Assignment 1 iap
IP Addressing and Subnetting 1. Write the default Masks for the Class A, Class B and Class C IP addresses. 2. How we can distinguish Class A, Class B, Class C, Class D and Class E IP addresses from each other. Write the range of first octet in decimal and Binary for all the 5 IP address classes. 3. Write the default subnet Masks for the following IP addresses: 4. Write down the three available ranges for assigning Private IP addresses recommended by IANA (Internet Assigned Number Authority). 5. A broadcast address is the one that addresses to all the hosts in any network. State that to create a broadcast address, all the bits of network ID portion or all the bits of host ID portion are set to 1? Write down the broadcast addresses of the networks to which the following IP addresses belong, write network addresses and ranges of their valid IP address too. (No subnetting). 6. Subnet Mask or Custom mask tells us that how many bits are used for Subnet ID portion and how many for host ID portion. Identify how many bits are used for sub netting in the following IP address using its subnet mask: 7. Extract the Network Addresses of the given IP addresses in question number 8, using the subnet masks given with them. (Remember that ANDing the IP address with the Mask extracts the network address from the given IP address). 8. Suppose you have a class C Network 208.94.115.0. Your task is to design a subnet scheme so that we can create 16 Network segments (subnets) within this Network. Each subnet should support 10-14 hosts. 9. Suppose you have a class C Network 220.94.115.0. Your task is to design a subnet scheme so that we can create 28 Network segments (subnets) within this Network. Each subnet should support hosts as given below. • 2 Network Segment support 30 Hosts • 4 Network Segment support 14 Hosts • 8 Network Segment support 6 Hosts • 14 Network Segment support 2 Hosts
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Similar to Assignment 1 iap
Similar to Assignment 1 iap (20)
More from university of Gujrat, pakistan
More from university of Gujrat, pakistan (20)
Recently uploaded
Recently uploaded (20)
Assignment 1 iap
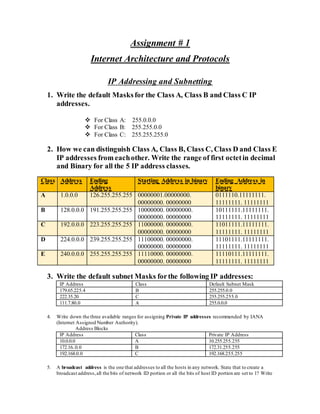
- 1. Assignment # 1 Internet Architecture and Protocols IP Addressing and Subnetting 1. Write the default Masks for the Class A, Class B and Class C IP addresses. For Class A: 255.0.0.0 For Class B: 255.255.0.0 For Class C: 255.255.255.0 2. How we can distinguish Class A, Class B, Class C, Class D and Class E IP addresses from eachother. Write the range of first octetin decimal and Binary for all the 5 IP address classes. Class Address Ending Address Starting Address in binary Ending Address in binary A 1.0.0.0 126.255.255.255 00000001.00000000. 00000000. 00000000 0111110.11111111. 11111111. 11111111 B 128.0.0.0 191.255.255.255 10000000. 00000000. 00000000. 00000000 10111111.11111111. 11111111. 11111111 C 192.0.0.0 223.255.255.255 11000000. 00000000. 00000000. 00000000 11011111.11111111. 11111111. 11111111 D 224.0.0.0 239.255.255.255 11100000. 00000000. 00000000. 00000000 11101111.11111111. 11111111. 11111111 E 240.0.0.0 255.255.255.255 11110000. 00000000. 00000000. 00000000 11110111.11111111. 11111111. 11111111 3. Write the default subnet Masks forthe following IP addresses: IP Address Class Default Subnet Mask 179.65.225.4 B 255.255.0.0 222.35.20 C 255.255.255.0 111.7.80.0 A 255.0.0.0 4. Write down the three available ranges for assigning Private IP addresses recommended by IANA (Internet Assigned Number Authority). Address Blocks IP Address Class Private IP Address 10.0.0.0 A 10.255.255.255 172.16..0.0 B 172.31.255.255 192.168.0.0 C 192.168.255.255 5. A broadcast address is the one that addresses to all the hosts in any network. State that to create a broadcast address,all the bits of network ID portion or all the bits of host ID portion are set to 1? Write
- 2. down the broadcast addresses ofthe networks to which the following IP addresses belong,write network addresses and ranges of their valid IP address too.(No subnetting) IP Address Network Address Broadcast Address 129.65.225.4 129.65.0.0 129.65.255.255 211.35.20.18 211.35.20.0 211.35.20.255 180.47.115.6 180.47.0.0 180.47.255.255 6. Subnet Mask or Custom mask tells us that how many bits are used for Subnet ID portion and how many for host ID portion. Identify how many bits are used for sub netting in the following IP address using its subnet mask: IP Address Subnet Mask Binary Subnet ID bits Host ID bits 135.65.225.4 255.255.240.0 255.255.11110000.0 20 12 210.35.20.18 255.255.255.248 255.255.255.11111000 29 3 190.47.115.6 255.255.254.0 255.255.11111110.0 23 9 7. Extract the Network Addresses of the given IP addresses in question number 8, using the subnet masks given with them. (Remember that ANDing the IP address with the Mask extracts the network address from the given IP address). 1- IP Address 135.65.11100001.4 Subnet Mask 255.255.11110000.0 After AND Network Address 135.65.11100000.0 135.65.224.0 2- IP Address 210.35.20.00010010 Subnet Mask 255.255.255.11111000 After AND Network Address 210.35.20.00010000 210.35.20.16 3- IP Address 190.47.01110011.6 Subnet Mask 255.255.11111110.0 After AND Network Address 190.47.01110010.0 190.47.114.0 8. Which of the following Subnet masks would allow a class A network to allow subnets to have up to 150 hosts and allow for up to 164 subnets? a. 255.0.0.0 b. 255.255.255.0 c. 255.255.192.0 d. 255.255.240.0 e.255.255.252.0 For allowing 150 hosts minimum 8 bits of host part should be available. And for allowing 164 subnets 8 bits are minimal required. All of these will allow to have up to 8 host’s bits and 8 network bits available. According to the formula 2n >= required hosts For Hosts 2n >= required subnets For Subnets 9. Suppose you have a class C Network 208.94.115.0. Your task is to design a subnet scheme so that we can create 16 Network segments (subnets)within this Network. Each subnet should support 10-14 hosts. 2n >= 14 24 >= 14 16 > 14 So, n = 4. a. How many bits would you use for the subnet ID? 28 bits are used for subnet ID. b. How many bits would you use for the Host ID? 4 bits are used for Host ID c. How many maximum possible subnets will be there?
- 3. 24 subnets are possible because we have 8 bits for Host ID. So, 16 maximum subnets are possible. d. How many maximum possible hosts will be there in each subnet? 24 subnets are possible because we have 8 bits for Host ID. So, 16 maximum hosts are possible per subnet. e. Write down the Subnet Mask of your scheme. 208.94.115.11110000 255.255.255.240 f. Write down All the valid IP addresses Valid IP’s 208.94.115.0/28 208.94.115.16/28 208.94.115.32/28 208.94.115..48/28 208.94.115.64/28 208.94.115.80/28 208.94.115.96/28 208.94.115.112/28 208.94.115.128/28 208.94.115.160/28 208.94.115.176/28 208.94.115.192/28 208.94.115.208/28 208.94.115.224/28 208.94.115.240/28 g. The broadcast address ofthe First subnet ofyour scheme. 208.94.115.15 /28 10. Suppose you have a class C Network 220.94.115.0. Your task is to design a subnet scheme so that we can create 28 Network segments (subnets)within this Network. Each subnet should support hosts as given below. Steps 1- Write IP 220.94.115.0 2- Convert to binary 220.94.115.00000000 3- Find n 2n >= max host value 2n >= 30 25 >= 30 N=5 4- Give bits to network 220.94.115.11100000 5- IP of this network 220.94.115.224 6- Subnet Mask of IP 255.255.255.224/27
- 4. 7- Subnets 220.94.115.0/27 220.94.115.32/027 220.94.115.64/027 220.94.115.96/027 220.94.115.128/027 220.94.115.160/027 220.94.115.192/027 220.94.115.224/027 These are the network segments that can be created. Each subnet will support up to 32 hosts. To make the 28 segments we can use Class A or B for more segments.