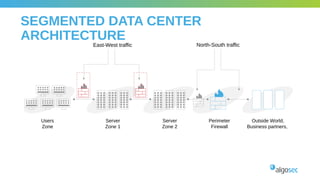
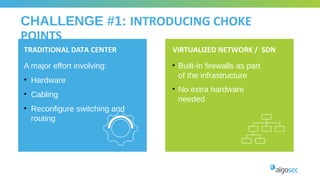
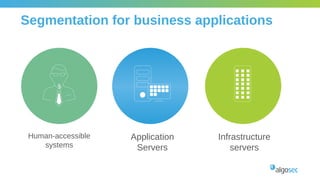
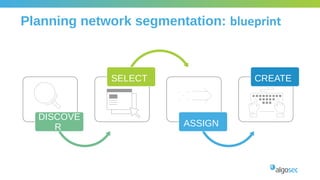
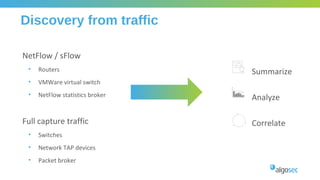
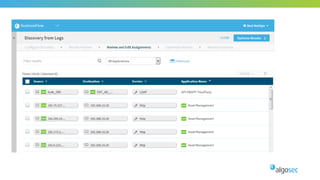
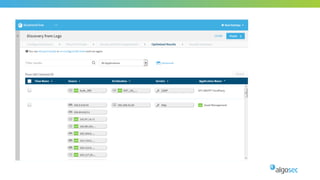
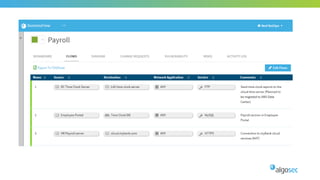
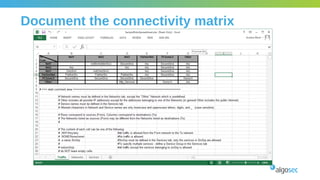
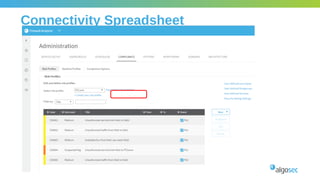
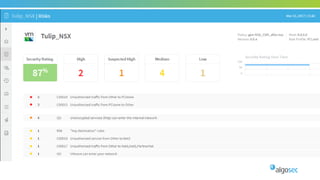
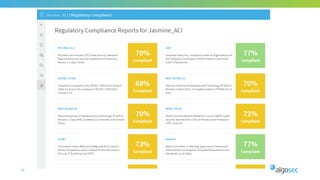
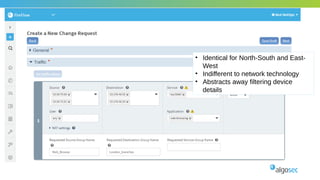
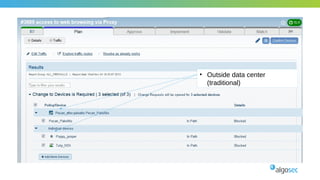
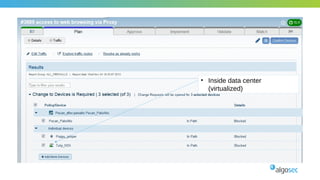
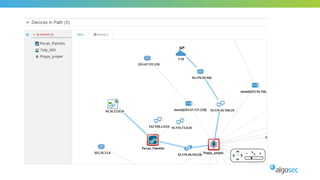
The document outlines the importance of micro-segmentation in securing data centers against lateral movements by attackers. It discusses the challenges of implementing segmentation, including the need for hardware and zoning, as well as the necessity of maintaining filtering policies that adapt to evolving application connectivity requirements. The focus is on creating a structured approach to network segmentation that enhances security without compromising essential business operations.