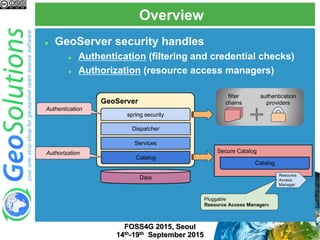
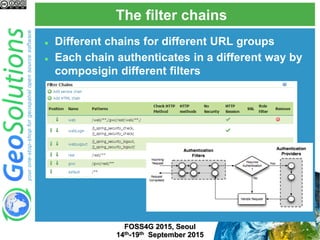
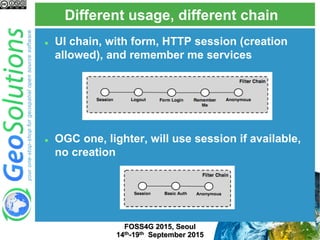
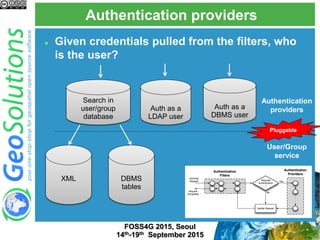
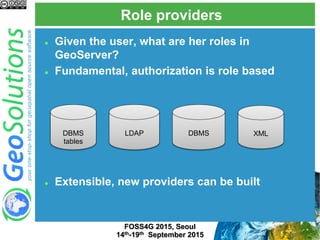
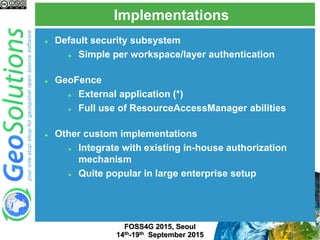
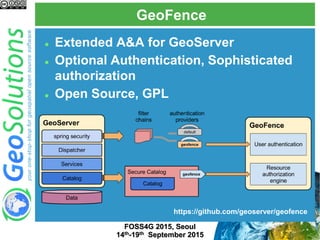
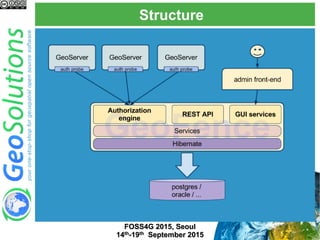
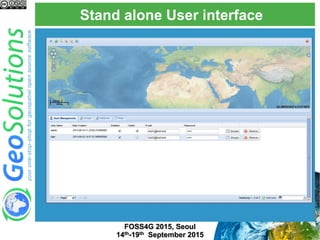
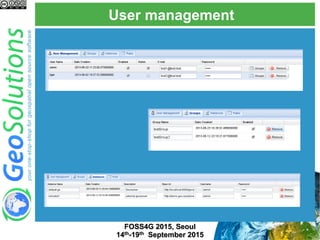
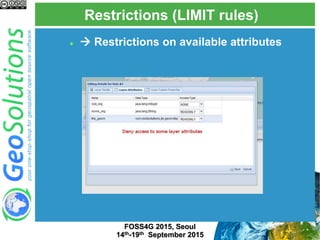
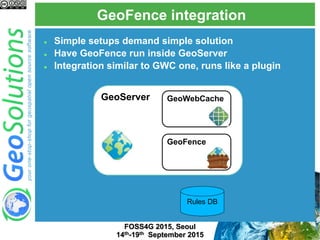
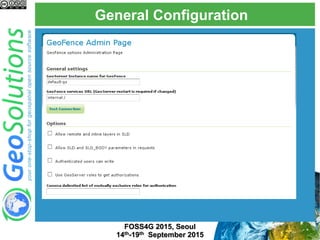
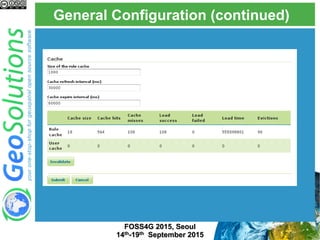
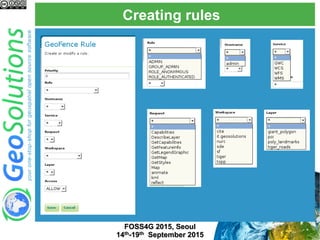
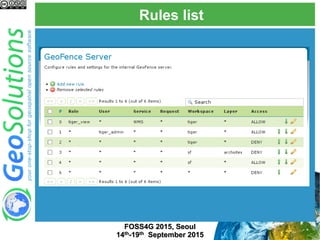
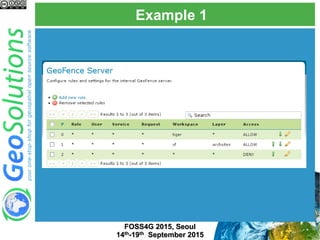
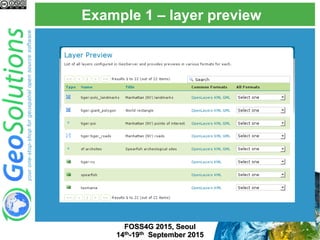
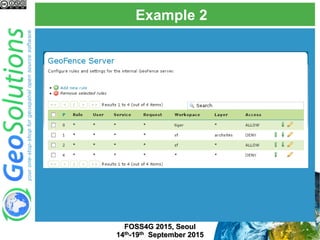
The document discusses advanced security features of GeoServer, focusing on authentication and authorization processes. It outlines various authentication methods, role-based authorization, and the integration of Geofence for enhanced access control. Additionally, it details the configuration and management of rules that dictate user permissions for resource access on GeoServer.