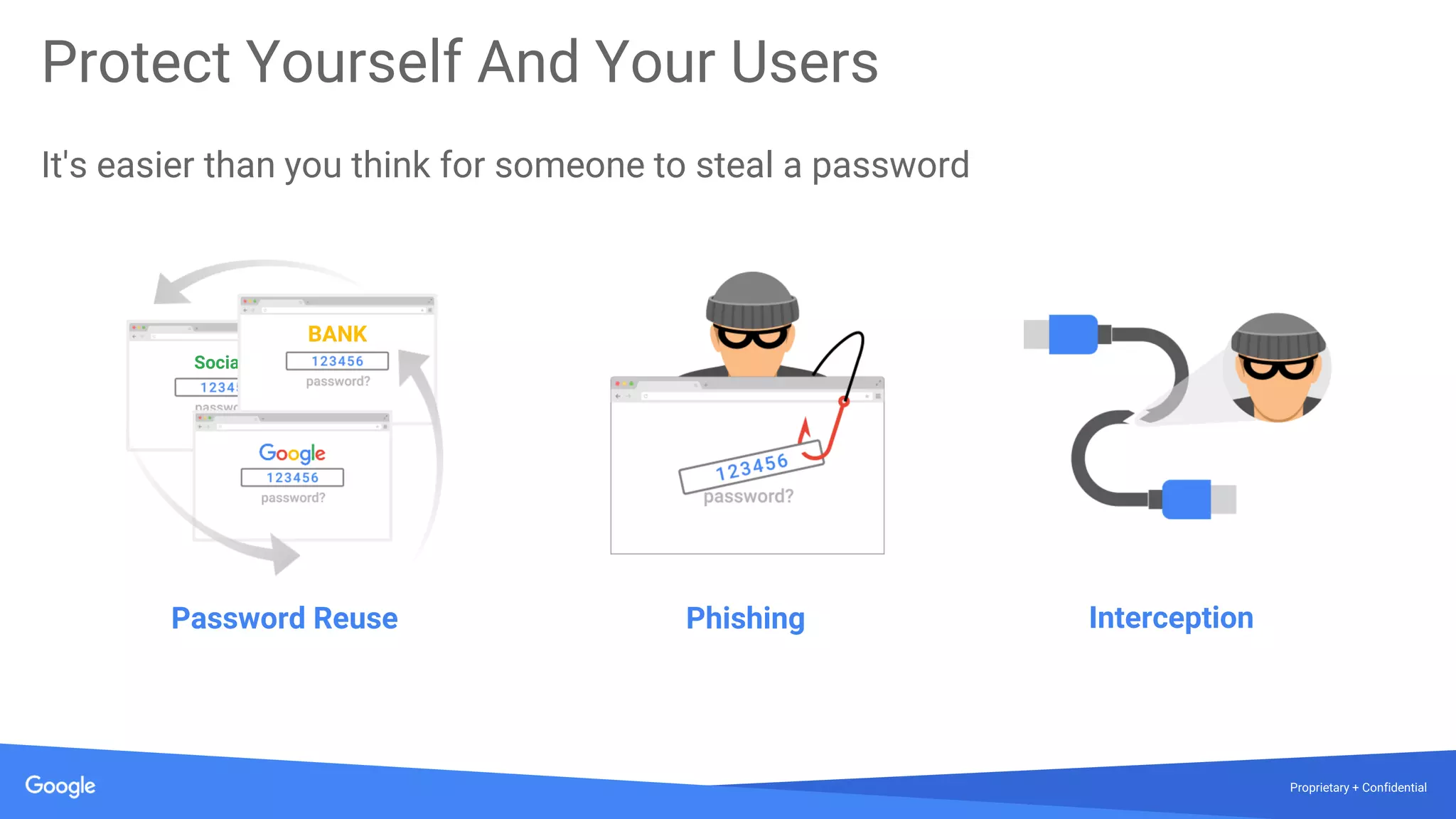
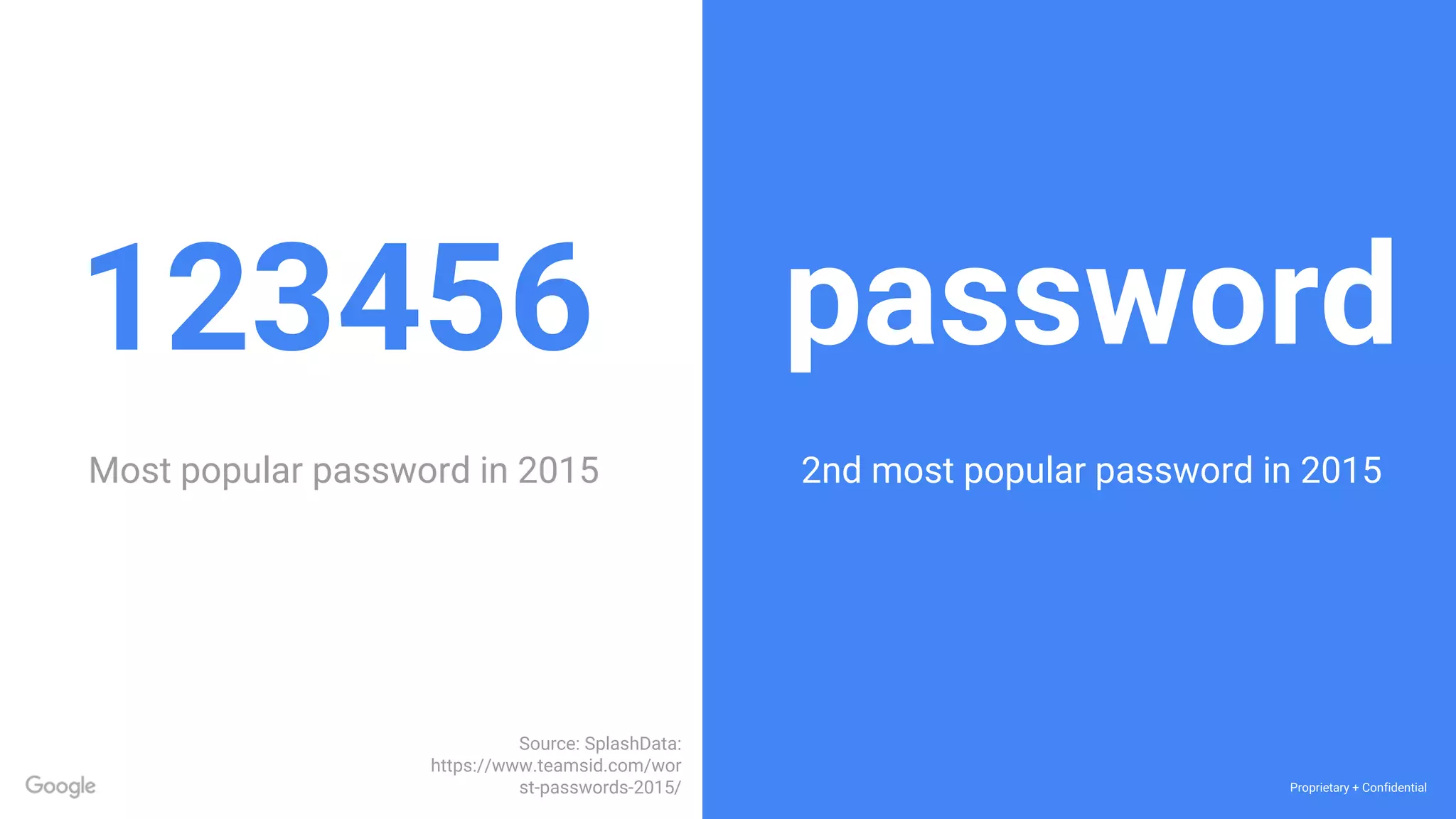
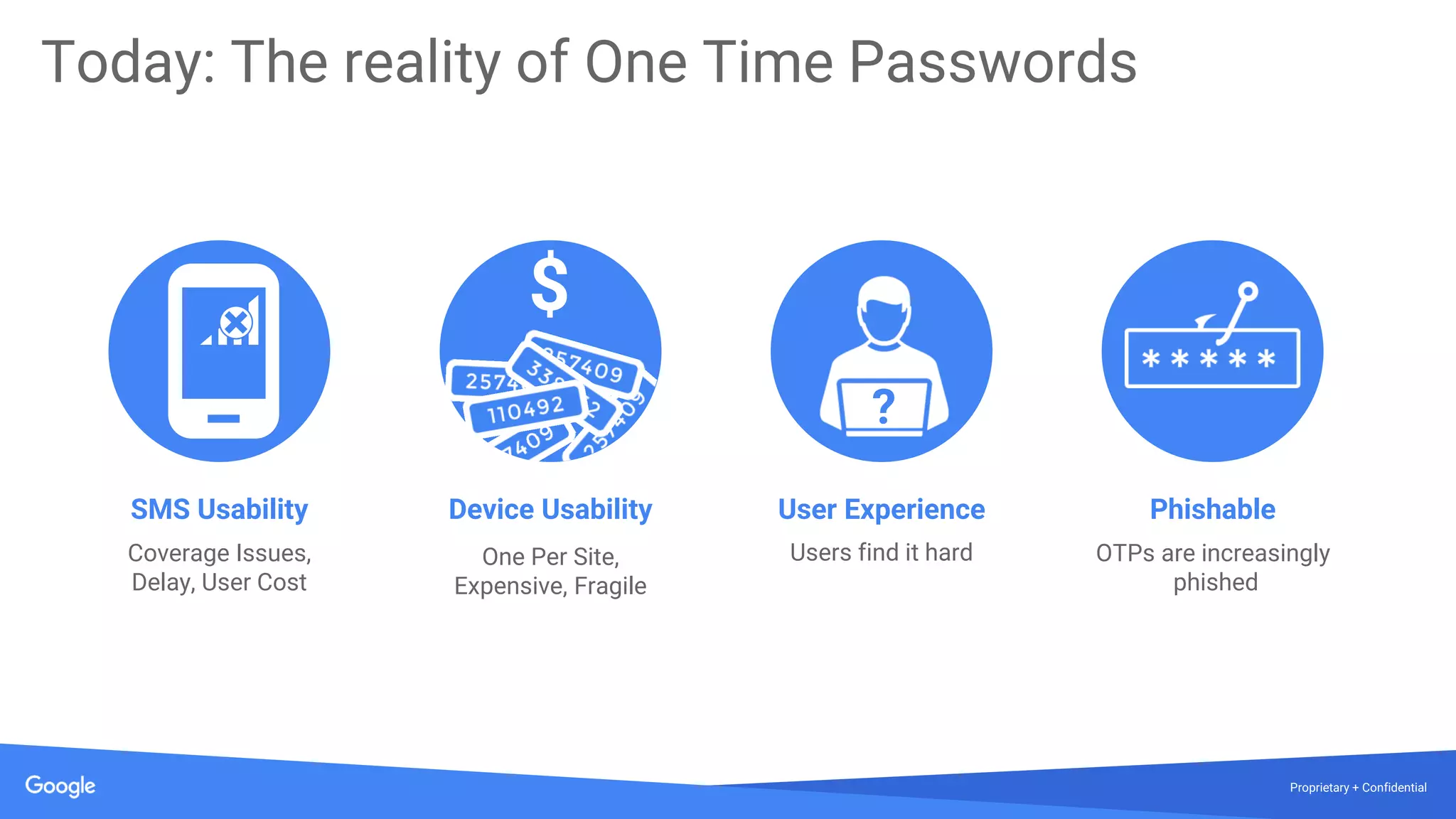
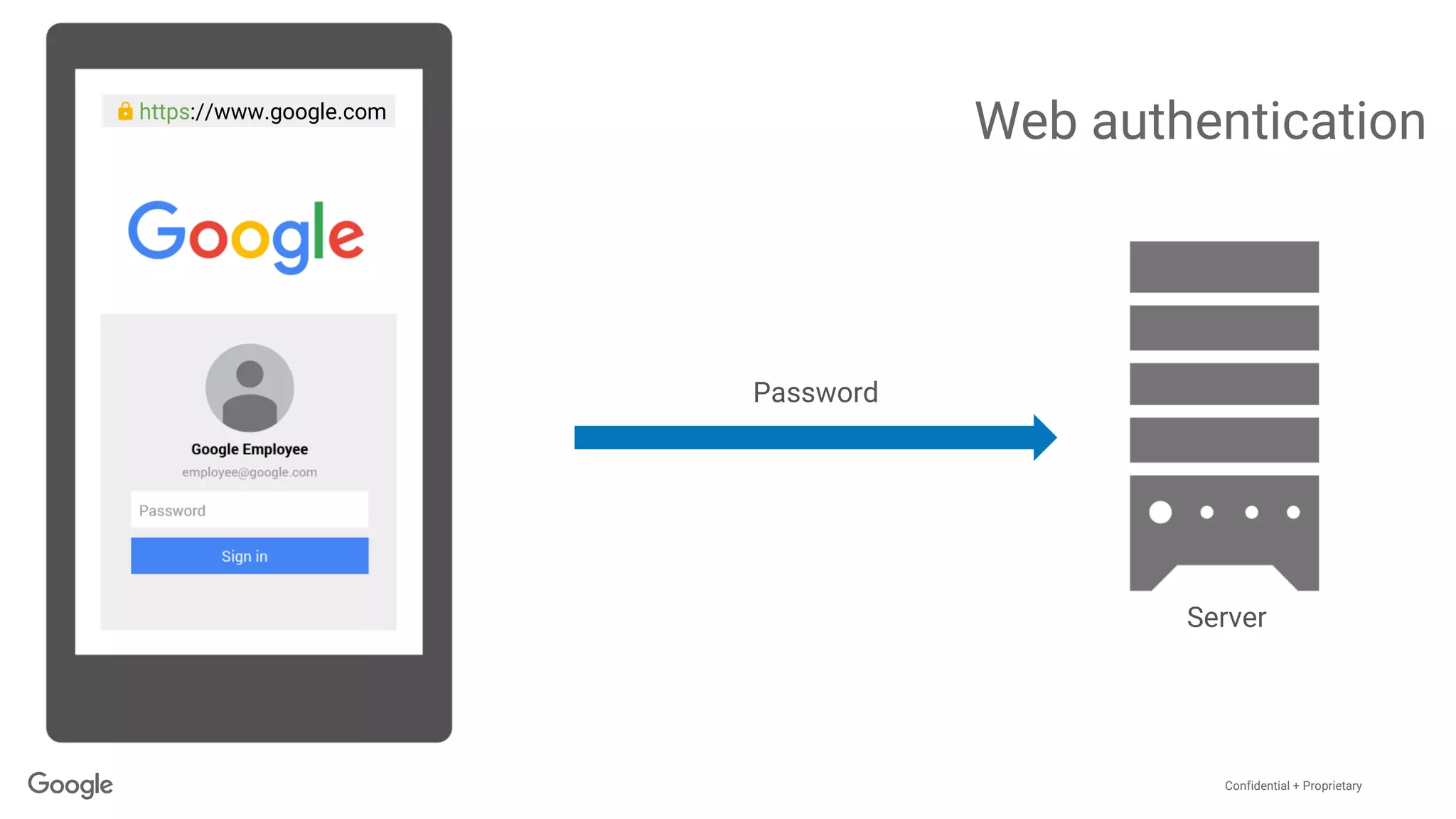
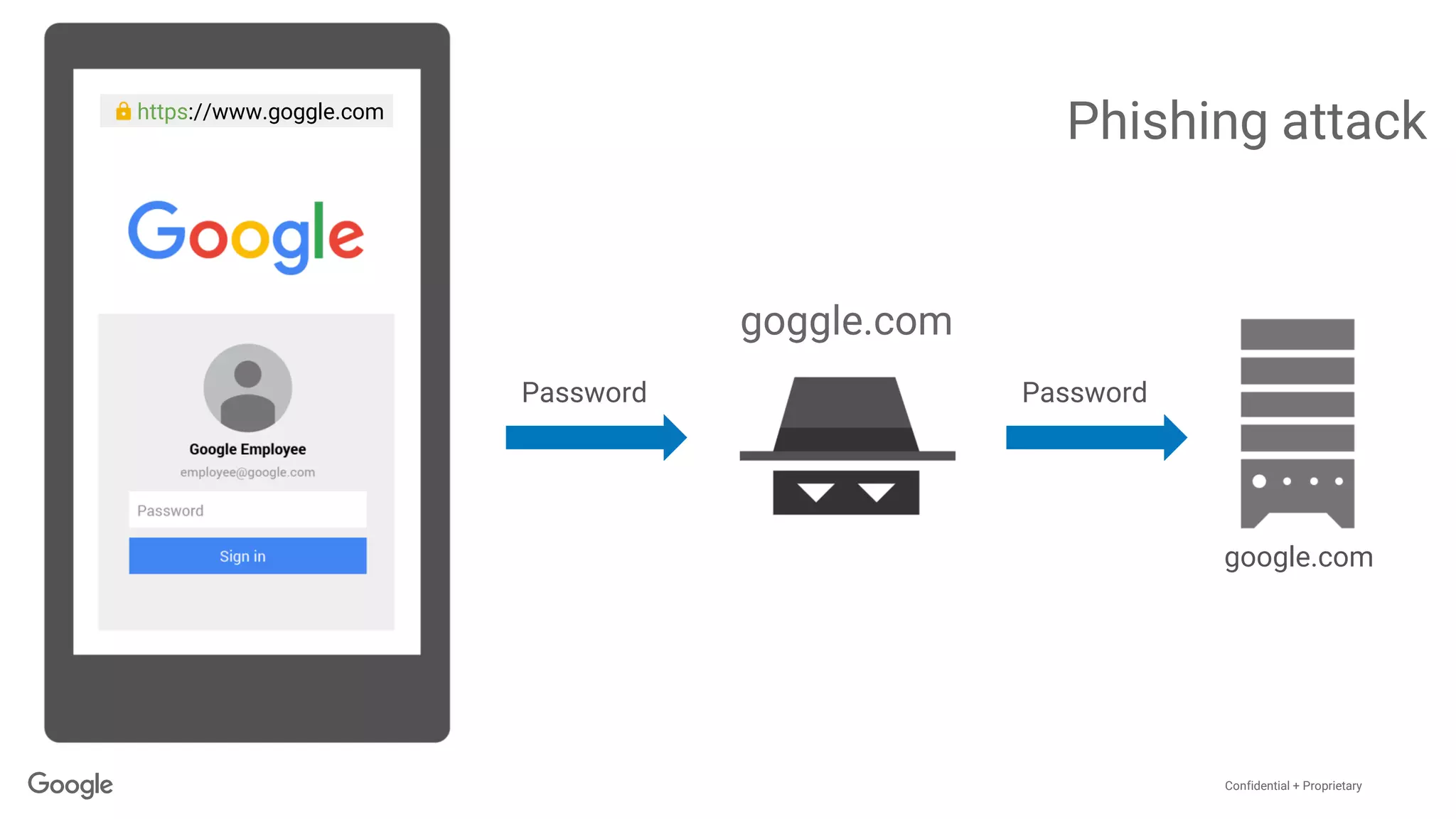
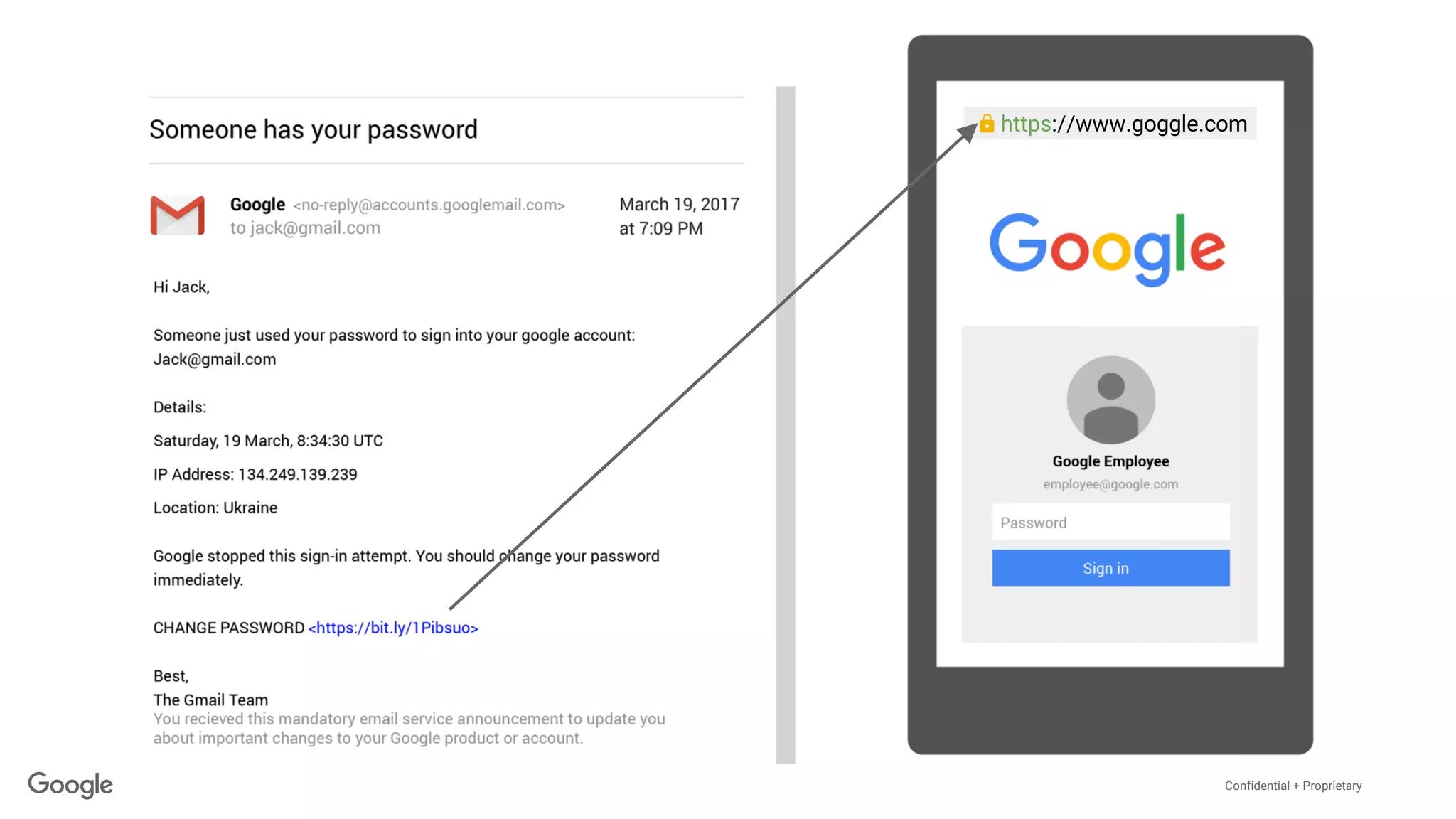
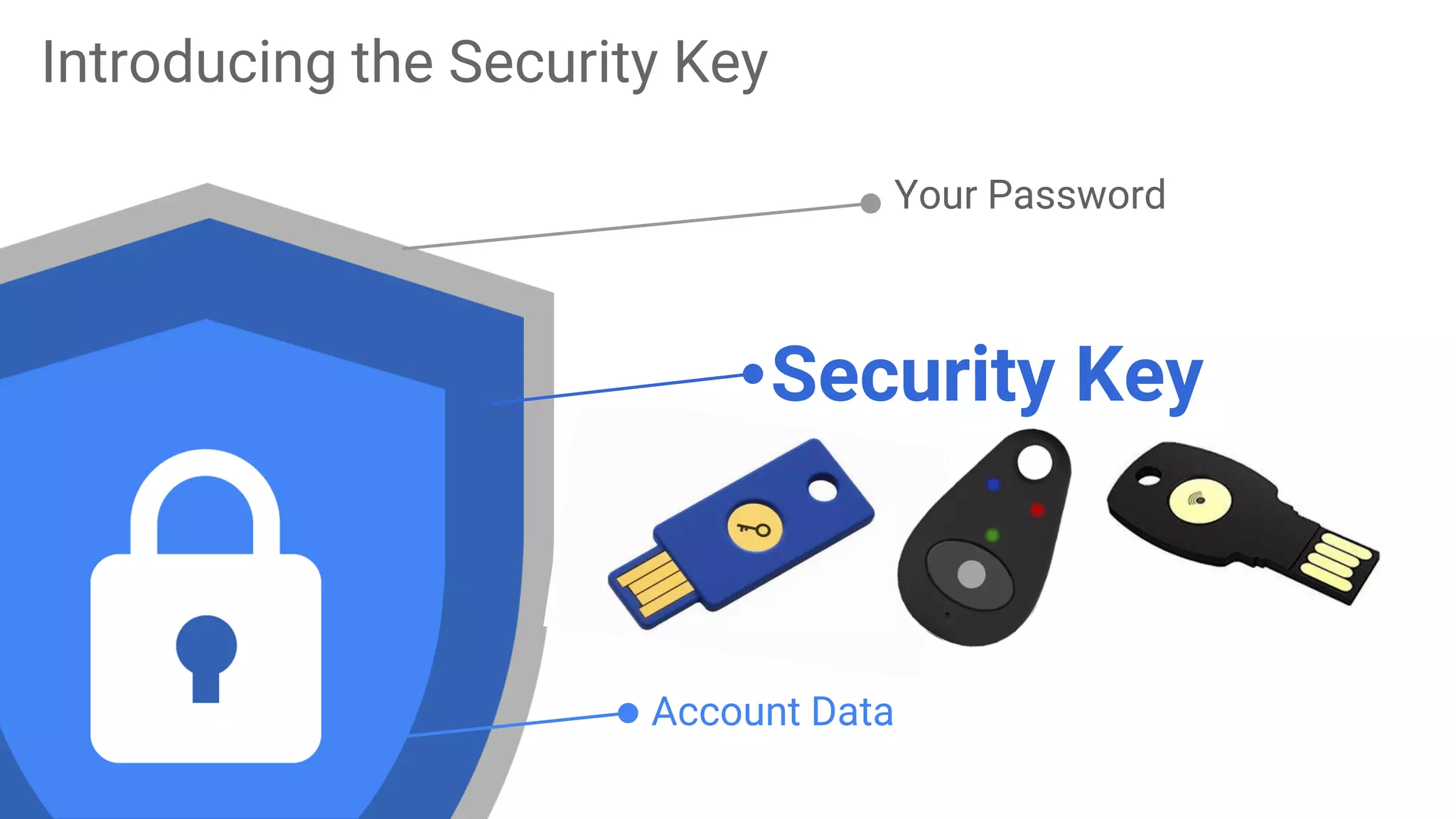
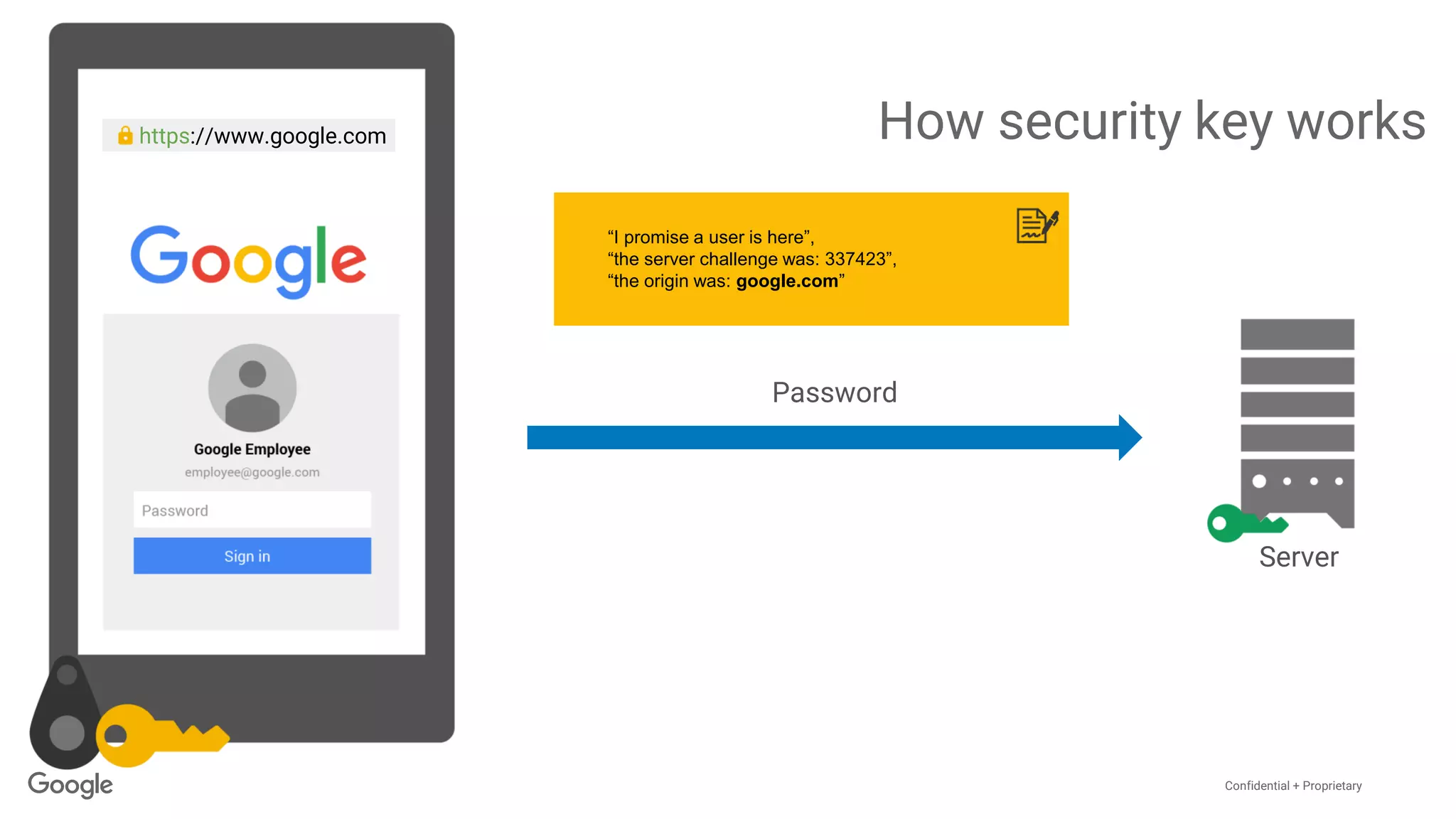
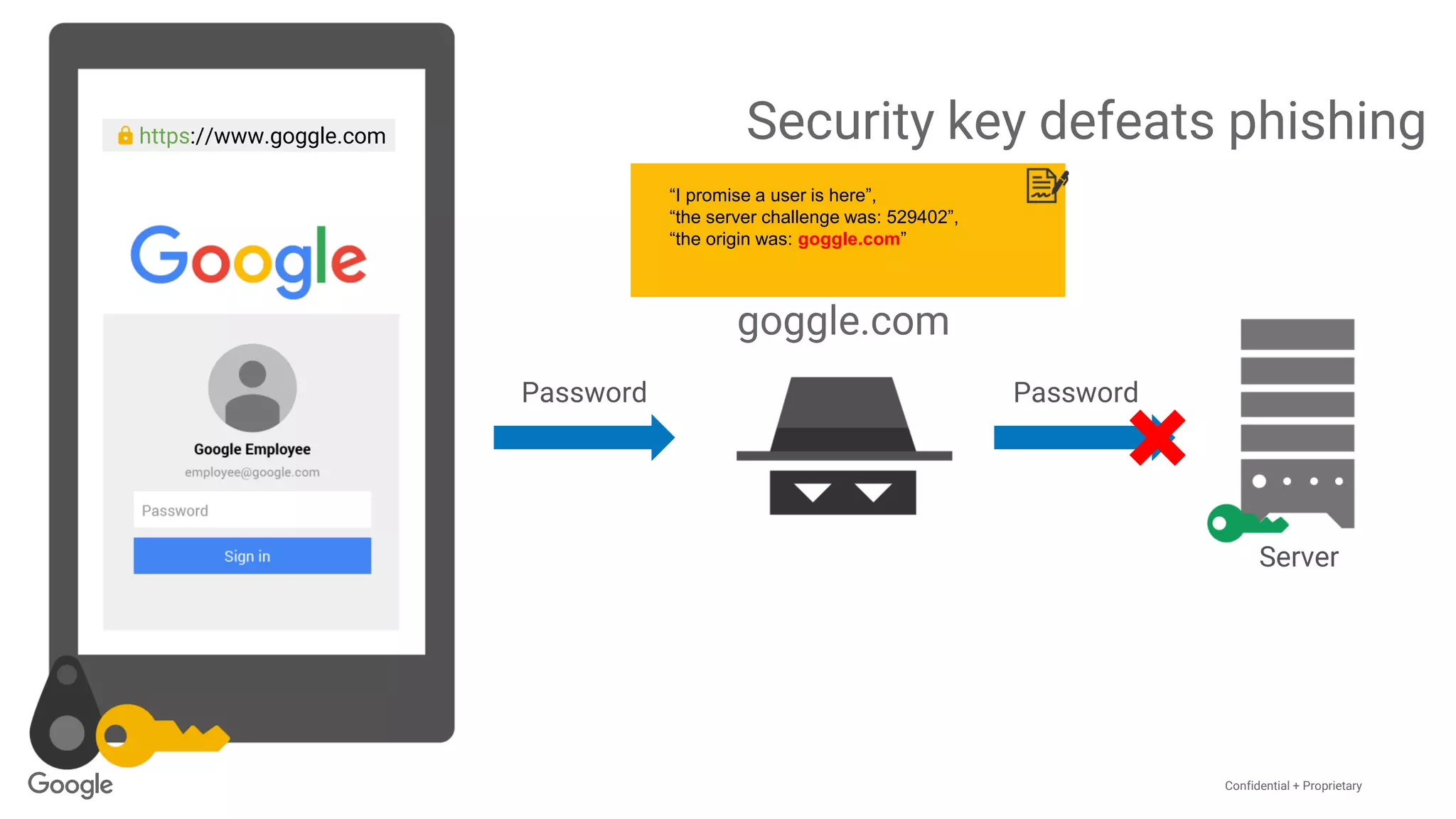
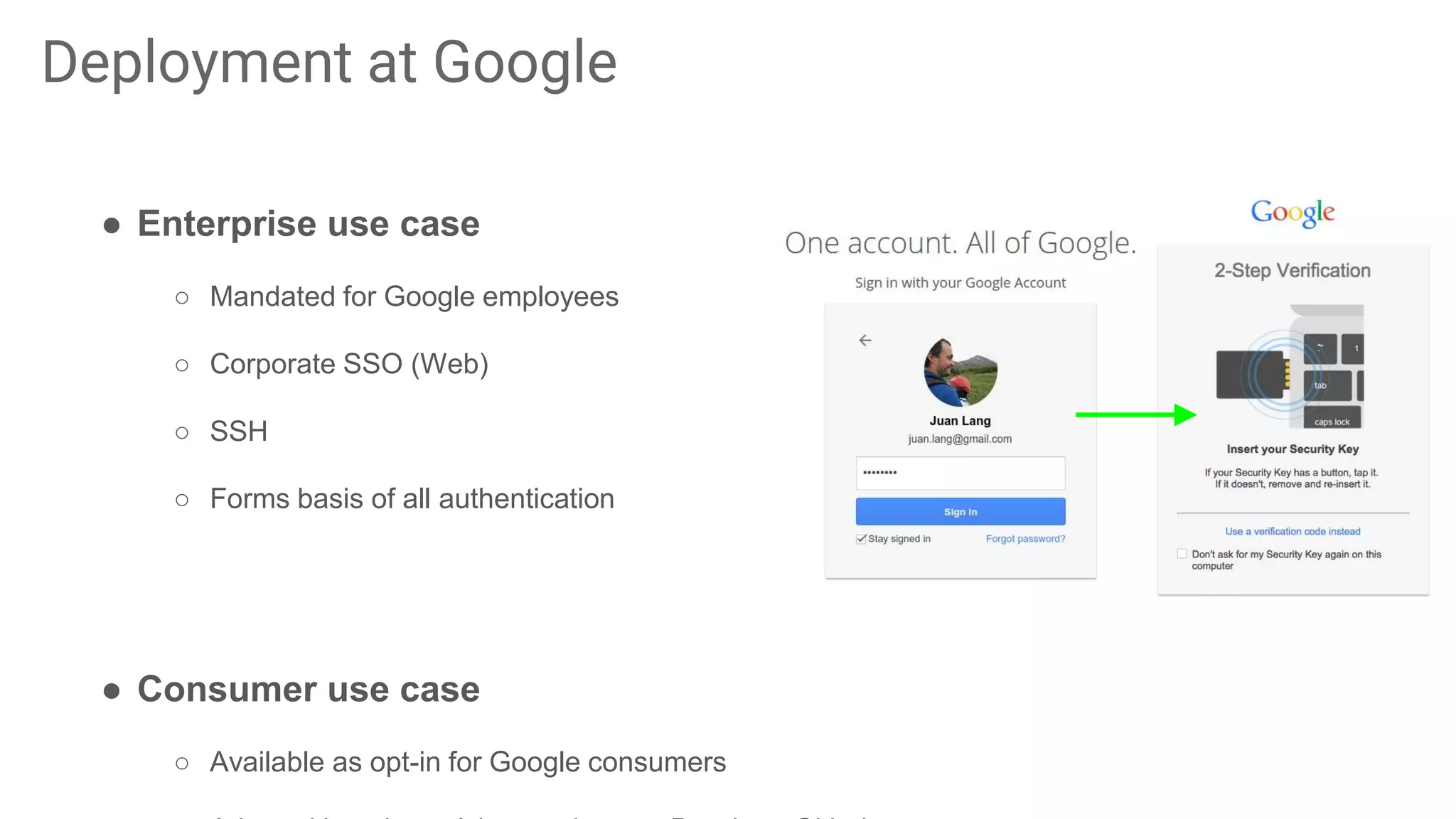
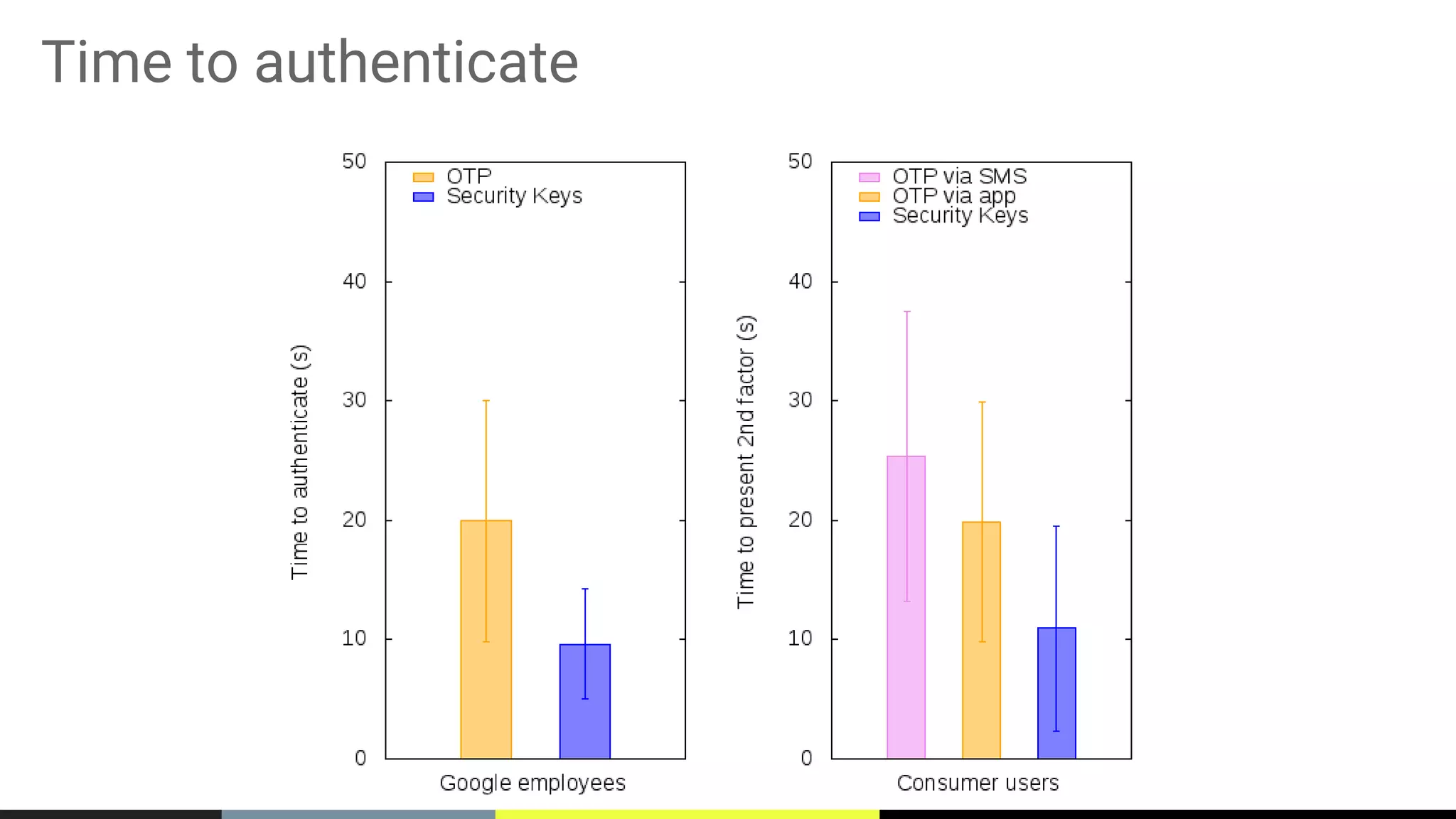
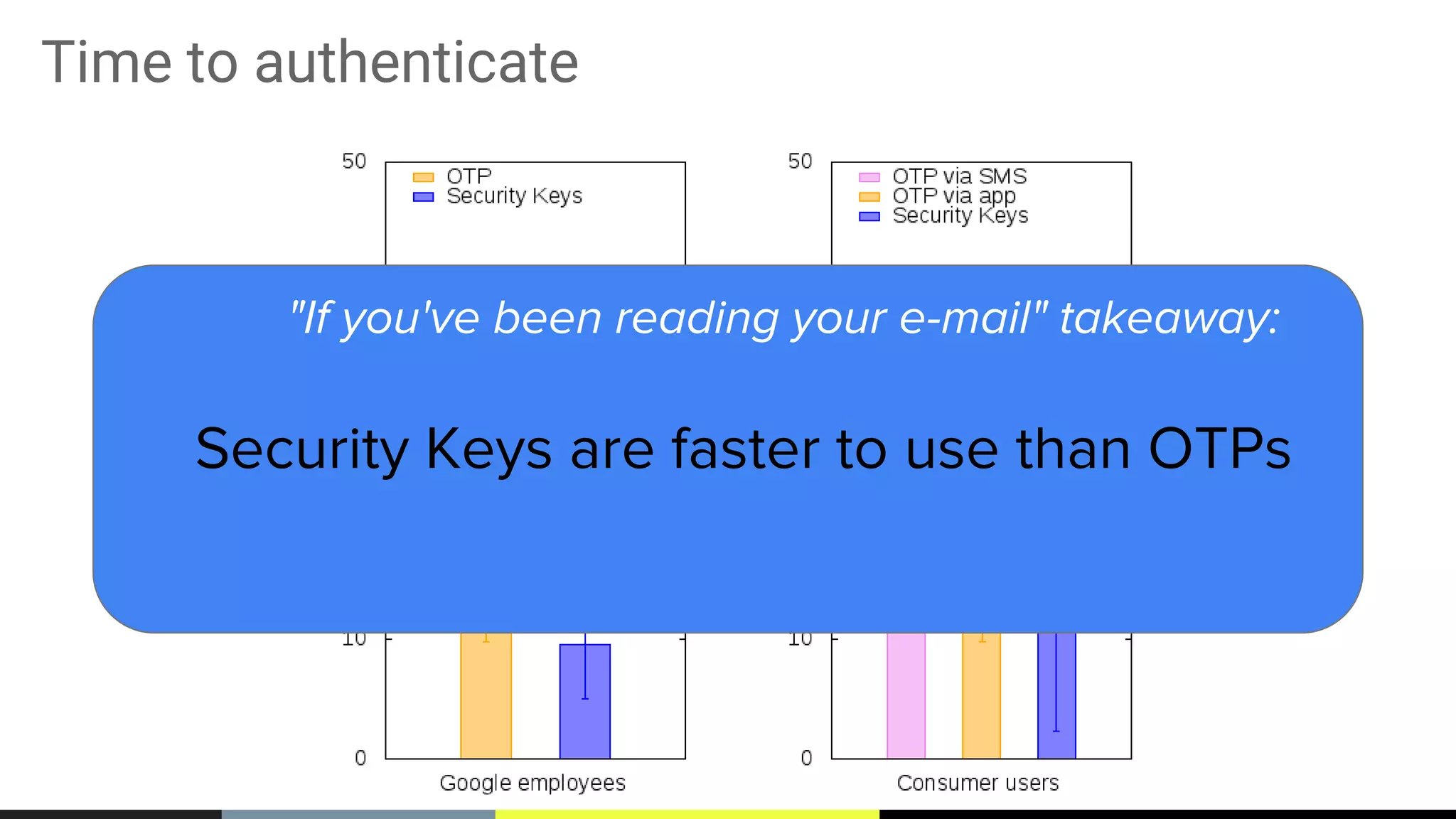
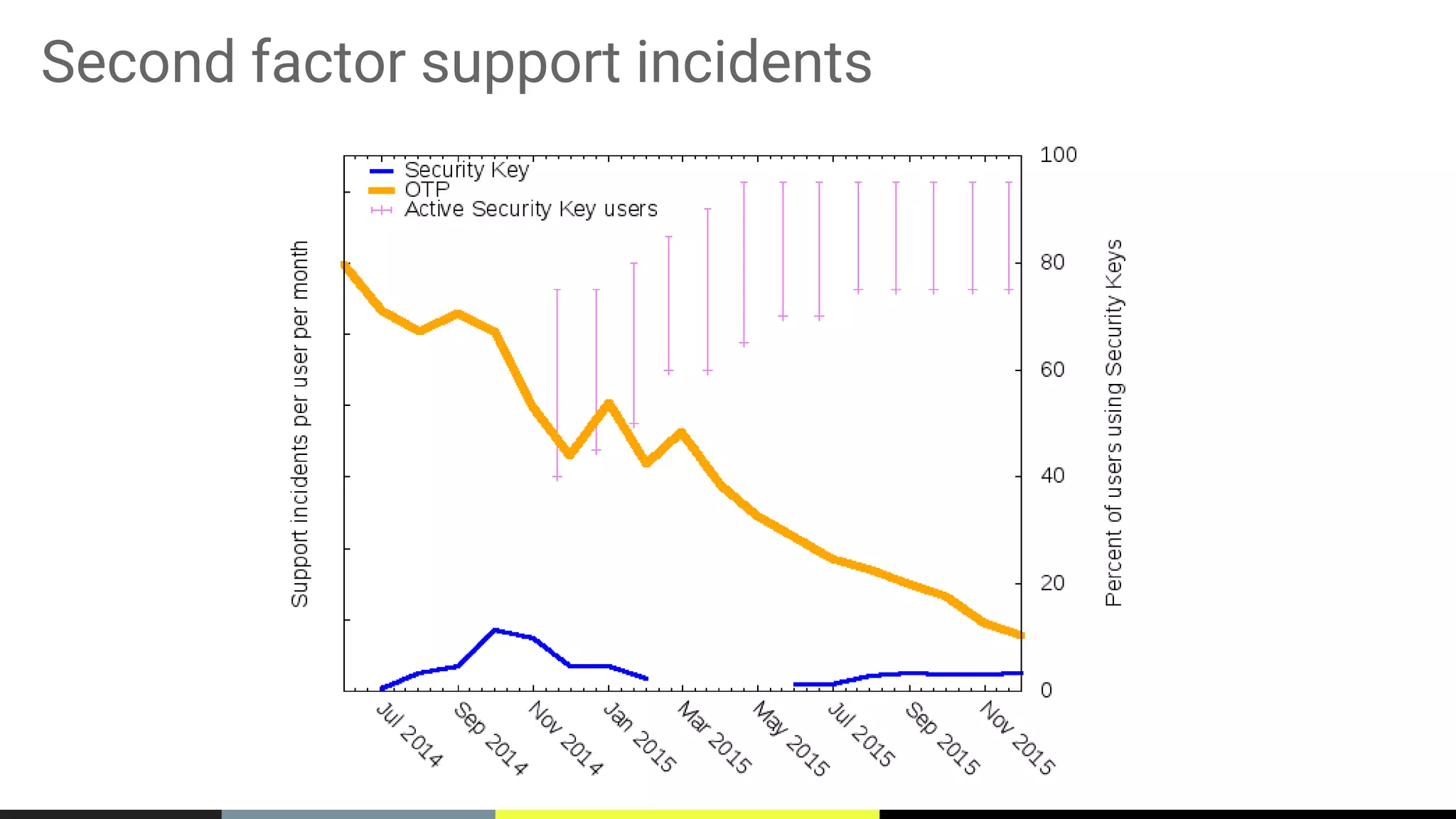
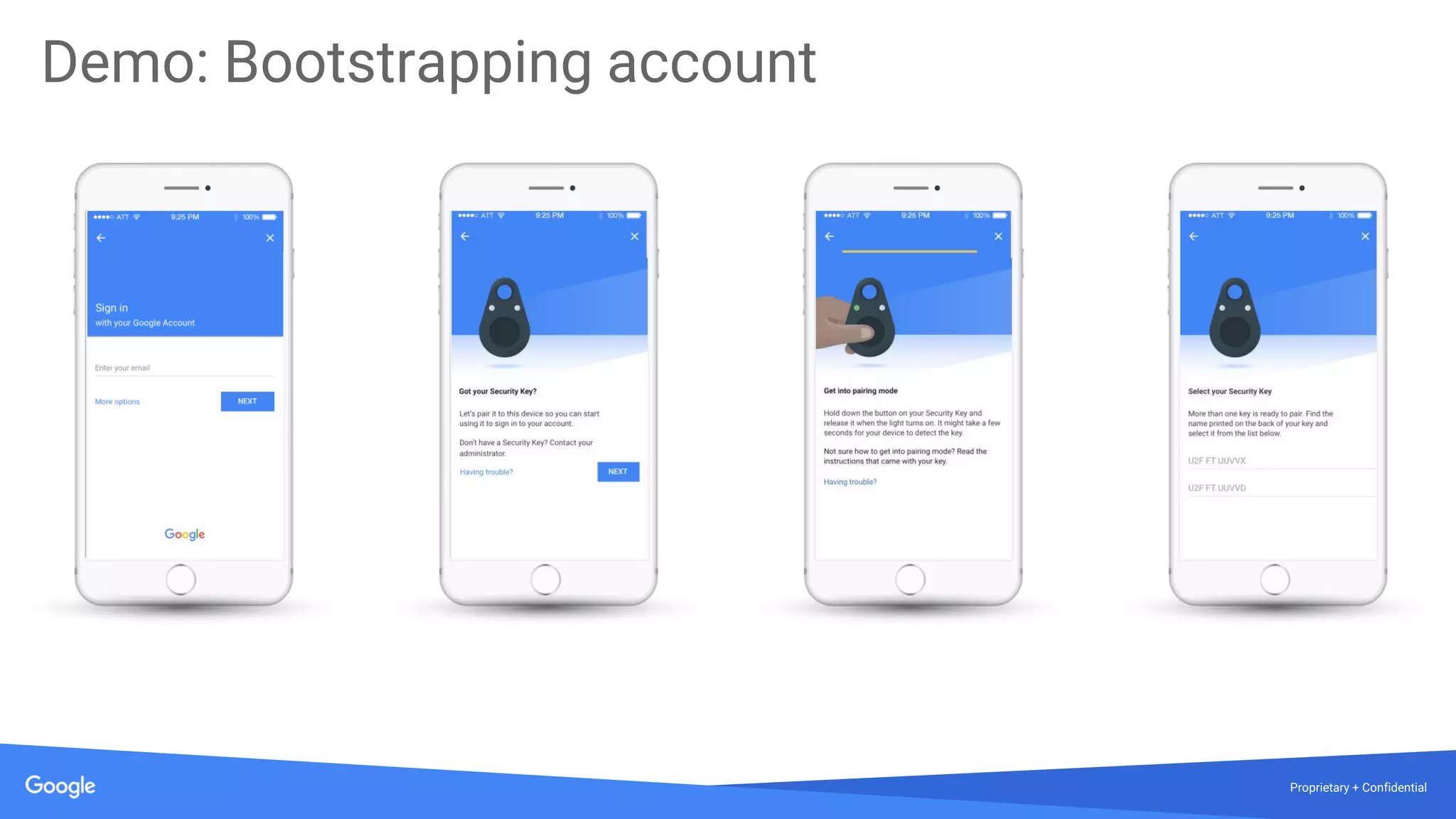
The document discusses the vulnerabilities of traditional password-based authentication and the need for stronger, more secure alternatives like security keys. It outlines how security keys operate using public key cryptography, significantly reducing phishing risks and support incidents. Additionally, it provides guidance for deploying security keys at scale and using them with various platforms, including Google and others.