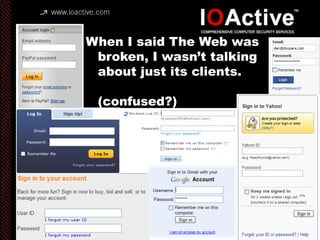
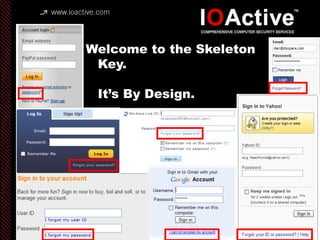
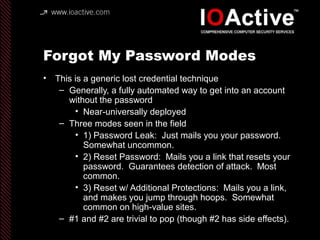
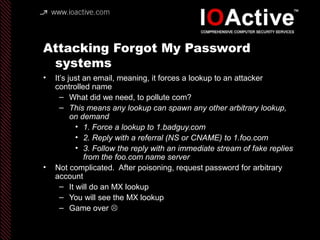
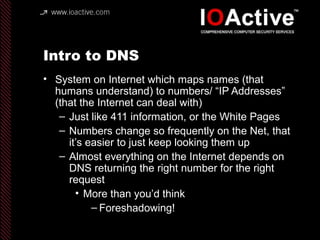
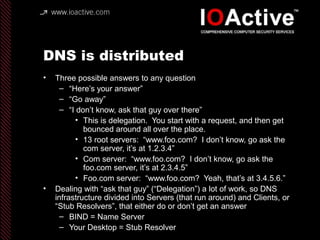
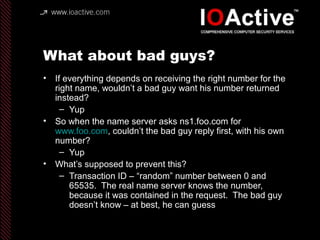
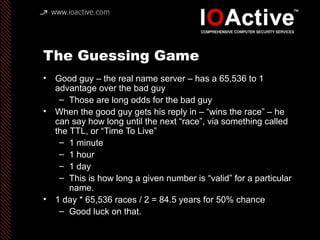
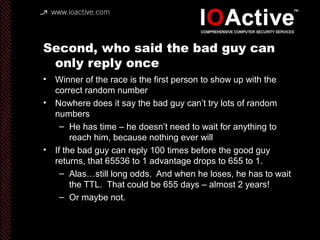
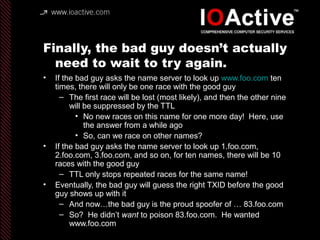
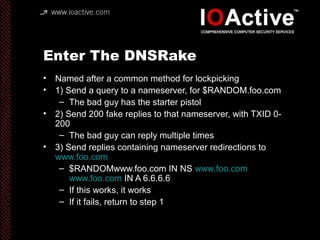
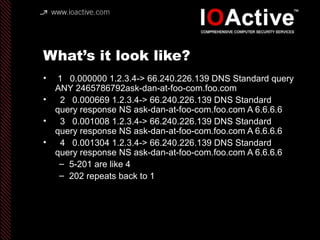
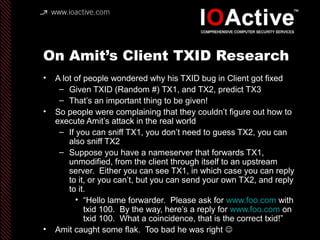
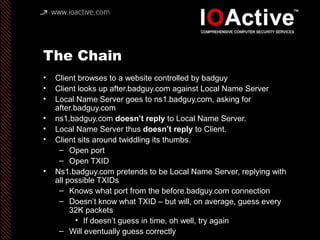
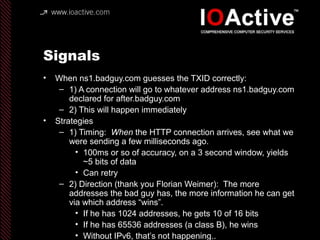
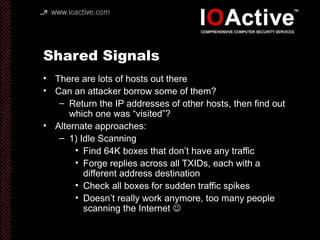
This document summarizes Dan Kaminsky's 2008 talk at Black Hat about a vulnerability he discovered in the Domain Name System (DNS) that allowed attackers to spoof DNS responses. The vulnerability, known as DNS cache poisoning, could allow attackers to redirect traffic to malicious websites by guessing the random transaction ID associated with DNS queries. Kaminsky worked with DNS developers and organizations to coordinate a massive patching effort that updated DNS servers for over 120 million users within a few weeks. His talk analyzed the impact of the patching and discussed the technical details of how the vulnerability worked.


























![Who needs an exploit? Lured by
design, upgraded by design
• Francisco Amato’s EvilGrade
– Implemented modules: ------------------- - Java
plugin - Winzip - Winamp - MacOS -
OpenOffices - iTunes - Linkedin Toolbar - DAP
[Download Accelerator] - notepad++ - speedbit
– Bigger companies than I thought. But
otherwise, yeah, we knew this was going to be
a problem
– Actually warned LinkedIn in advance](https://image.slidesharecdn.com/dmkbo2k8-101127182039-phpapp02/85/Dmk-bo2-k8-60-320.jpg)