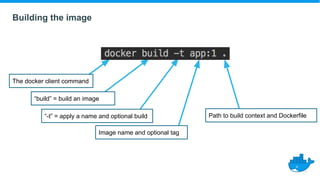
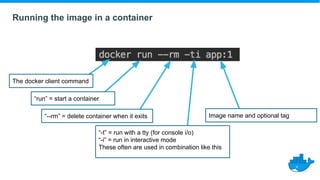
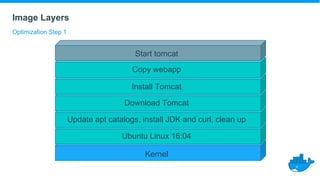
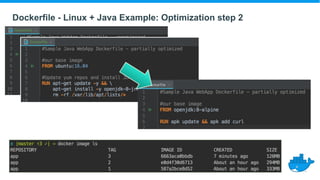
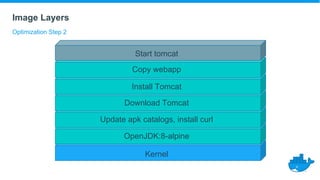
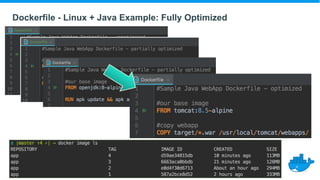
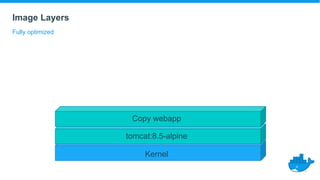
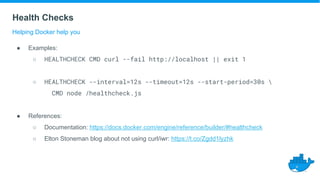
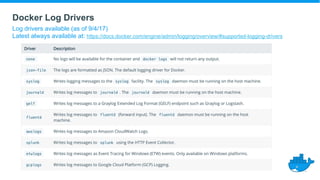
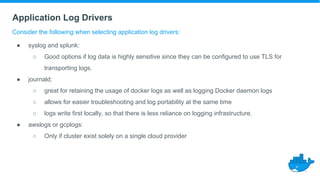
This document provides a summary of best practices for developing and deploying Java applications with Docker. It begins with an introduction and overview of Docker terminology. It then demonstrates how to build a simple Java web application as a Docker image and run it as a container. The document also covers deploying applications to clusters as services and stacks, and techniques for application management, configuration, monitoring, troubleshooting and logging in Docker environments.