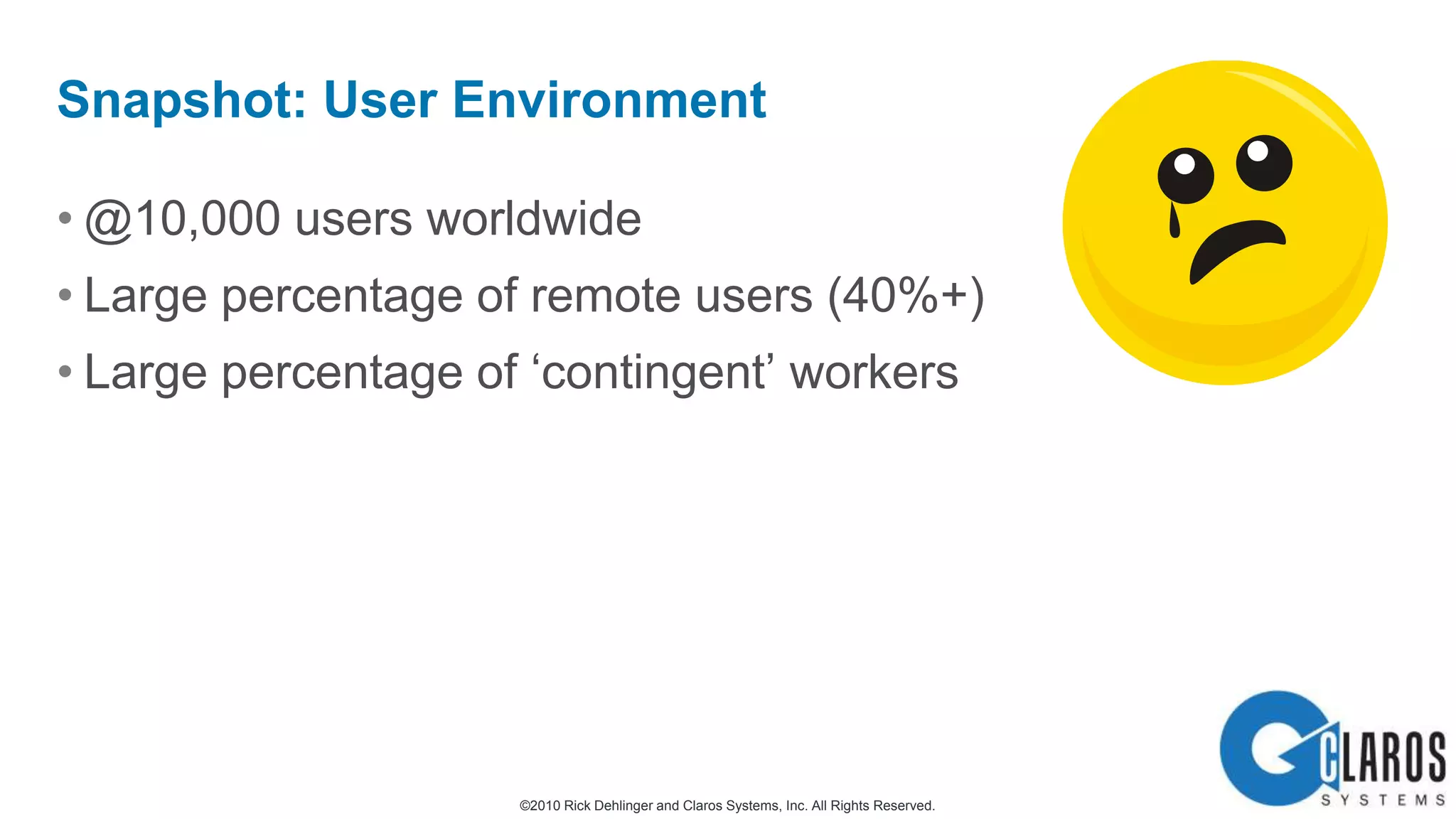
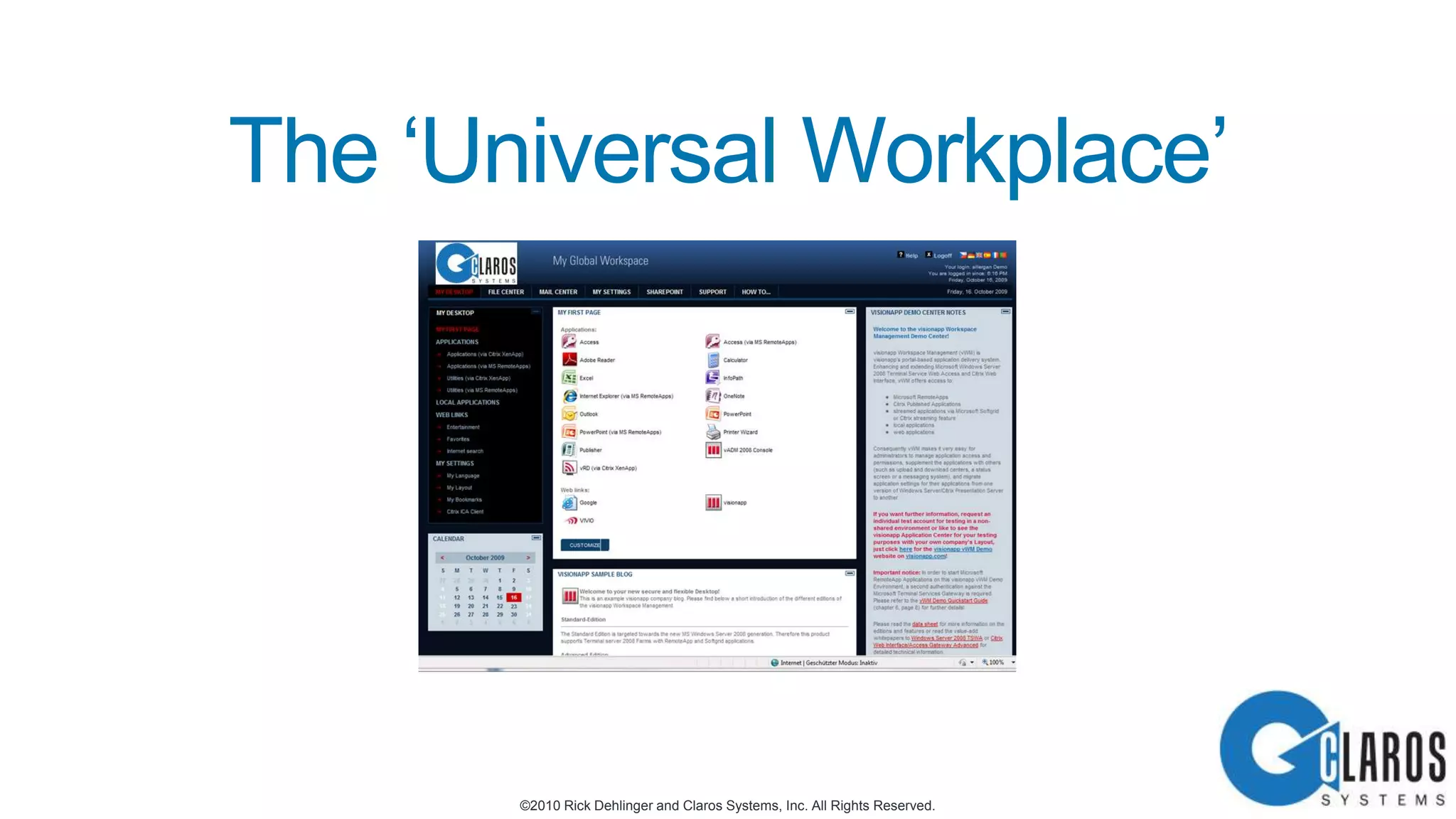
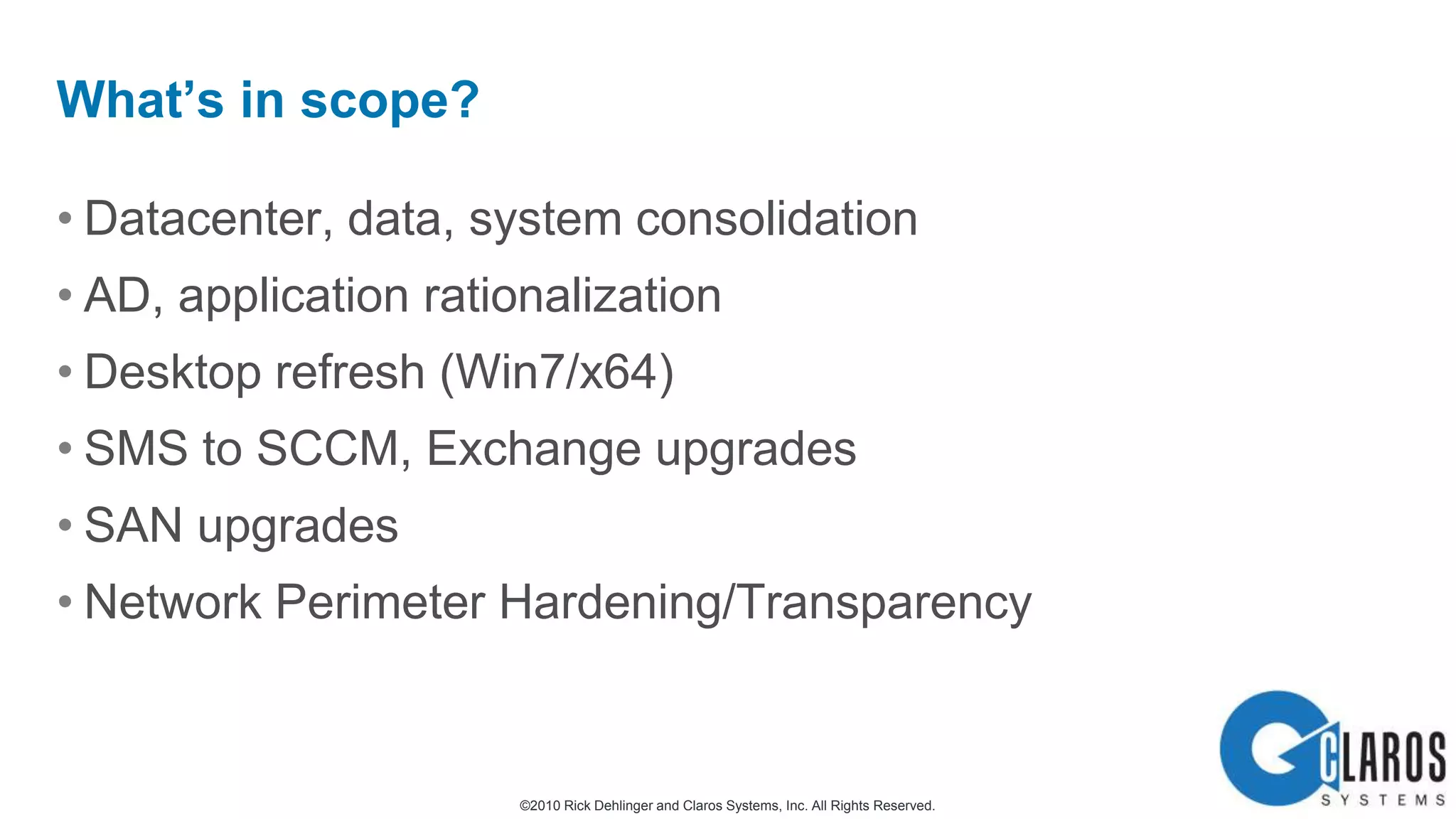
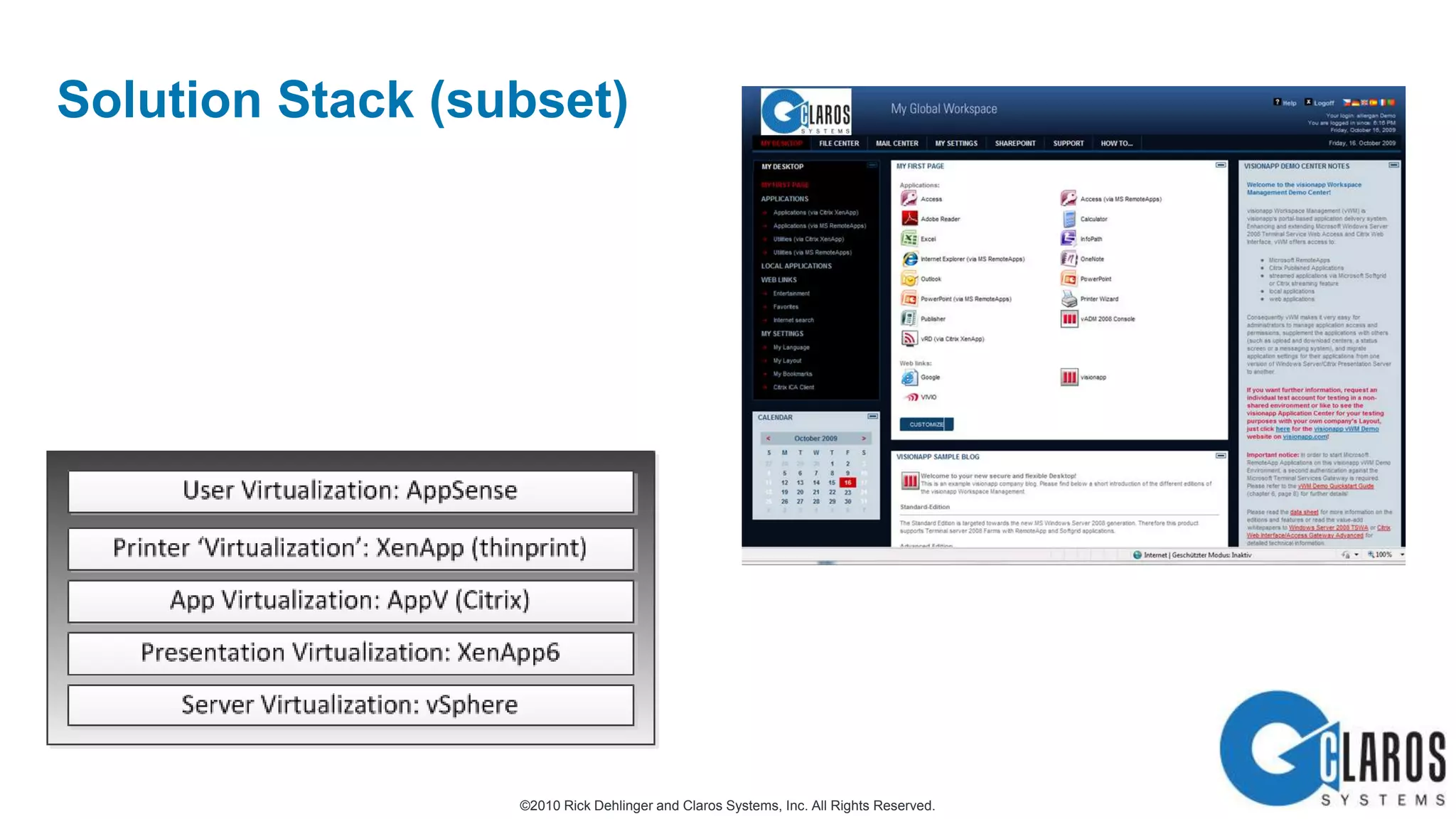
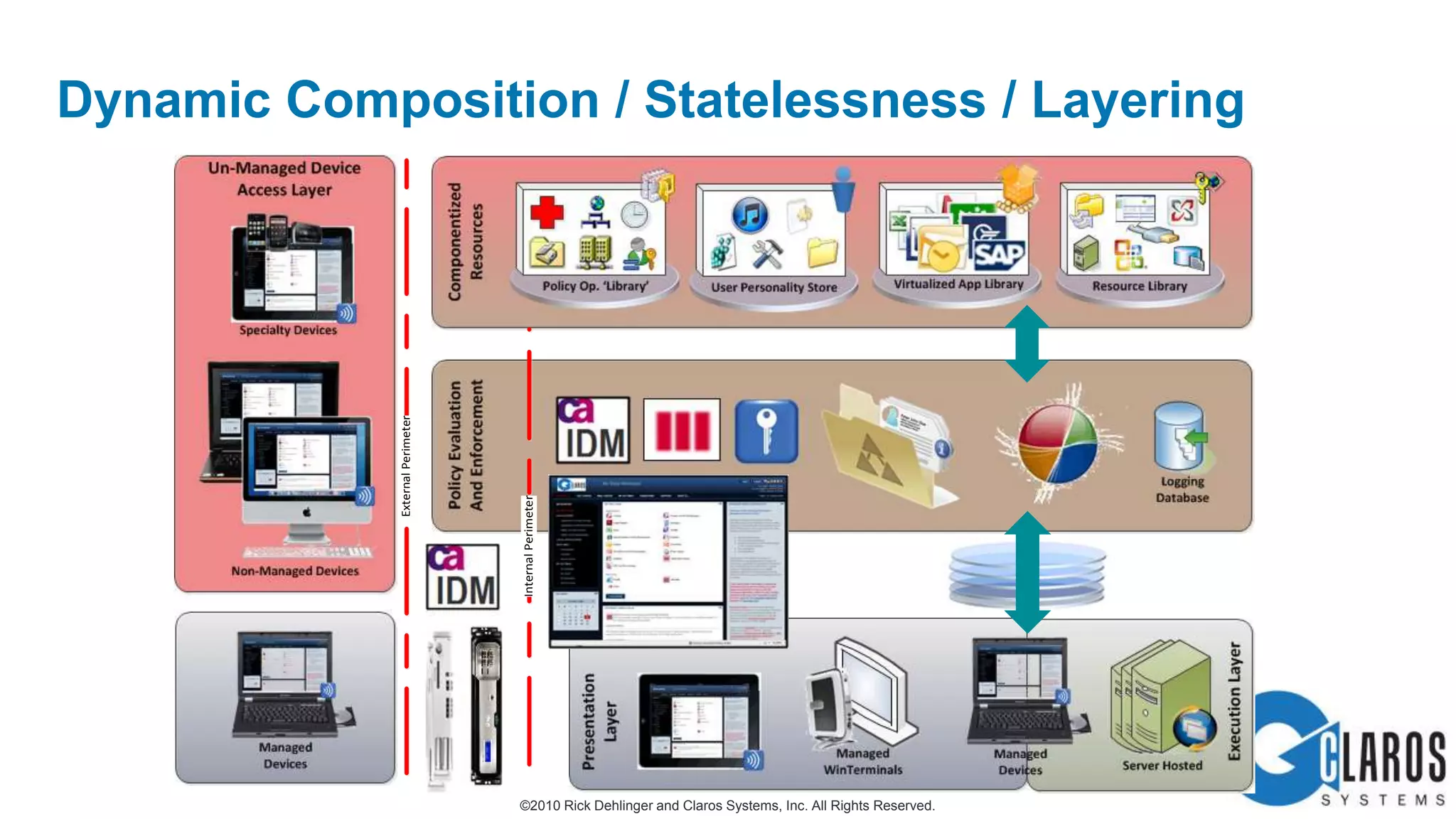
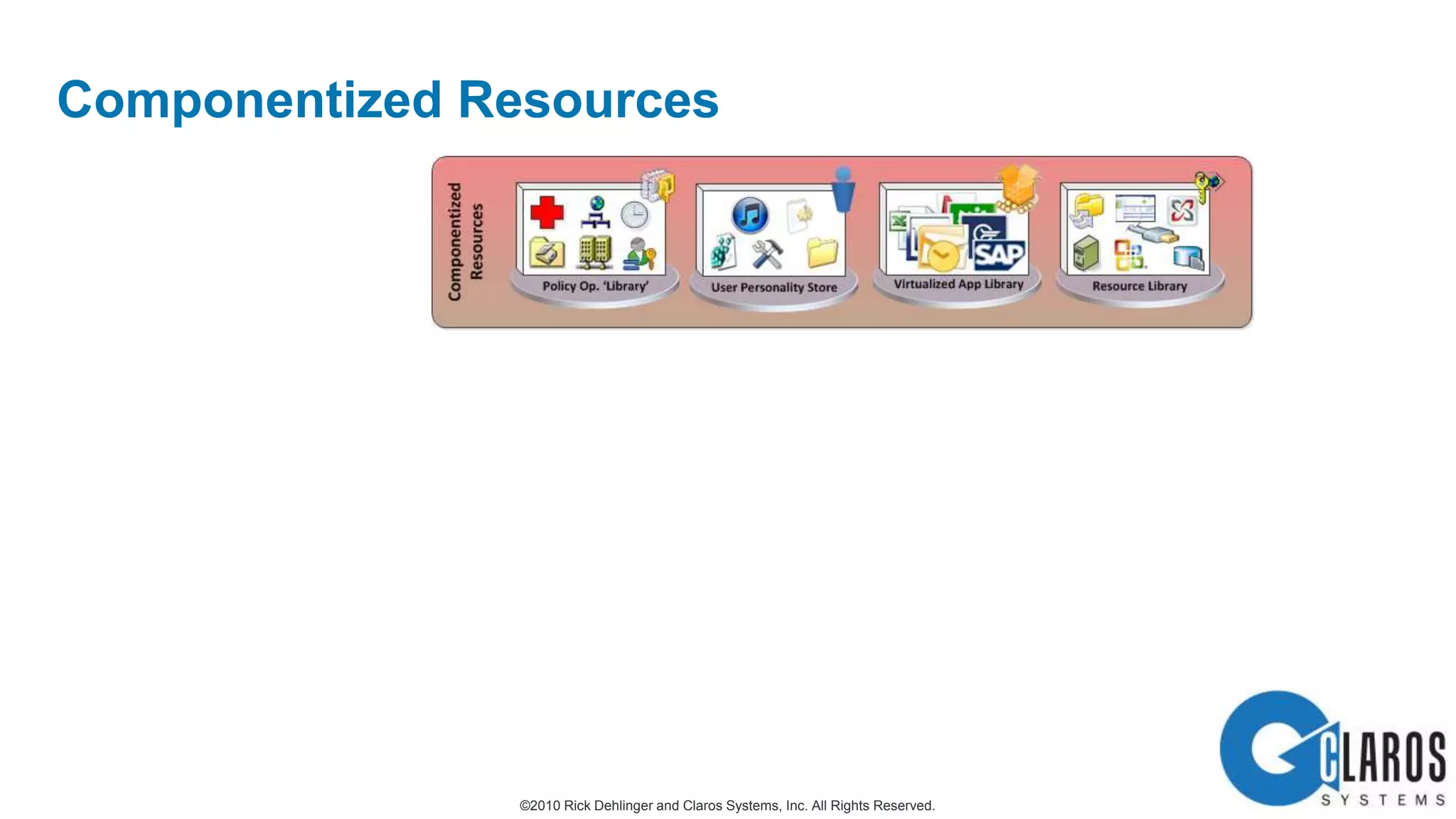
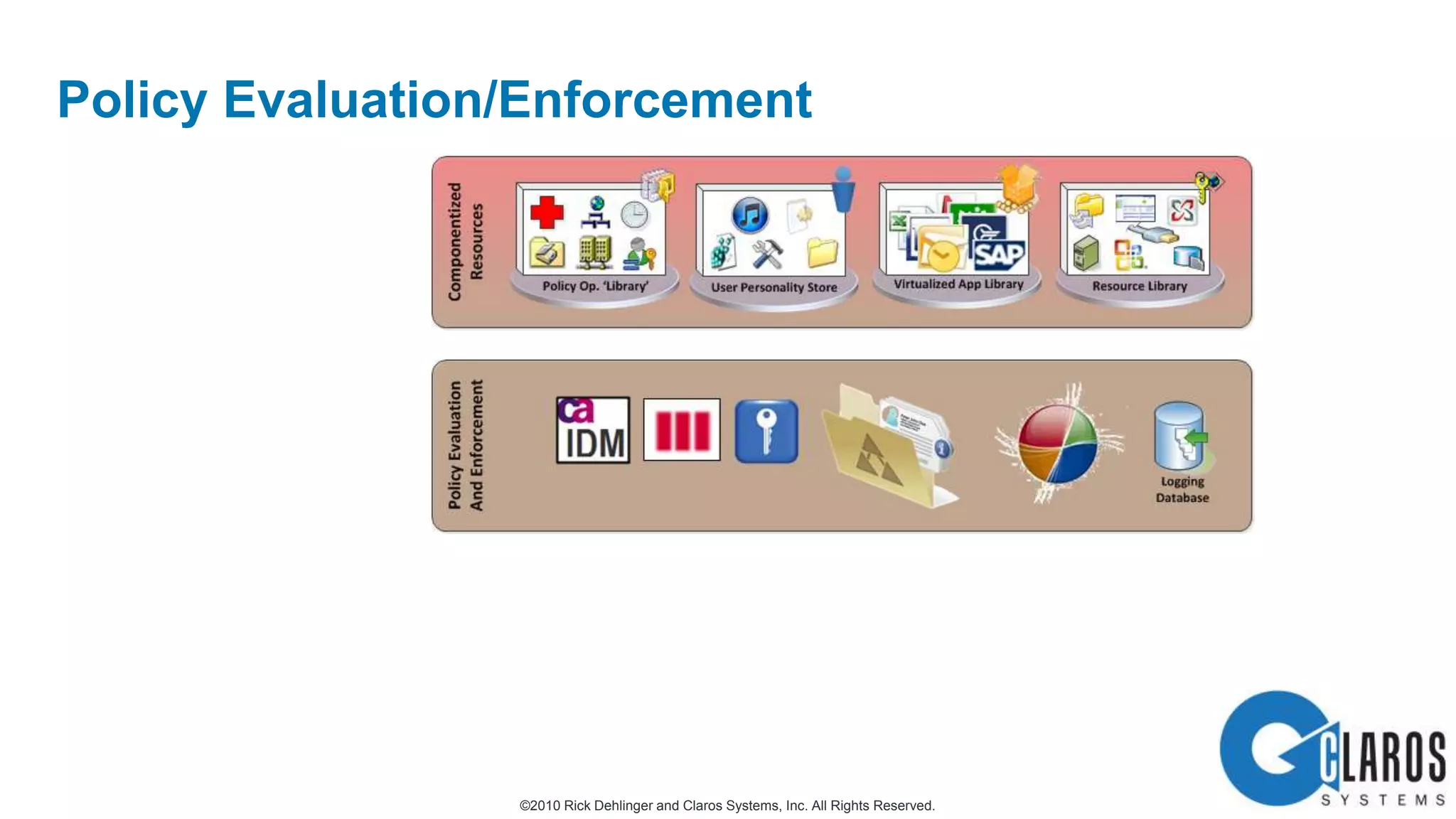
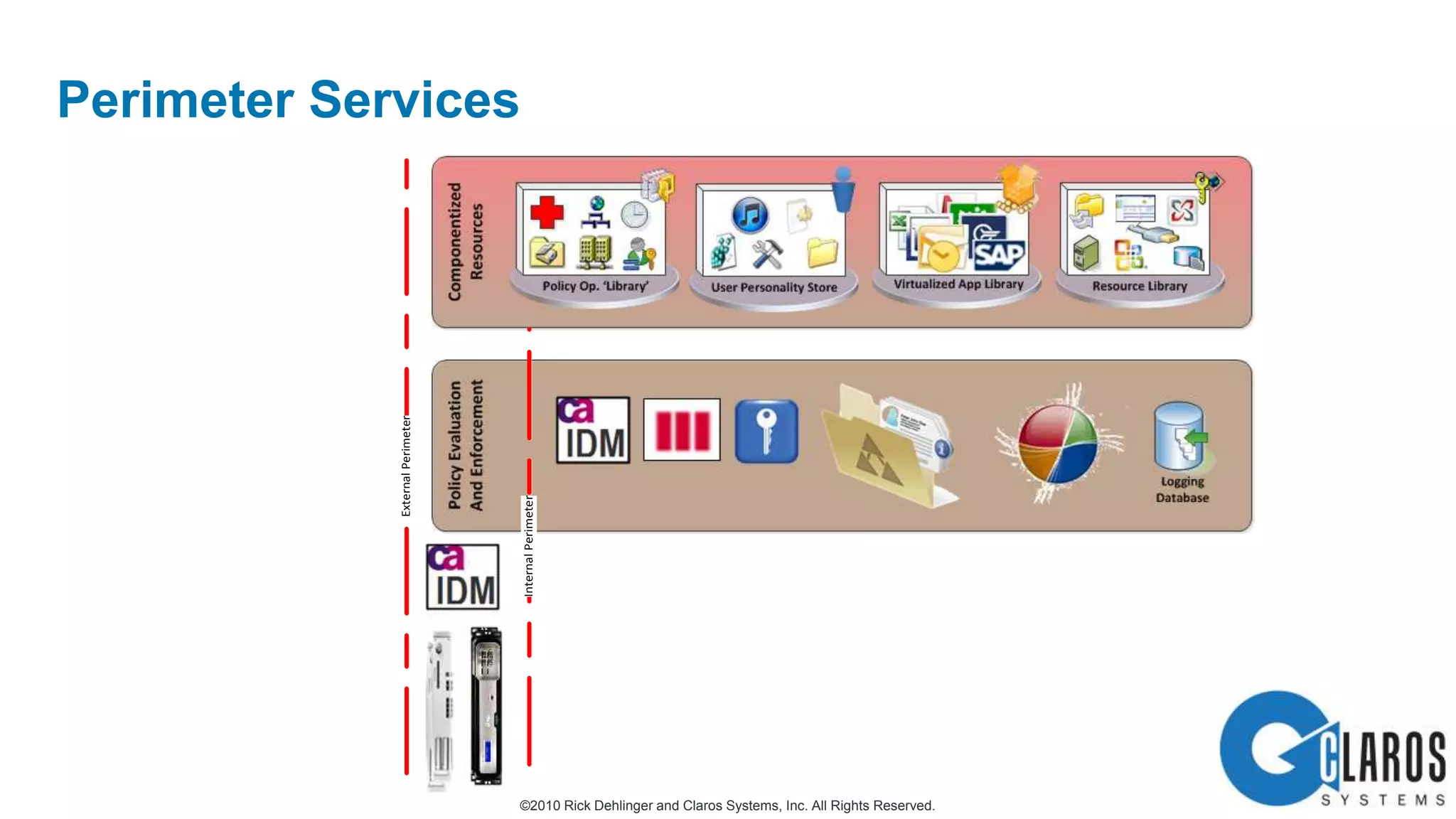
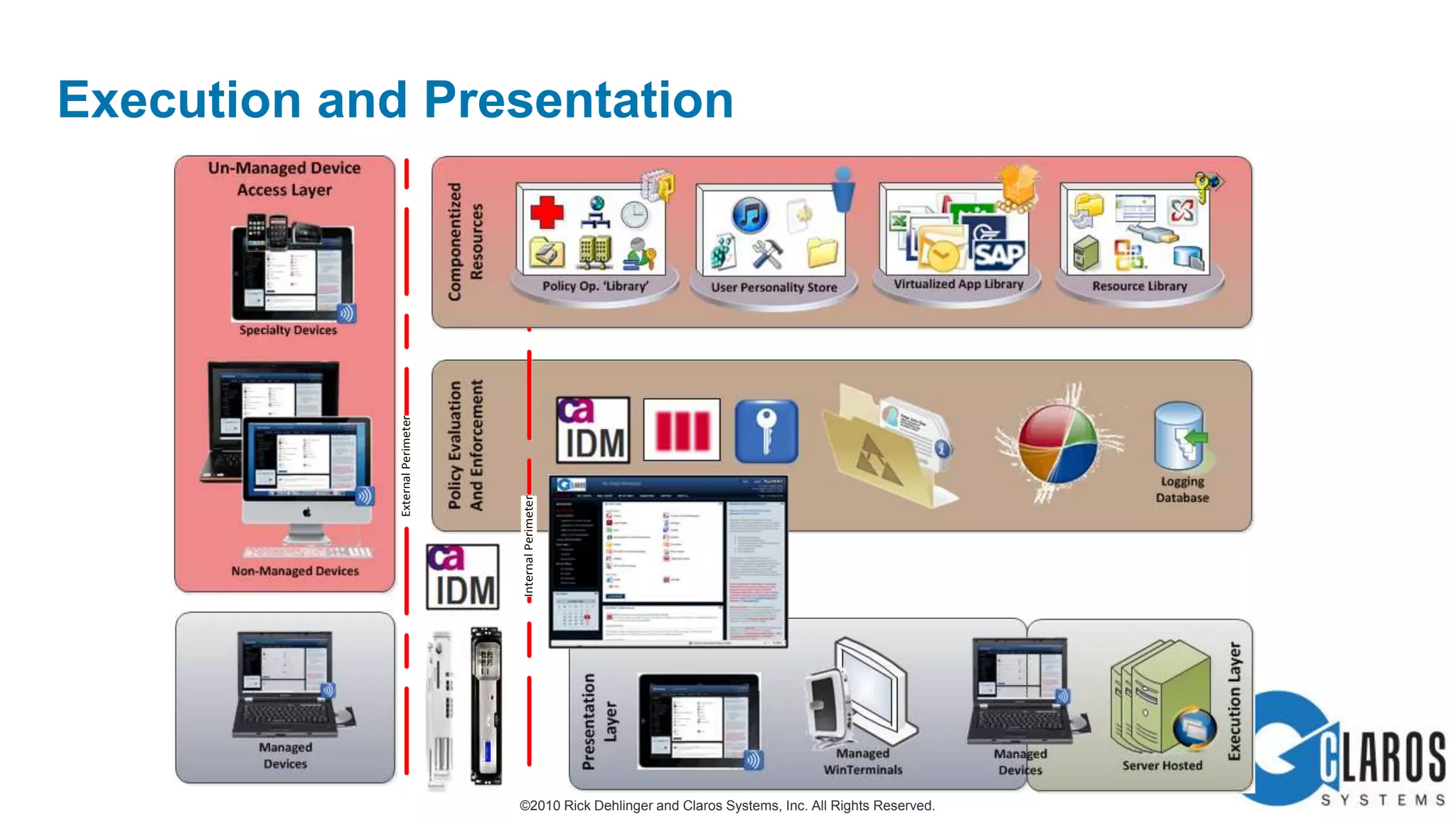
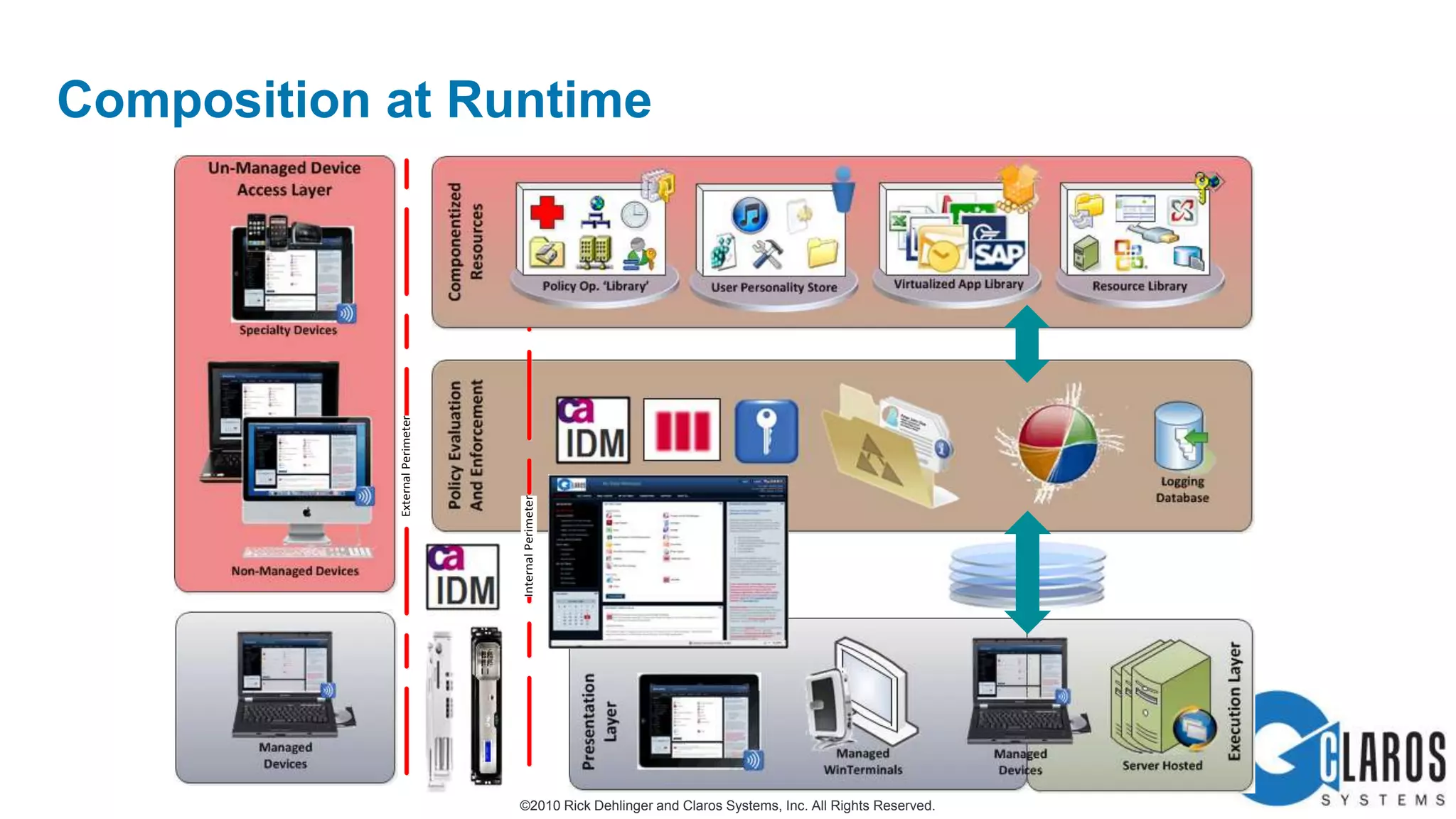
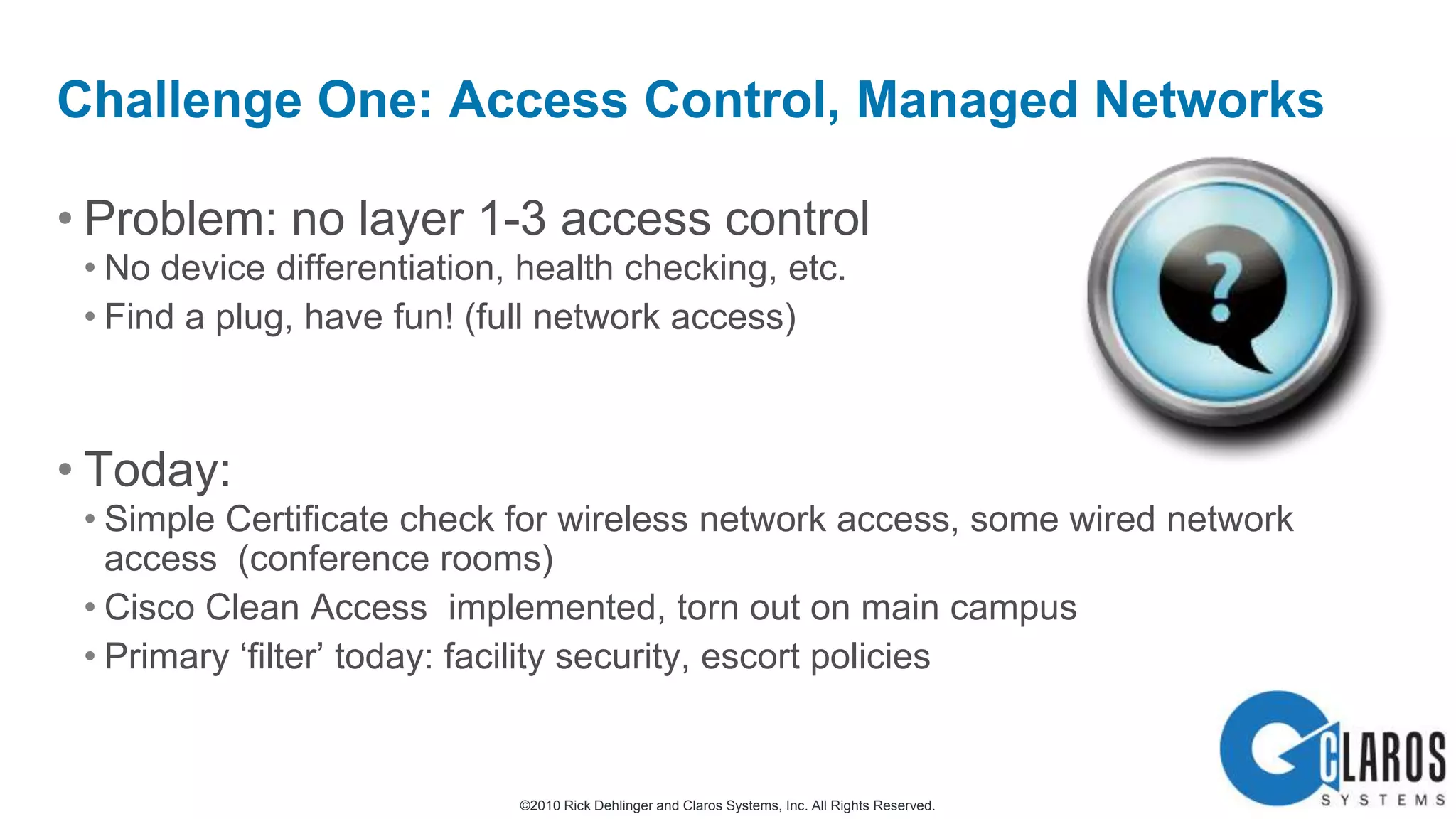
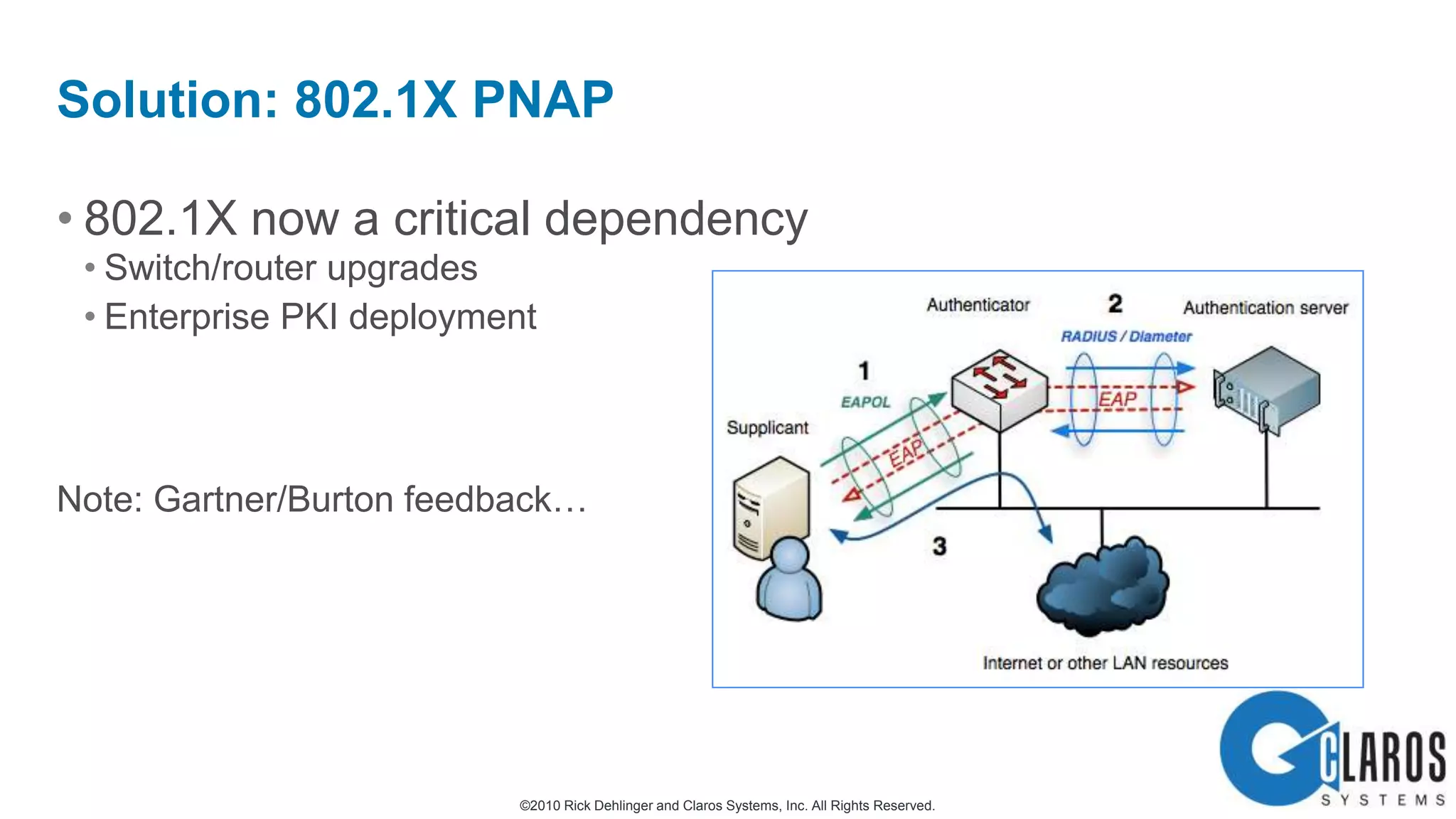
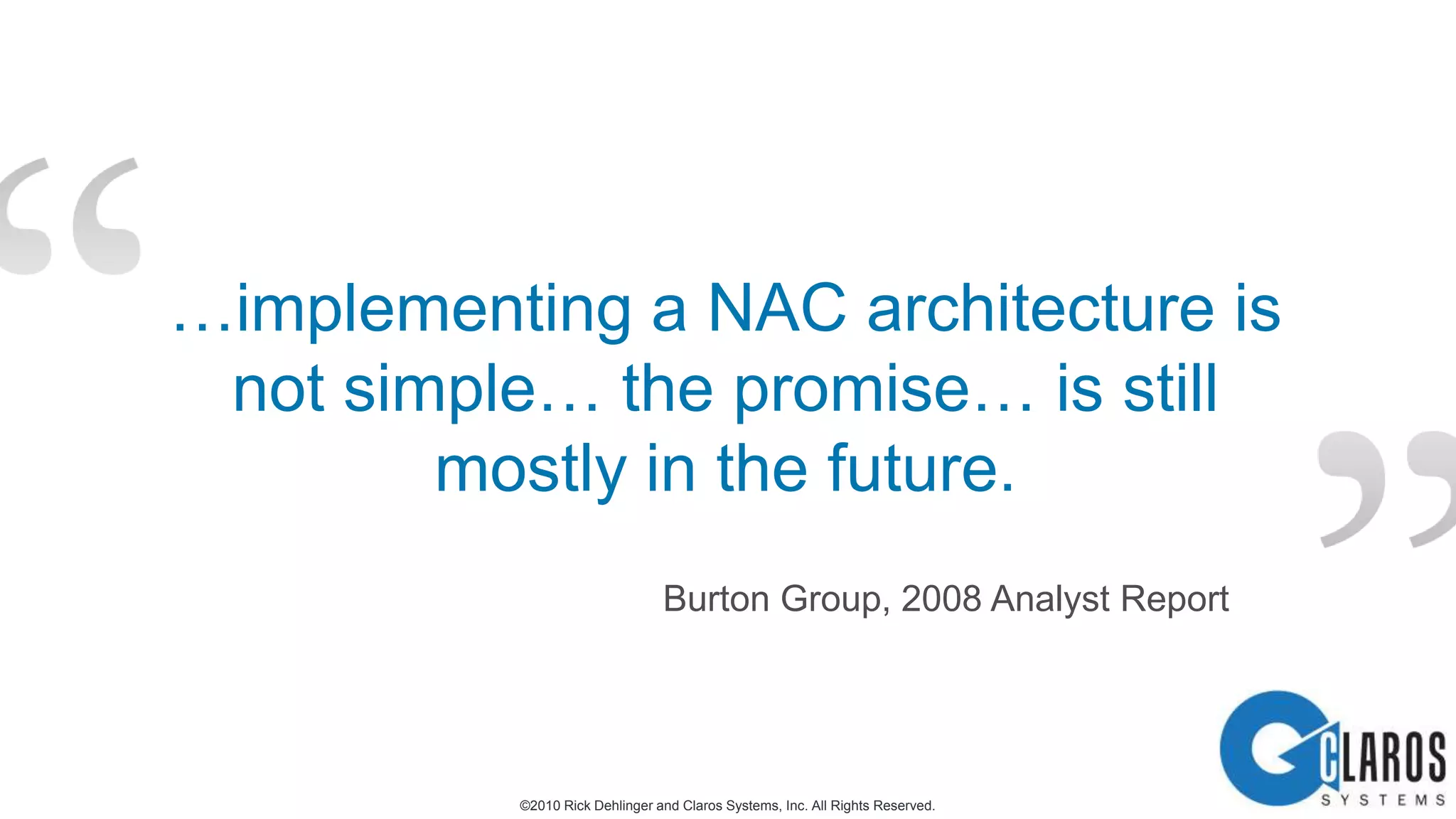
The document discusses the transformative journey of a global pharmaceutical manufacturer, 'Pharmaco,' towards a 'universal workplace' that enhances user satisfaction and operational efficiency. It outlines challenges such as managing off-network devices, complex IT architecture, and the need for robust security measures while proposing solutions like 802.1x access control and DirectAccess. The overview highlights the strategic importance of adapting to a highly regulated and competitive market through improved IT service delivery and user experience.