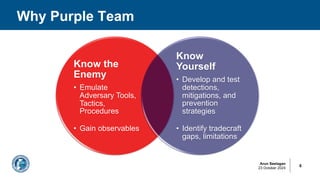
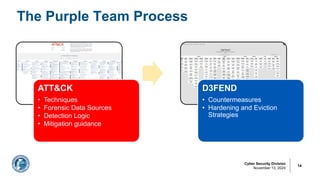
The document discusses the importance of purple teaming in cyber security, particularly for detecting cloud breaches and improving defensive strategies. It outlines processes involving threat intelligence, adversary emulation, and incident response to enhance detection capabilities and reduce risks. Additionally, it provides case studies and technical details on cloud exploitation techniques and offers guidelines for securing cloud infrastructures.








![Arun Seelagan
23 October 2024
The Need: Detect Cloud Breaches
12
https[:]//www.reuters.com/technology/chinese-hackers-breached-us-commerce-
chiefs-emails-blinken-warns-chinese-2023-07-13/
2023 Case Study
§ Storm-0558
§ Techniques
§ Unsecure Credentials: Private Key
(T1552.004)
§ Forge Web Credentials (T1606)
§ Cloud Accounts (T1078.004)
§ Application Access Token (T1550.001)
§ PowerShell (T1059.001)
§ Remote Email Collection (T1114.002)
§ Multi-hop Proxy (T1090.003)
How to Detect?](https://image.slidesharecdn.com/seelageneverycloudhasapurpleliningv1-241129172646-32746d2a/85/Every-Cloud-Has-a-Purple-Lining-Arun-Seelagan-12-320.jpg)
![Cyber Security Division
November 13, 2024
The Need: Detect Cloud Breaches
13
2024 Case Study
§ NOBELIUM
§ Techniques
§ Password Spraying (T1110.003)
§ Cloud Accounts (T1078.004)
§ Application Access Token (T1550.001)
§ Remote Email Collection (T1114.002)
§ Network Devices (T1584.008)
§ Proxy (T1090)
§ Forge Web Credentials (T1606)
https[:]//www.theverge.com/2024/7/4/24192159/micro
soft-midnight-blizzard-hack-targets](https://image.slidesharecdn.com/seelageneverycloudhasapurpleliningv1-241129172646-32746d2a/85/Every-Cloud-Has-a-Purple-Lining-Arun-Seelagan-13-320.jpg)





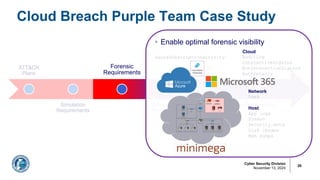
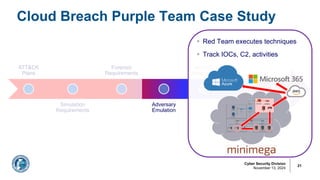
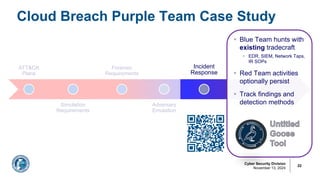
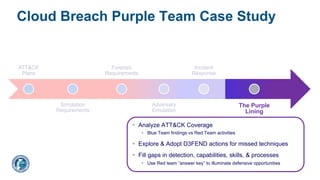

![Arun Seelagan
23 October 2024
Outcome: Federal Cloud Threat Detection
25
§ Identified key forensic artifacts to
detect Azure/M365 exploitation
§ Promote collection of appropriate
cloud logs to enable threat hunting
§ Implemented detection logic in
ATT&CK-annotated detection rules
Image Source: https[:]//www.cisa.gov/sites/default/files/2023-02/NCPS%20Cloud%20Interface%20RA%20Volume%20One%202021-05-14.pdf](https://image.slidesharecdn.com/seelageneverycloudhasapurpleliningv1-241129172646-32746d2a/85/Every-Cloud-Has-a-Purple-Lining-Arun-Seelagan-25-320.jpg)





