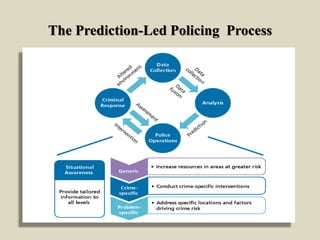
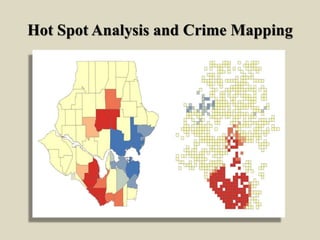
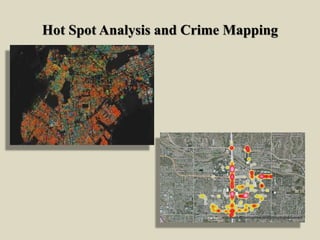
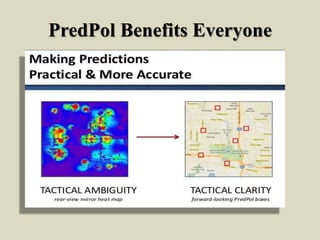
Predictive policing uses statistical analysis and data to predict criminal activity and identify crime patterns in order to prevent future crimes and solve past cases. It relies on the idea that criminals tend to operate within a "comfort zone" and commit similar crimes in similar locations. Predictive policing involves collecting large data sets, analyzing the data to identify crime hot spots or individuals at risk of offending, intervening through police operations, and assessing the results to continue refining predictions. While predictive policing shows promise, its effectiveness depends on proper implementation and action based on predictions, and it has certain limitations in predicting some types of crimes.