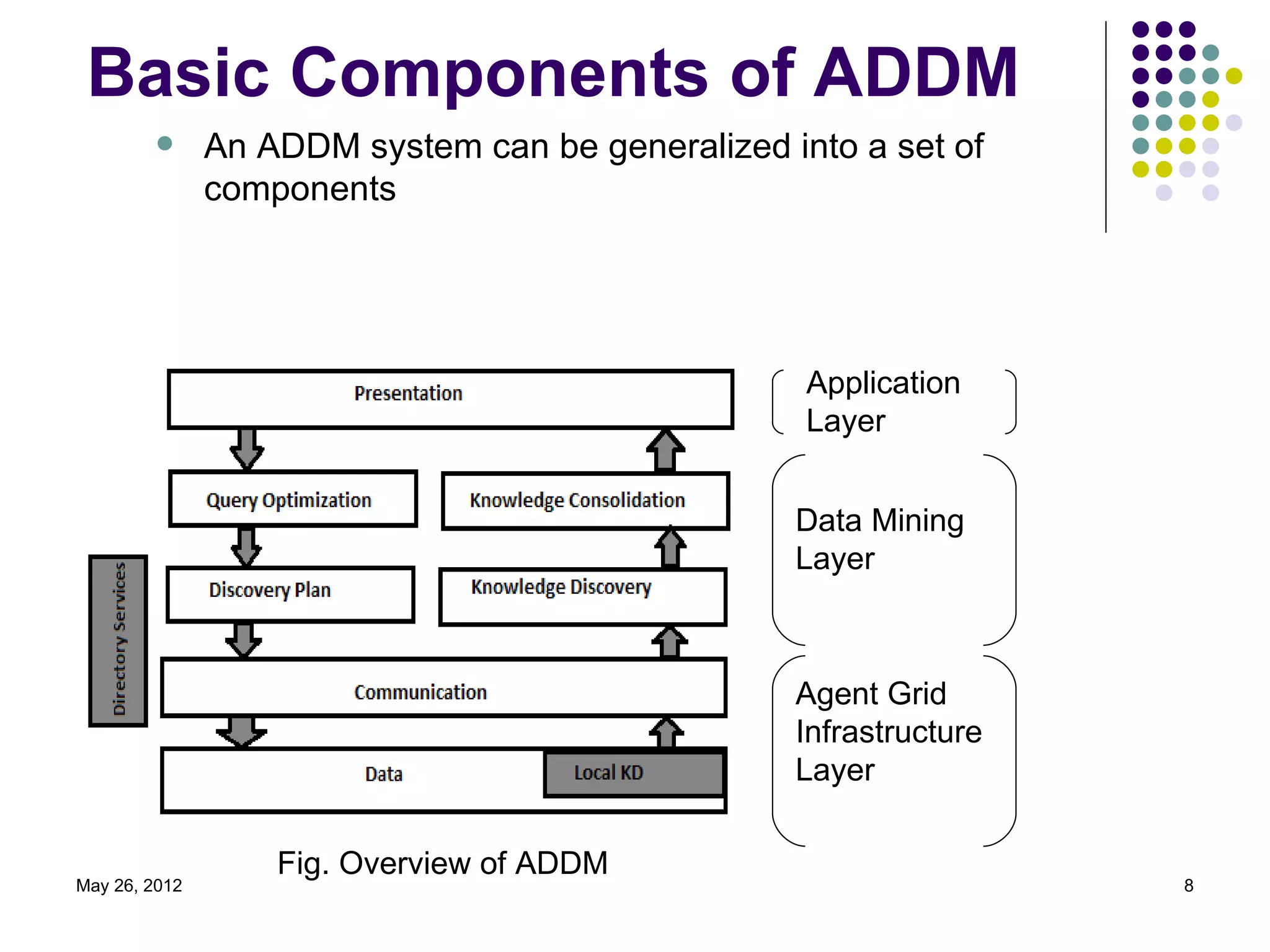
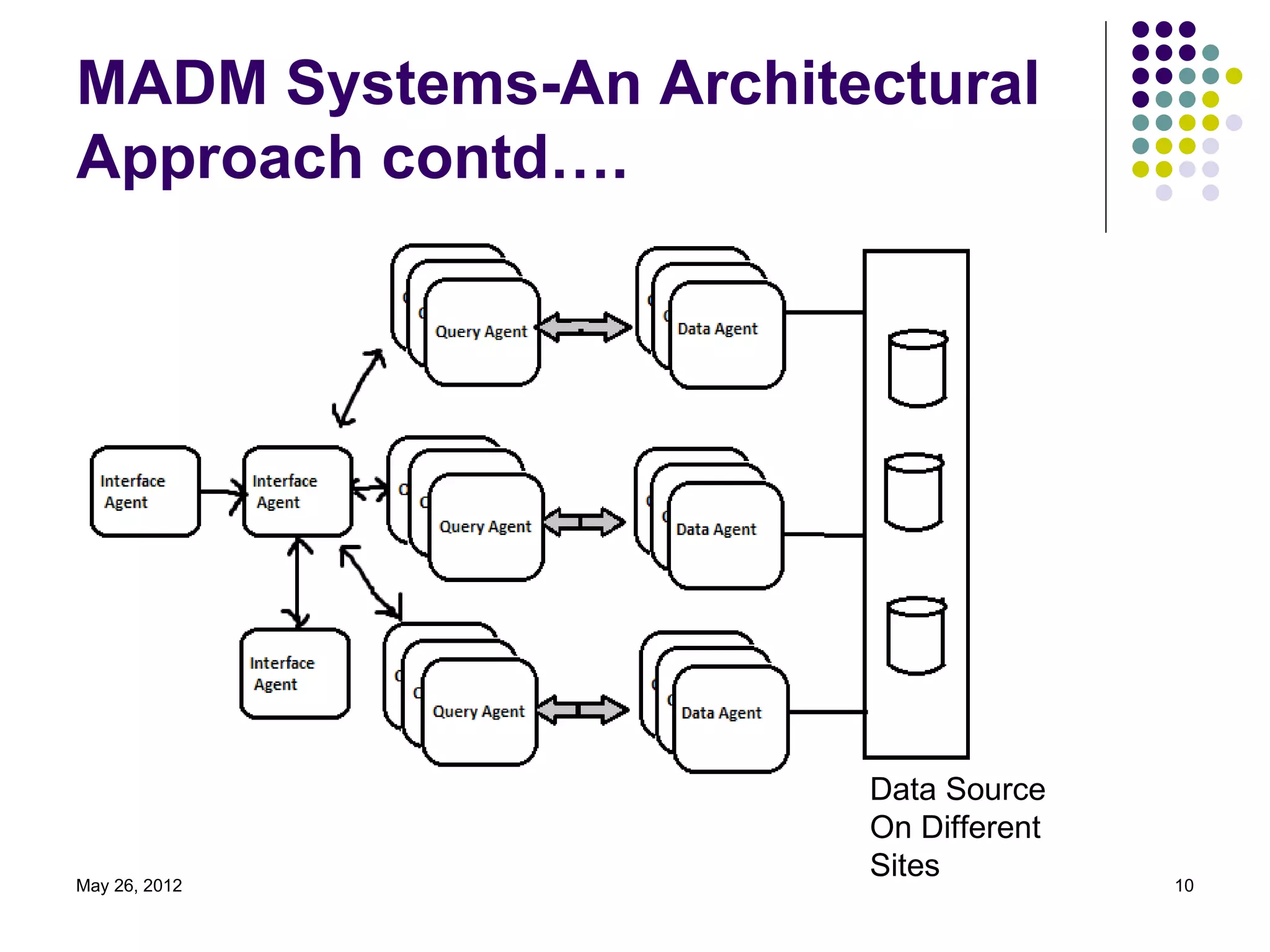
The document presents an overview of multi-agent based decentralized knowledge discovery and agent security. It discusses data mining versus decentralized data mining and the use of agents for distributed data mining. It describes the basic components of agent-based distributed data mining systems including the application layer, data mining layer, and agent grid infrastructure layer. It also discusses multi-agent distributed data mining systems, the roles of different agent types, security issues for agents, and measures to secure agents. Finally, it outlines potential future applications and provides references for further reading.










![References
[1] IJRIC ISSN: 2076-3328 www.ijric.org E-ISSN: 2076-3336 “. Agent based distributed data
mining: AN OVER VIEW “VUDA SREENIVASA RAO, 2009-2010
[2] M. Klusch, S. Lodi, G. Moro. Agent-based Distributed Data Mining: The KDEC Scheme.
Intelligent Information Agents - The AgentLink Perspective. Lecture Notes in Computer Science 2586
Springer 2003.
[3] “Distributed Data Mining and Agents” Josenildo C. da Silva, Chris Giannella, Ruchita Bhargava,
Hillol Kargupta1;, and Matthias Klusch
[4] Y. Xing, M.G. Madden, J. Duggan, G. Lyons. A Multi-Agent System for Context-based Distributed
Data Mining. Technical Report Number NUIG-IT-170503, Department of Information Technology,
NUI, Galway, 2003.
[5] “Agent-Based Data-Mining” Winton Davies 15 August 1994
[6] Priyanka Makkar et. al. / (IJCSE) International Journal on Computer Science and Engineering
Vol. 02, No. 04, 2010, 1237-1244 DISTRIBUTED DATA MINING AND MINING MULTI-AGENT
DATA ,Vuda Sreenivasa Rao, Dr. S Vidyavathi
[7] V. Gorodetsky and I. Kotenko. “The Multiagent Systems for Computer Network Security
Assurance: frameworks and case studies.” In IEEE International Conference on Artificial Intelligence
Systems, 2002, pages 297–302, 2002.
[8] International Journal of Computer Applications (0975 – 8887) Volume 4– No.12, August 2010
23 “A Comparative study of Multi Agent Based and High- Performance Privacy Preserving Data
Mining”, Md Faizan Farooqui, Md Muqeem, Dr. Md Rizwan Beg
[9] Future Generation Computer Systems 23 (2007) 61–68 ,www.elsevier.com/locate/fgcs
“Distributed data mining on Agent Grid: Issues, platform and development toolkit” Jiewen Luoa,b,_,
Maoguang Wangc, Jun Hud, Zhongzhi Shia
[10] Sung W. Baik, Jerzy W. Bala, and Ju S. Cho. Agent based distributed data mining. Lecture
Notes in Computer Science, 3320:42–45, 2004.
[11]Xining Li and Jingbo Ni. Deploying mobile agents in distributed data mining. Lecture Notes in
Computer Science 4819:322–331, 2007 .
May 26, 2012 16
[12]“Mobile agent security” Niklas Borselius Mobile VCE Research Group Information Security Group,
Royal Holloway, University of London Egham, Surrey, TW20 0EX, UK ,Niklas.Borselius@rhul.ac.uk](https://image.slidesharecdn.com/amanmadm-120526045753-phpapp01/75/Distributed-Datamining-and-Agent-System-security-16-2048.jpg)