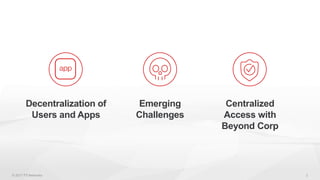
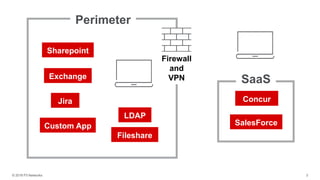
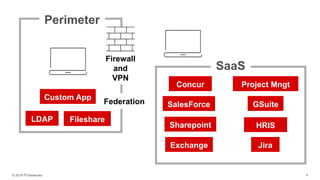
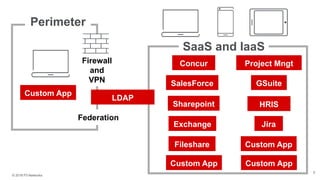
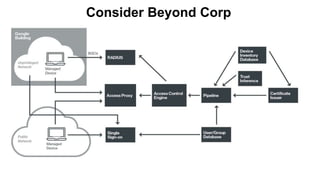
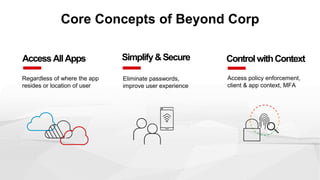
The document discusses the challenges of managing user access in a decentralized, multi-cloud environment, highlighting issues like security, visibility, and management of accounts. It notes that many users engage in poor password practices, leading to significant risks due to data breaches. To address these challenges, it suggests implementing centralized access solutions and multi-factor authentication to enhance security and user experience.