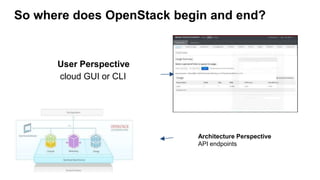
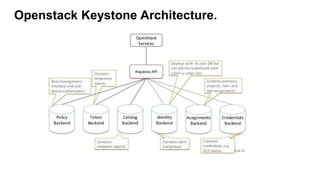
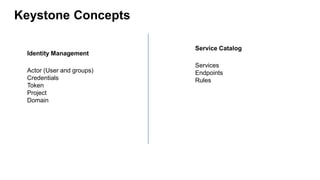
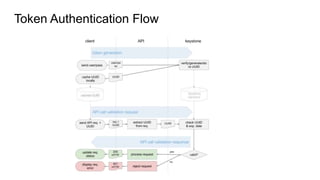
This document provides an overview of Keystone, the OpenStack identity service. It discusses key Keystone concepts like projects, domains, actors (users and groups), service catalogs, and identity providers. It also covers token types in Keystone including UUID, PKI, and Fernet tokens. The document outlines Keystone's architecture and APIs. It describes how tokens are used to authenticate to OpenStack services and how the service catalog provides endpoint information. Troubleshooting tips are also provided like checking Keystone logs and enabling debug output.







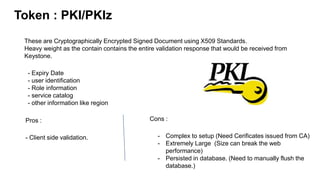
![Identity Management: Tokens :
An arbitrary bit of test taht is used to access resources. Each token has a scope
which described which resources are accessible with it.
There are four types of token that you can use with OpenStack.
"keystone.token.providers.[fernet|pkiz|pki|uuid].Provider".](https://image.slidesharecdn.com/keystone-160722071800/85/Keystone-Openstack-Identity-Service-11-320.jpg)




![Configuration file (keystone.conf)
/etc/keystone/keystone.conf
[DEFAULT] - general configuration
[sql] - optional storage backend configuration
[ec2] - Amazon EC2 authentication driver configuration
[s3] - Amazon S3 authentication driver configuration.
[oauth1] - Oauth 1.0a system driver configuration
[identity] - identity system driver configuration
[catalog] - service catalog driver configuration
[token] - token driver & token provider configuration
[cache] - caching layer configuration
[policy] - policy system driver configuration for RBAC
[signing] - cryptographic signatures for PKI based tokens
[ssl] - SSL configuration
[auth] - Authentication plugin configuration
[os_inherit] - Inherited Role Assignment extension
[paste_deploy] - Pointer to the PasteDeploy configuration file](https://image.slidesharecdn.com/keystone-160722071800/85/Keystone-Openstack-Identity-Service-18-320.jpg)

![Keystone Troubleshooting
Keystone Log file :
/var/log/keystone
Enabling Debug output: Set debug to True in the
/etc/keystone/keystone.conf configuration file
Raw
# Print debugging output (set logging level to DEBUG instead
# of default WARNING level). (boolean value)
#debug=false
debug=True
- Debug keystone tokens :
https://access.redhat.com/solutions/2166921
Access database
#mysql
MariaDB [(none)]> use keystone;
MariaDB [keystone]> show tables;
MariaDB [keystone]> show tables;
+------------------------+
| Tables_in_keystone |
+------------------------+
| access_token |
| assignment |
| consumer |
| credential |
| domain |
| endpoint |
| endpoint_group |
--------------------------](https://image.slidesharecdn.com/keystone-160722071800/85/Keystone-Openstack-Identity-Service-21-320.jpg)
