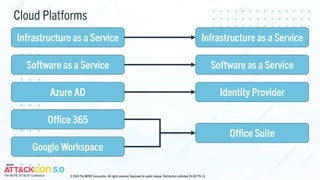
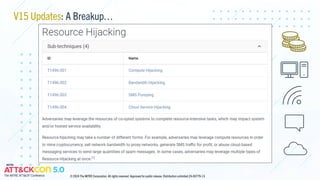
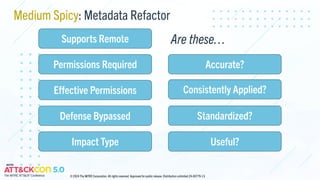
The document provides updates on the MITRE ATT&CK framework, focusing on enhancements in version 16 regarding cloud platforms and identity-as-a-service solutions. It highlights upcoming content updates, particularly emphasizing support for Linux, network, and defense evasion strategies. The document also invites contributions related to cyber threat intelligence, especially concerning unconventional defense evasion behaviors.