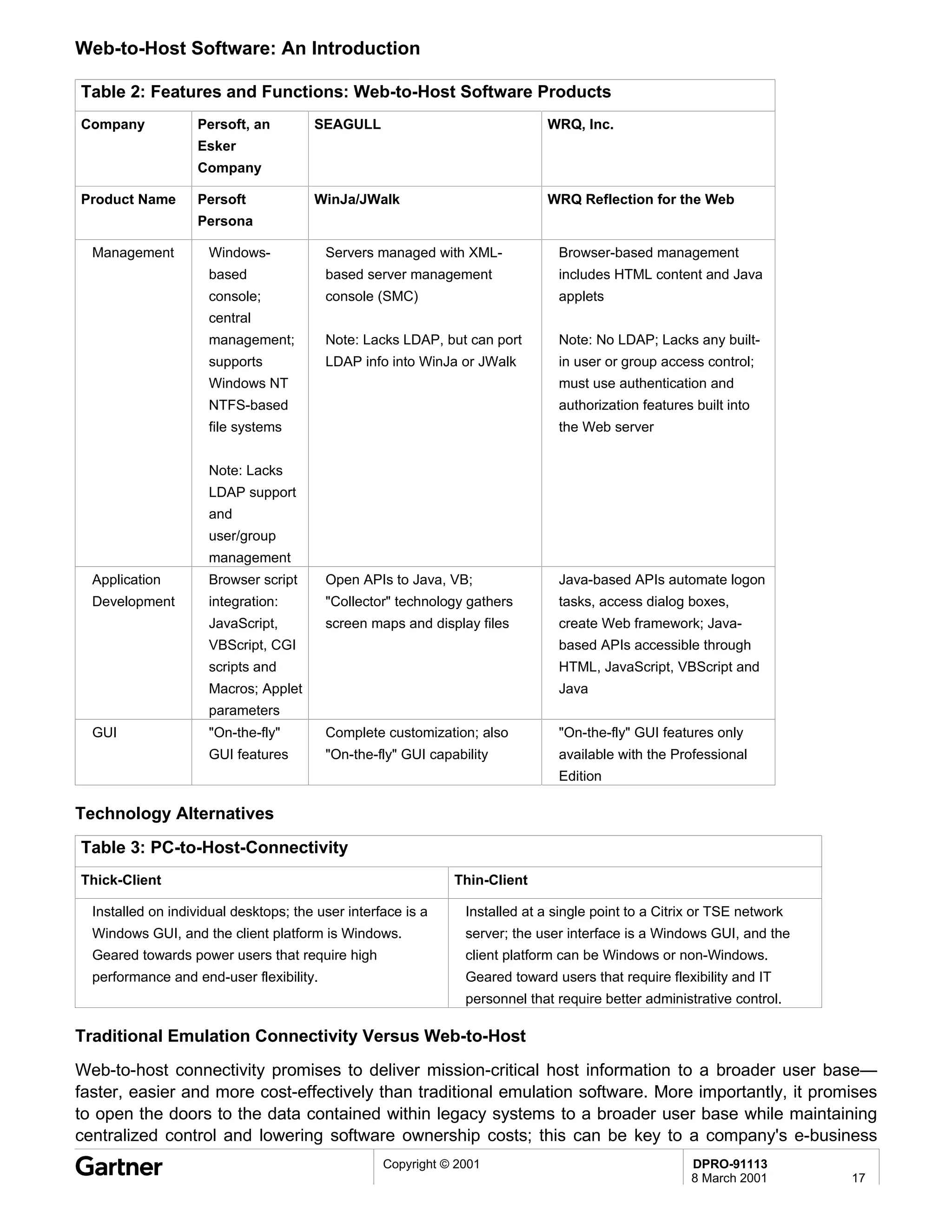
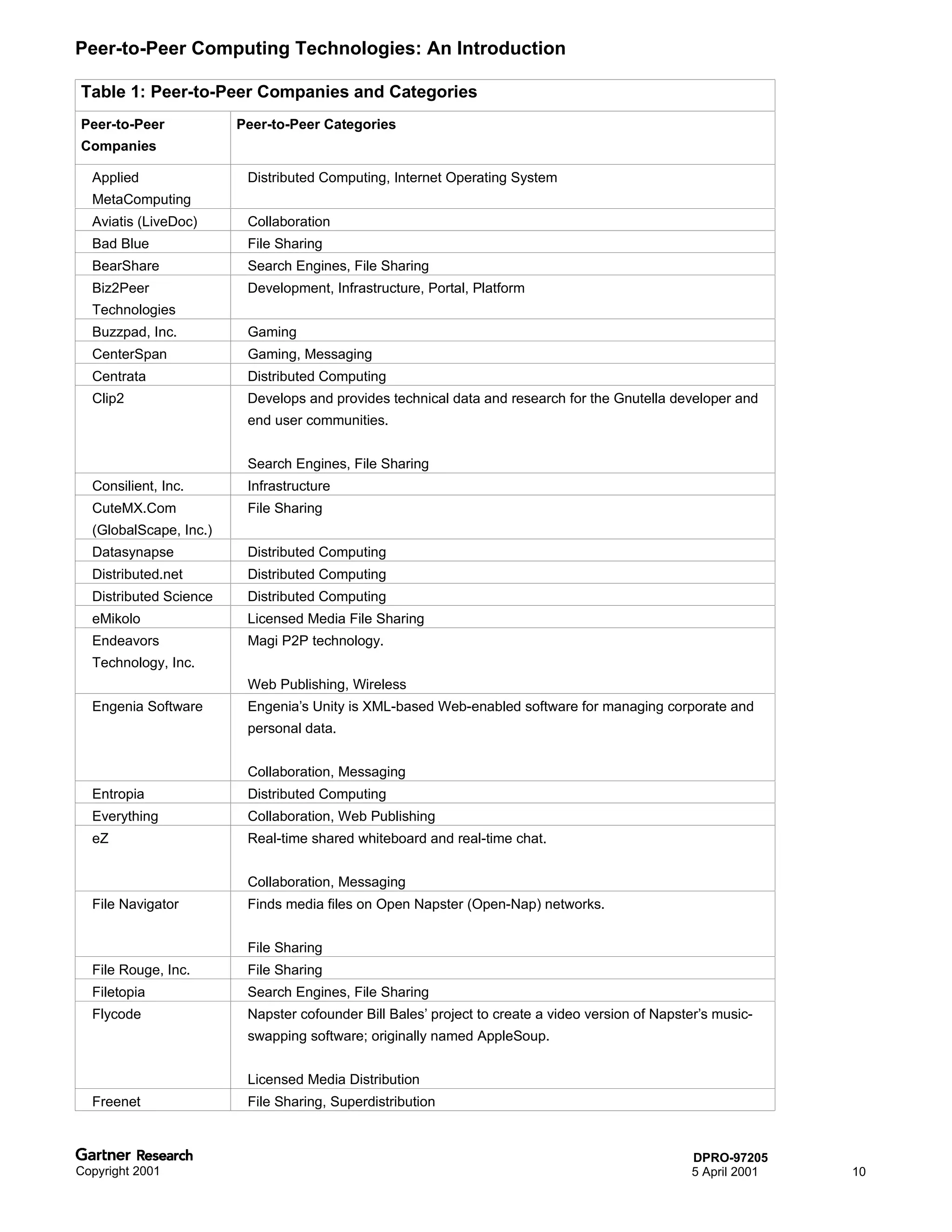
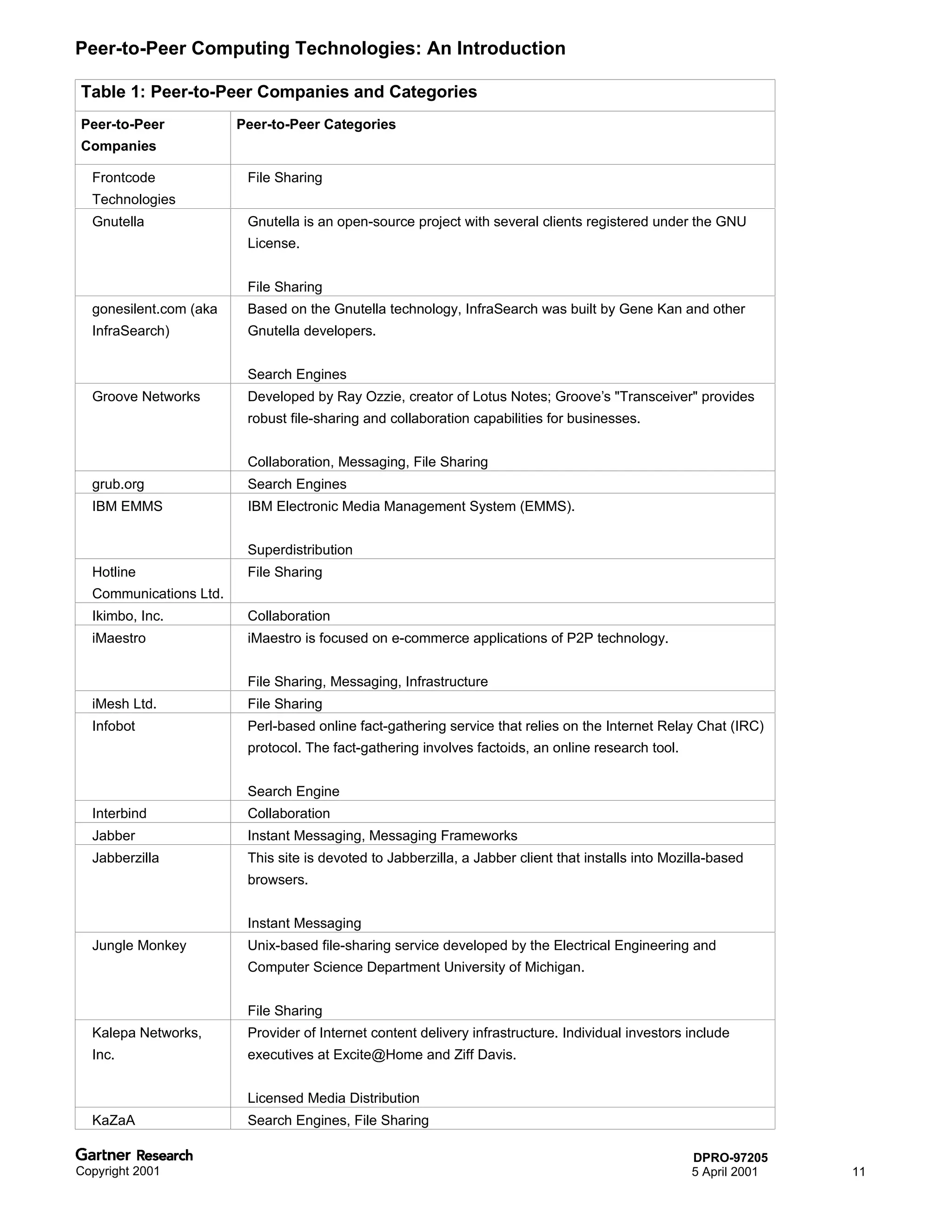
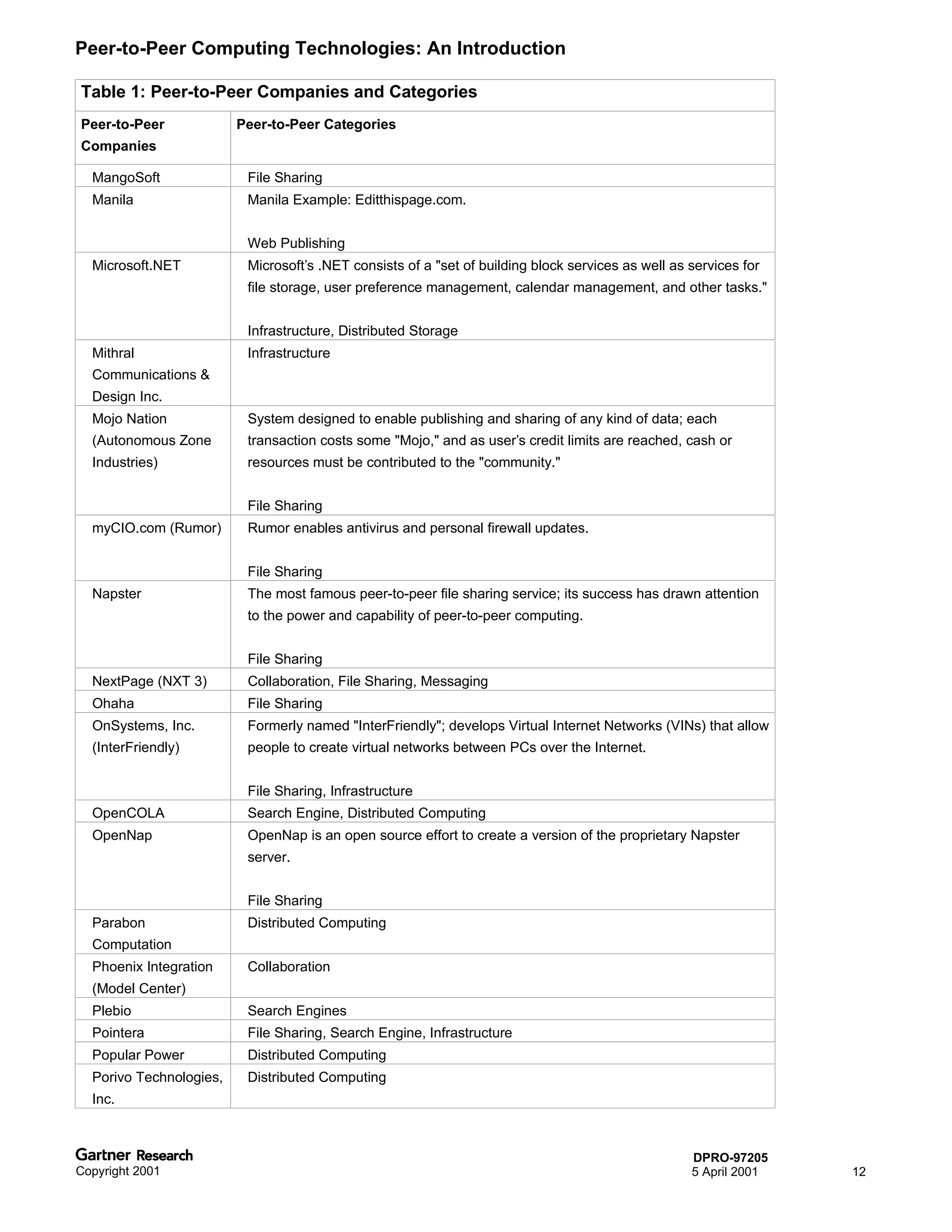
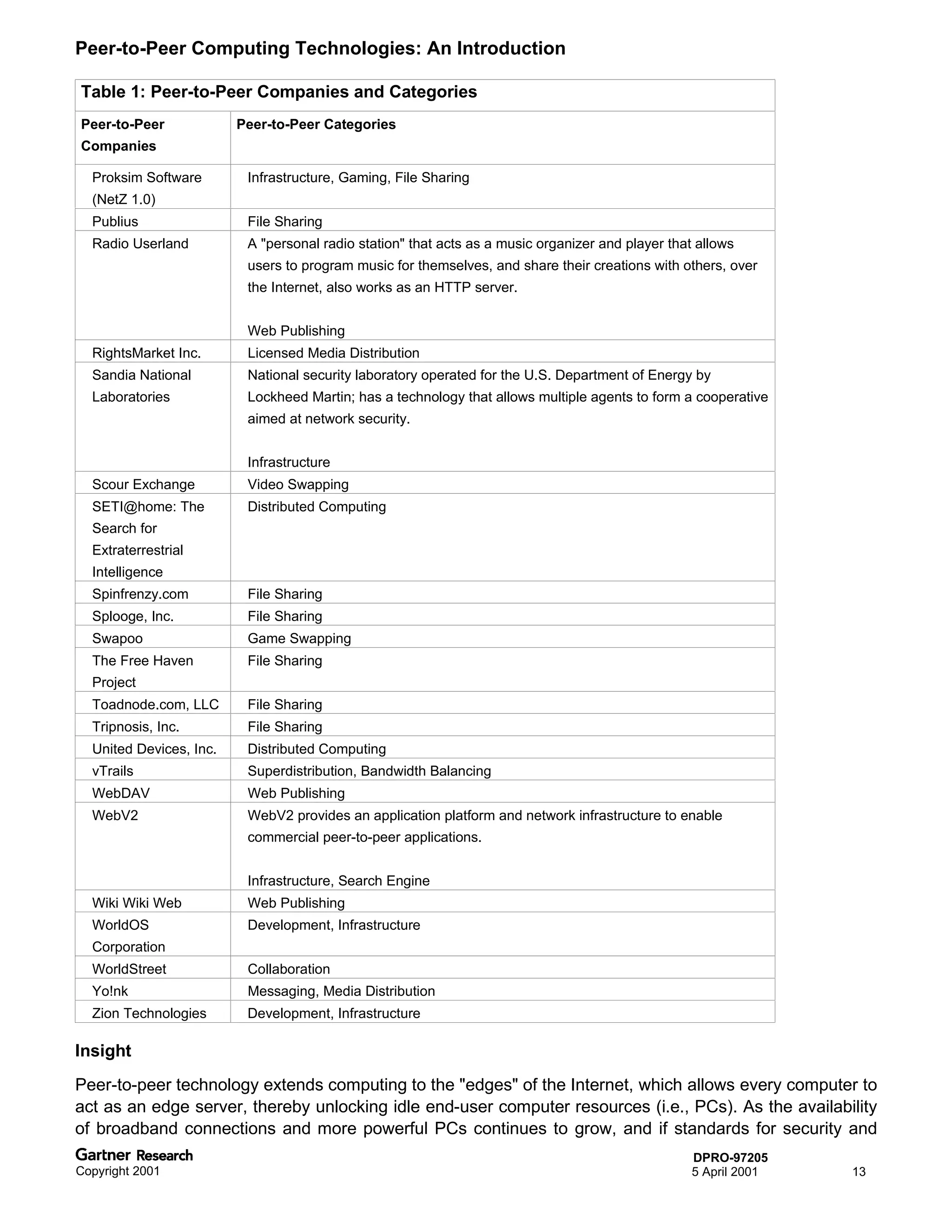
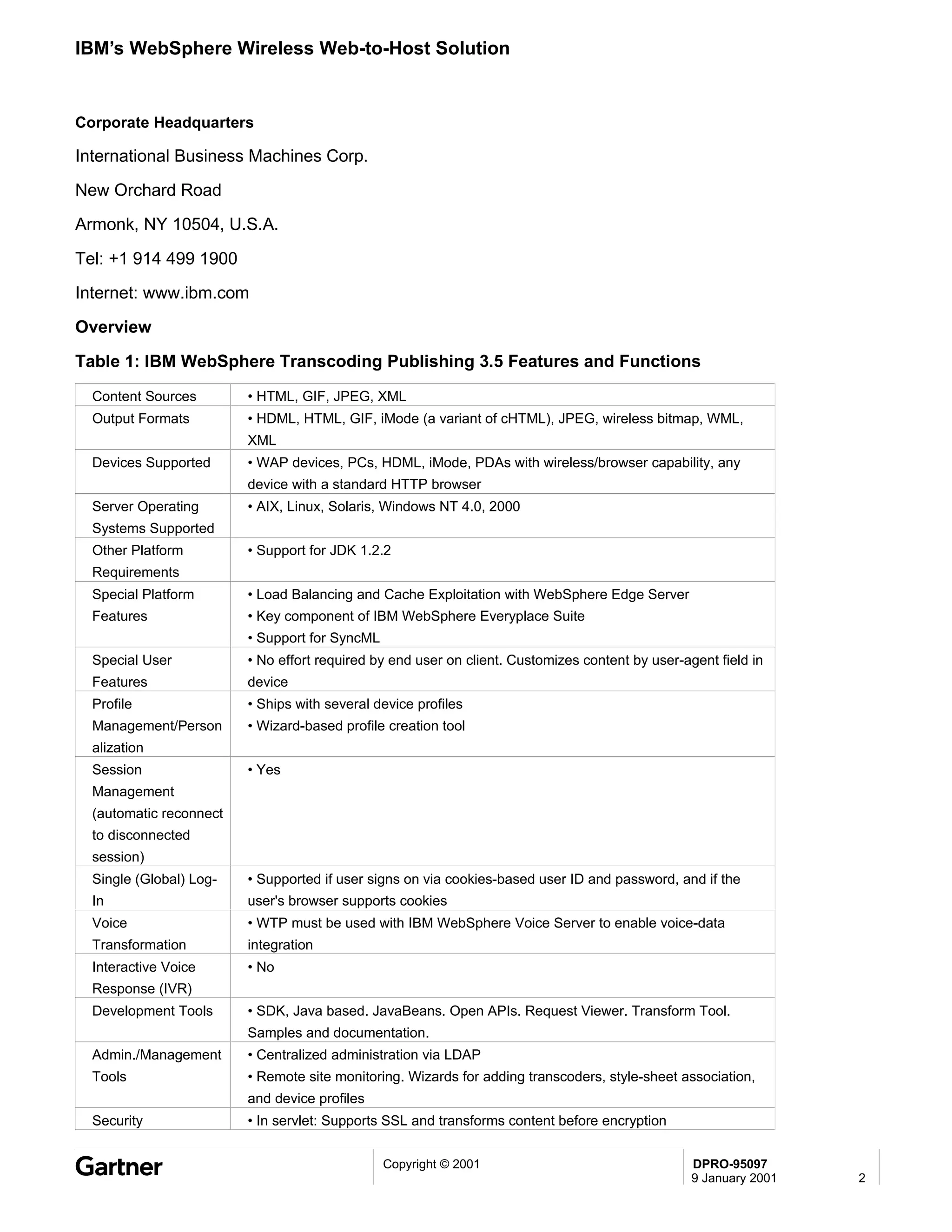
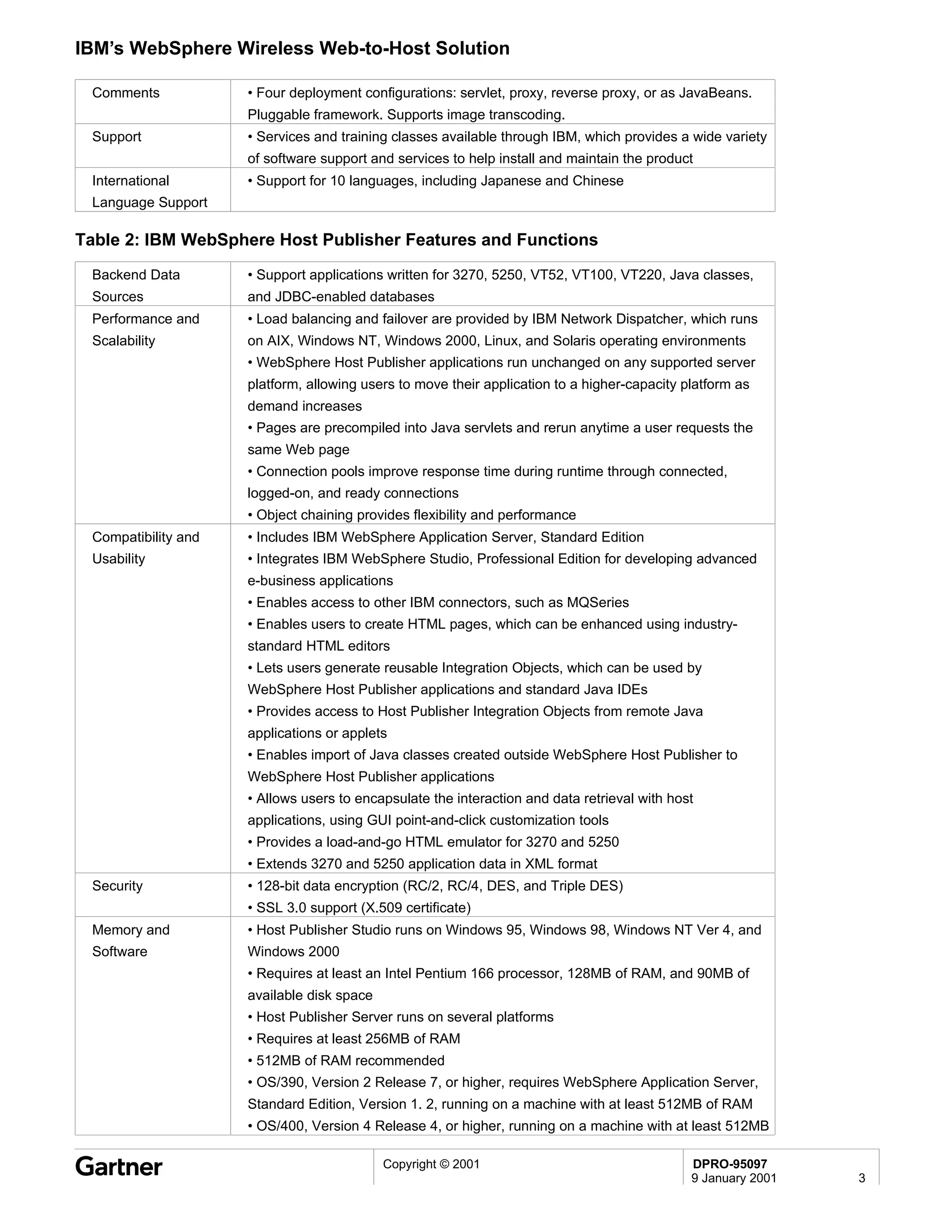
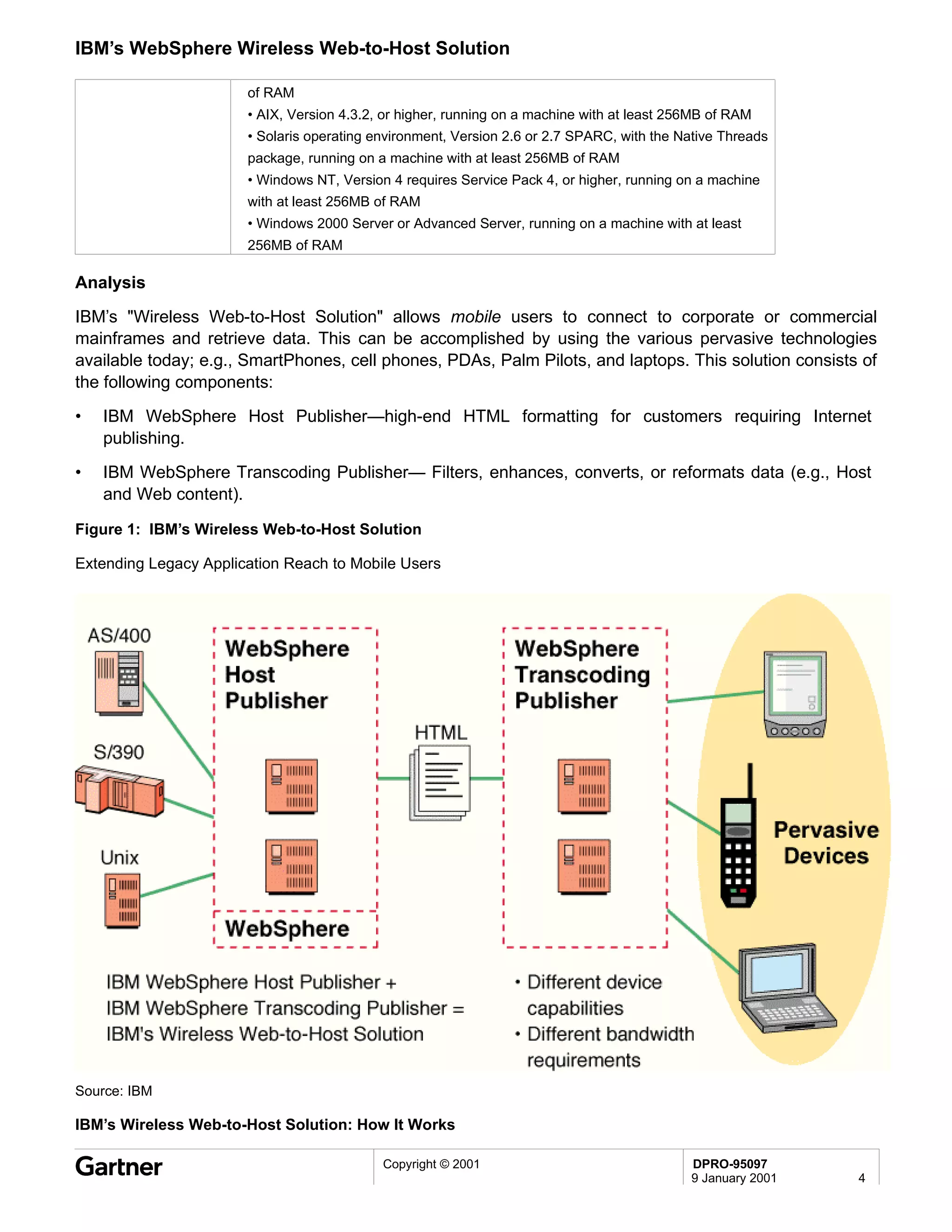
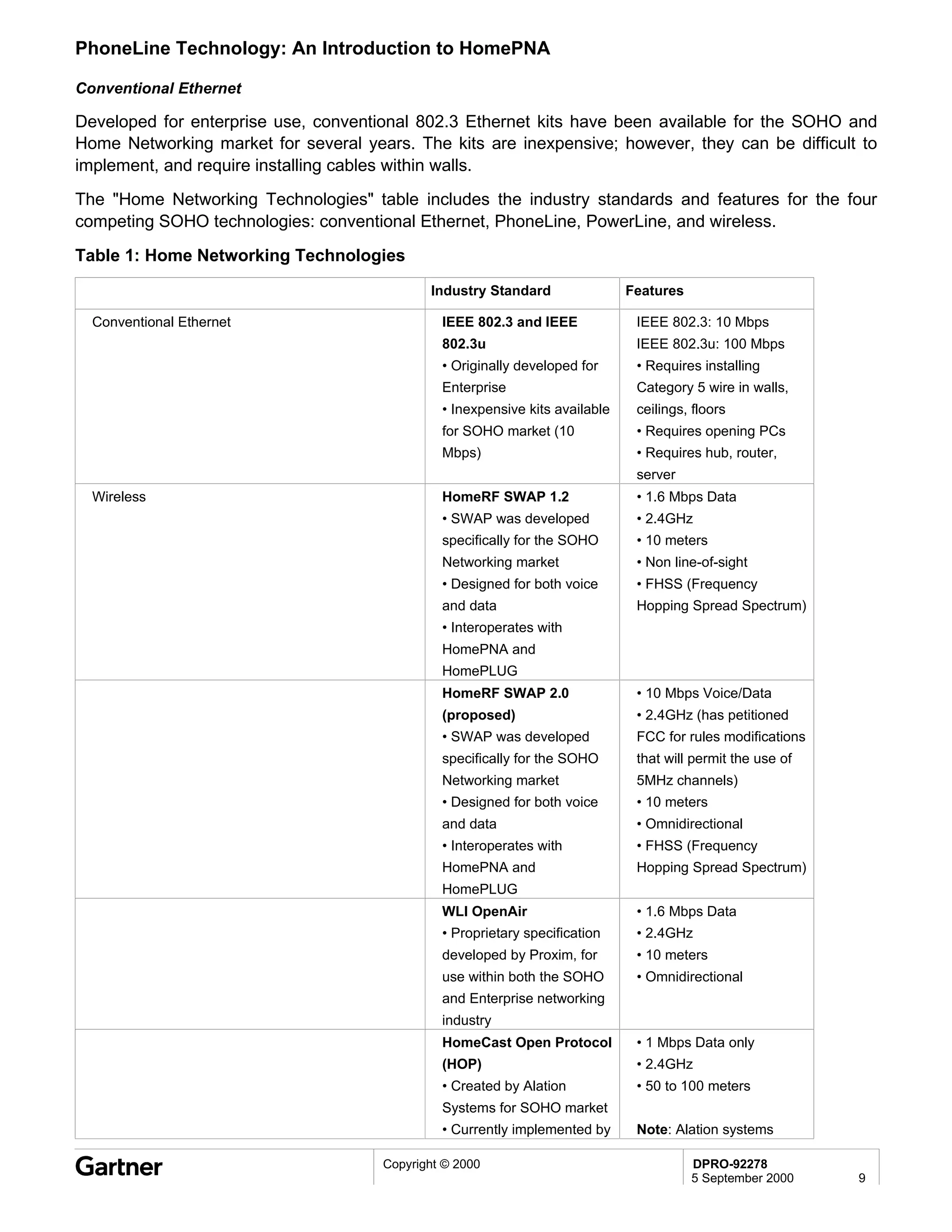
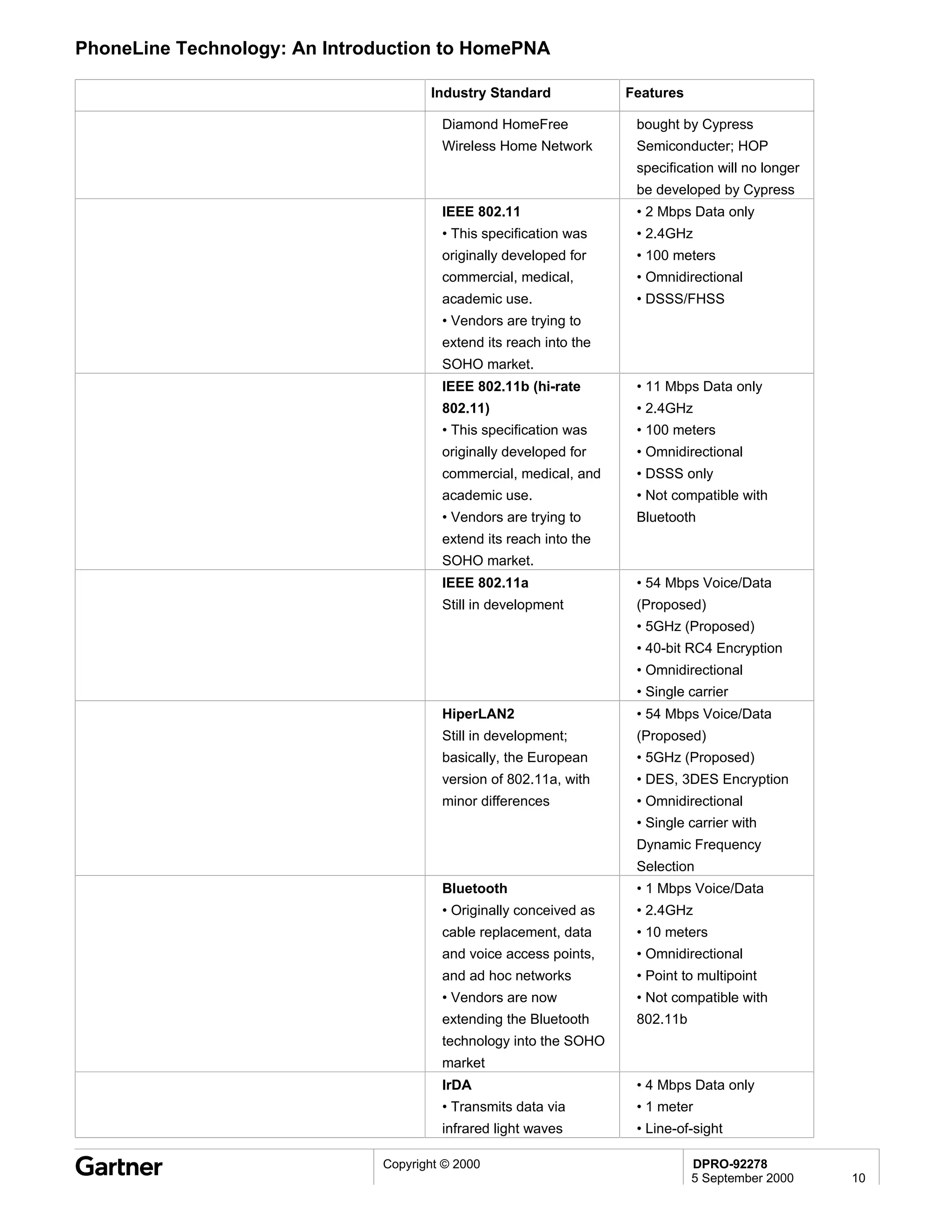
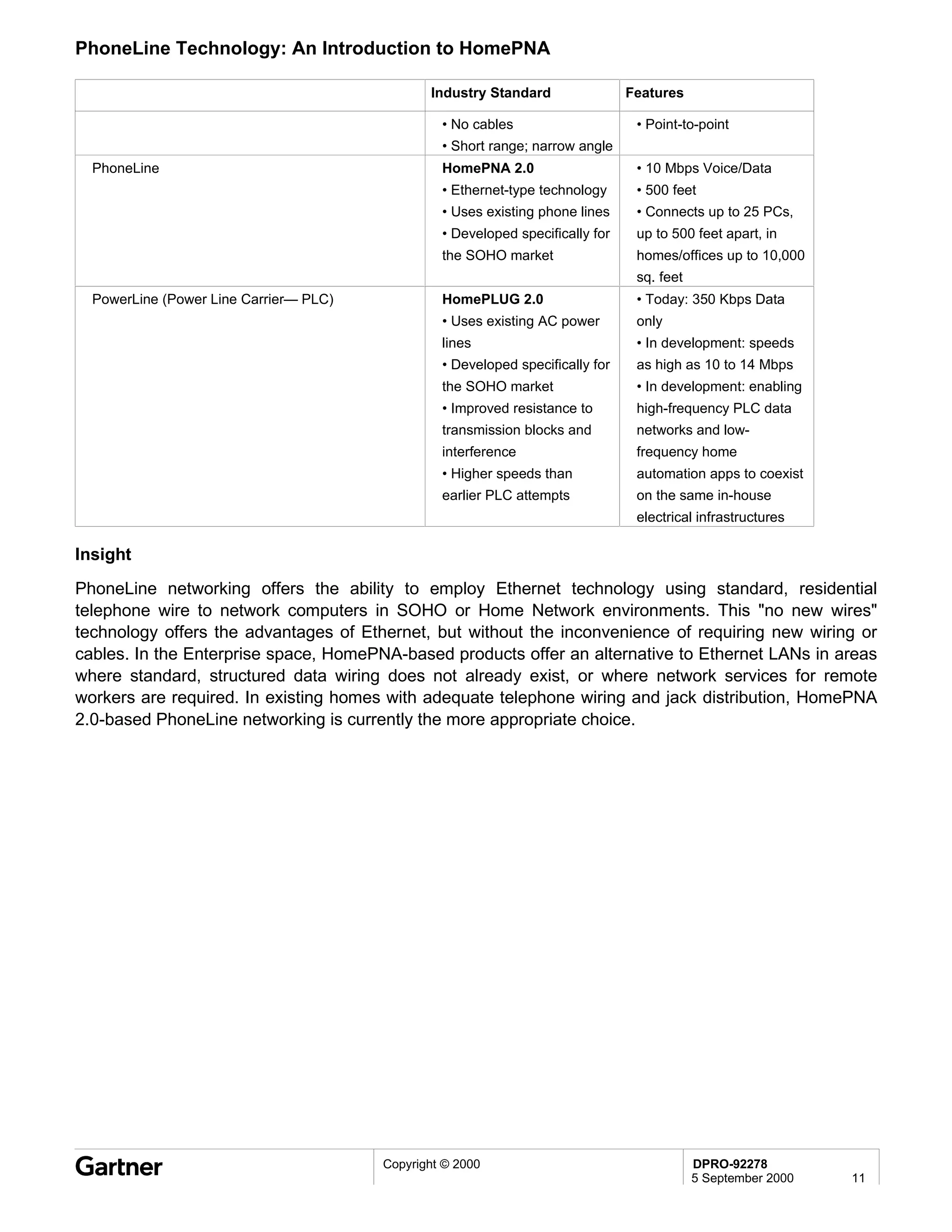
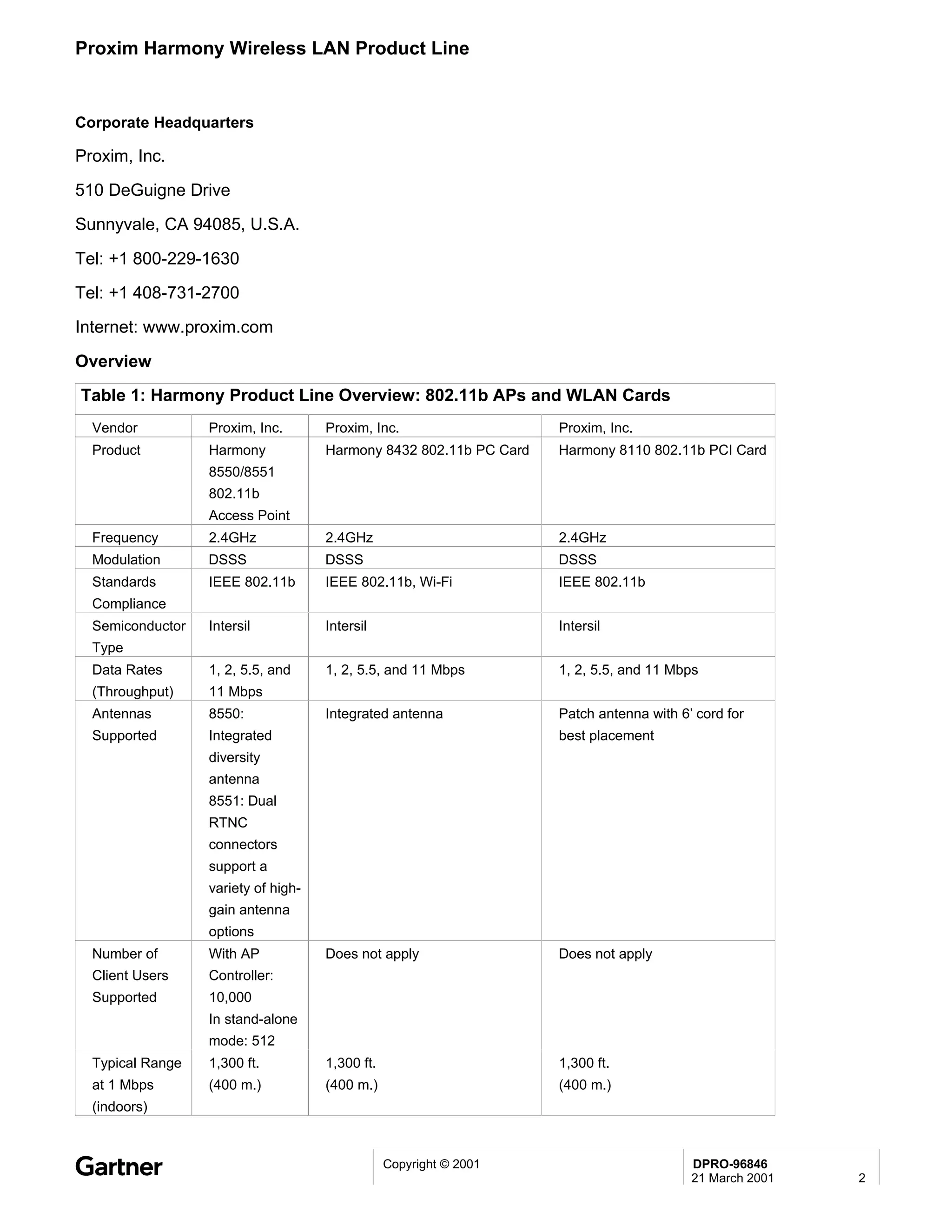
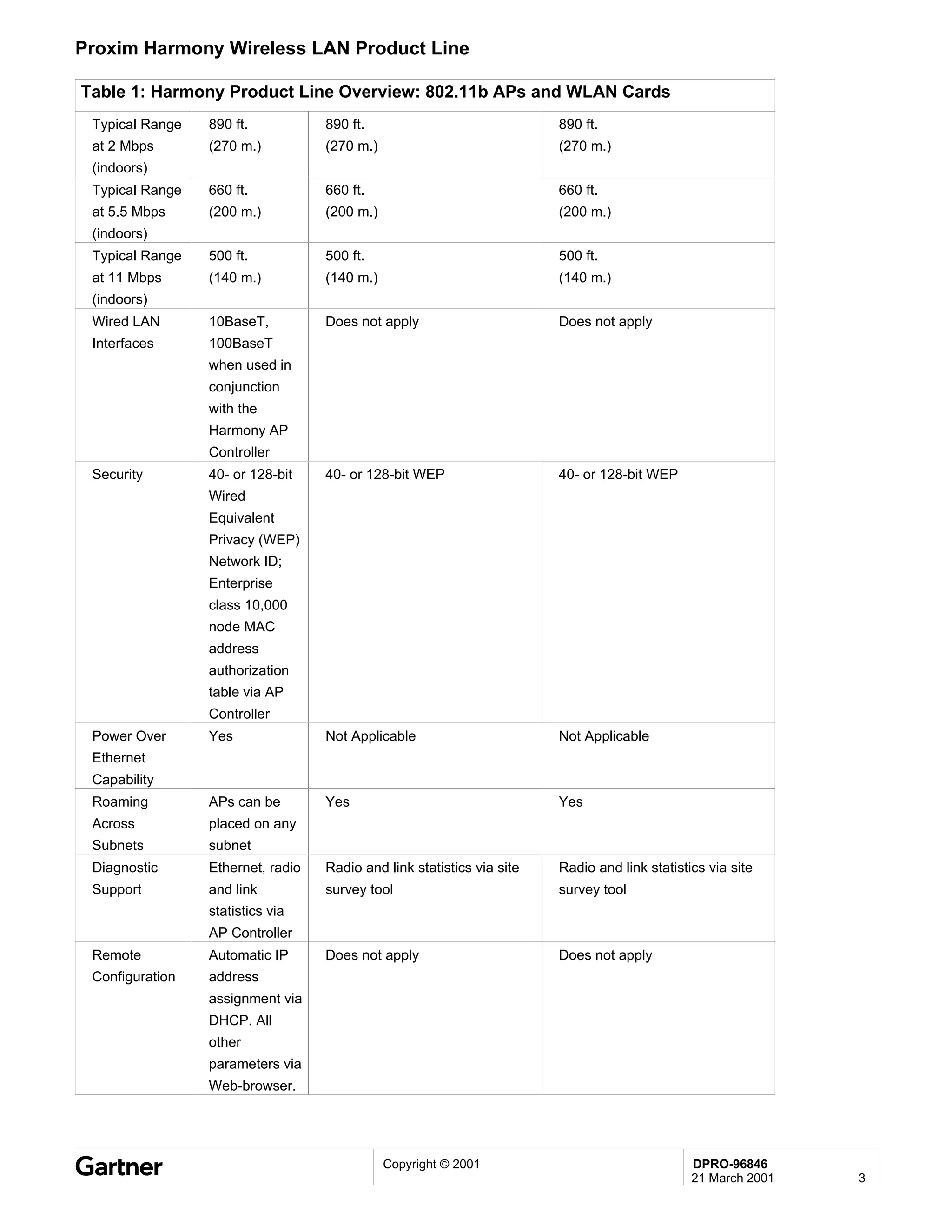
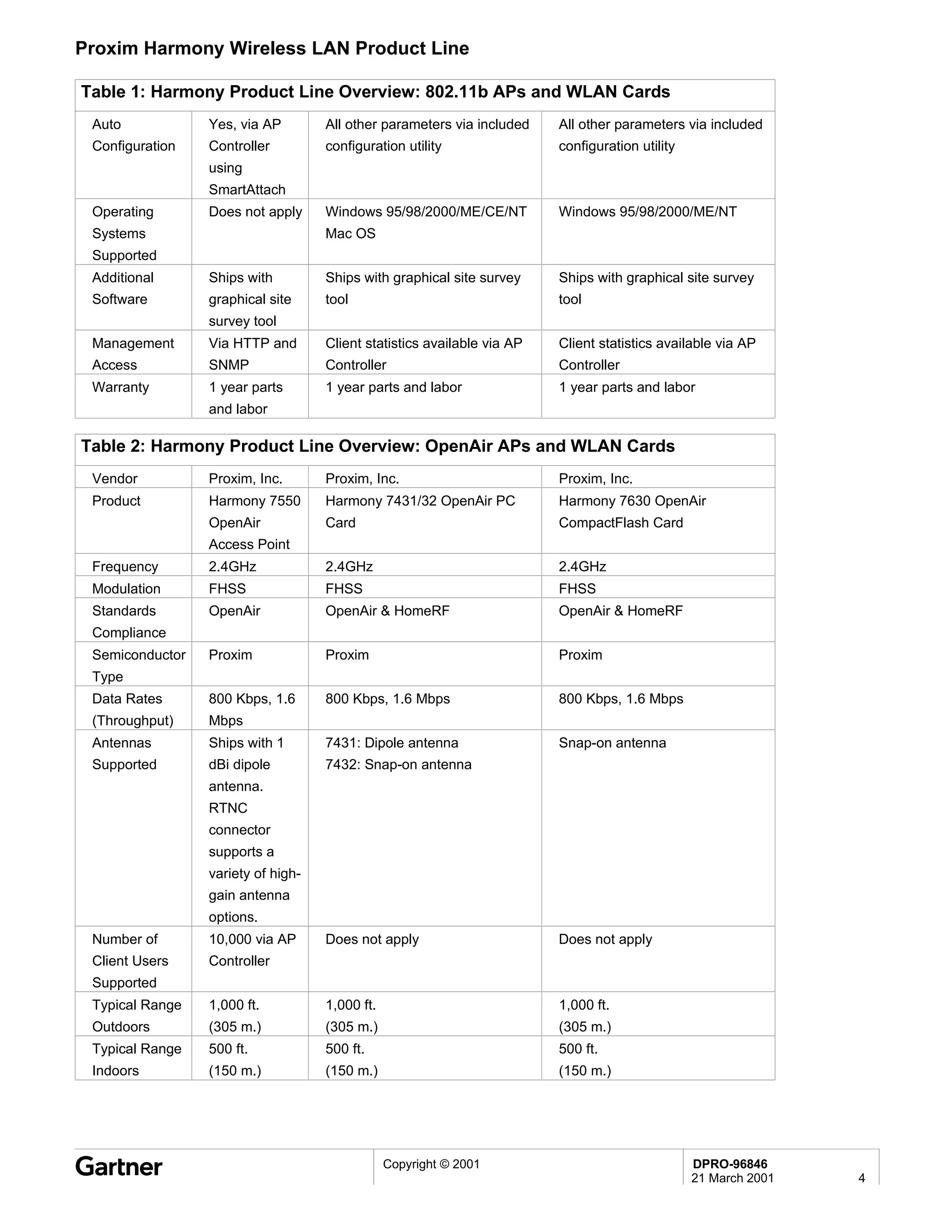
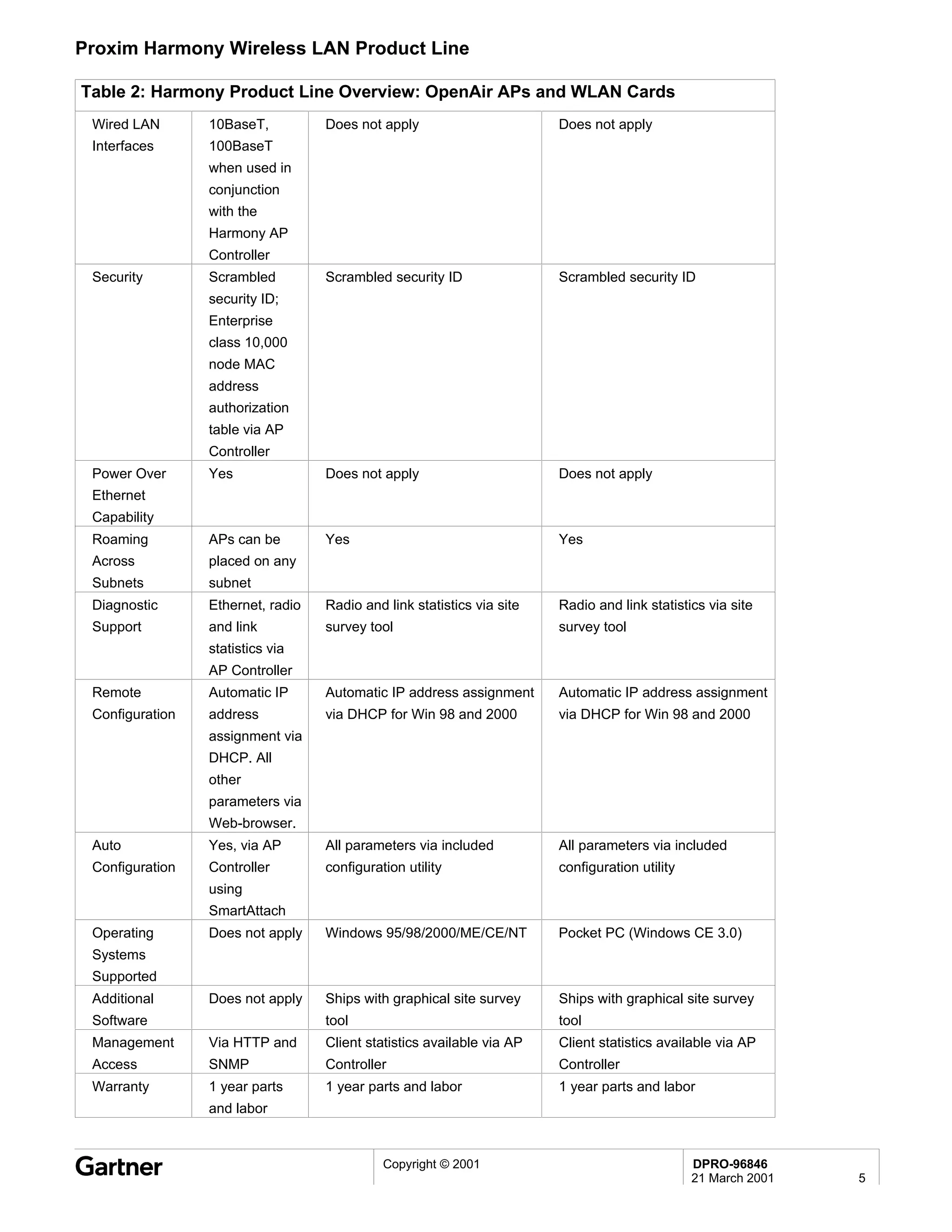
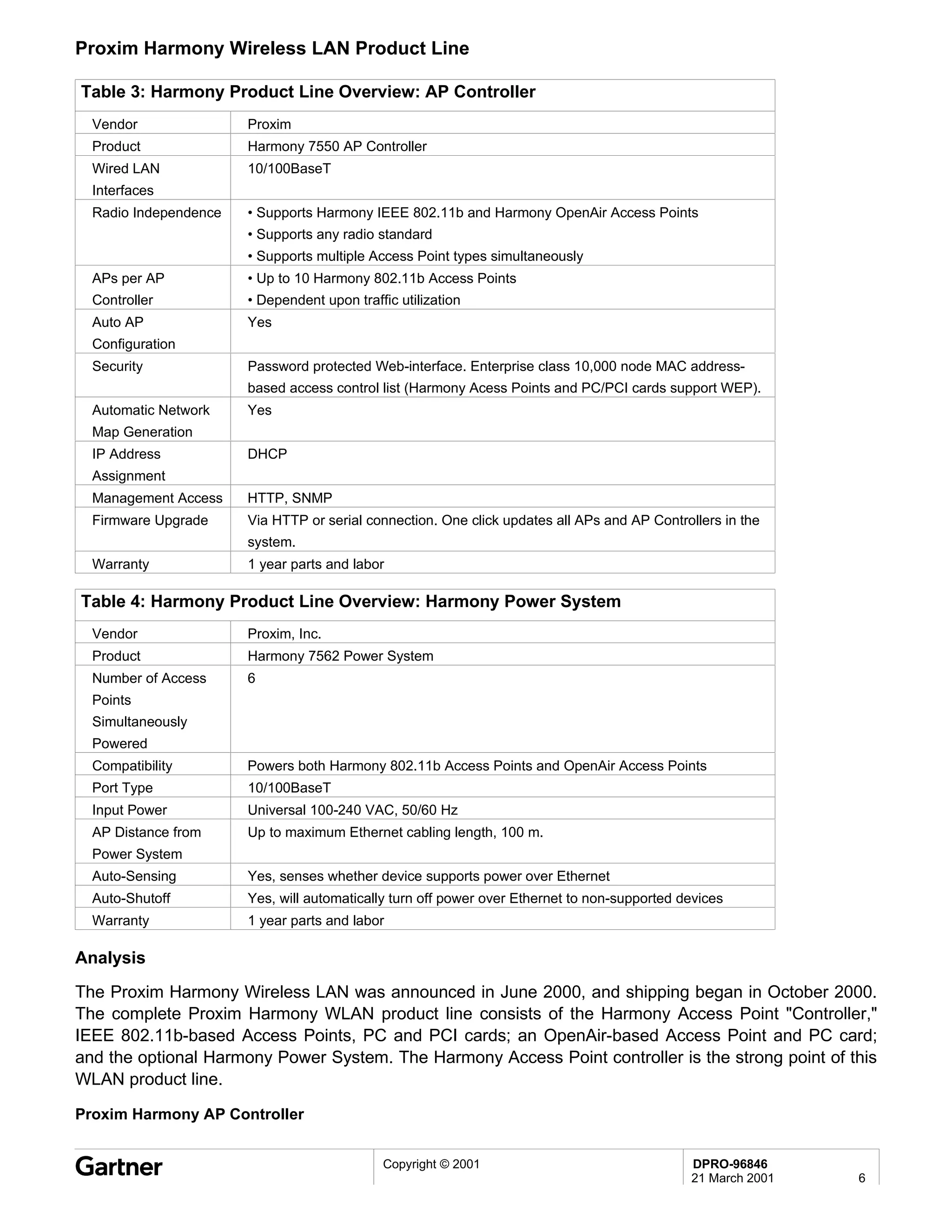
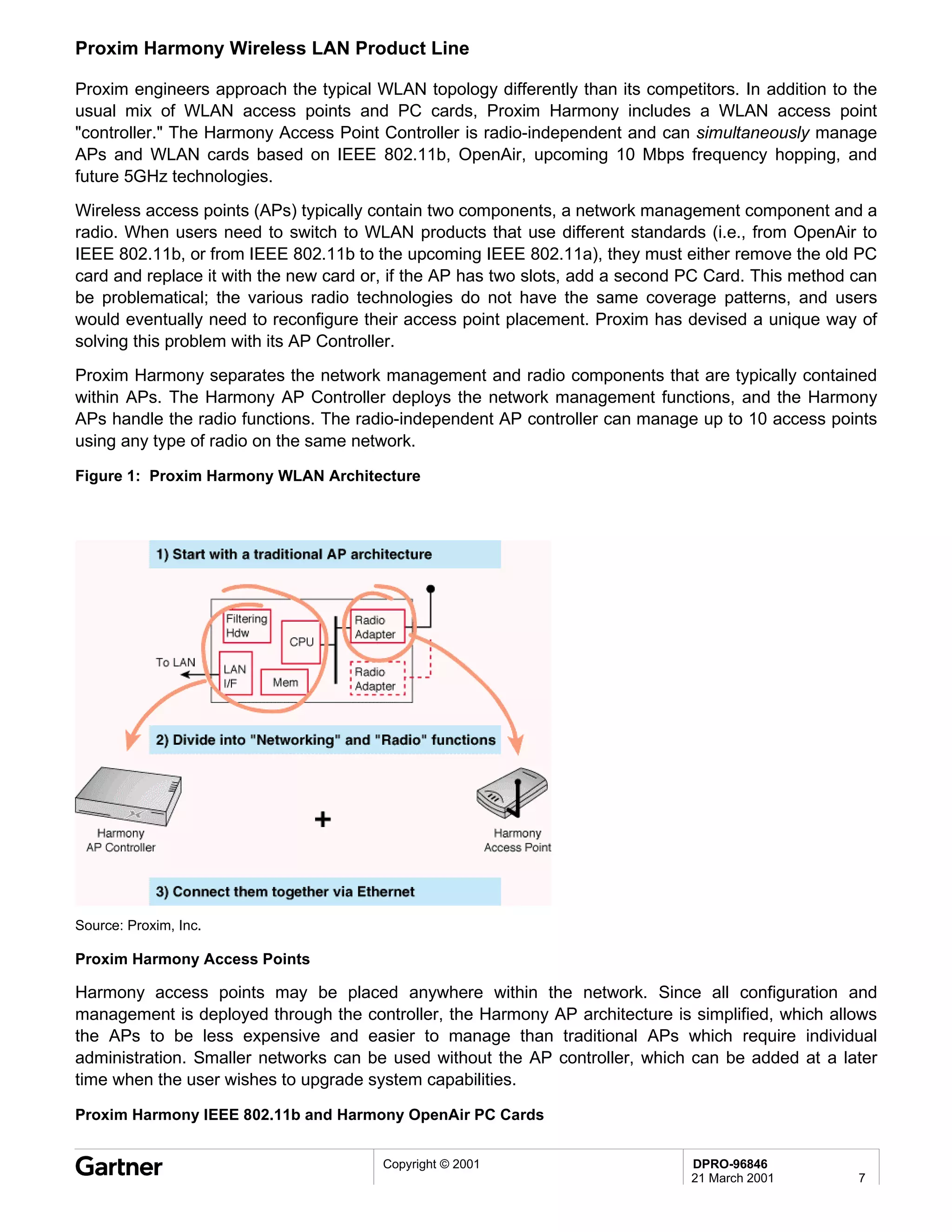
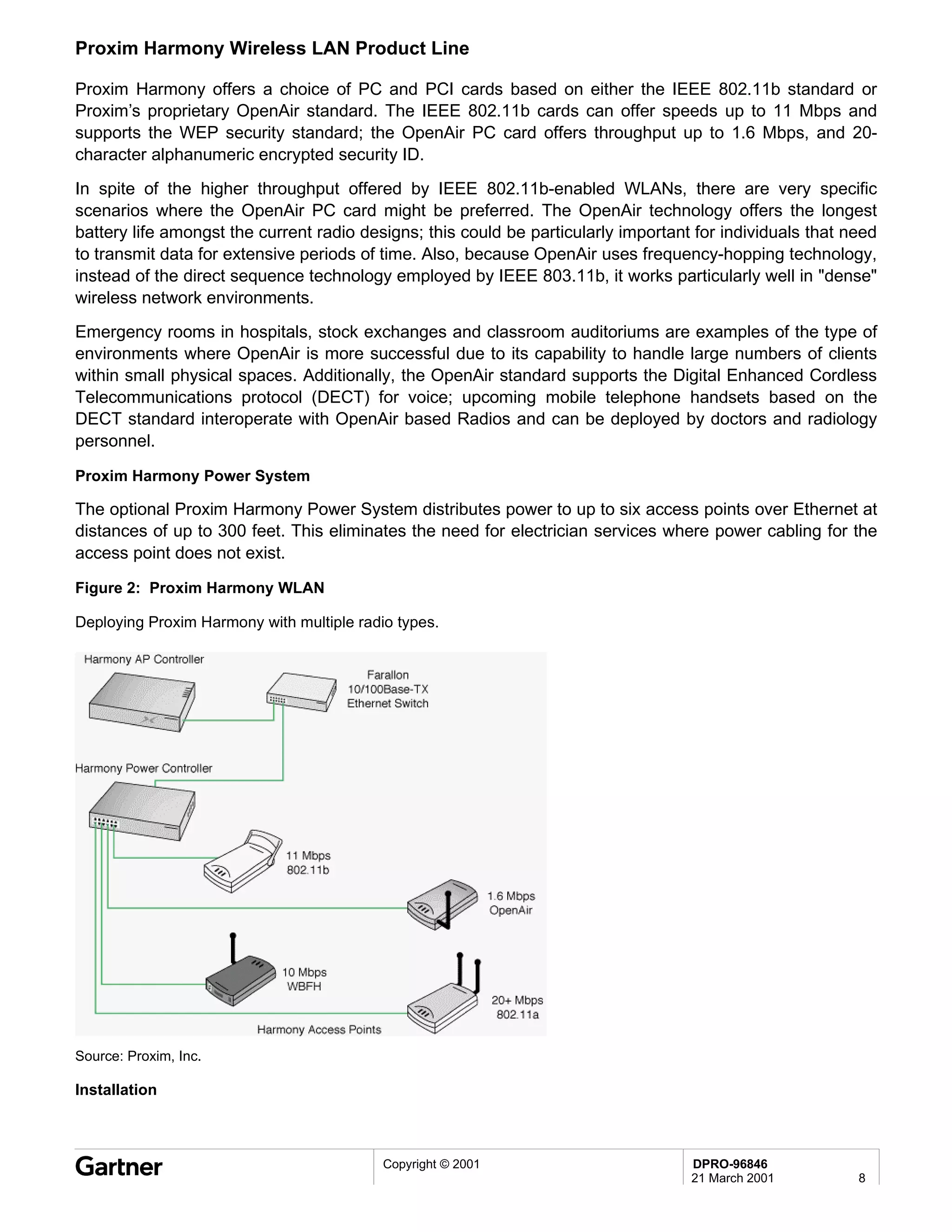
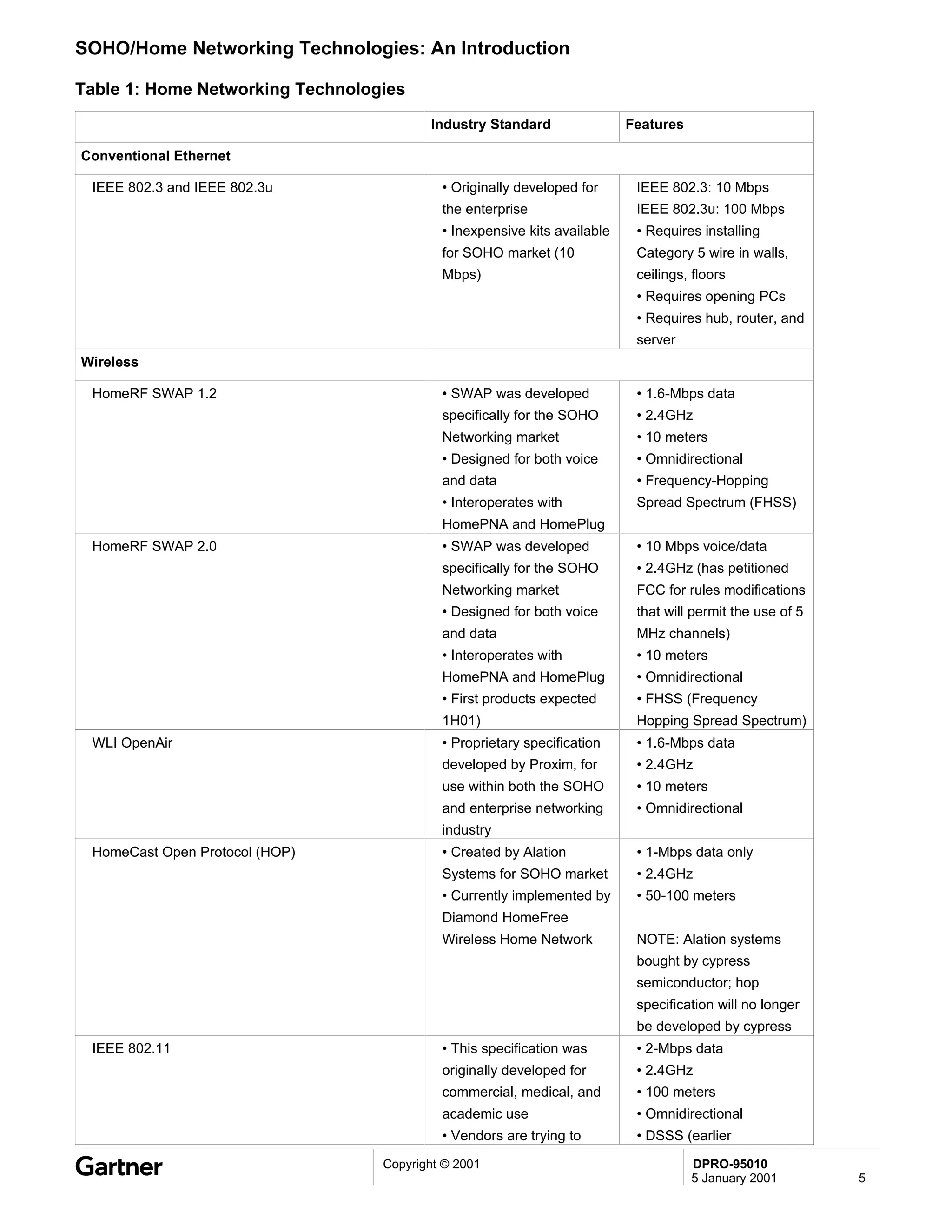
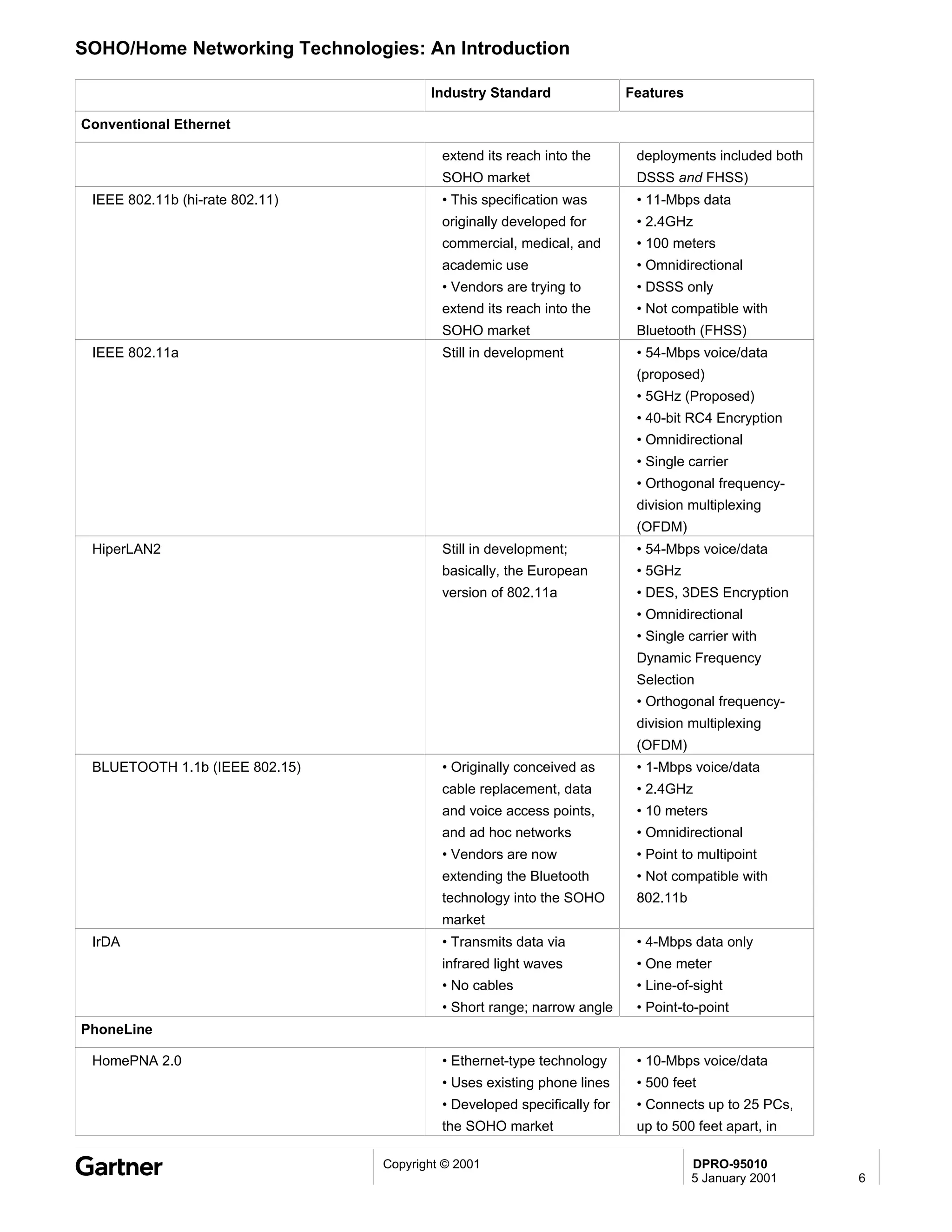
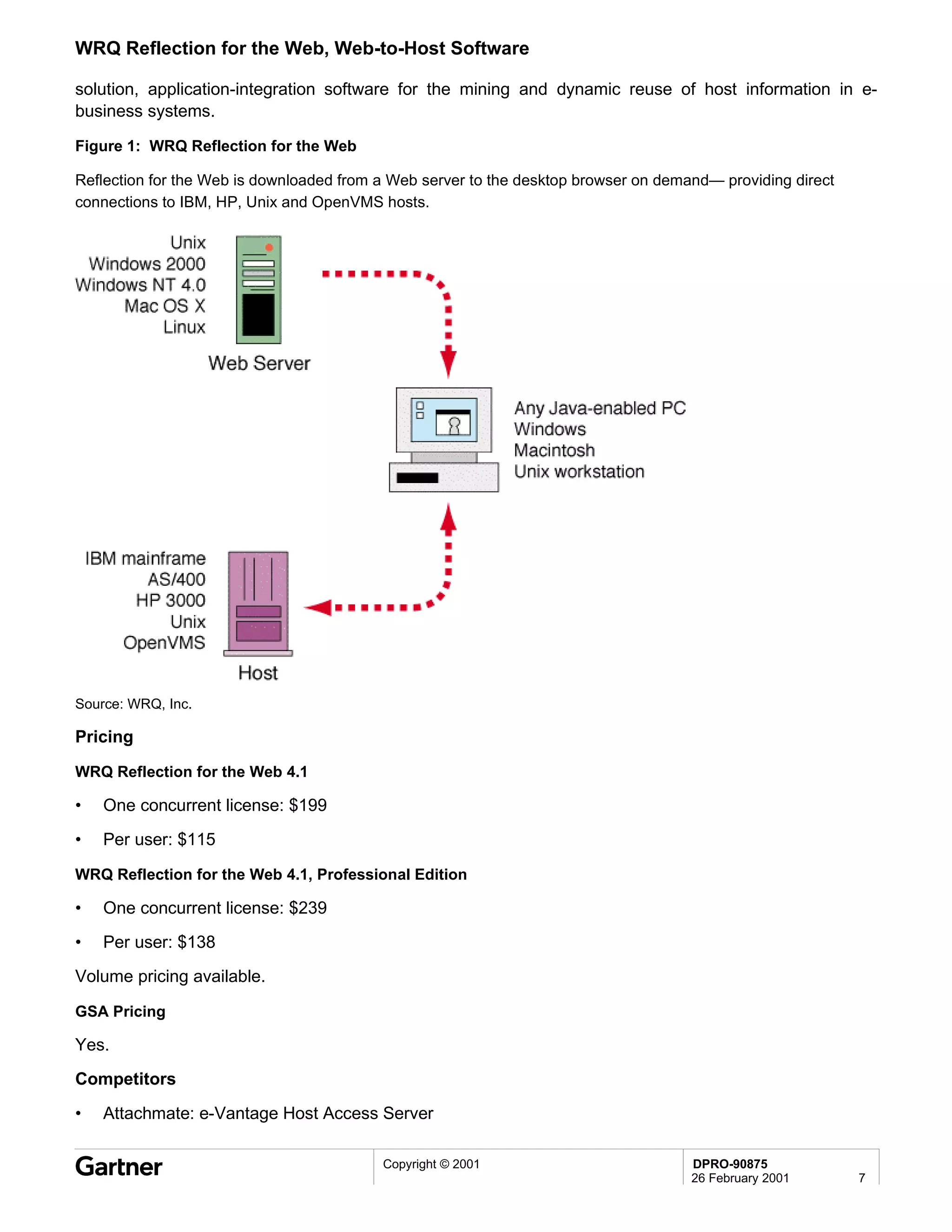
Bluetooth is a wireless technology standard that allows short-range wireless connections between devices like mobile phones, laptops, printers, and other electronics. The document provides an overview of Bluetooth including its history, how it works using frequency-hopping spread spectrum in the 2.4GHz band, supporting up to 10 meters of range. It discusses Bluetooth components, security modes, early slow product rollout, and potential business uses and benefits like replacing cables and wireless file sharing. Standards bodies like the Bluetooth SIG and key technology leaders are also mentioned.