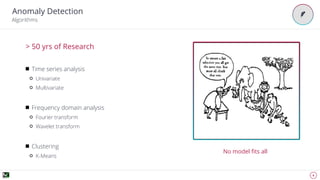
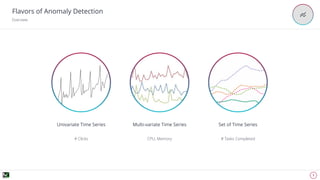
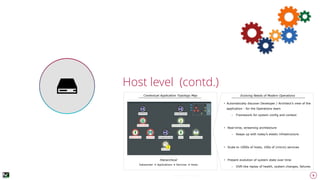
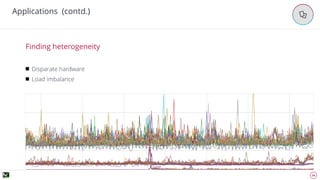
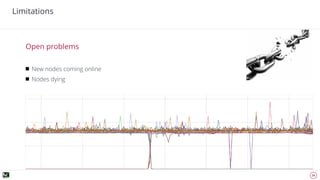
The document discusses advanced techniques for anomaly detection in high-volume data environments, specifically focusing on real-time information consumption and performance monitoring across microservices and clusters. It outlines a scalable, algorithmic approach for identifying performance regressions and discrepancies in system behavior, leveraging historical time series analysis. The presentation also details applications in production environments, challenges in data consistency, and plans for future enhancements in data granularity and classification.