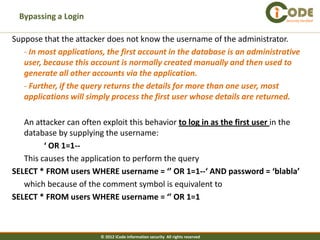
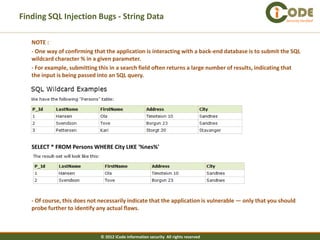
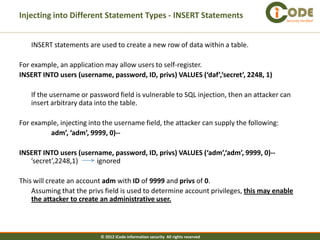
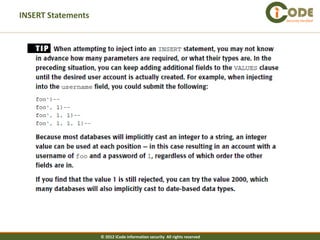
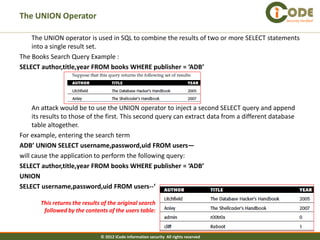
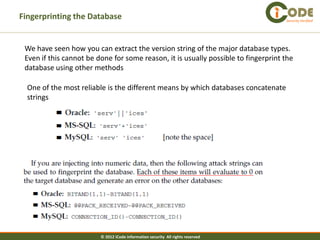
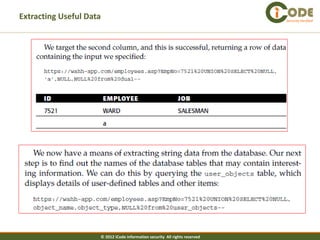
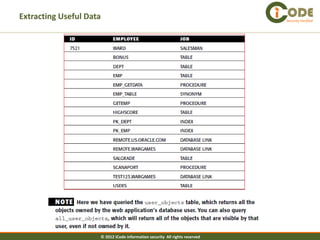
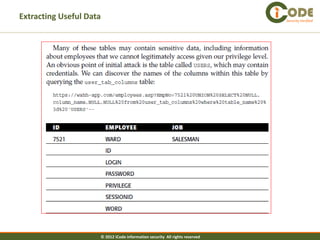
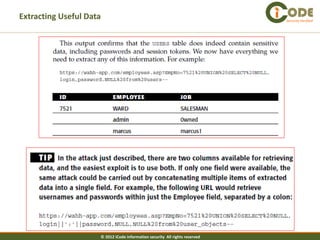
The document discusses SQL injection vulnerabilities in web applications. It provides examples of how SQL injection can be used to extract all data from a database, bypass login authentication by modifying SQL queries, and insert arbitrary data into a database by exploiting vulnerabilities in INSERT statements. The document emphasizes that both string and numeric data needs to be validated to prevent SQL injection attacks.