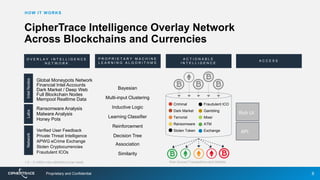
1) CipherTrace provides intelligence, compliance, forensics and security services for cryptocurrencies, crypto assets and blockchains to make them safe and trusted.
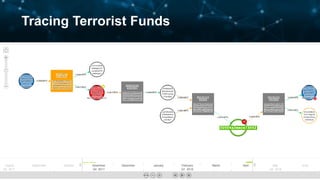
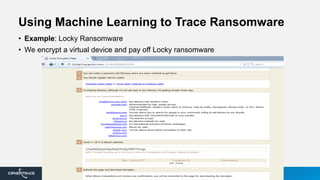
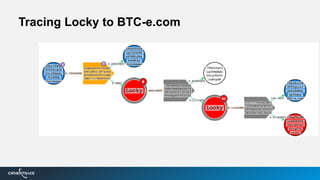
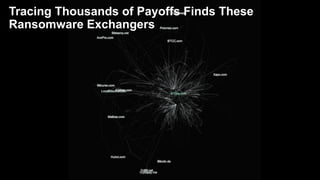
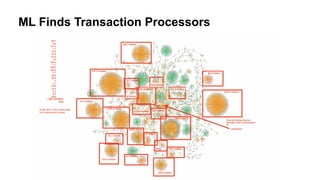
2) They use machine learning algorithms and proprietary intelligence networks to trace criminal activity like ransomware, money laundering, and terrorist funding on blockchains and cryptocurrency exchanges.
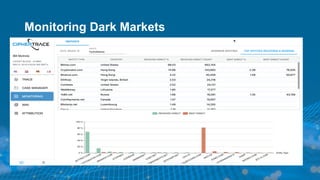
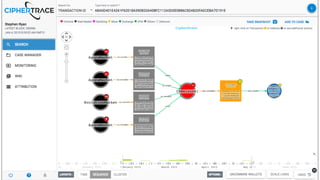
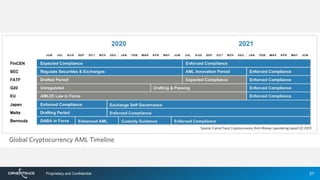
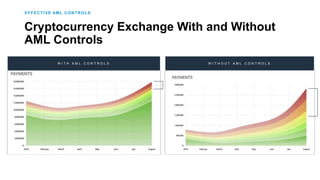
3) By tracing transactions, CipherTrace can identify exchanges, money transmitters, and other businesses that may need enhanced anti-money laundering controls to comply with regulations.





![Proprietary and Confidential 9
[EnExchanger | 2019 Nov | http://www.enexchanger.com]](https://image.slidesharecdn.com/ciphertracerakutennov-2019machinelearningnov07-191126045451/85/AI-and-Machine-Learning-for-Analyzing-Cryptocurrencies-and-the-Blockchain-9-320.jpg)
![Proprietary and Confidential 10
[Coin ATM Rader | 2018 Sep | https://coinatmradar.com/]](https://image.slidesharecdn.com/ciphertracerakutennov-2019machinelearningnov07-191126045451/85/AI-and-Machine-Learning-for-Analyzing-Cryptocurrencies-and-the-Blockchain-10-320.jpg)

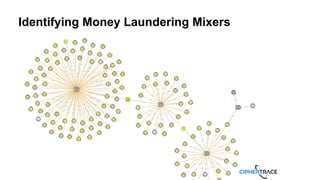
![12Proprietary and Confidential
Tracing Money Laundering
[BITCOIN MIXER | 2019 Nov | https://bitcoinmix.org/]](https://image.slidesharecdn.com/ciphertracerakutennov-2019machinelearningnov07-191126045451/85/AI-and-Machine-Learning-for-Analyzing-Cryptocurrencies-and-the-Blockchain-12-320.jpg)
![[Benjamin Strick at Medium | 2019 Nov | https://medium.com/@benjamindbrown/tracing-syrian-cell-
kidnappers-scammers-finances-through-blockchain-e9c52fb6127d]](https://image.slidesharecdn.com/ciphertracerakutennov-2019machinelearningnov07-191126045451/85/AI-and-Machine-Learning-for-Analyzing-Cryptocurrencies-and-the-Blockchain-14-320.jpg)