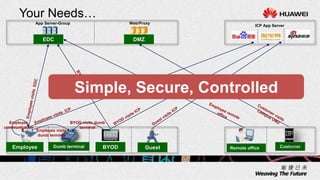
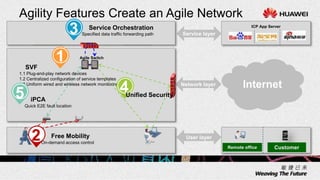
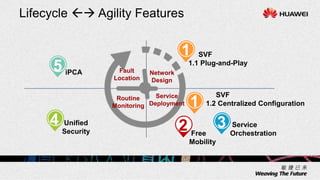
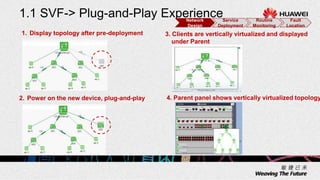
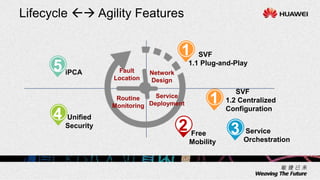
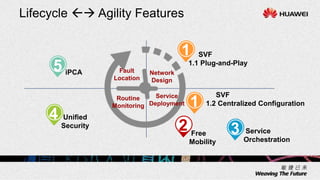
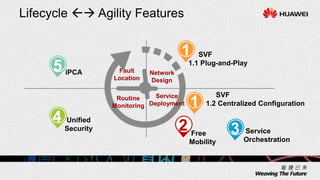
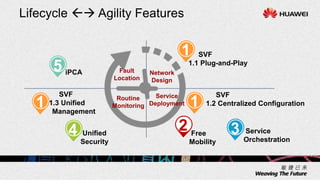
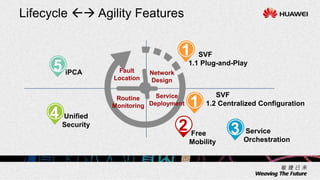
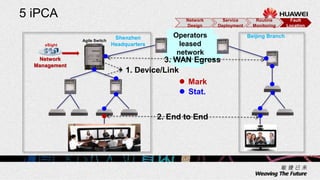
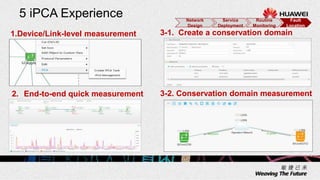
1. The document describes an agile network solution that features plug-and-play deployment, centralized configuration, free user mobility, service orchestration, unified security, and intelligent fault location.
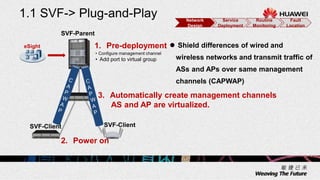
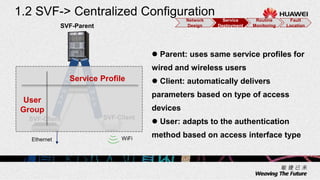
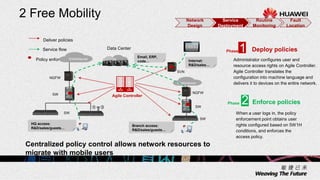
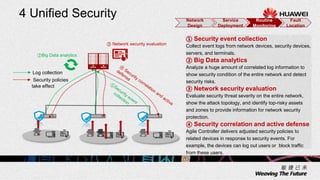
2. The solution allows for automated management channel creation between devices, centralized management of configurations, flexible policy-based access control, and concentration of security resources for improved protection.
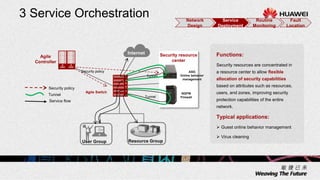
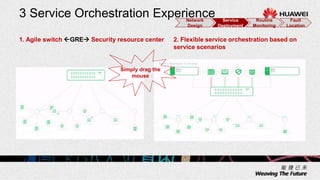
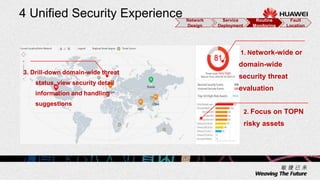
3. Key benefits include easy deployment of new devices, consistent policies for wired and wireless users, mobile access based on user attributes, and network-wide security monitoring, evaluation and response.