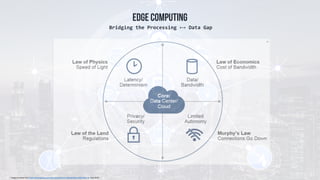
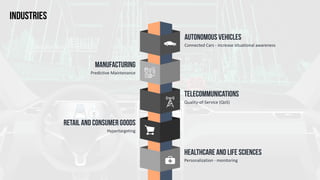
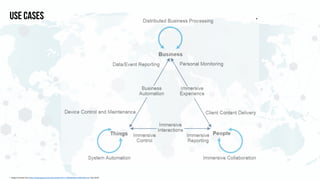
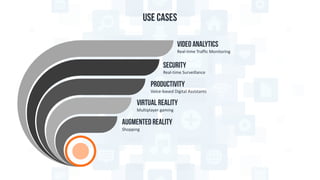
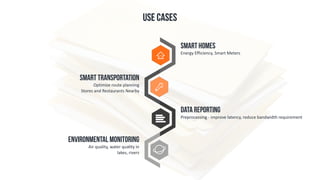
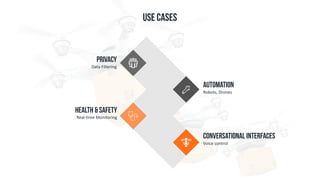
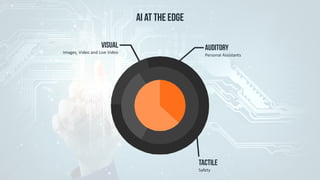
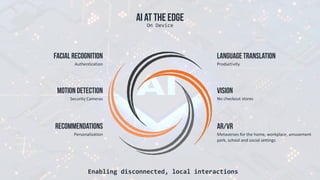
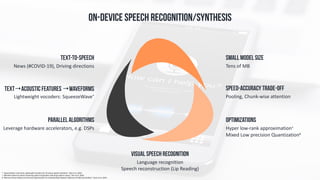
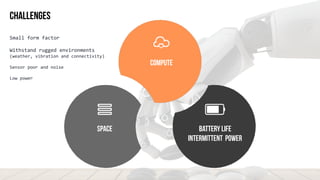
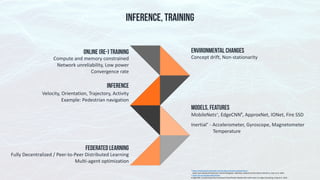
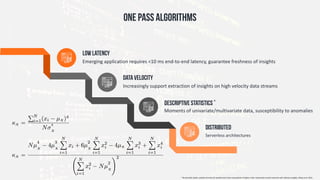
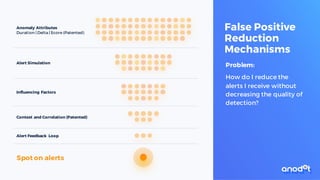
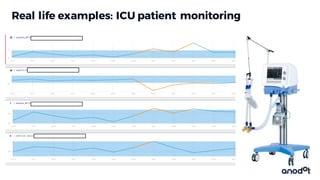
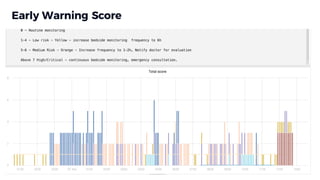
The document discusses edge computing, highlighting its role in anomaly detection and its potential to reduce network traffic by processing data closer to the source. It outlines various use cases across industries such as healthcare, agriculture, and finance, emphasizing the importance of low-latency processing and decentralized systems. Additionally, the document addresses the challenges of implementing edge computing, including data security, network reliability, and the need for efficient algorithms.











![Bloom filter [Bloom 1970] and variants (Neural Bloom Filter)
Count-Min [Cormode and Muthukrishnan 2005] and variants
Filter & COUNT Sketches
Dolha [Zhang et al. 2019], Spotlight [Eswaran et al. 2018]
TCM [Tang et al. 2016], gMatrix [Khan and Aggarwal 2016]
Graph Sketching
Random Sampling/Projections [Mahoney 2011]
Frequent Directions [Ghashami et al. 2016]Matrix Sketching
SKETCHING](https://image.slidesharecdn.com/adattheedge-200625054421/85/Anomaly-Detection-At-The-Edge-29-320.jpg)

![[Kim et al. 2017]
CNN-Variational Autoencoder
[Kim et al. 2017]
Squeezed Convolutional Variational
Autoencoder
[Lu and Lysecky, 2019]
One Class SVM
[Lin et al. 2019]
Edge-Based RNN
[Nguyen et al. 2019]
GRU
[Yang et al. 2019]
Federated XGBoost
MODELS for Anomaly detection at the Edge
Subcomponent timing
FEATURES](https://image.slidesharecdn.com/adattheedge-200625054421/85/Anomaly-Detection-At-The-Edge-31-320.jpg)









![[Mattia et al. 2019]
A Survey on GANs for Anomaly Detection
[Fadhel and Nyarko, 2019]
GAN Augmented Text Anomaly Detection with Sequences
of Deep Statistics
[Wen and Keyes 2019]
Time Series Anomaly Detection Using Convolutional
Neural Networks and Transfer Learning
[Pol et al. 2019]
Anomaly Detection with Conditional
Variational Autoencoders
[Wang et al. 2019]
adVAE: A self-adversarial variational autoencoder
with Gaussian anomaly prior knowledge for
anomaly detection
[Akçay et al. 2018]
GANomaly: Semi-Supervised Anomaly
Detection via Adversarial Training
[Tsukada et al. 2019]
A Neural Network-Based On-device Learning
Anomaly Detector for Edge Devices
[Bhatia et al. 2019]
MIDAS: Microcluster-Based Detector of
Anomalies in Edge Streams
READINGS
[Choudhary et al. 2017]
On the Runtime-Efficacy Trade-off of Anomaly Detection Techniques for Real-Time Streaming Data](https://image.slidesharecdn.com/adattheedge-200625054421/85/Anomaly-Detection-At-The-Edge-50-320.jpg)
![[Huan et al. 2019]
[Puzanov and Cohen 2019]
[Hannon et al. 2019]
[Maciąg et al. 2019]
[Calikus et al. 2019]
[Zhong et al. 2019]
Active anomaly detection in heterogeneous processes
Deep reinforcement one-shot learning for change point detection
Real-time Anomaly Detection and Classification in Streaming PMU Data
Unsupervised Anomaly Detection in Stream Data with Online Evolving Spiking Neural Networks
No Free Lunch But A Cheaper Supper: A General Framework for Streaming Anomaly Detection
Deep Actor-Critic Reinforcement Learning for Anomaly Detection
READINGS](https://image.slidesharecdn.com/adattheedge-200625054421/85/Anomaly-Detection-At-The-Edge-51-320.jpg)
![READINGS
[Nolle et al. 2020[
DeepAlign: Alignment-based Process
Anomaly Correction Using Recurrent
Neural Networks
[Li et al. 2020]
RCC-Dual-GAN: An Efficient Approach for
Outlier Detection with Few Identified
Anomalies
[Ngo et al. 2019]
Fence GAN: Towards Better
Anomaly Detection
[Ngo et al. 2020]
Adaptive Anomaly Detection for IoT Data
in Hierarchical Edge Computing
[Gao et al. 2020]
RobustTAD: Robust Time Series Anomaly Detection via Decomposition and Convolutional Neural Networks](https://image.slidesharecdn.com/adattheedge-200625054421/85/Anomaly-Detection-At-The-Edge-52-320.jpg)

