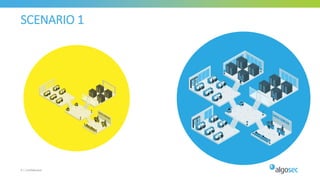
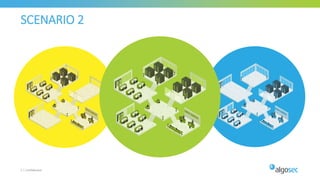
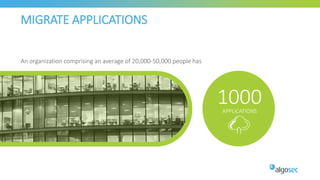
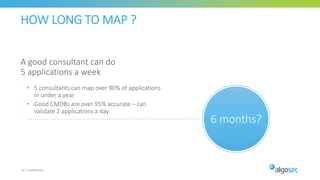
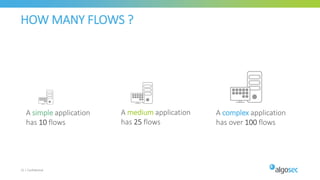
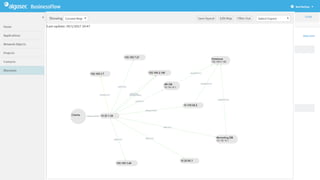
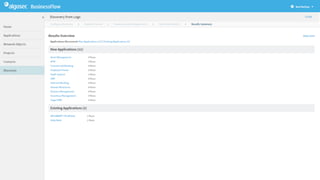
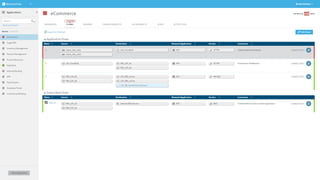
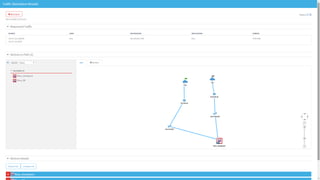
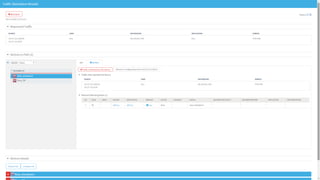
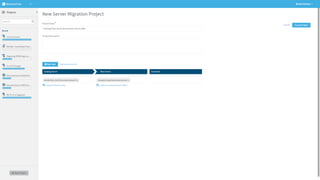
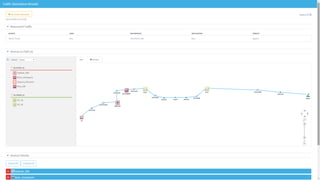
The document discusses secure management of application connectivity during mergers and acquisitions (M&A), presenting various scenarios such as company integrations and splits. It outlines the importance of mapping applications, identifying security challenges, and provides solutions for effective migration. The document emphasizes the need for proper visibility, security controls, and the use of automated tools to facilitate application migrations.