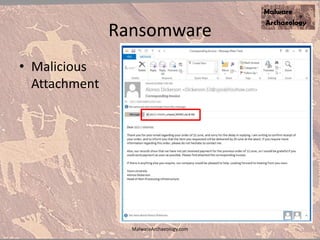
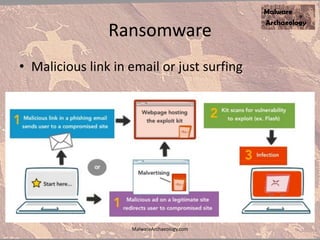
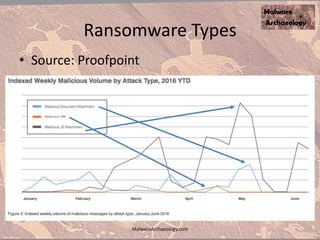
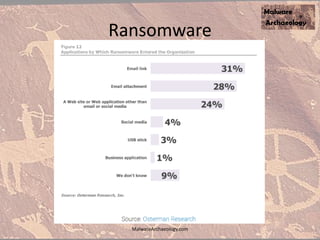
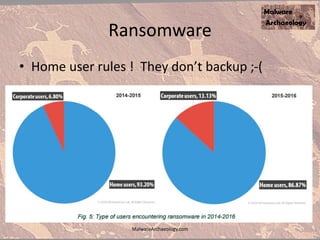
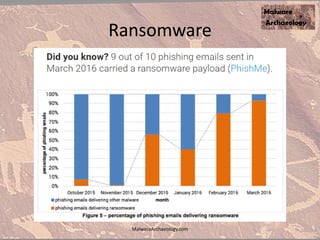
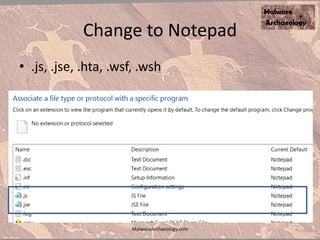
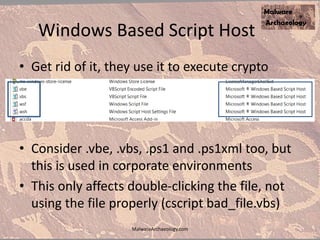
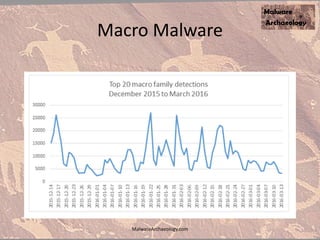
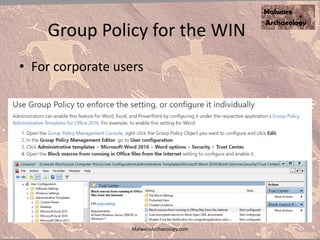
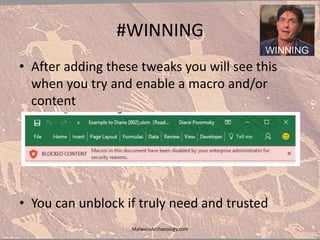
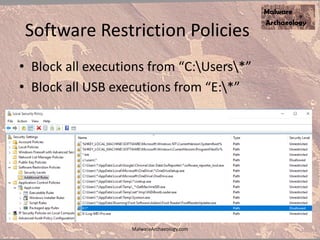
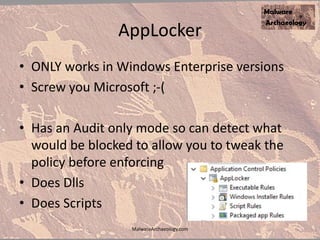
The document discusses the rise of ransomware and its prevention strategies, emphasizing the inadequacy of traditional antivirus solutions against script-based attacks. It highlights the importance of configuring systems to block script execution and suggests specific Windows settings and policies to curb ransomware infections significantly. Additionally, it provides resources for system auditing and monitoring to detect and manage malware threats effectively.