Embed presentation
Download to read offline






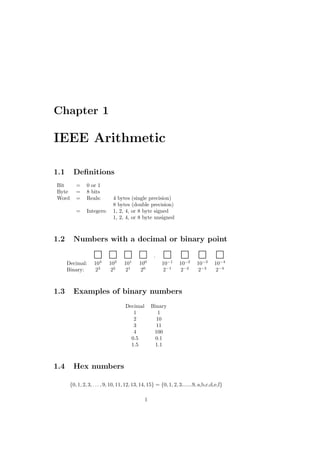
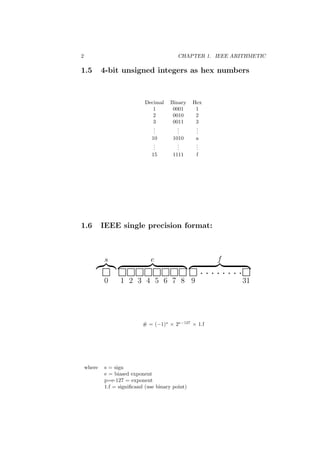


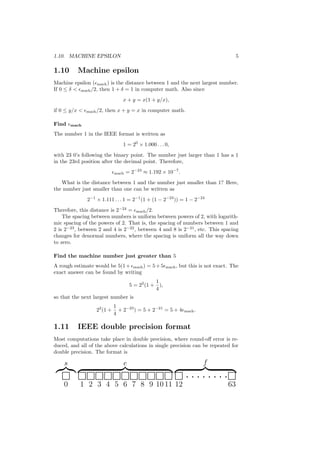







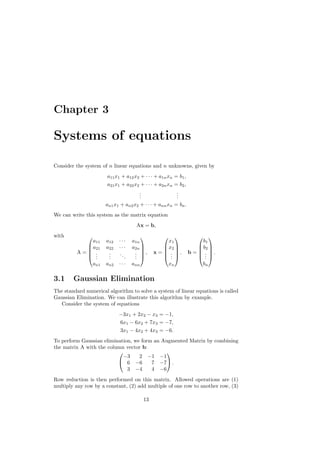


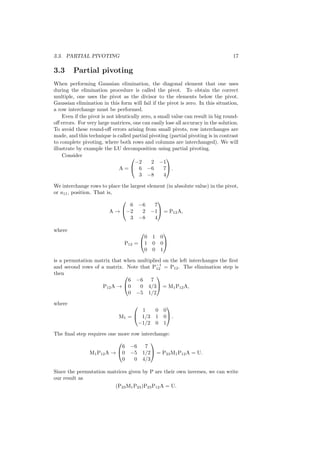








































This document contains lecture notes for an introduction to numerical methods course. It covers various topics in numerical analysis including IEEE floating point arithmetic, root finding methods, systems of equations, interpolation, integration, and ordinary differential equations. The notes provide definitions, formulas, examples and explanations of concepts in numerical methods. They are intended for engineering students and made freely available online for teaching and learning purposes.






























































