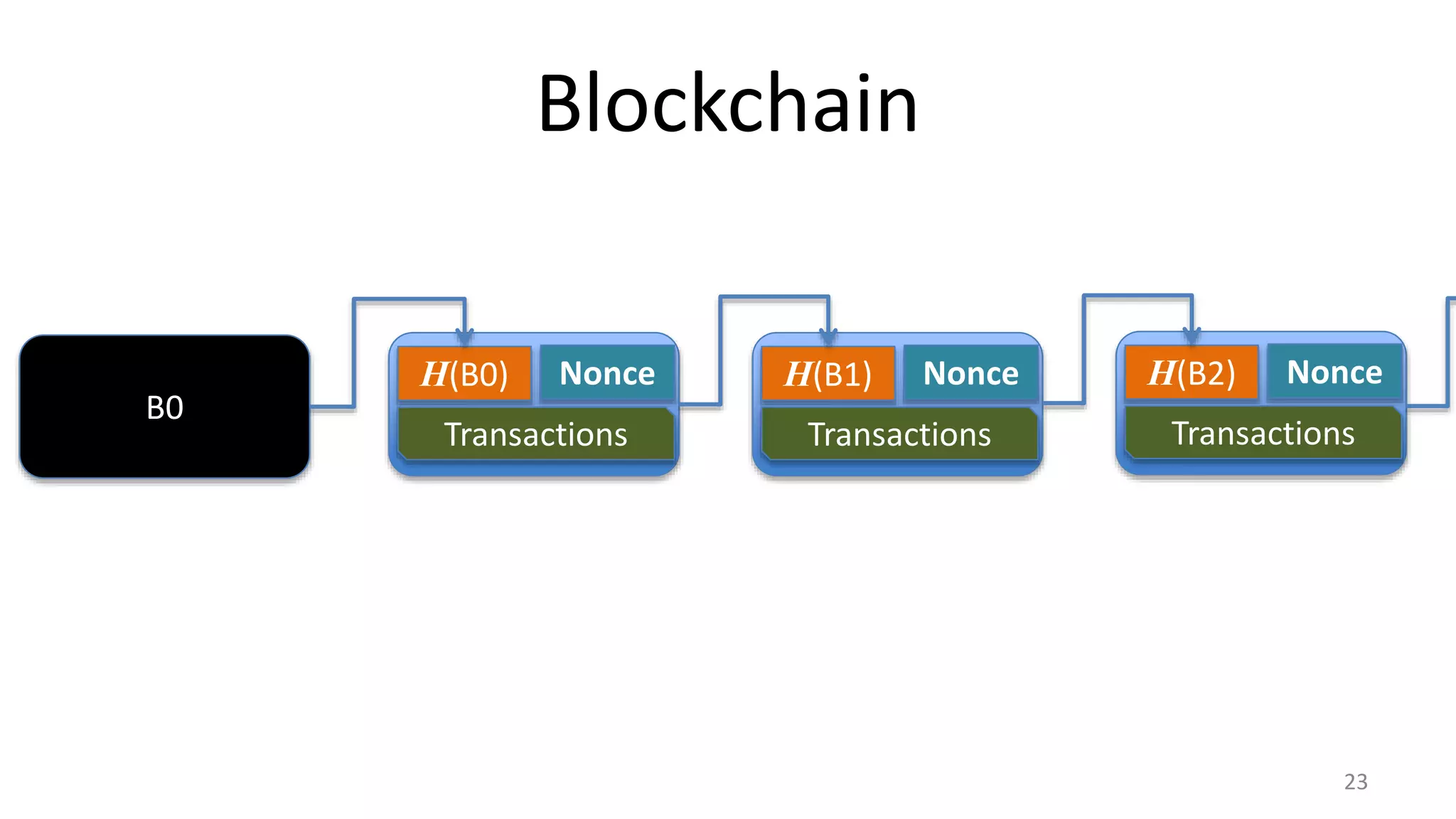
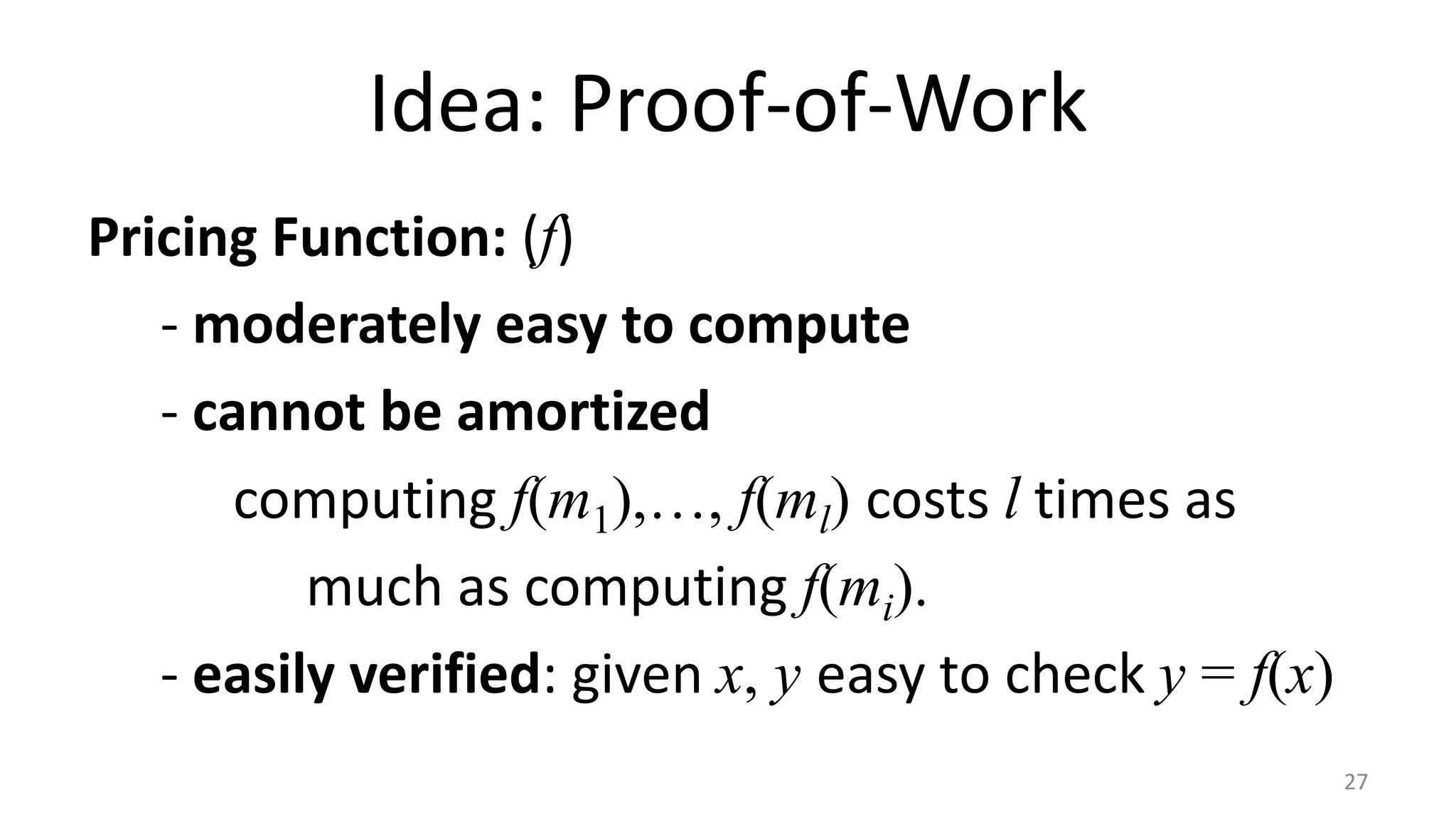
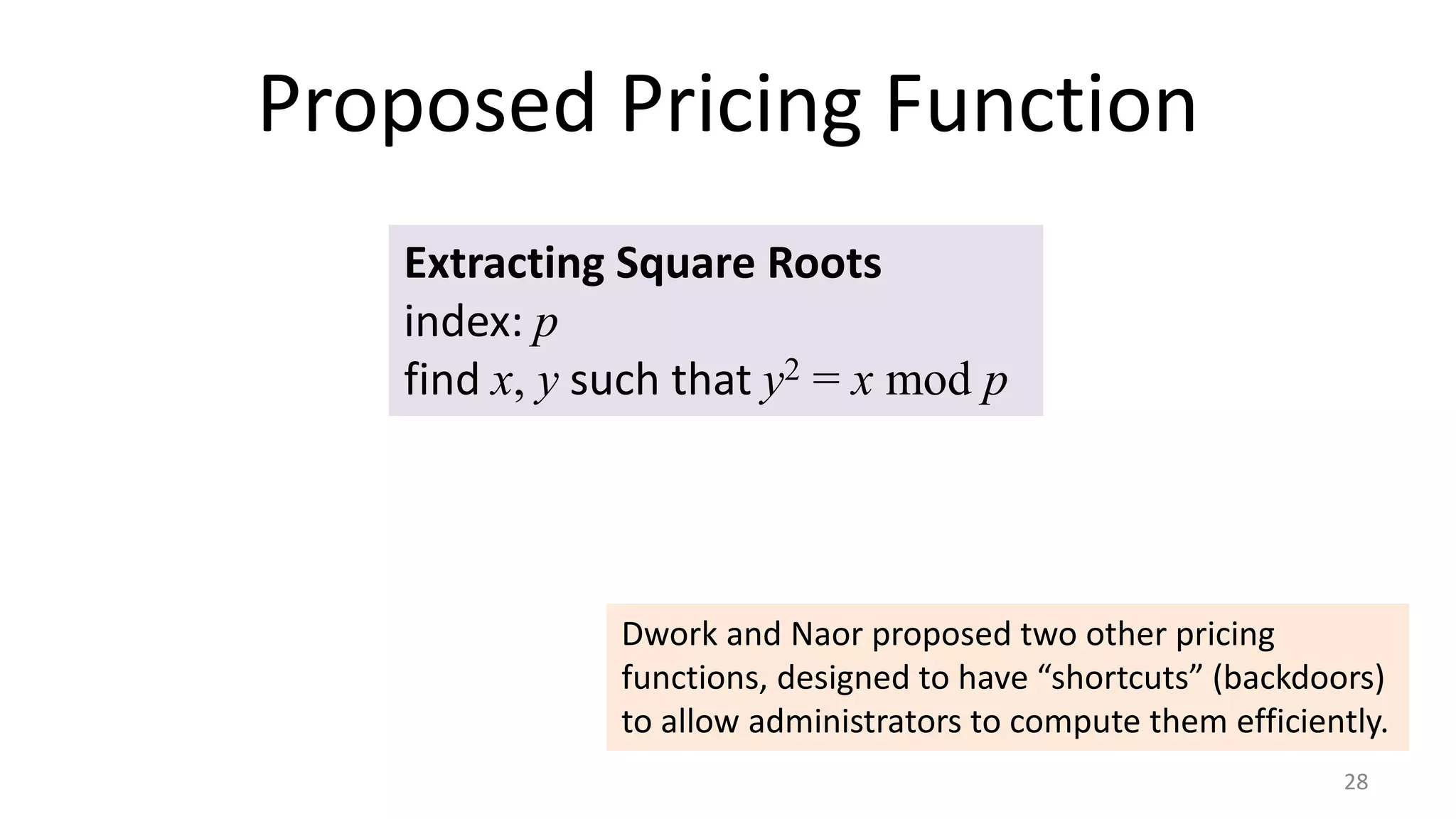
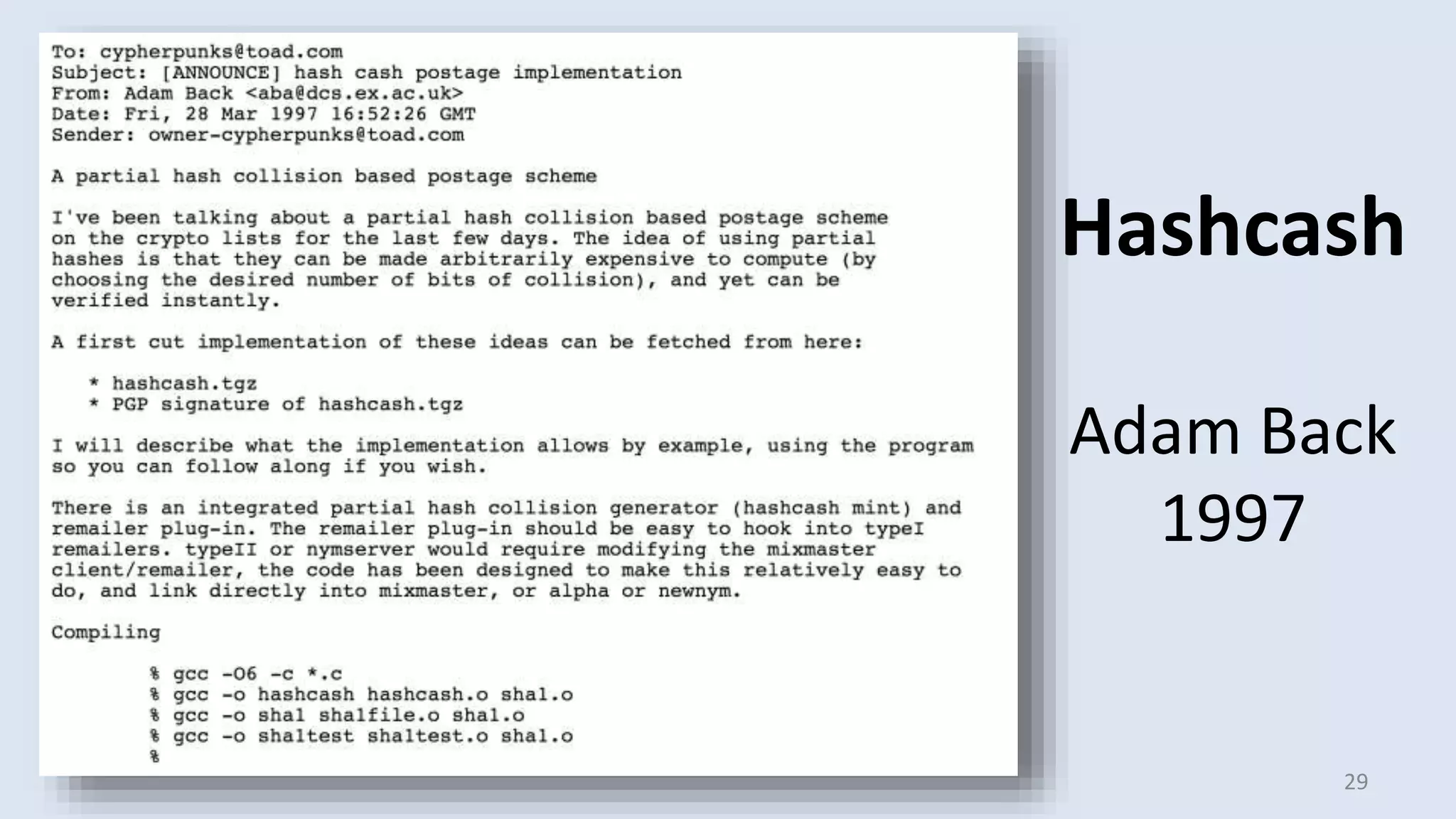
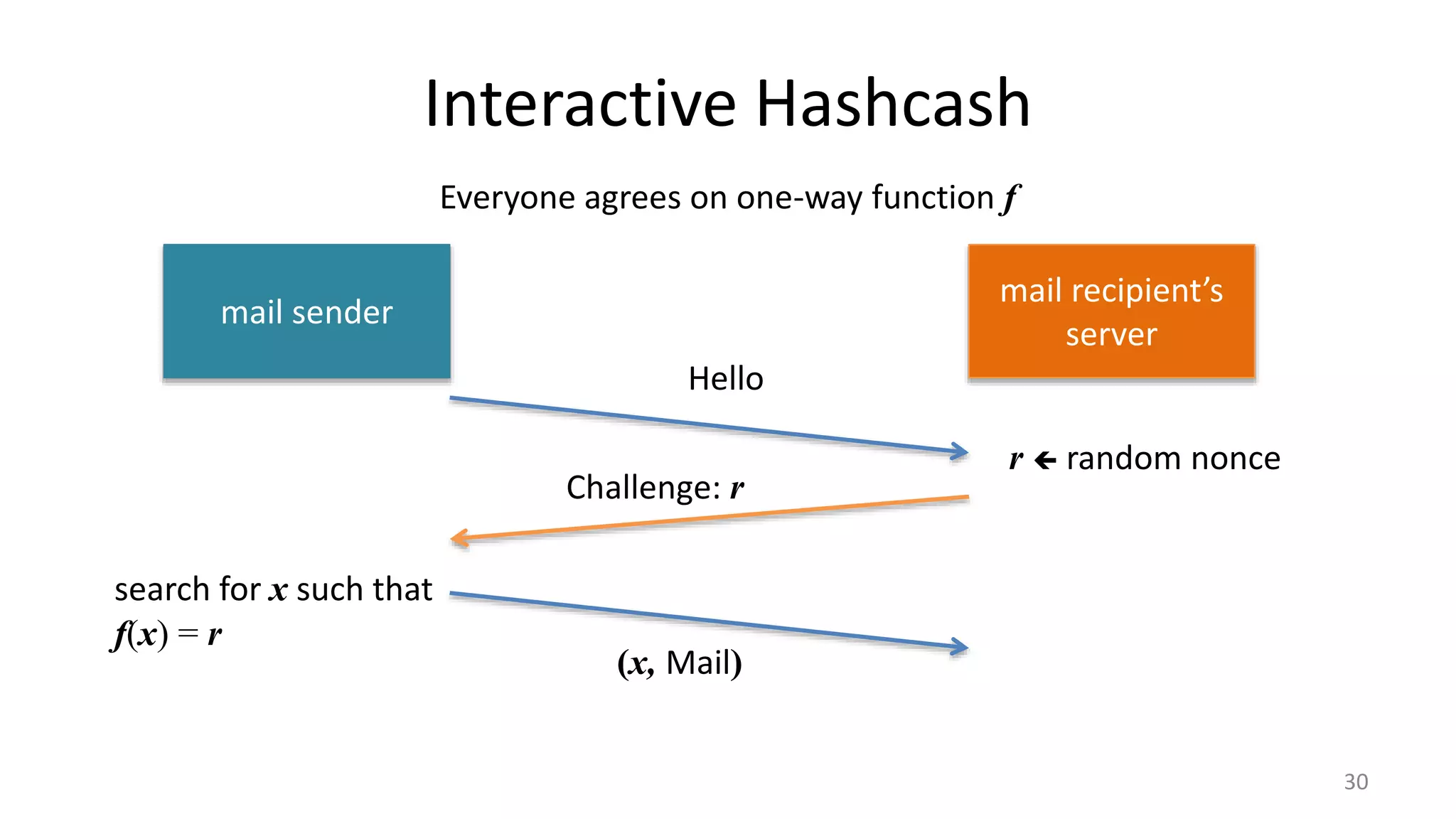
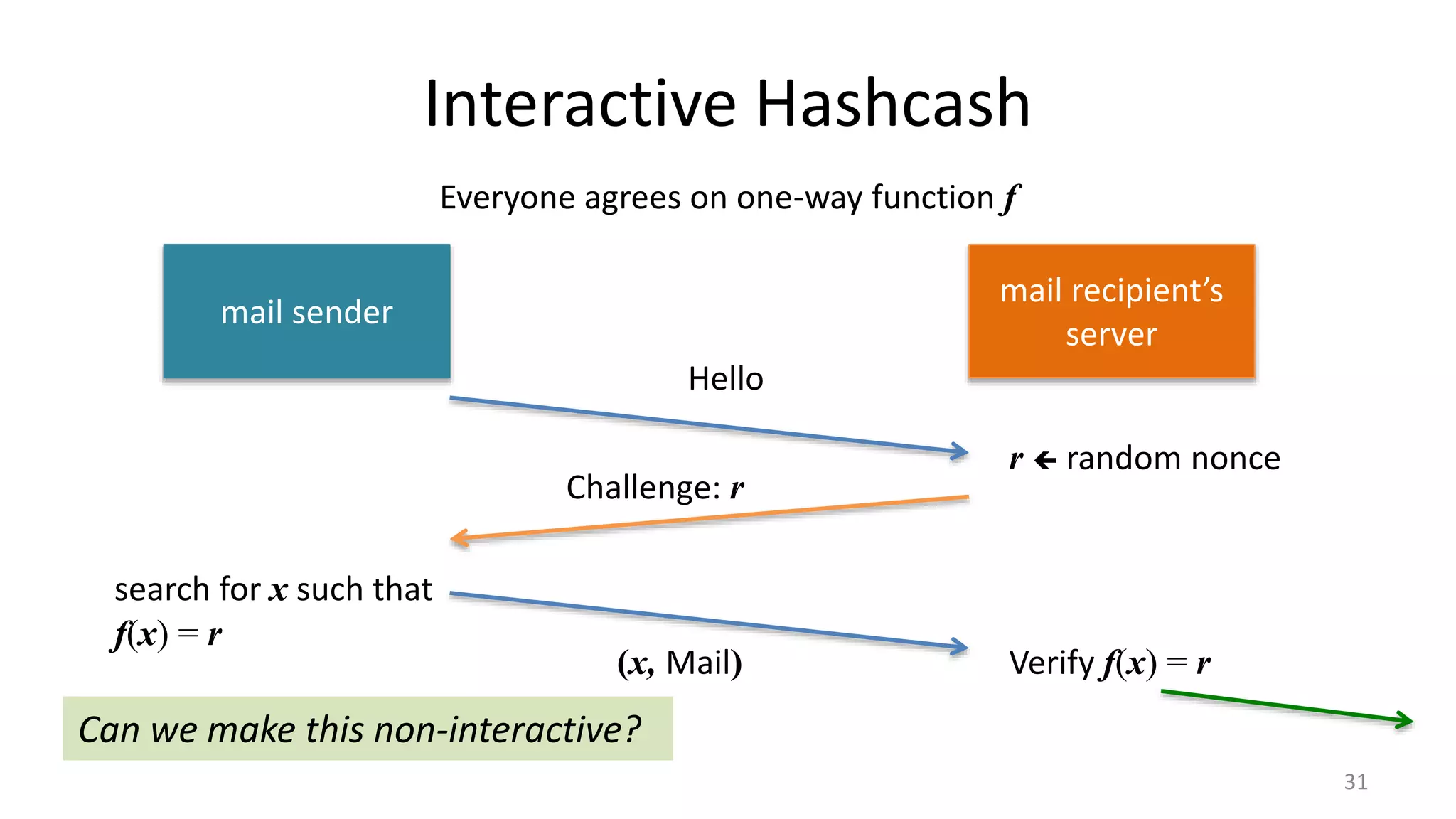
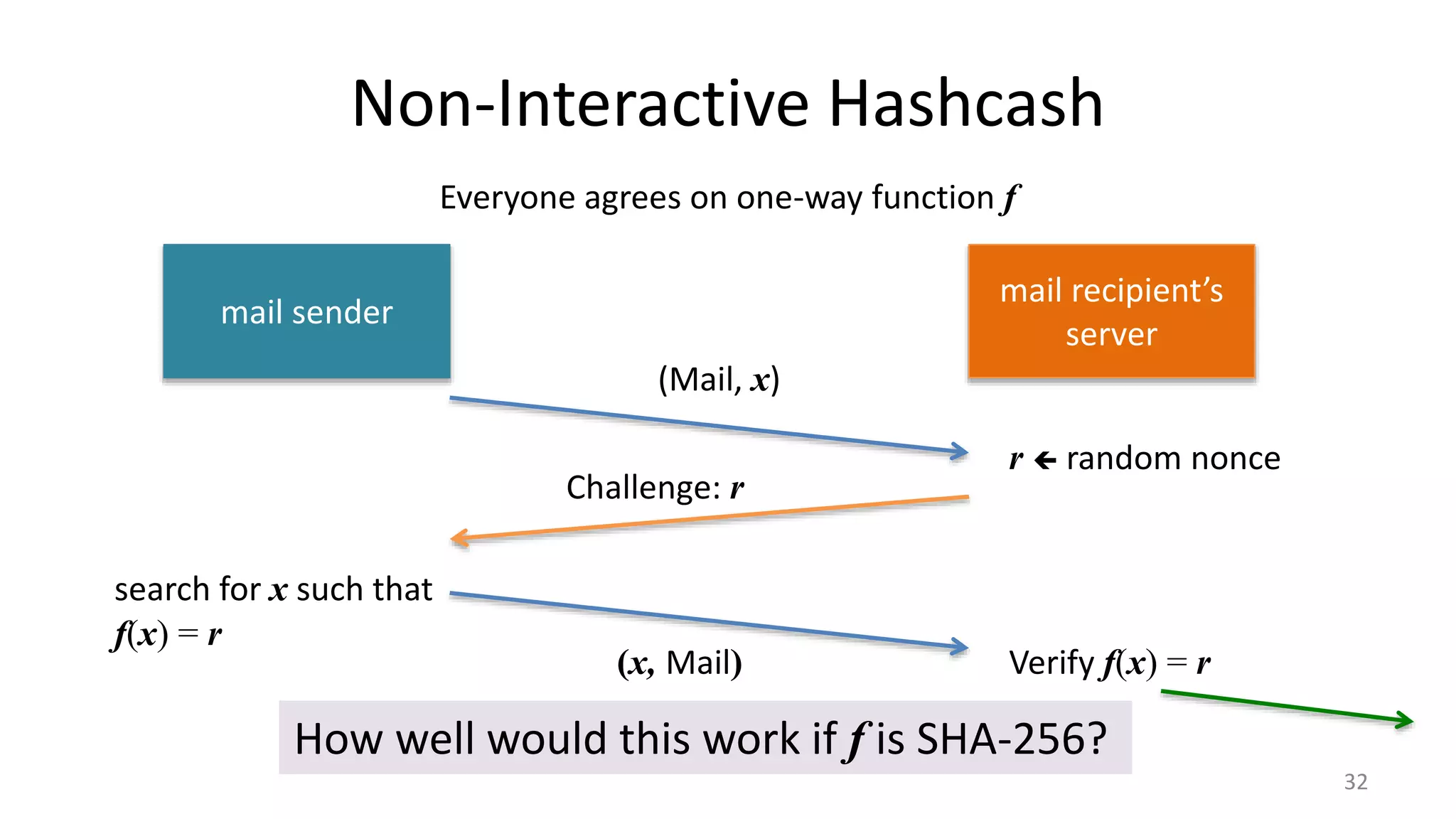
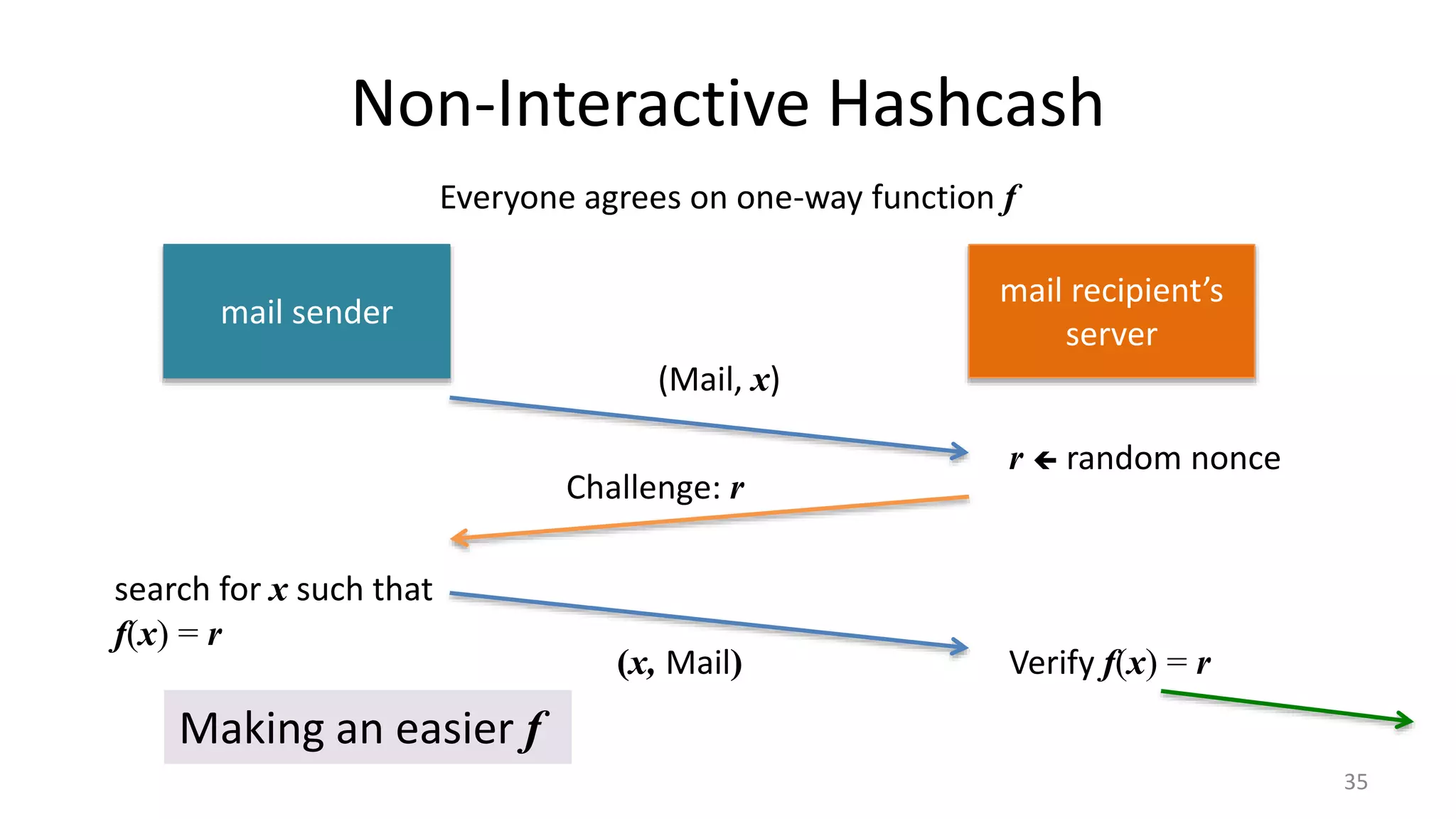
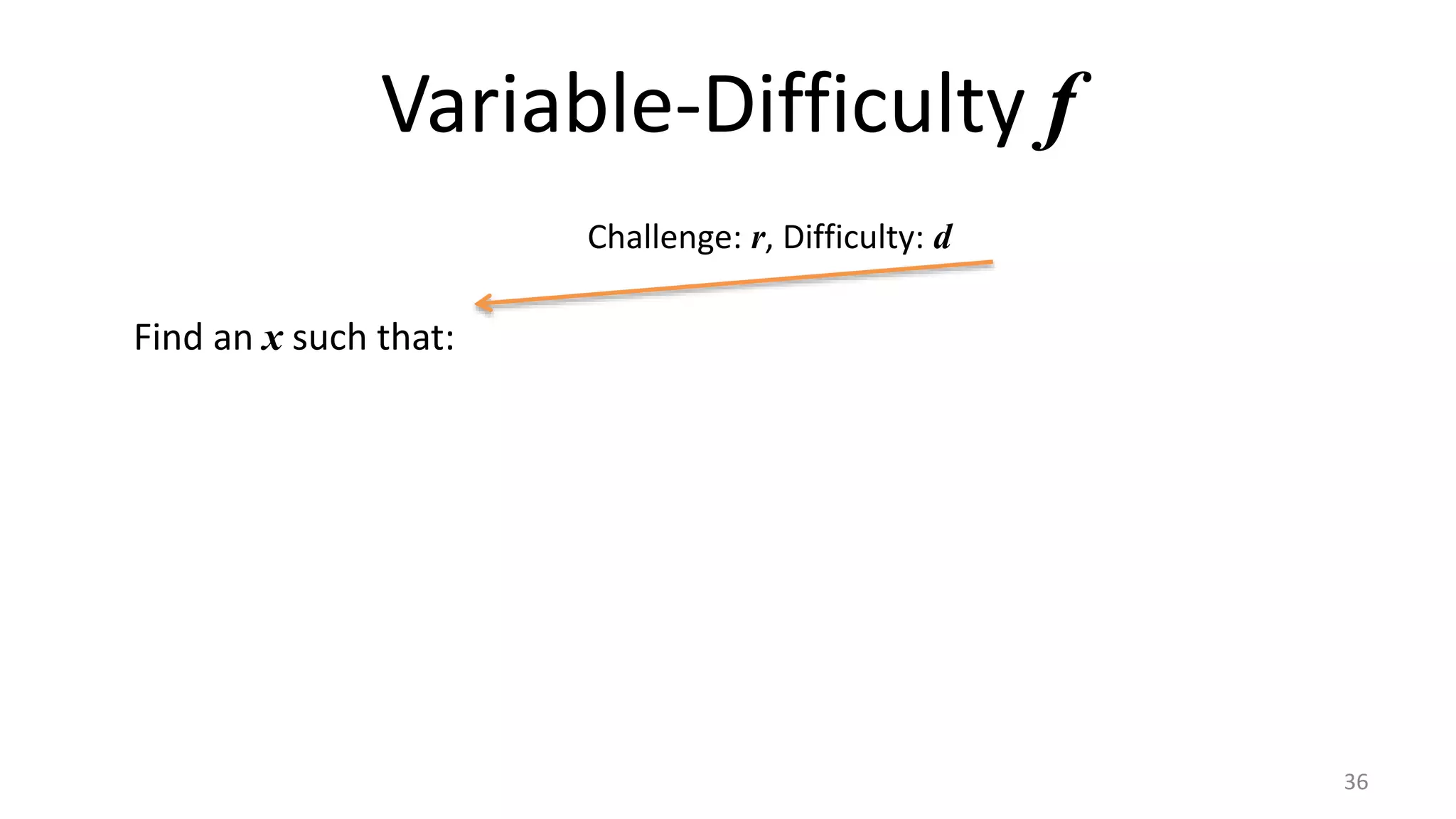
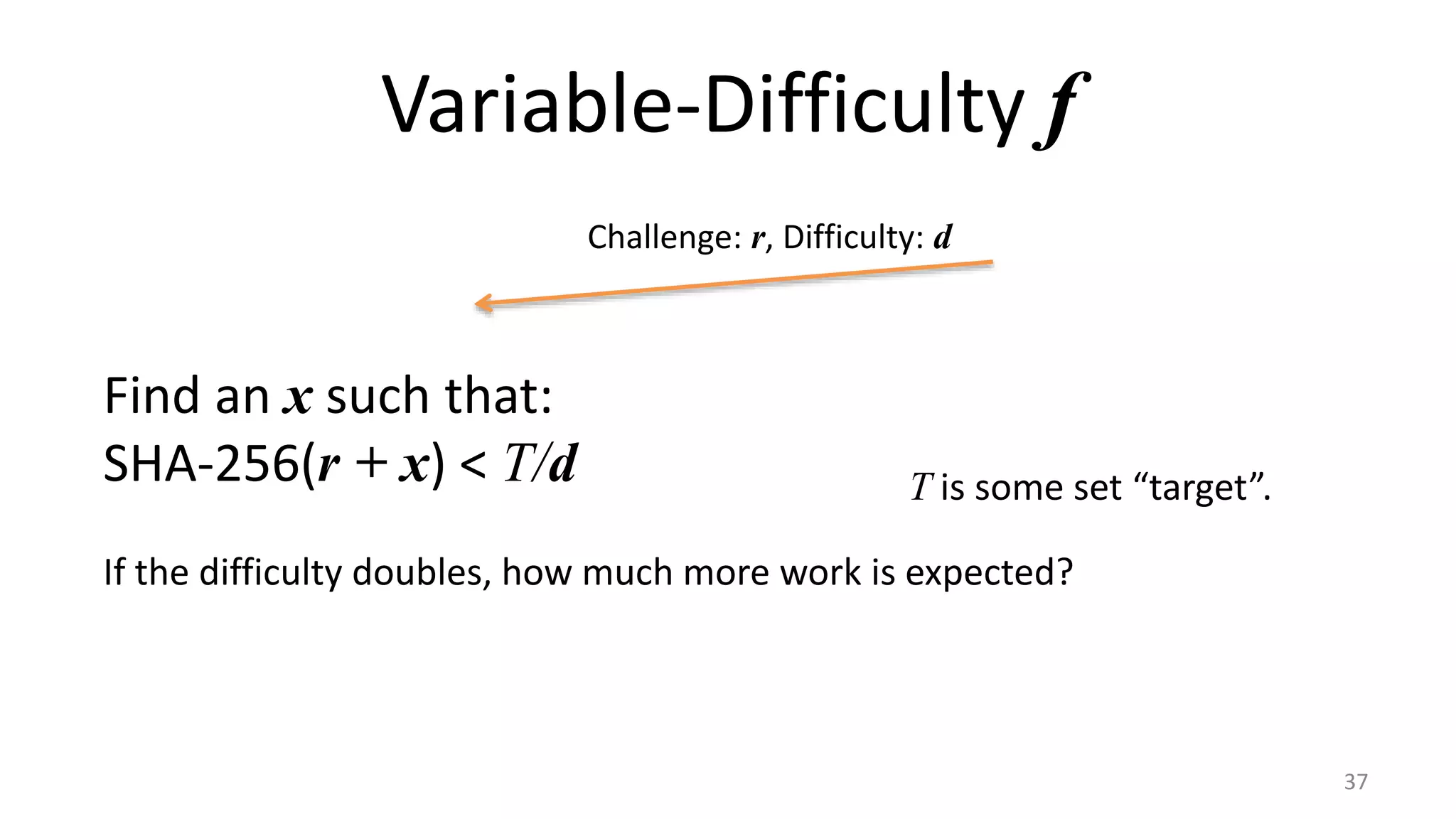
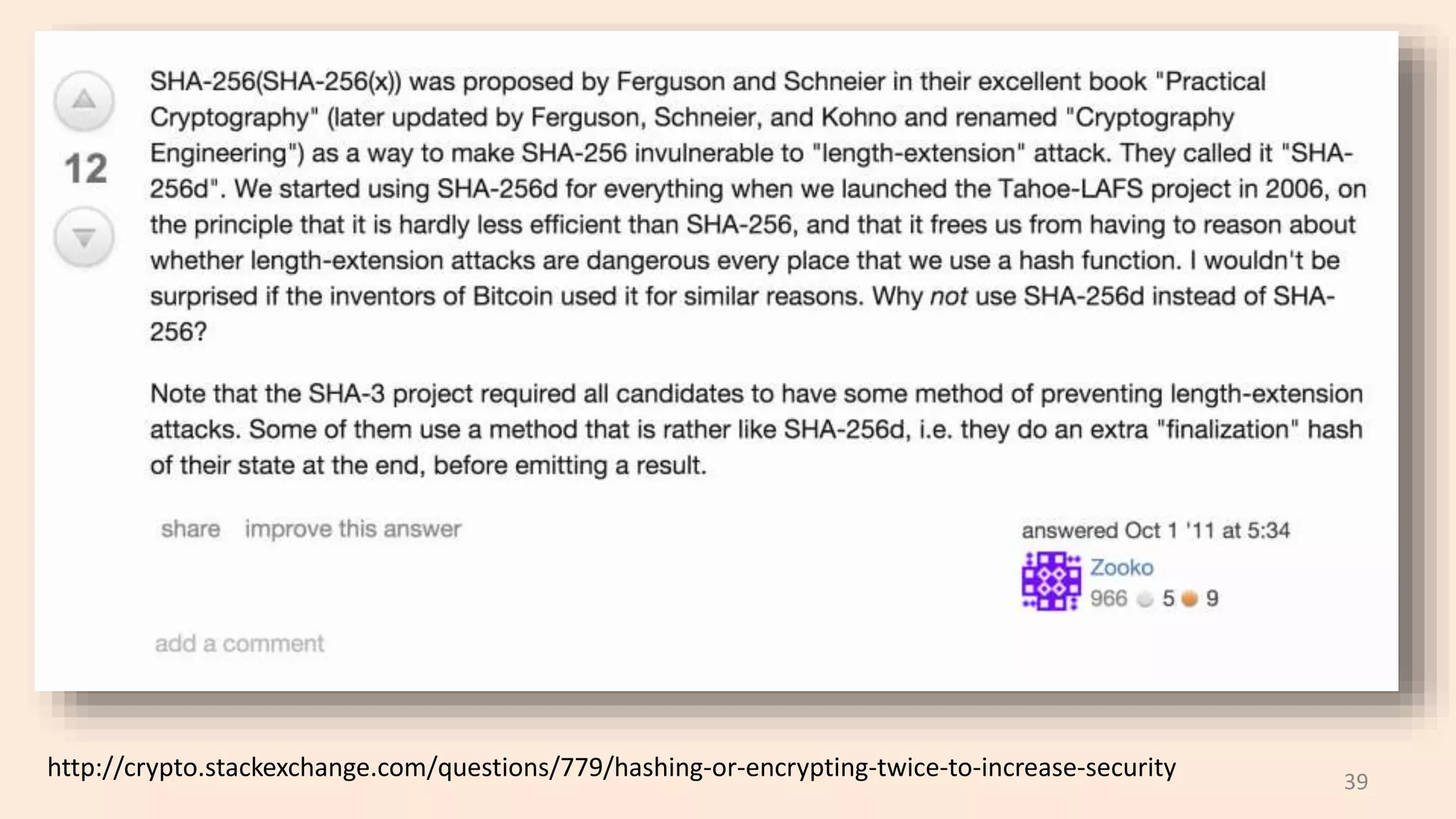
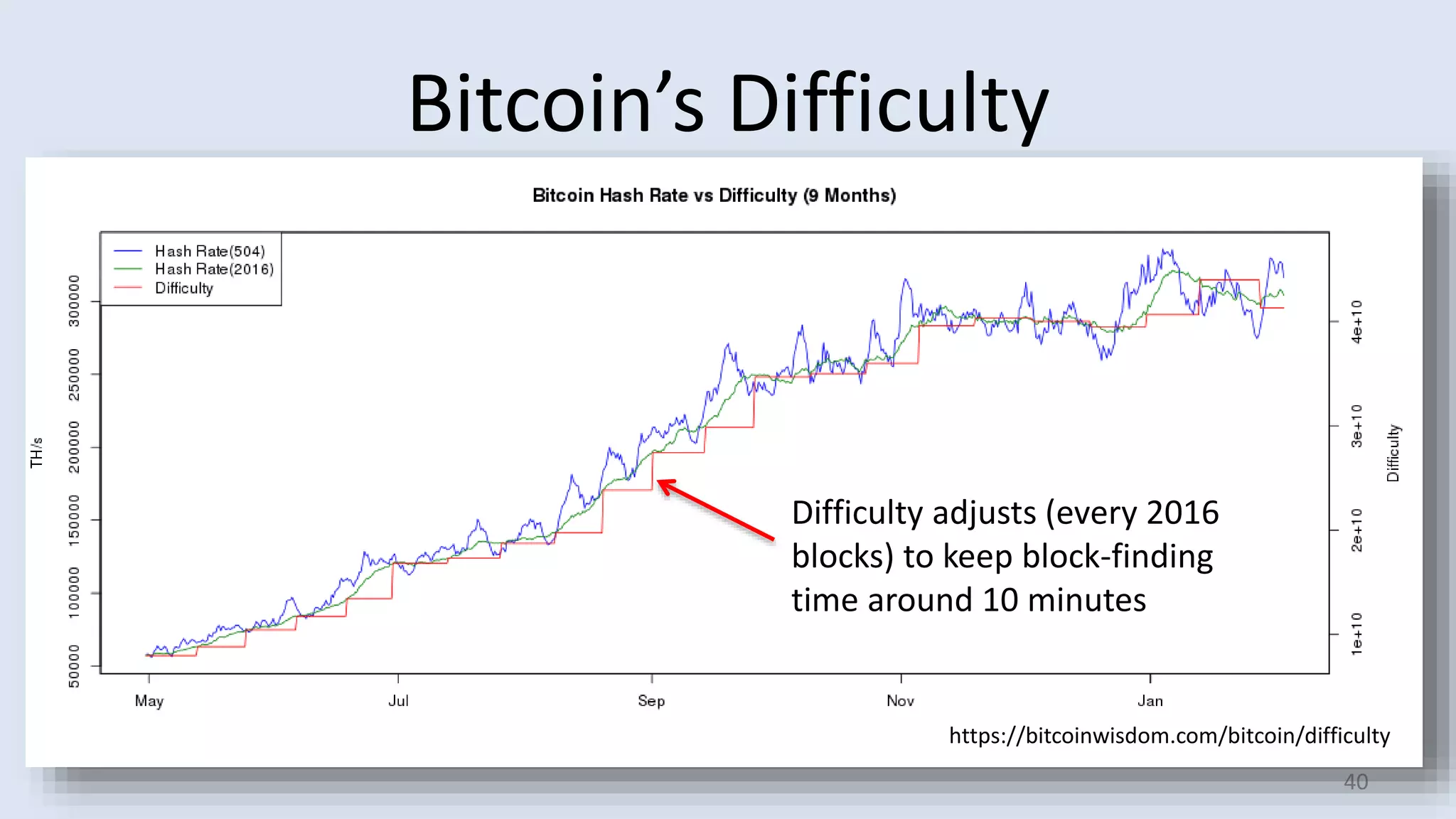
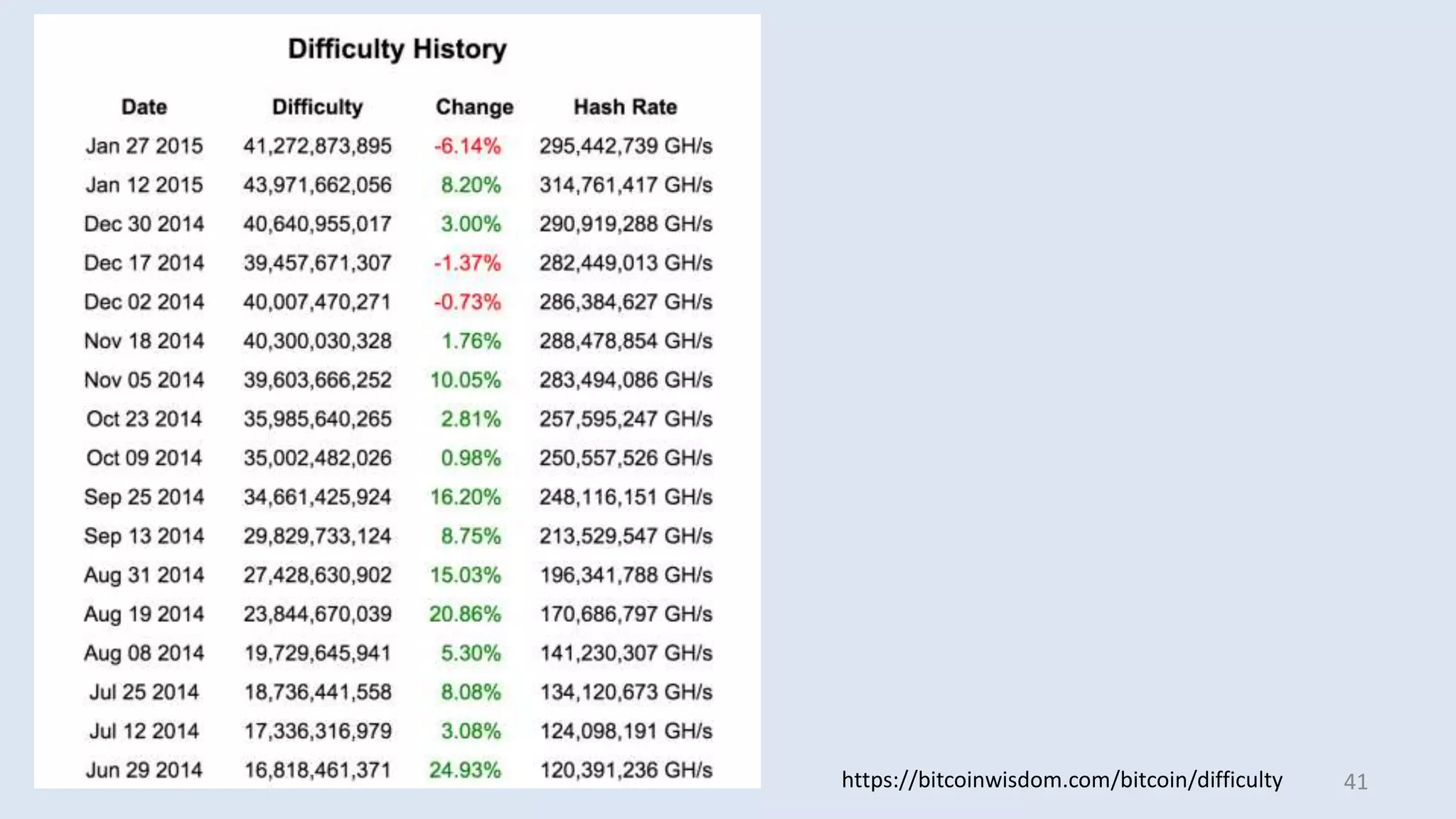
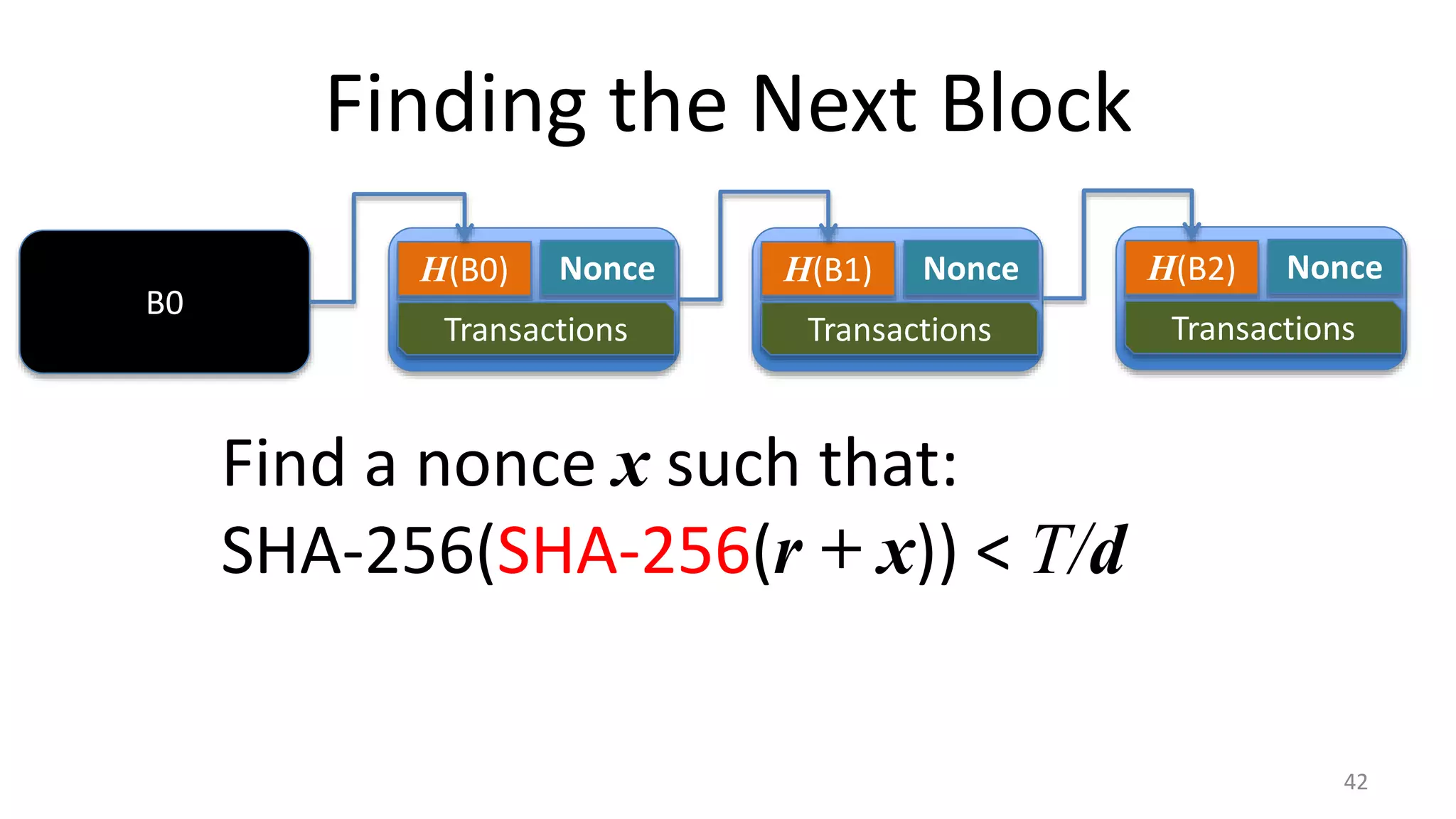
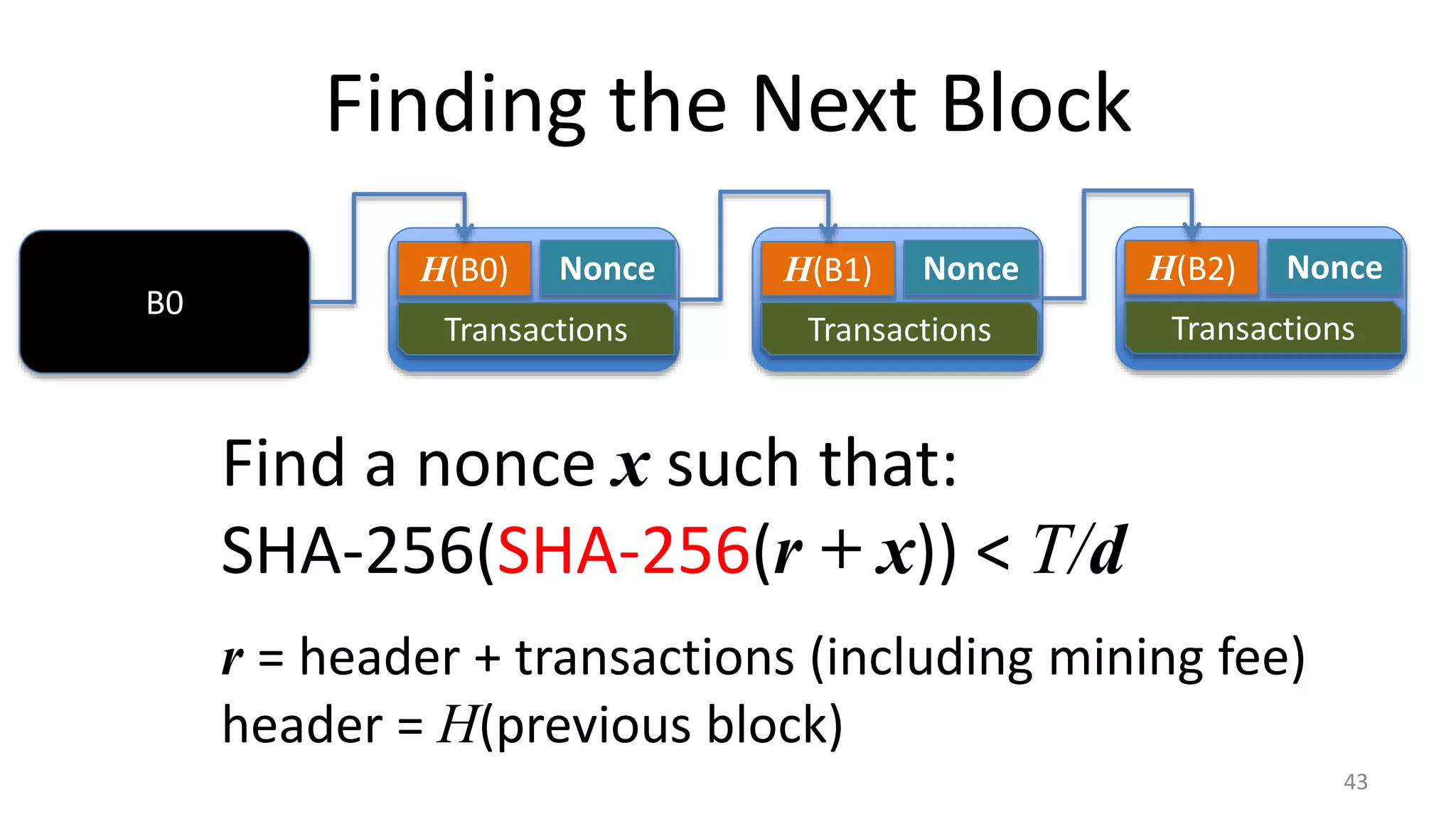
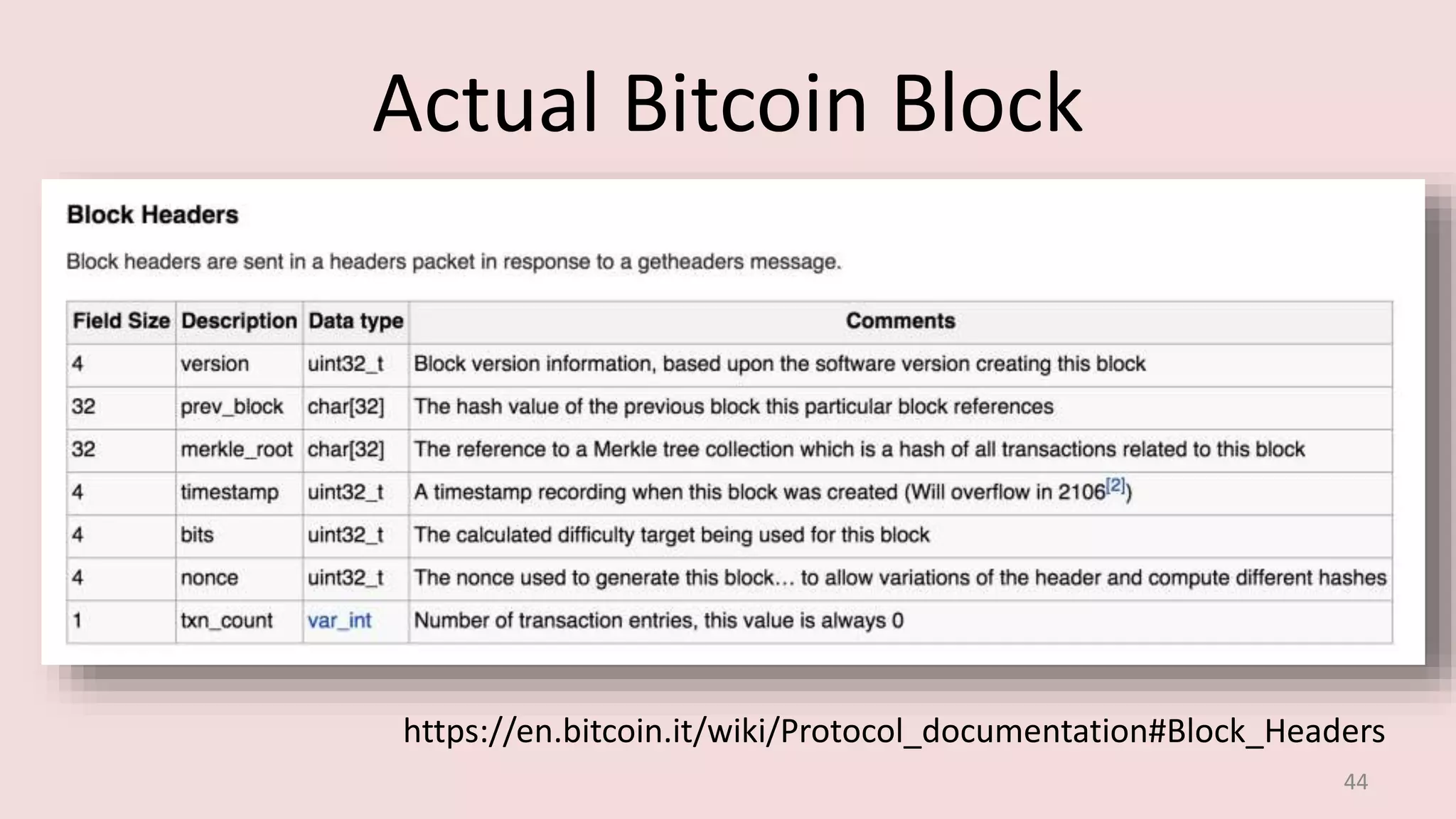
This document discusses proofs of work and blockchain technology. It begins by explaining the purpose of project 1 and opportunities for students to earn credit. It then covers how proofs of work can be used to establish distributed trust in a public ledger or blockchain without a centralized authority. Specifically, it discusses how Bitcoin uses the SHA-256 hash function and difficulty adjustment to implement a proof of work that requires computational resources to add a block to the blockchain and maintain consensus. Students are also given opportunities to earn credit for project 1 by posting additional comments.












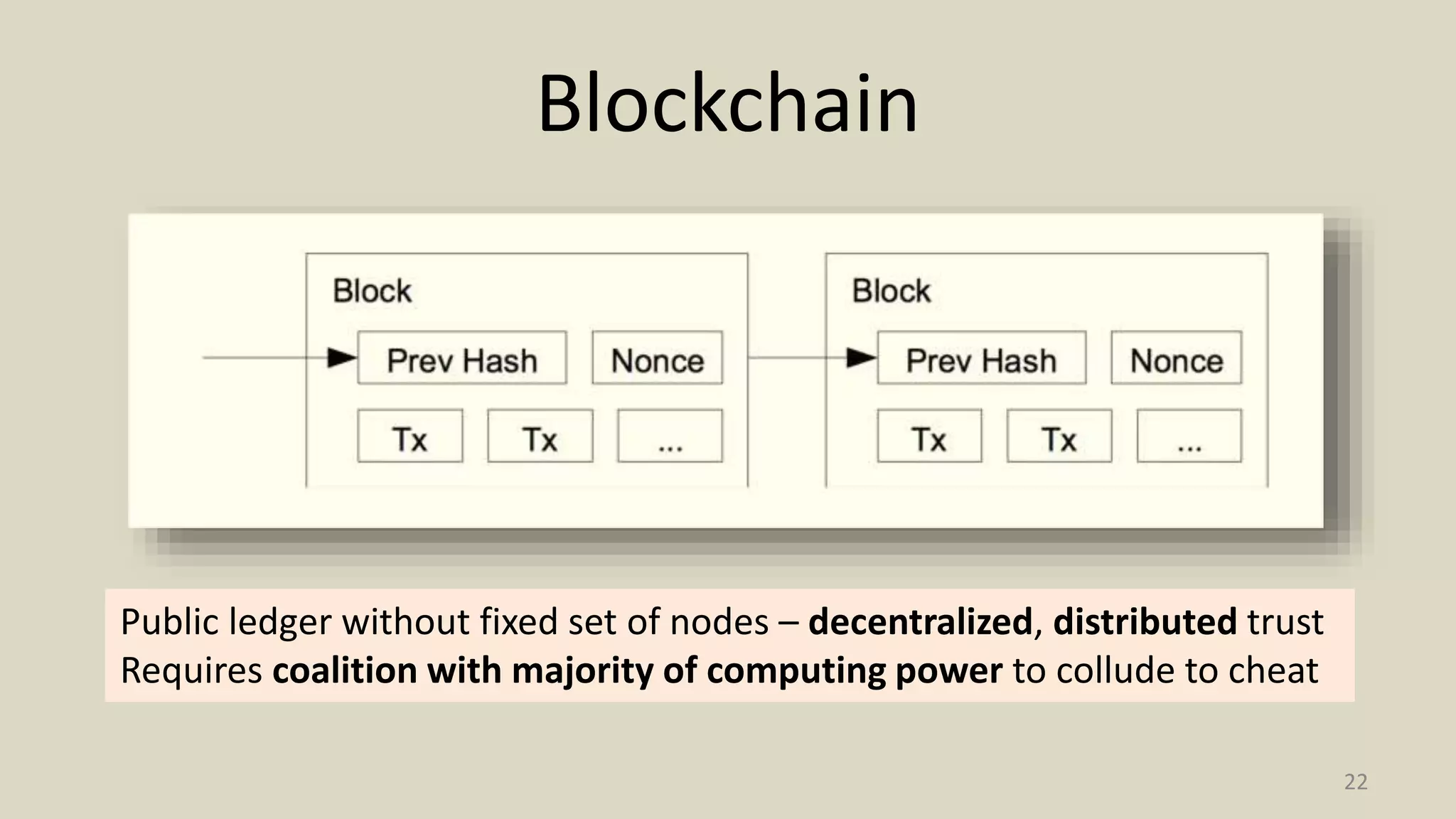
![Public Ledger
16
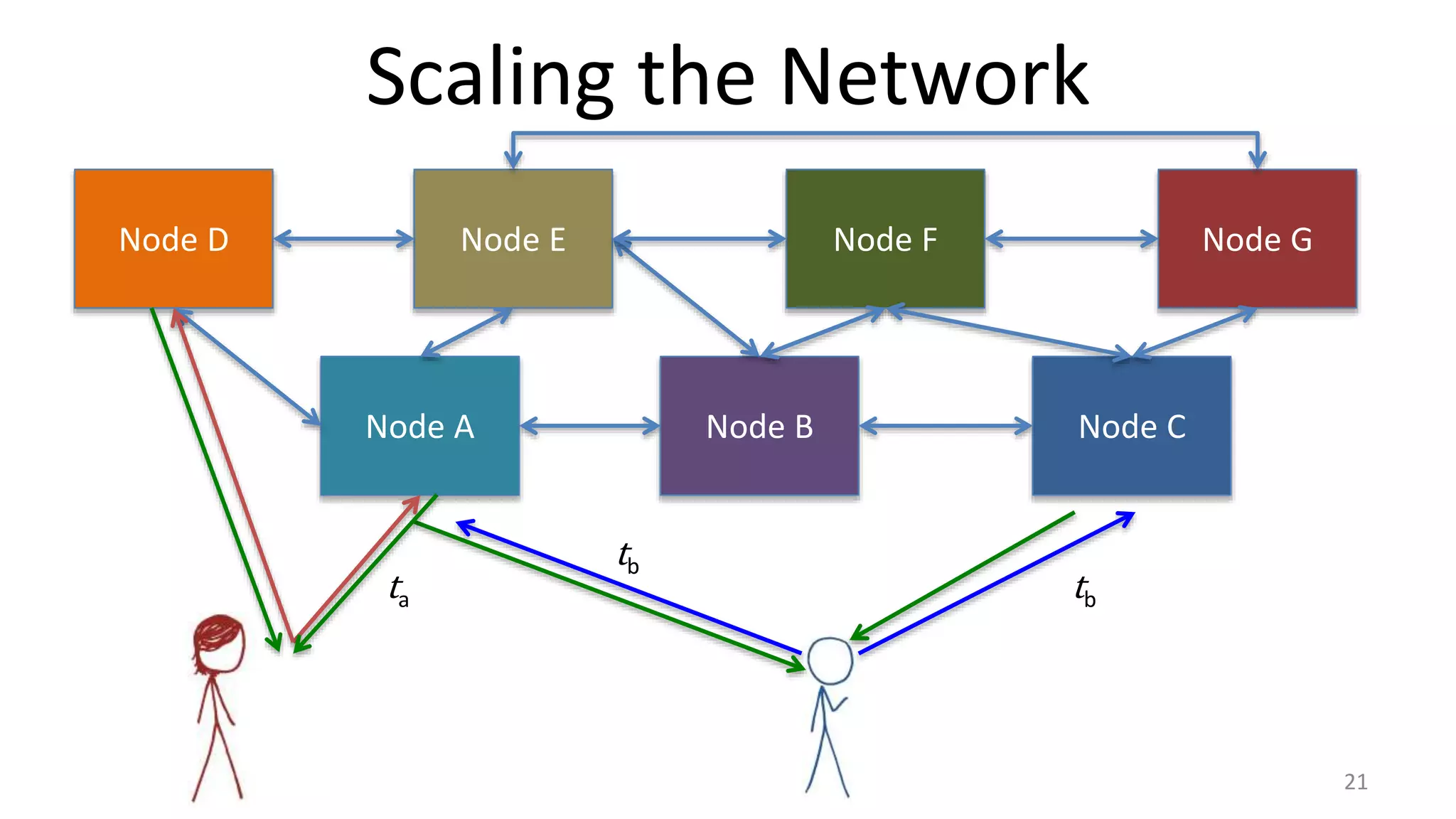
Node A Node B Node C
M = transfer X to Bob EKRA
[H(M)]
Bob wants to verify:
1. Alice hasn’t already transferred X
2. The coin will be valuable for Bob](https://image.slidesharecdn.com/class6-inked-150202145534-conversion-gate02/75/Proofs-of-Work-17-2048.jpg)
![Public Ledger: Distributed Trust (?)
17
Node A Node B Node C
M = transfer X to Bob EKRA
[H(M)]
Bob wants to verify:
1. Alice hasn’t already transferred X
2. The coin will be valuable for Bob
tb
tb
tb tb](https://image.slidesharecdn.com/class6-inked-150202145534-conversion-gate02/75/Proofs-of-Work-18-2048.jpg)
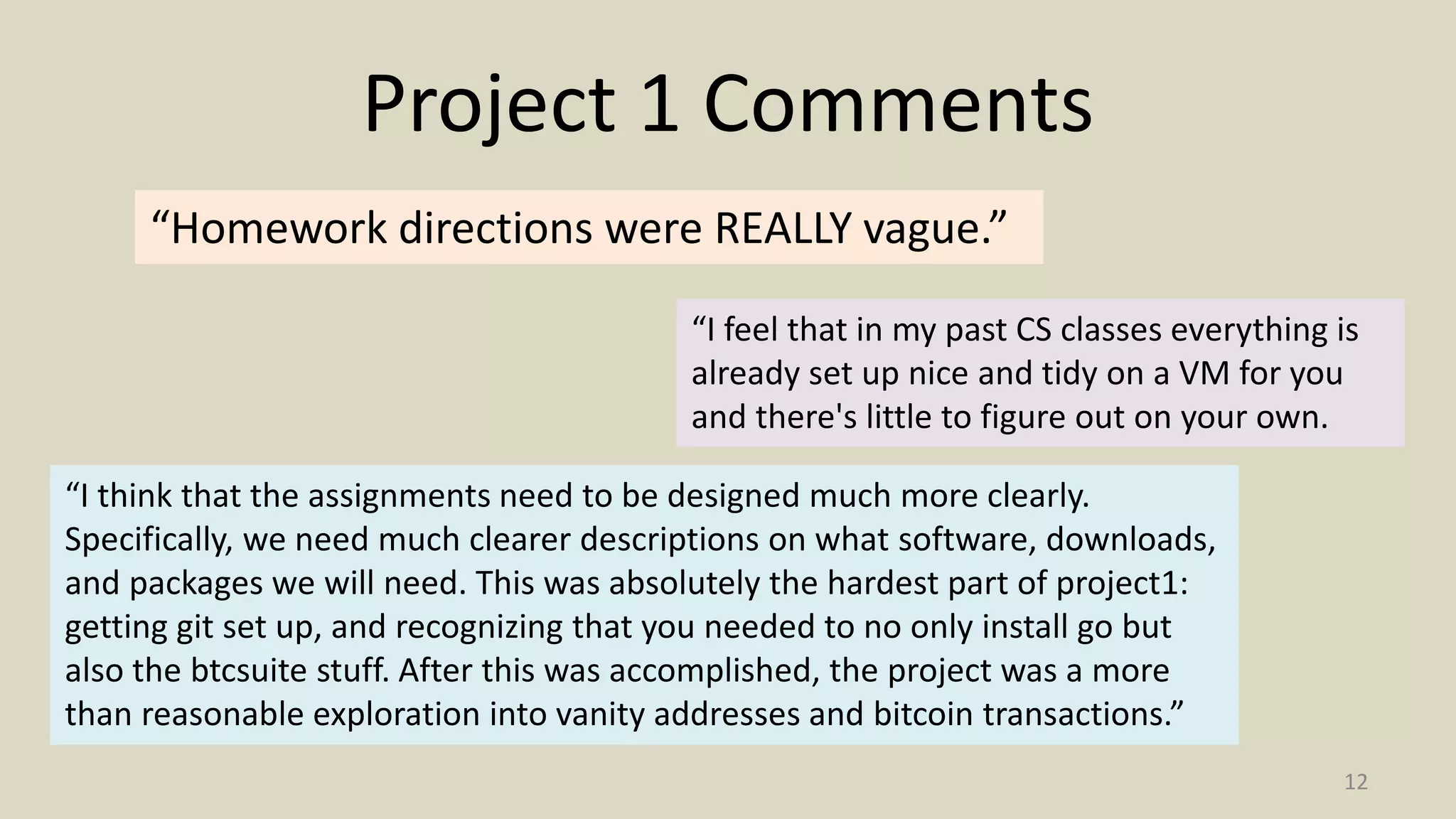
![18
Node A Node B Node C
M = transfer X to Bob EKRA
[H(M)]
Bob wants to verify:
1. Alice hasn’t already transferred X
2. The coin will be valuable for Bob
tb
tb
tb tb
ok!
ok!
t
Transactions
1 tb (X->Bob)
Transactions
1 tb (X->Bob)](https://image.slidesharecdn.com/class6-inked-150202145534-conversion-gate02/75/Proofs-of-Work-19-2048.jpg)
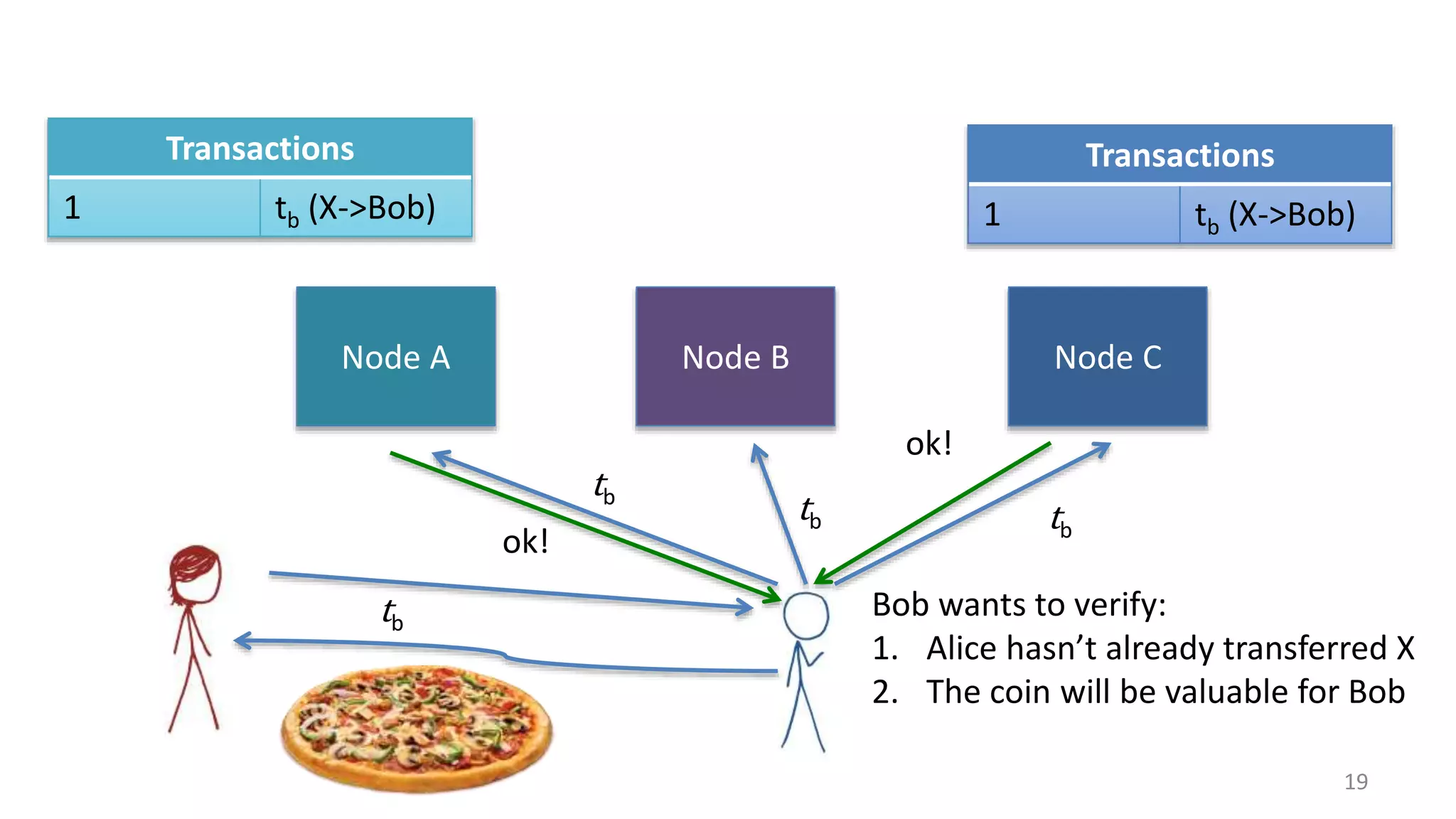
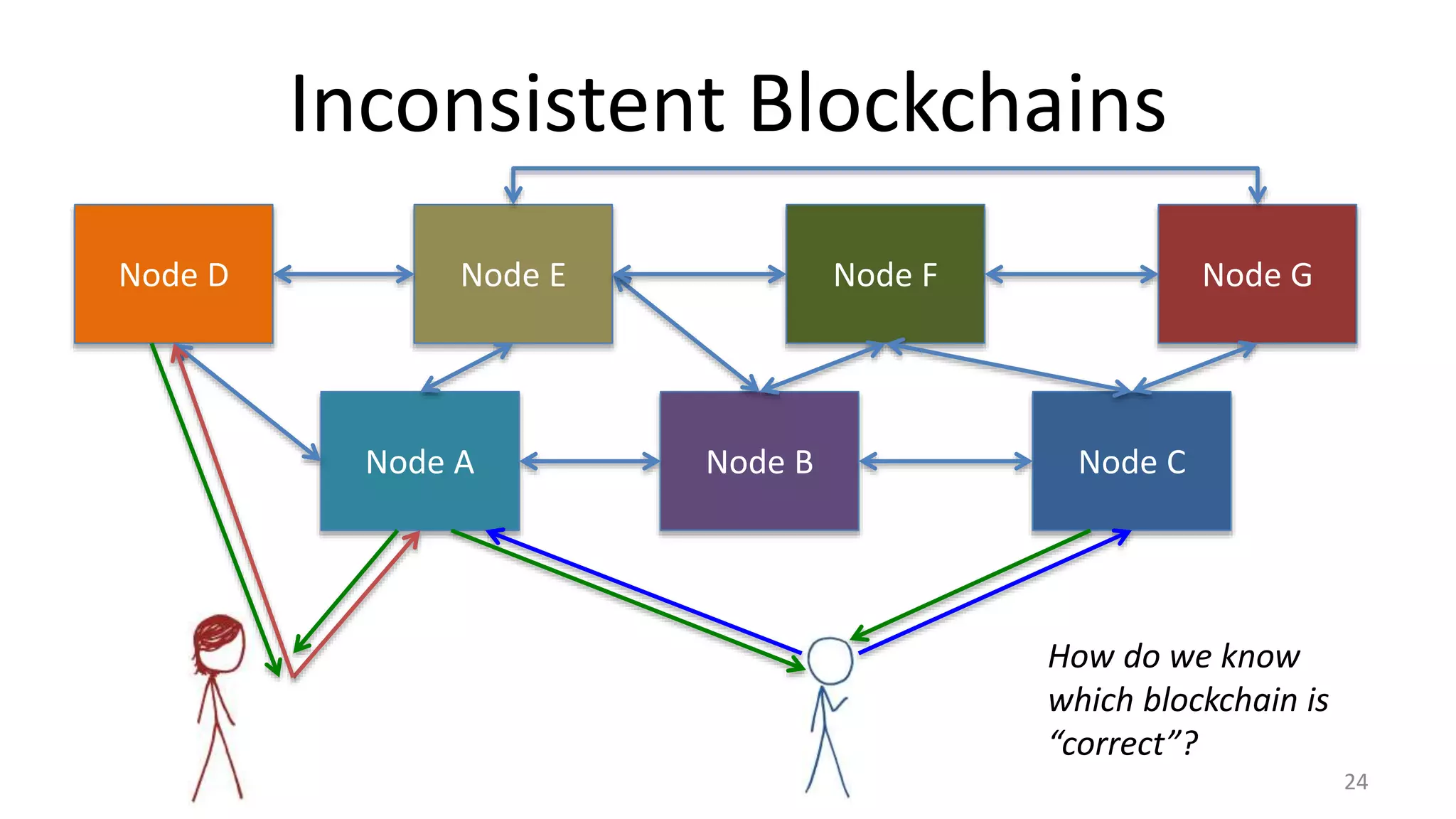
![20
Node A Node B Node C
M = transfer X to Cathy EKRA
[H(M)]
tc
tc
tc tc
BAD!
t
Transactions
1 tb (X->Bob)
Transactions
1 tb (X->Bob)
Transactions
1 tc (X->Cathy)](https://image.slidesharecdn.com/class6-inked-150202145534-conversion-gate02/75/Proofs-of-Work-21-2048.jpg)