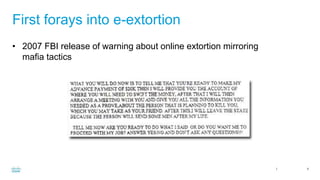
This document summarizes an presentation on e-extortion trends and defense. It discusses the evolution of extortion from early distributed denial of service attacks and ransomware to more sophisticated techniques that combine encryption, data exfiltration, and extortion demands. The presentation outlines strategies for defending against these threats, including backups, system hardening, endpoint security solutions, threat intelligence sharing, and following financial trails.



















![Cisco Confidential 23
Endpoint Solutions
• Able to review for heuristic patterns of binaries being called, and review
command line parameters such as:
• “Vssadmin.exe delete shadows /all /quiet del /f /q %0”
• “rundll32.exe C:Users$usernameAppDataLocalTemp”
• “rundll32.exe javascript:”mshtml,RunHTMLApplication<script execution
stuff>.RegRead(”HKCU<specific registry path>”) “ will interpret in the
command line as “rundll.exe mshtml.dll, $hexadecimal for entry point in
memory”
• “regsvr32.exe /s /u /i:< ^((http[s]?|ftp):/)?/?([^:/s]+)((/w+)*/)([w-
.]+[^#?s]+)(.*)?(#[w-]+)?$ > scrobj.dll
• “Powershell -nop -c "iex(New-Object Net.WebClient).DownloadString :
“^((http[s]?|ftp):/)?/?([^:/s]+)((/w+)*/)([w-.]+[^#?s]+)(.*)?(#[w-]+)?$ ’)"
• “Maliciousbinary.exe %windir%system32....%smstc.exe”](https://image.slidesharecdn.com/tampabsidese-extortion2-170212000427/85/e-Extortion-Trends-and-Defense-23-320.jpg)










